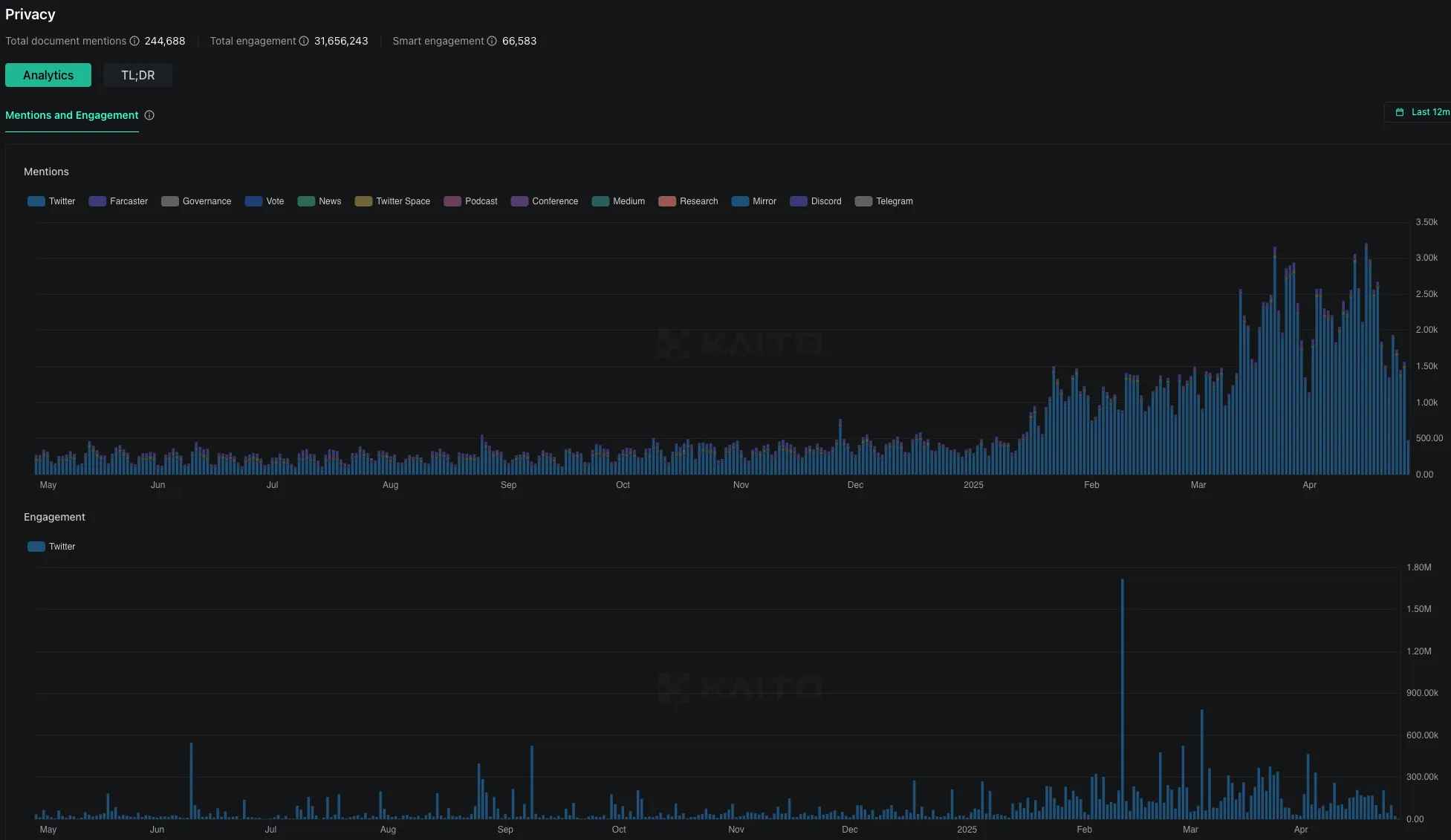
The Missing Cloud Primitive
Nilion addresses the privacy issue in cloud computing by allowing encrypted data to be processed without needing decryption. Today, every AI workflow, credit-scoring engine, or IoT fleet still funnels sensitive records through a trusted server or hardware enclave. That construct exposes a single point of failure: it expands the attack surface, violates emerging privacy mandates, and concentrates operational risk.
Nillion eliminates that failure point by letting any workload run directly on encrypted data. Encrypted assets never leave cryptographic protection, as Petnet shards encrypted inputs across decentralized nodes while nilChain manages payments, staking, and governance. Each read, transform, or signature over encrypted assets consumes $NIL. That’s the token demand sink.
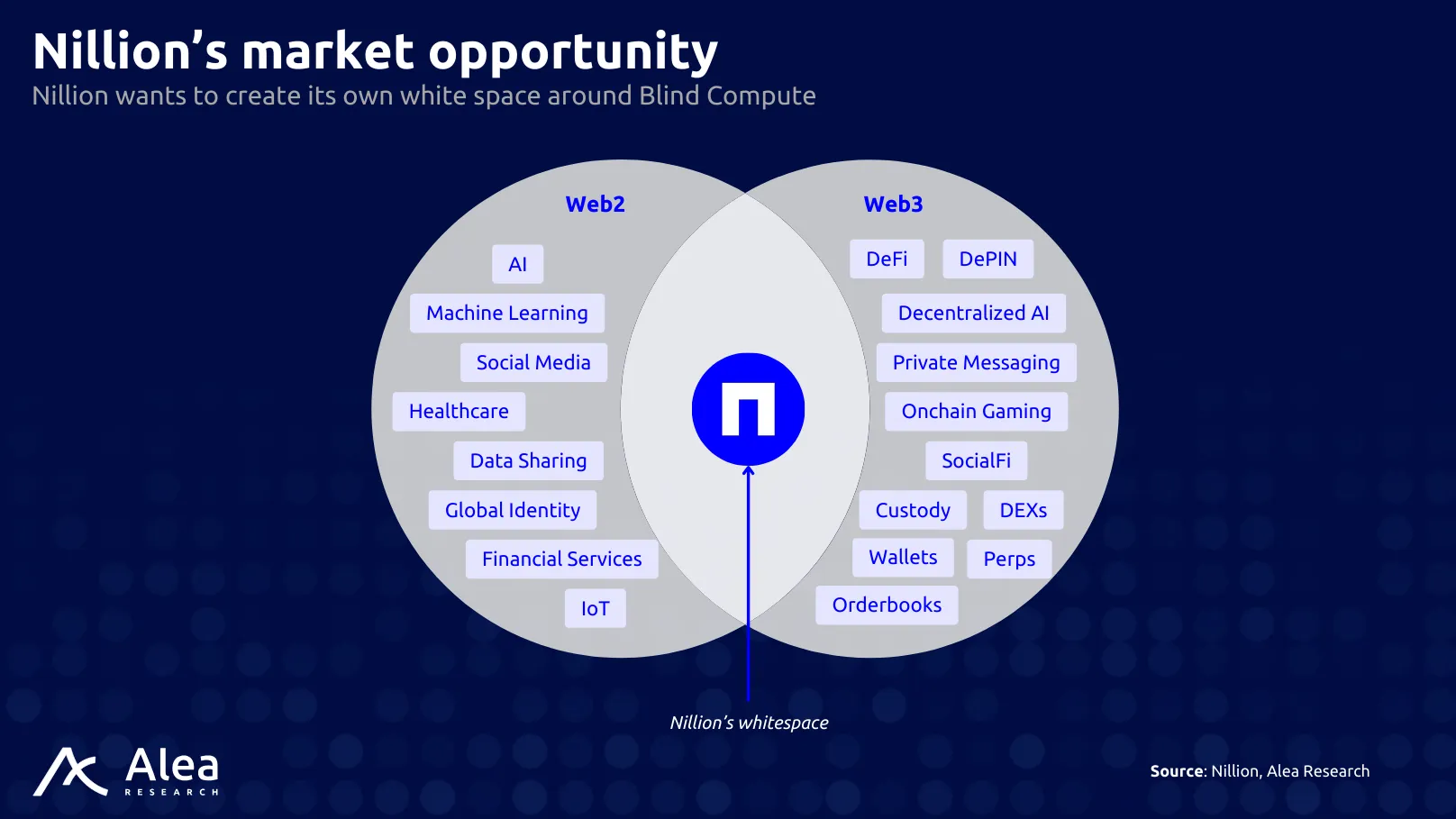
Bridging a structural gap between AI and privacy, Nillion is creating a new market sector by building where no one is: computation on encrypted data without decryption. That narrative can potentially attract institutions and AI firms if execution proves real, especially when Nillion is the first and only entrant targeting this challenge. It’s not competing for liquidity with DeFi L1s or L2s; it’s building new demand. Supply unlocks are a concern, but vesting is long, and major listings give liquidity depth. The speculative component is also overshadowed by being the vehicle granting exposure to the first cloud-grade primitive that prices privacy as a metered resource, right at the very moment when that AI, DePIN, and data-sovereignty regulation make that meter indispensable.
Key Takeaways
- Privacy Compute as a Missing Primitive: Nillion enables computation on encrypted data without decryption, a foundational capability absent in both Web2 and Web3. It faces no direct competition with equivalent scale or architectural modularity.
- Separation of Compute and Consensus: Nillion decouples privacy-preserving computation (off-chain) from settlement (on-chain), delivering cloud-like scalability with decentralized trust while flexibly integrating MPC, FHE, ZK, and TEEs depending on workload constraints.
- Token Demand Drivers: Each encrypted read, write, or blind signature requires $NIL as gas, creating hardwired, consumption-based token demand proportional to network usage.
