Introduction
Restaking has emerged as a novel solution to address the economic security challenges faced by new decentralized protocols that require consensus mechanisms but that live fundamentally off-chain. By allowing previously staked assets to be utilized again, restaking allows protocols to borrow trust from a decentralized and credible-neutral layer, such as Ethereum. This makes it possible for restaking protocols to borrow slashing rights from the original validator set in order to leverage the economic weight of already staked assets. This primitive was pioneered by EigenLayer and originally conceived the use of existing staked assets, such as $ETH staked in the Ethereum Beacon PoS chain, to be used to secure multiple services and applications. This would allow users to earn enhanced yield (from both Ethereum PoS rewards and AVS yield) while simultaneously reducing the bootstrapping costs for new protocols, which would no longer have to create their own economic security from scratch by relying on a native token from day 1.
Figure 1: Transforming rollup economics through restaking
Source: EigenLayer Presentation
Since the original thesis and conceptualization, many protocols have joined this market vertical, ranging from Liquid Restaking Tokens (LRTs) to marketplaces for decentralized trust. The latter will be the focus of this report, which will expand on the unique selling points of the 3 main market leaders in the Ethereum ecosystem: EigenLayer, Symbiotic, and Karak. This report will explore the rapid growth of this market sector, emphasizing the tradeoffs and mechanism designs put in place by different protocols in order to connect stakers with node operators and protocol developers.
Over the past year, these protocols have advanced from relying solely on $ETH-backed collateral to supporting multi-asset collateral and offering more flexible security solutions. For many, this flexibility creates an incentive for risk-taking, but others view this as an opportunity for every token to have the potential opportunity for being restaked, capturing additional value as a result. Expanding support to other assets allows for a more diversified risk profile, but the additional revenue streams also carry extra risks. The report will also analyze the main factors that should be considered for asset selection and the key considerations to account for from a DeFi user’s perspective.
Key Takeaways
- Applications that can not rely on Ethereum’s robust economic security, often struggle to establish their own security, requiring significant capital and resources – most often with their own native token and crypto-economic incentives to bootstrap and retain a large validator set.
- Restaking seeks to address the challenges faced by new protocols that require the achievement of distributed consensus for its operation in a trustless manner.
- EigenLayer pioneered restaking, with Symbiotic and Karak emerging as the main competitors. Although each protocol has unique characteristics, they share the common goal of connecting stakers, node operators, and protocol developers to enhance the economic security of new services that borrow trust from an existing substrate, such as the $ETH validator set.
- In just over a year, restaking protocols have rapidly evolved from being solely $ETH-backed to supporting a wide range of assets, and from pooled security models to more flexible solutions like attributable security.
- EigenLayer has earned strong support from the Ethereum community due to its conservative approach, which has instilled a high level of trust since its launch. However, learning from its own experience and competitors, it has shown adaptability. While it initially only supported $ETH-backed collateral, it has since expanded to support multiple assets.
- In contrast, Karak has focused on speed and yield opportunities with its multi-network and multi-asset strategy. It has taken an opportunistic approach to gain market share by enabling the restaking of LRTs already staked on EigenLayer. This allows users to earn rewards from LRTs, EigenLayer, and Karak simultaneously, giving farmers the opportunity to maximize their returns by stacking rewards across multiple protocols.
- Symbiotic positions itself between EigenLayer and Karak, serving as Paradigm’s answer to a16z’s investment in EigenLayer and supported by Lido co-founders through Cyber Fund. It launched on Ethereum mainnet but operates across multiple chains, offering a flexible, modular architecture. Like Karak, it supports multi-asset deposits, allowing any ERC-20 token to be used as collateral, with an abstraction layer that makes it both chain- and asset-agnostic. This enables crypto protocols to implement native staking for their tokens to enhance security. For example, Ethena has partnered with Symbiotic to provide cross-chain security for USDe using staked $ENA.
- The decision regarding the best tokens for restaking primarily depends on two factors: the economic security tied to the token’s price stability and liquidity, and the application’s business model and security requirements.
- While restaking offers clear advantages, such as enhanced security and additional yields, users must carefully consider risks, including systemic vulnerabilities, slashing, rehypothecation, and centralization concerns.
Background
Consensus is a core function of blockchains and distributed systems, vital for maintaining the chain’s immutability and block irreversibility—acting as the source of truth that all parties agree upon. Different blockchains can choose from a variety of consensus mechanisms, such as Proof-of-Stake (PoS), Proof-of-Work (PoW), Proof-of-Authority (PoA), etc, which help protect against Sybil attacks. These mechanisms encompass native L1 assets and token incentives enabling distributed nodes to agree on the blockchain’s state.