- Market Tailwinds: The convergence of data-hungry AI systems and tightening global privacy regulations makes blind computation a non-cyclical, horizontal requirement across sectors.
- Strategic Advantage: Major unlock cliffs for insiders begin in Q3 2025 (Series A) and peak in Q1 2026 (Seed + Core Team), allowing a 12-18 month window to compound adoption and compute usage before structural token sell pressure intensifies.
- Upcoming Catalysts: Permissionless validator onboarding, enterprise-grade SLAs, and tier-one exchange listings in 2025 are poised to drive usage and price discovery.
- Invalidation & Risks: Despite strong infrastructure and partnerships, actual demand for blind compute is early-stage, and speculative flows currently outpace utility-driven token velocity.
From Patents to Mainnet
Founded in 2021, Nillion evolved from a cryptographic research publisher into implementing a dual-layer privacy-preserving compute network. Key milestones include the official release of foundational papers, an internal testnet in 2023, and the public release of a developer SDK along with the Coordination-Layer testnet by mid-2024. That same period saw the rollout of the Nada AI toolkit and initial Petnet pilots, achieving cross-chain integrations with NEAR, Aptos, and Arbitrum in Q4 2024. By March 24, 2025, Nillion had launched its Alpha Mainnet, open-sourced core repos, conducted an airdrop, and introduced production-grade blind-compute modules, marking its transition into a live privacy infrastructure.
Nillion is led by ex-banker Alex Page, serial founder Andrew Masanto (Hedera, Reserve), and cryptographer Dr Miguel de Vega, inventor of NMC (Nil Message Compute). Key executives include the COO, Mark McDermott, the CMO, Andrew Yeoh, and the Head of Growth, Lukas Bruell.
Funding stands at $50M, starting with a $22M seed round in December 2022, which deliberately included over 150 investors to avoid cap-table concentration. Subsequent rounds added Hack VC, HashKey, Animoca, and many notable angels. Nillion completed two additional fundraising rounds in 2024: a Series A and a community round. Both rounds occurred at the same valuation and with the same token supply, bringing the total amount raised to $50M.
The community round (CoinList) had the same valuation as the Series A round, a strategy not commonly adopted by protocols. Additionally, Nillion provided the same percentage of the token supply for the community round.
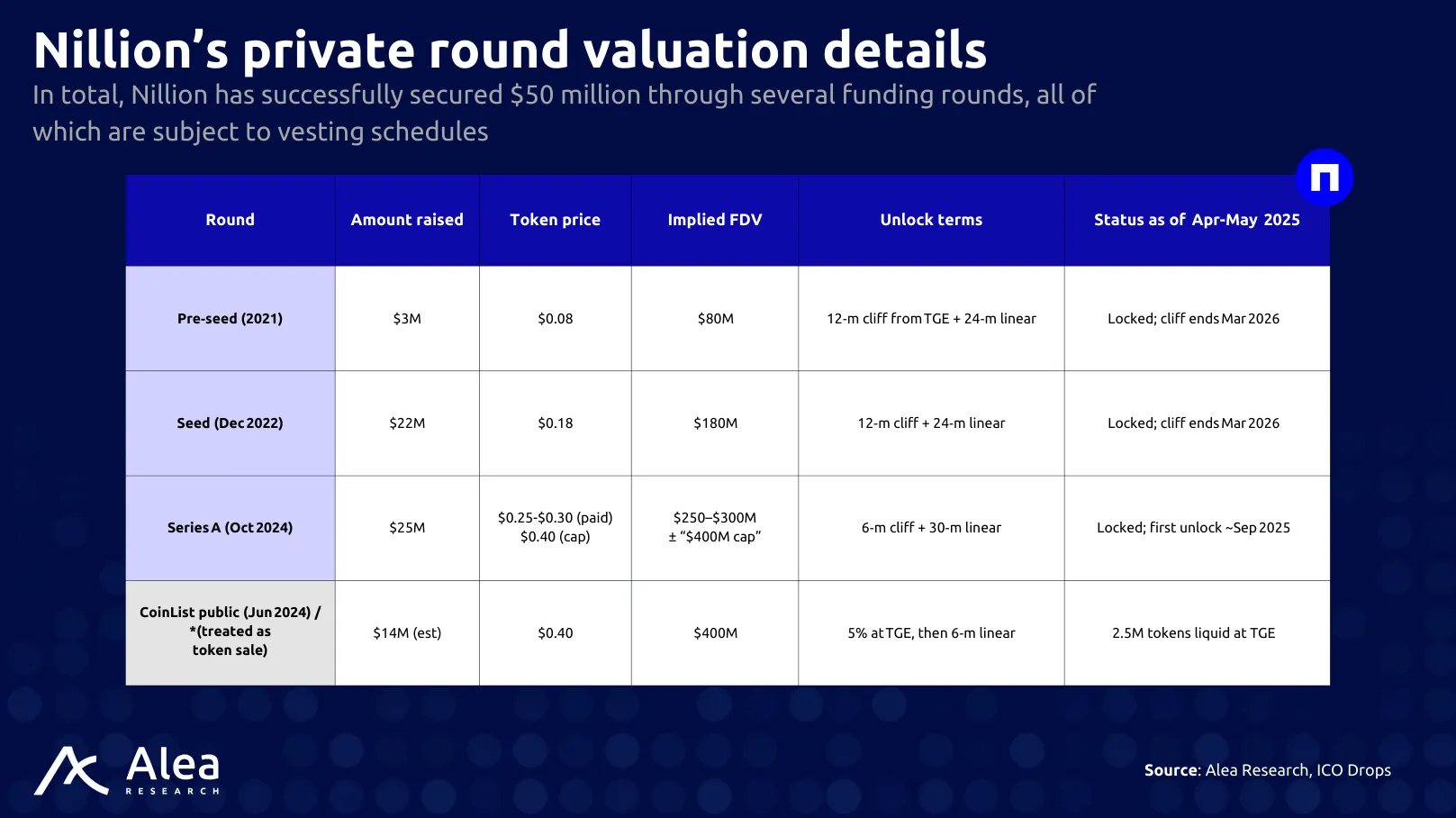
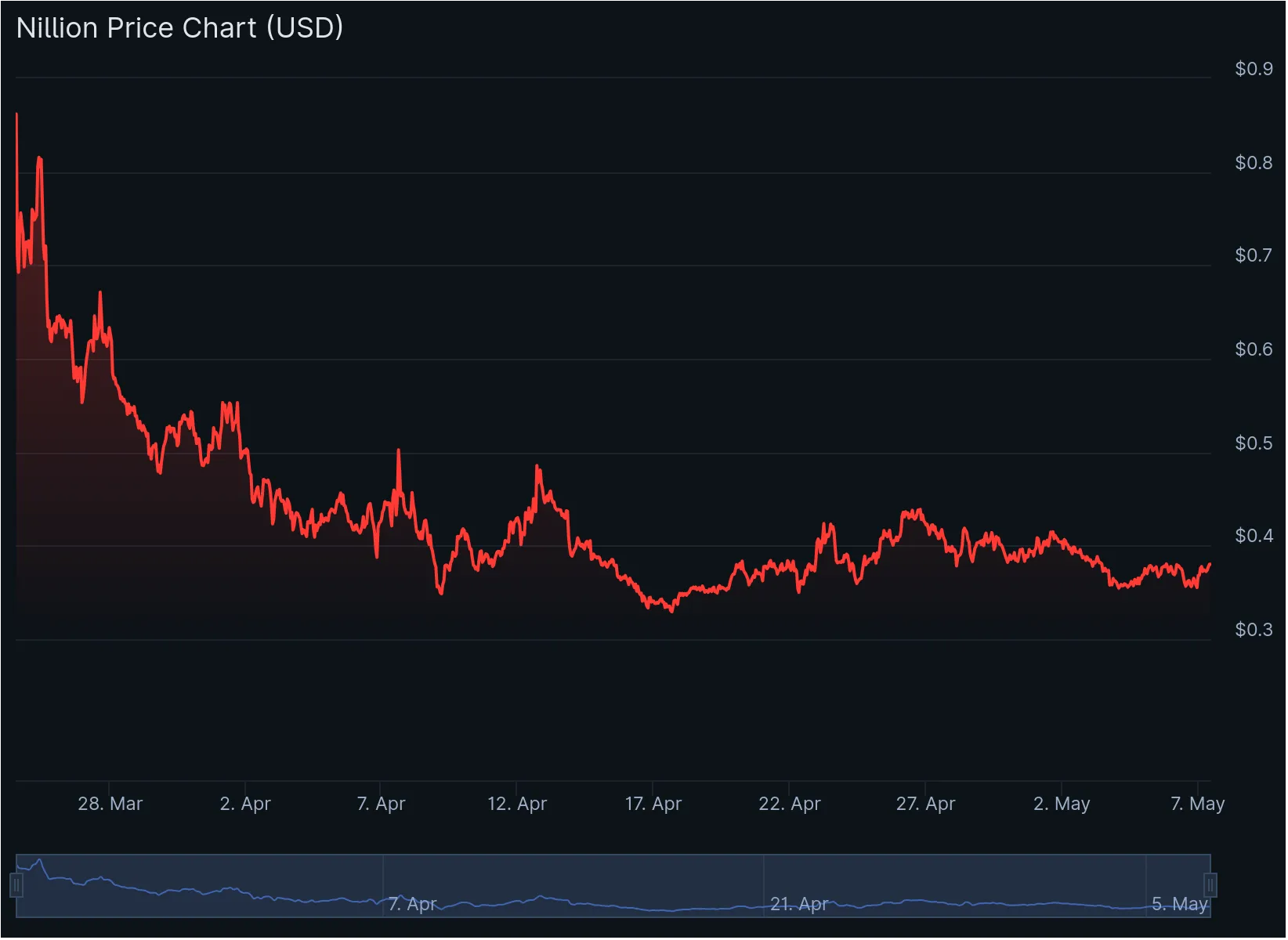
As of now, the price of $NIL is hovering around $0.40, meaning there’s an opportunity to accumulate at nearly the same valuation as the last two rounds while remaining liquid. A price drop around the $0.35 level would present a chance to build a solid position at an 8-10% discount to the last public round while front‑running the seed unlocks. Next steps would be monitoring liquidity spikes around September 2025 (Series A cliff) and March 2026 (seed cliff) for potential structural entry points.