In PoS, validators (stakers) propose and verify new blocks by staking a minimum amount of tokens, such as 32 $ETH in the case of Ethereum. Consensus is achieved when at least 66% of nodes agree. Validators are then rewarded for honest behavior (positive incentive), while dishonest actions are penalized through slashing, where a portion of their staked assets is forfeited (negative incentive). This system of incentives creates strong economic security, aligning validators’ financial interests with the network’s integrity.
The key difference between PoW and PoS lies in their incentive models. PoW relies on positive incentives, rewarding miners for block creation without penalties for malicious actions. PoS, on the other hand, combines rewards with penalties (i.e. both positive and negative incentives), incentivizing both honest behavior and discouraging malicious actions. In PoS, validators risk losing their stake, which increases security. As more tokens are staked, attacking the network becomes increasingly expensive, making it more secure. Ethereum’s network security depends not only on both the amount of staked $ETH and its value, but also on the decentralization of its validator set, economic finality, security, community and network effects, etc.
Crypto Economic Security (CES) in PoS Blockchains
Crypto Economic Security (CES) is a useful framework for assessing the security of PoS blockchains. It operates under the assumption that a group of colluding validators, referred to as the attacker, could potentially corrupt the majority of the network’s validators. With this control, the attacker could manipulate the consensus process, leading to issues like double-spending, transaction censorship, or compromising the integrity of the blockchain’s state.
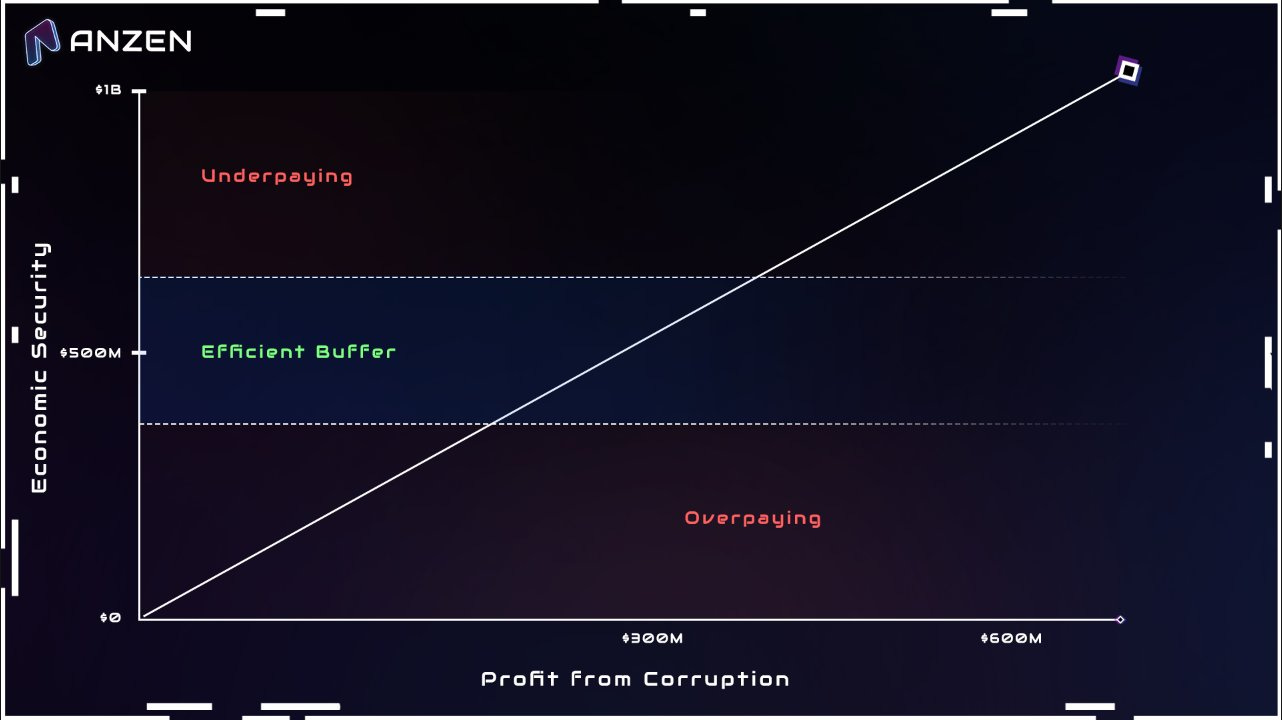
The CES framework focuses on two key metrics: Cost of Corruption (CoC) and Profit from Corruption (PfC). CoC refers to the minimum cost or loss an attacker must incur to successfully breach the system. PfC represents the maximum profit an attacker can gain from a successful attack. A system is considered economically secure if the CoC is greater than PfC, meaning that it is more expensive to corrupt the system than the potential gains from doing so. Given that these metrics can be volatile and shift quickly, protocols may want to establish a buffer where the CoC is intentionally set higher than the PfC by a specific margin. This to ensure that, even in the event of sudden fluctuations in either CoC or PfC, the CoC is likely to stay above the PfC. This approach is similar to the concept of over-collateralization in DeFi.