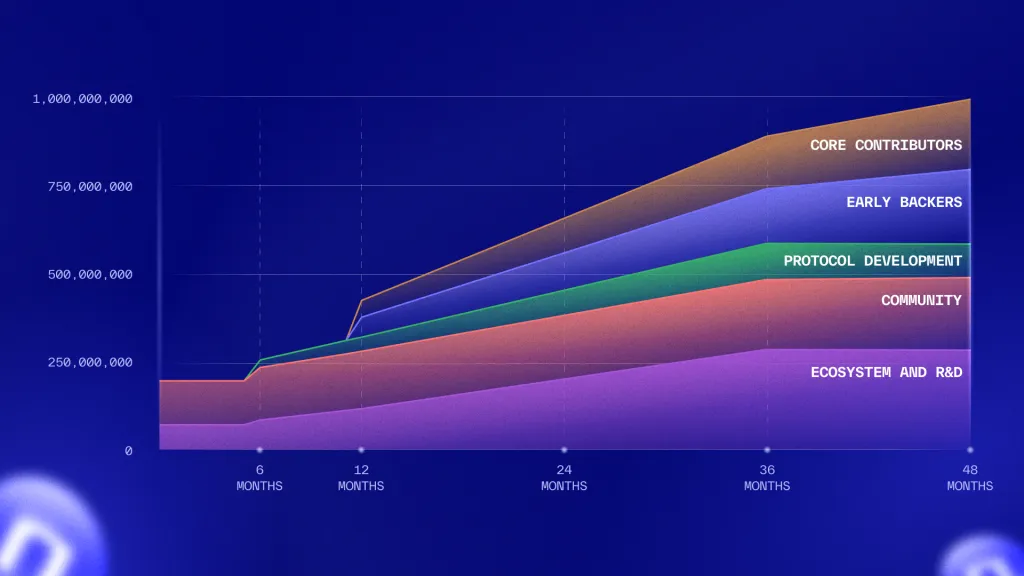
Unlocks cliffs range from 6 to 12 months, followed by linear vesting over 48 months. Specifically, Core Contributors and Early Backers (collectively holding 41%) are subject to a 1-year cliff following the TGE, after which their tokens vest linearly on a monthly basis over a 3-year period. Tokens sold in the Coinlist Community Round have varied schedules, with some having 5% unlocked at TGE followed by a 6-month linear release, and others with 25% unlocked with a 24-month vesting period.
Turning Encrypted Data into a Monetizable Asset
Global business relies on transferring and handling regulated data, including medical records, financial information, and personal identifiers. However, these datasets currently remain siloed due to sharing risks, creating vulnerabilities to breaches and compliance failures. To remove that barrier, Nillion lets multiple parties compute on that data while it stays cryptographically veiled, enabling use cases such as cross-hospital analytics, private AI fine-tuning, sealed-bid trading, and on-chain KYC without custody leakage.
Public blockchains expose all data by default, a dealbreaker for many enterprise and institutional use cases. Nillion adds the missing privacy layer, allowing regulated or sensitive transactions (e.g., private bids, identity-aware DeFi) to be processed without revealing underlying data. No existing L1 offers this capability in a trust-minimized form.
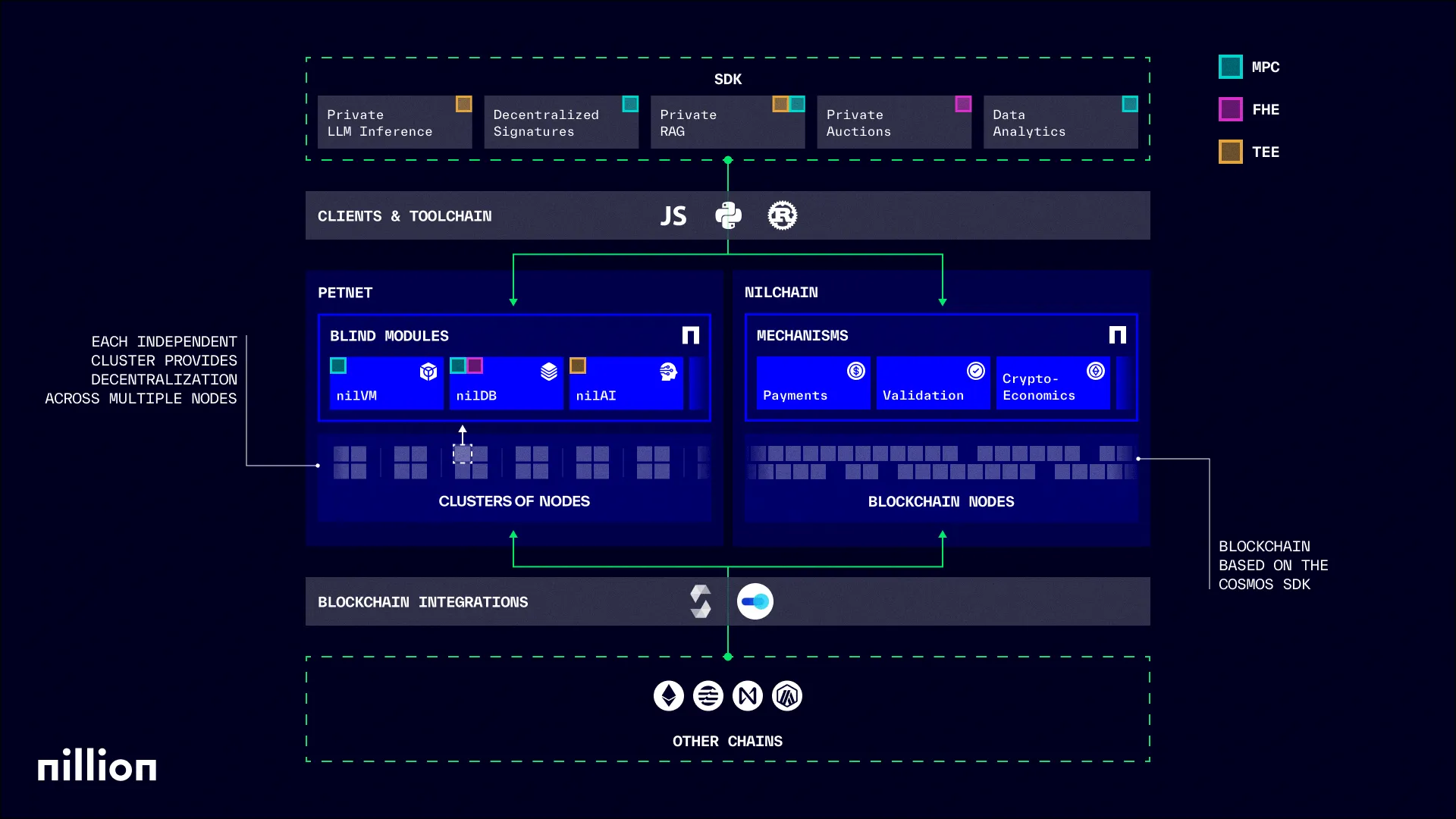
Nillion’s dual-layer architecture combines Petnet, an orchestration layer using NMC for low-latency processing of secret-shared data, with nilChain, a Cosmos-SDK blockchain for $NIL transfers, staking / slashing, validator elections, governance votes, and cryptographic receipts for off‑chain Petnet computations, giving full on‑chain traceability. Petnet’s NMC (Nil Message Compute) non-interactive MPC algorithm minimizes latency compared to traditional MPC or ZK circuits and supports other privacy techniques via plugins.
Nillion’s edge is not only speed but optionality. By pairing the ultra‑low‑latency NMC core with a modular plugin layer, Petnet can load the best privacy primitive (MPC, ZK, FHE, or future post‑quantum schemes) for each workload instead of forcing every use‑case through the same cryptographic bottleneck. That keeps developers unchained from vendor lock‑in, lets the protocol evolve as new research emerges, and gives allocators confidence that the compute layer will stay relevant as regulatory and performance requirements change.
Macro Tailwinds for the Privacy Stack
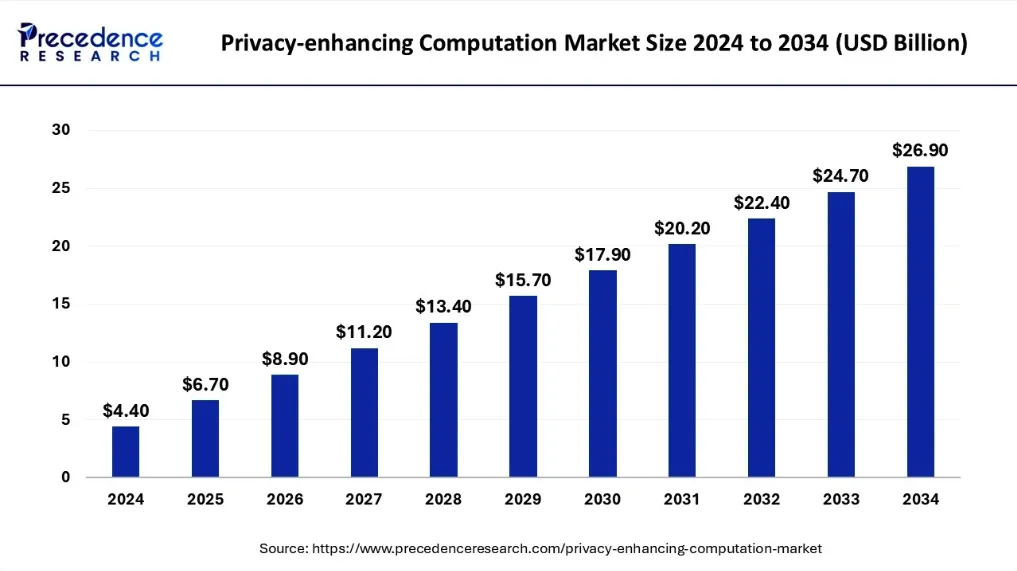
Global demand for privacy-enhancing computation is accelerating, and the AI-data-privacy stack is scaling from a niche into a multibillion-dollar market. Researchers expect privacy-enhancing computation (MPC, FHE, federated learning) to reach $26.9 billion by 2034 on a 19.9% CAGR.
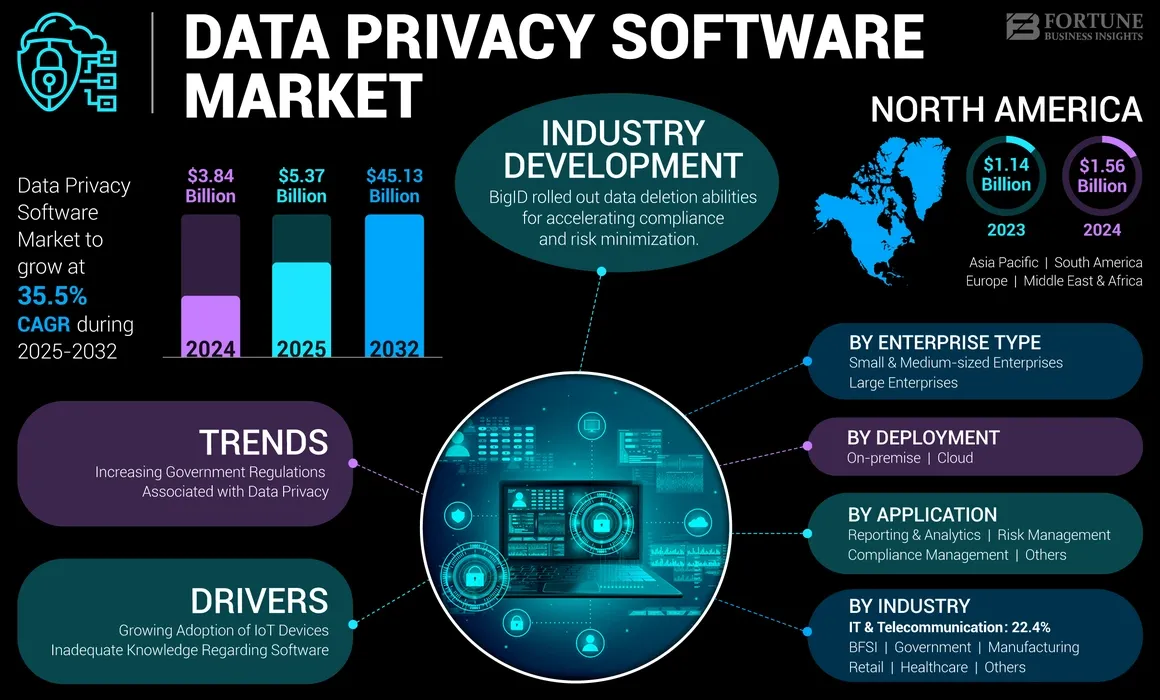
Enterprise-grade privacy tooling is moving in parallel: off-the-shelf AI-governance software will quadruple, hitting $15.8 billion by 2030 at ~30% CAGR, as firms scramble to validate training data and model outputs under tightening rules; dedicated data-privacy-software spend itself is forecast to jump from $3.84 billion in 2024 to $45.1 billion by 2032, compounding 35% annually.