Figure 2: Economic security buffer
Source: Anzen Protocol Blog
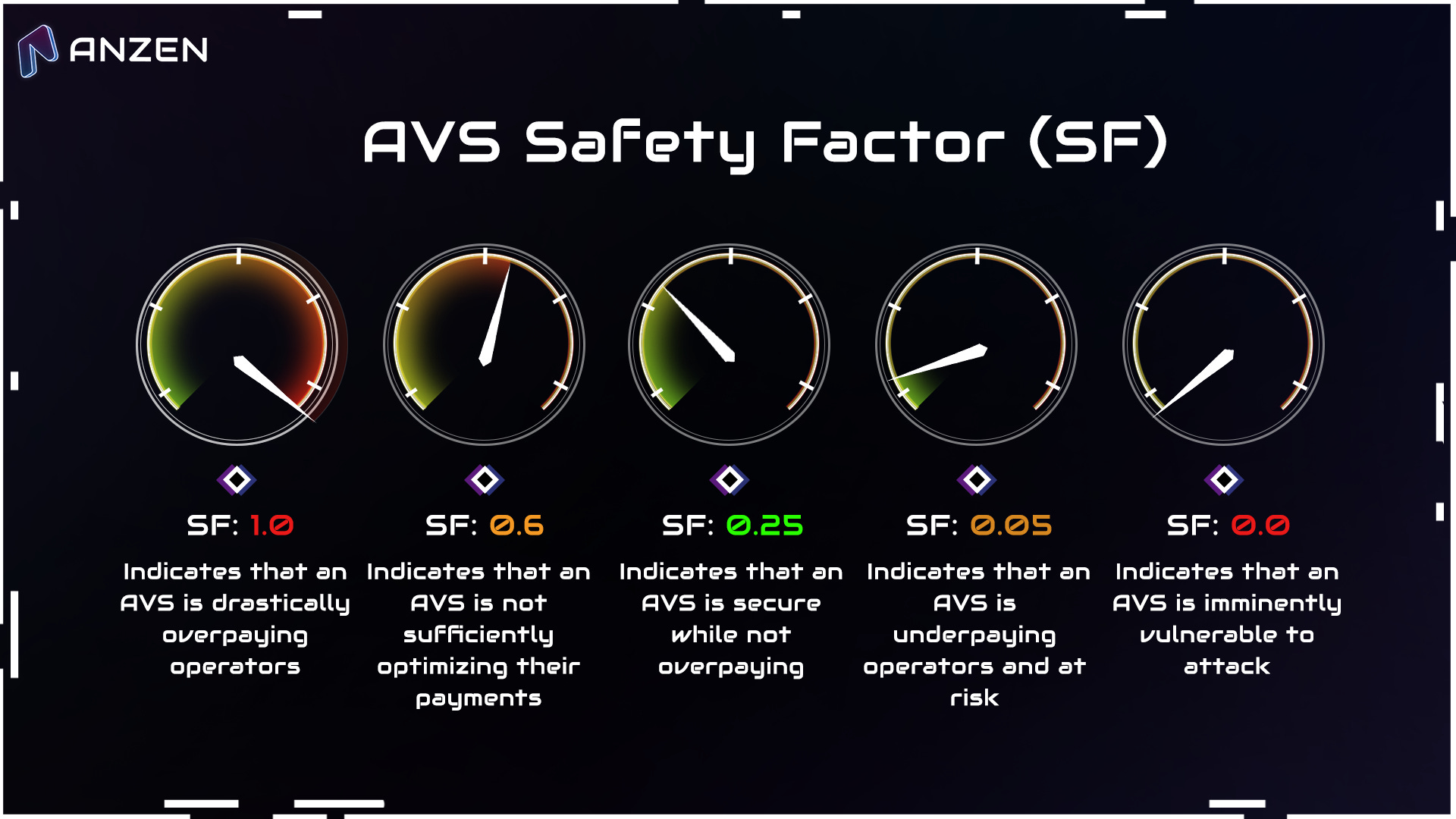
Anzen Protocol introduced the concept of Safety Factor (SF) as a universal metric to evaluate the economic security of AVS, similar to how health factors are commonly applied across DeFi. The SF is derived from the CoC and the PfC.