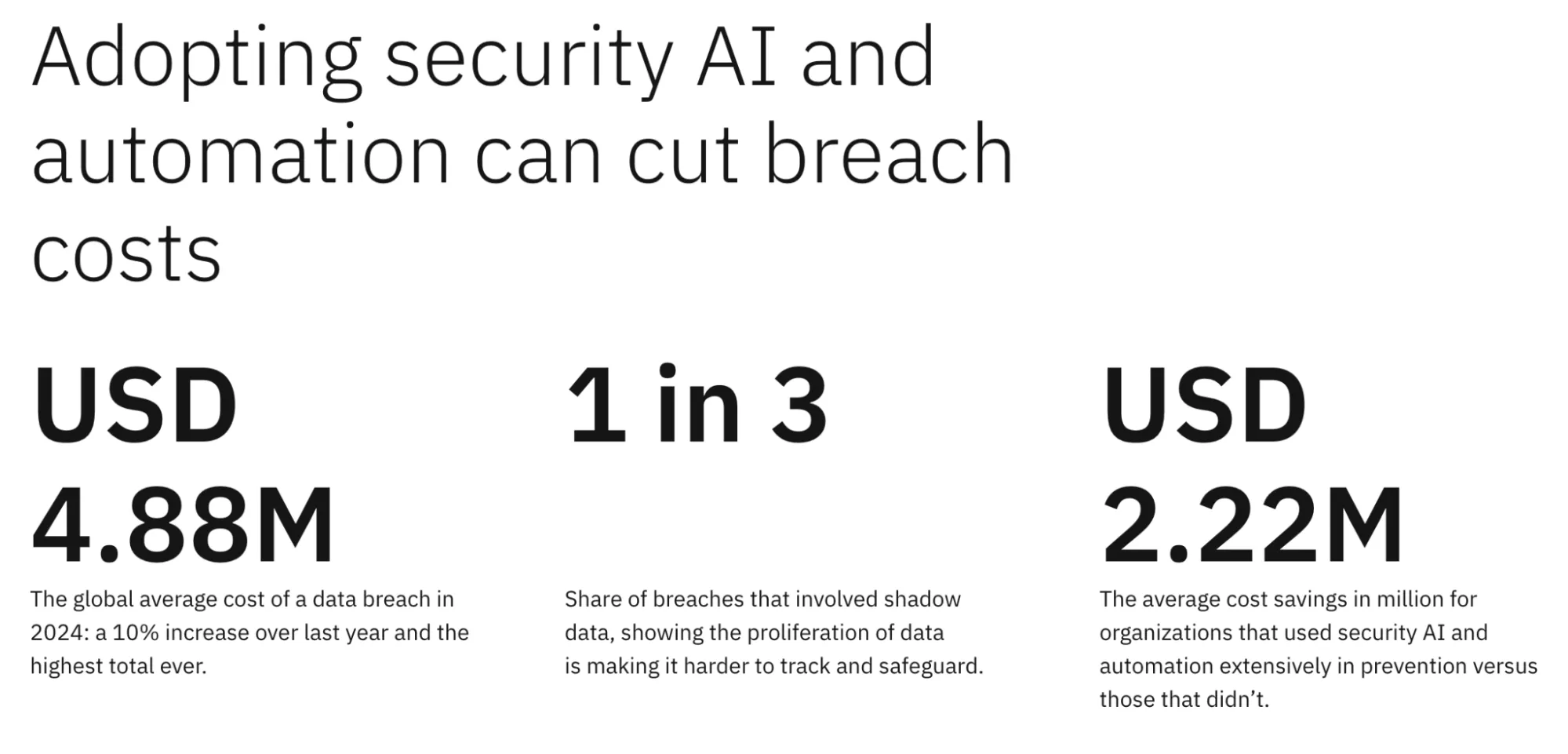
The driver is simple: the average breach now costs $4.88 million, up 10% year-on-year, and one-third of incidents involve “shadow data” that organisations lost track of in sprawling AI pipelines. Regulators and boards are aligning: the EU AI Act will force strict data-governance requirements in August 2025, while U.S. states roll out copycat privacy laws; breach fines and lost business already dwarf the price of prevention.
Nillion’s privacy-computation angle has a strong edge and considerable potential for TAM sitting at the convergence of multiple secular waves, enabling compute without custody and transforming regulated datasets into usable assets without compromising trust or compliance. The blind-compute concept is unique, with clear demand from AI and secure data analytics, and it has credible partners lined up. That combination typically attracts liquidity and momentum.
This surge in demand and awareness aligns perfectly with what Nillion offers. Its blind-compute network lets multiple parties run AI training or analytics on encrypted shards without ever reconstructing raw data, eliminating the “shadow-data” exposure IBM highlights. The Nil-token model meters that compute and rewards the nodes that provide it, while its modular PET stack (MPC, FHE, ZK) satisfies the same privacy-enhancing-computation workflows researchers size as the fastest-growing slice of AI spend. As breaches escalate and compliance budgets expand, Nillion offers enterprises a cloud-neutral approach to demonstrate that they never accessed the customer data they just processed, transforming a runaway liability into a token-priced service line.
Structural drivers such as regulation, cyber-risk, and AI data hunger outlive crypto cycles; cyclical risk is predominantly token-unlock supply and speculative leverage. On a 12-24 month horizon, we are early in the privacy-compute S-curve: usable MPC/FHE infrastructure has only just escaped academia and is making headlines. Therefore, entry before enterprise SLAs (Q4’25 roadmap) prices technology optionality at discipline-adjusted multiples.
Nillion’s Architectural Moat
Nillion’s edge is architectural and adaptive. Unlike single-tech privacy chains locked into SGX or a fixed cryptographic method, Nillion runs a modular blind-compute mesh. Petnet dynamically selects the most efficient privacy primitive per workload (one-message MPC, FHE, ZK, or even TEEs), avoiding the performance bottlenecks seen in competing alternatives. The NMC prototype removes the multi-round chatter that slows Partisia and cuts the prover cost, which still hampers ZK-heavy designs. Because the computation runs off-chain and only payments settle on nilChain, throughput scales with cloud hardware, not blockchain consensus. This has already been proven by early AI and dark-pool pilots. The trust anchor is economic: stake-slash security and no reliance on Intel microcode, so the constant SGX CVE cycle cannot blow up the network.
| Project | Tech Stack | Trust Model | Live Status / TPS | Metered Fee (USD) |
| Secret Network | SGX-backed confidential smart contracts | Hardware enclave; must trust Intel SGX | Mainnet since 2020; every validator runs SGX | $0.001 per 100 k‑gas tx (0.005 SCRT × $0.20) |
| Oasis (Sapphire) | Confidential EVM + ParaTimes on Intel SGX | Hardware enclave + PoS | Mainnet: devs choose public or private state | ≈ $0.000003 per std tx (0.0001 ROSE) |
| Partisia | Multi-round MPC L1 | Pure cryptography; no hardware | Mainnet | $0.06 for 1 KB tx + 1M WASM instructions |
| Aleo | zkSNARK L1 with Noir DSL | Cryptographic proofs | Mainnet | ≈ $0.010 per simple execute (0.041 credits × $0.24) |
| Nillion | Modular PET mesh (1-msg MPC, FHE, ZK, optional TEE) | Stake-slashing, no trusted hardware | Mainnet Mar-25; off-chain clusters hit cloud-like throughput | TBD – not disclosed. Nillion claims “10‑100× cheaper than classical MPC” |
The moat extends through distribution. Nillion is chain-agnostic middleware, integrating via SDKs with Aptos, NEAR, and Arbitrum to inject privacy into ecosystems hosting thousands of developers. A Nucleus program has already funded 50-plus dApps across AI, DeFi, and genomics, giving multiple demand legs before any one vertical matures.
Capital is deep and strategically deployed. In total, $50M+ has been raised from Hack VC, HashKey, Animoca, and Web3 founders, funding an estimated three-year runway to harden NMC and open validator entry. Where competitors are boxed into hardware reliance, single PET stacks, or enterprise-only sales, Nillion’s software-native, token-metered, and modular approach positions it to ride the structural wave of AI privacy mandates while remaining composable and chain-neutral. That’s an orthogonal moat few can replicate.
Privacy-as-a-Service: An Asymmetric Bet
$NIL has underperformed against other privacy coins since TGE. This lag is caused by the launch supply meeting weak organic demand. The airdrop and launchpool unlocked a large block of tokens into the hands of holders with no acquisition cost, so early selling drove the price below the private and community round level. That overhang is now largely absorbed. Circulating supply is still <20 % of the fully diluted number, and daily volume is modest, so relatively small bids can lift the market. In other words, liquidity is thin, float is limited, and the token trades cheaper than the price paid by seed and Series A investors, yet buyers remain fully liquid. If the privacy narrative regains momentum, $NIL offers leveraged upside from this oversold base while the downside is anchored by those historical valuations.
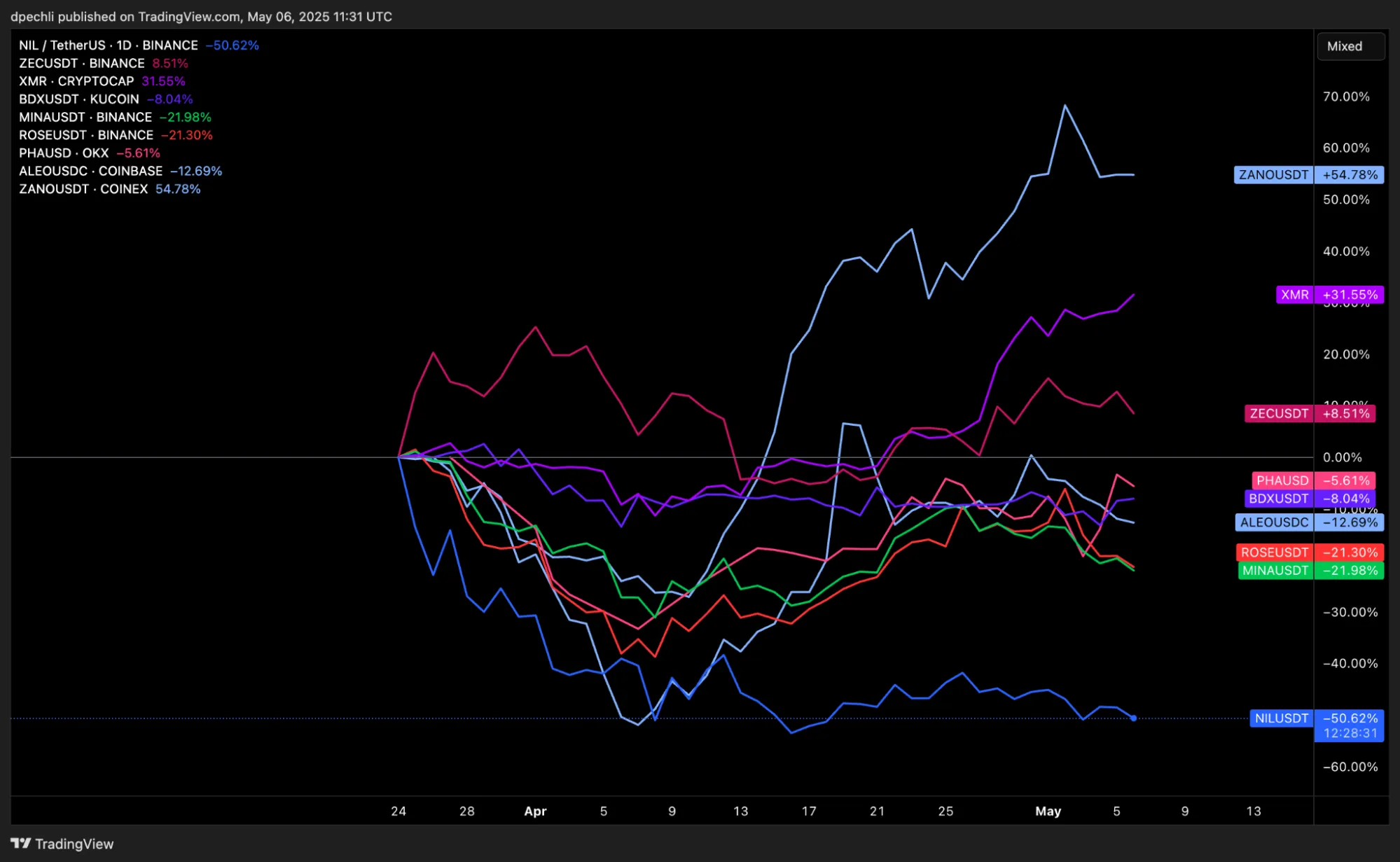
Investors are still pricing Nillion like a niche privacy coin, not as the default co-processor every chain and AI stack will need to remain compliant and competitive.
Nillion has a novel cryptographic approach, a “blind compute” that allows running operations on data without ever decrypting it. Turning privacy from a compliance burden into a metered service layer opens new use cases in AI and enterprise privacy. Factor in first-mover advantage and a stack of partnerships across L1s, and you’ve got a serious moat that can pull in demand, which is the main catalyst. That’s the main reason for the thesis.
The network forces real demand for $NIL because you can’t use the compute layer without it. More usage of the blind-compute solutions means more fees paid in $NIL. With supply relatively fixed and a real technology moat driving adoption, that fee flow props up the token’s price. If the tech delivers, the token should reflect that demand.
Nillion’s architecture is live, differentiated, and modular. That makes it capable of serving AI, compliance, and enterprise use cases that existing privacy chains cannot address due to technical or economic constraints. Meanwhile, token supply remains mostly locked, and upcoming catalysts (validator onboarding, enterprise SLAs, major listings) are set to unlock usage-driven demand. If Nillion delivers even modest adoption as the default privacy layer for AI and regulated data, $NIL’s fee-based demand could rerate it from an underpriced utility token to reflecting the premium attached to core infrastructure.
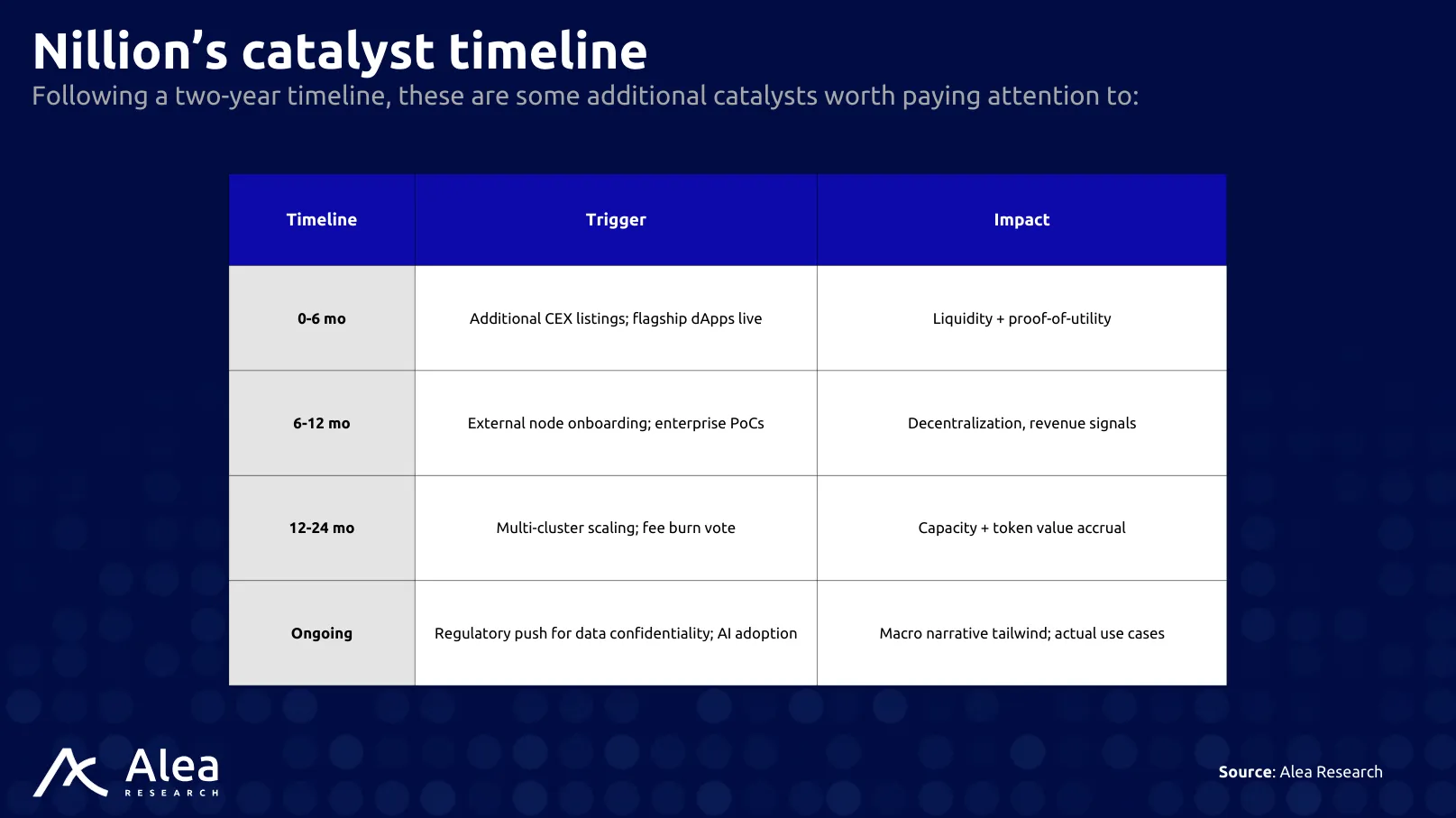
The catalysts and value drivers for Nillion all focus on actual demand and events that place privacy at the epicenter of attention:
- Validator Opening (Q3 2025)
Permissionless node onboarding converts wait-list demand into stake lock-up and fee capacity. - Enterprise SLA Tier (Q4 2025)
Paid contracts move usage from subsidised to full-price, validating the revenue model. - Major Exchange Listings
Coinbase or OKX listing widens fiat rails and removes Binance dependency. - Narrative Push
As the significance of safeguarding data becomes increasingly apparent, the importance of privacy grows more urgent.
- Privacy Incidents
Data breaches, scandals, and other privacy incidents will highlight the value proposition of solutions like Nillion.
Risks & Invalidations
Nillion’s flywheel: fee revenue → stake yield → node capacity → more workloads, rests on two unsolved tensions: (1) compute‑centric cash flows versus consensus‑centric security costs, and (2) a front‑loaded insider supply curve. Unless the revenue split and governance structure evolve before the 2026 cliffs, the economic game could equilibrate at low security or high user cost, either of which snaps network growth.
Price action is behaving rationally: the market is clearing present and expected supply against unproven demand. Until one (or several) of the following factors materialise, $NIL will likely keep trading like a high‑FDV pre‑revenue infrastructure play.
- Permissionless staking that locks meaningful float.
- Visible, fee‑driven burn or buy‑pressure.
- Evidence of non‑subsidised enterprise workloads driving token spend.
If, by Q1‑26, the network is still showing fewer than ten live dApps, flat fee throughput and only pilot‑level enterprise integrations, the thesis weakens on three fronts at once: the go‑to‑market engine (developer traction, validator onboarding, SLA‑grade enterprise roll‑outs) will have proved slower than advertised; the flagship “blind compute” primitive will remain a solution in search of paying users, meaning $NIL continues to trade as a purely speculative chip; and the March 2026 cliff, when 41 % of supply bulk‑unlocks, would arrive against a backdrop of tepid demand, leaving the market to digest a step‑change in float. In that scenario, supply‑led price compression is not a tail risk but the base case.
Conclusion
Nillion transforms privacy from a compliance cost into an addressable market, and $NIL is the granular unit to price that market. Its architecture is ambitious yet pragmatic, its team pedigreed, its cap table broad, and its token mechanics engineered for long-term alignment. Execution risk remains high, and insider cliffs loom, but the roadmap provides clear KPIs that will validate or nullify the thesis well before peak unlock pressure. We rate current conviction moderately high with a mandate to scale exposure tactically around unlock windows and mainnet usage data.
References
Trading View – $NILCoinGecko – Nillion
Privacy-enhancing Computation Market Size, Share, and Trends 2025 to 2034 – Precedence Research
Global Commercial AI Software Governance Market Forecast, 2024 To 2030 – Forrester
Data Privacy Software Market Size – Fortune Business Insights