When the SF is below 0, it means that a protocol is vulnerable to economic exploitation. When the SF approaches 1, it means that an AVS is overpaying for economic security. Anzen protocol expects the typical SF to trend near a target buffer above 0 to avoid being too close to an economic exploit.
Figure 3: Safety Factor
Source: Anzen Protocol Blog
As a PoS blockchain mechanism designer, the aim is to maximize the CoC while minimizing PfC. PoS chains like Ethereum have increased CoC by integrating slashing mechanisms, which economically penalize misbehaving validators by confiscating part or all of their staked tokens. Slashing targets specific validators without negatively affecting others who follow the rules. This feature is unique to PoS because it requires the blockchain to enforce penalties, a capability that PoW blockchains lack.
Lowering PfC is a more nuanced challenge. It involves identifying transactions that adversaries could exploit to extract value from the blockchain, particularly those that rely on subsequent off-chain actions, such as transactions involving CEXs or bridges. If adversaries confirm such transactions prematurely, they could create confusion by double-signing and generating a separate, finalized fork, even at the risk of being slashed. To reduce the potential profits from corruption, it’s essential to develop more robust confirmation rules for when these types of transactions should be considered safe for execution.
Establishing an Economic Security Model is Expensive
Developers building smart contract protocols like DEXs or lending platforms on Ethereum can take advantage of Ethereum’s strong trust network by deploying their contracts on the platform. While Ethereum offers solid economic security for these smart contract protocols, it doesn’t extend the same level of security to decentralized infrastructure or distributed systems that need their own consensus, such as bridges, keeper networks, oracle networks, rollup sequencers, data availability layers, and co-processors.
Modules that cannot be deployed as smart contracts or validated directly on-chain don’t benefit from Ethereum’s pooled trust. These modules often handle inputs from outside Ethereum, making in-protocol validation impossible. As a result, developers face the challenge of creating their own economic security model. This typically involves launching a native token, which introduces risks like the cold-start problem—where a drop in the token’s value can weaken the network’s security.
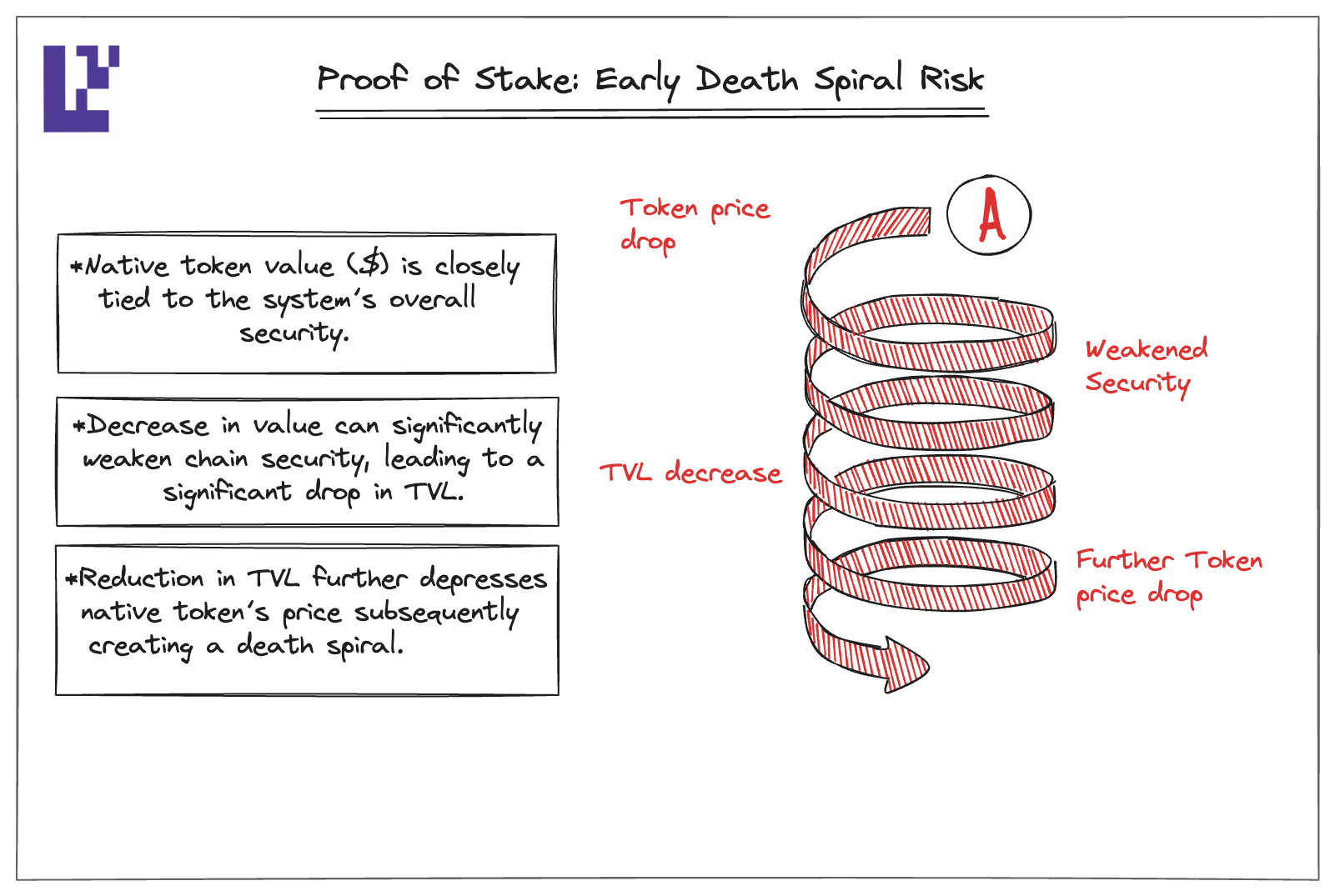
For example, a native token in its early stages is especially susceptible to a “death spiral”. A decline in the token’s value weakens the network’s security, potentially leading to a reduction in TVL. This, in turn, causes further drops in the token’s price, perpetuating the downward cycle and compromising the application’s economic security even more.
Figure 4: The early death spiral risk
Source: EigenLayer Blog
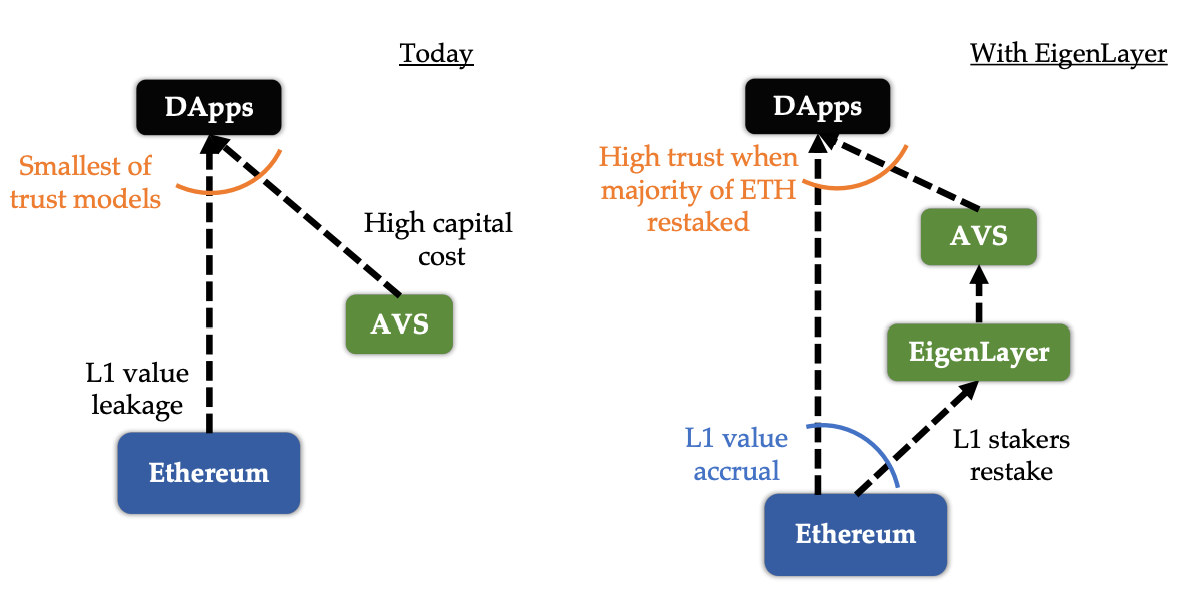
As a result, teams working on infrastructure or off-chain systems external to a primary blockchain face several challenges: (1) bootstrapping and maintaining a new distributed validator set, (2) managing capital costs and mitigating value leakage, (3) dealing with yield opportunity costs, and (4) operating with a lower trust model for dApps operating on top.
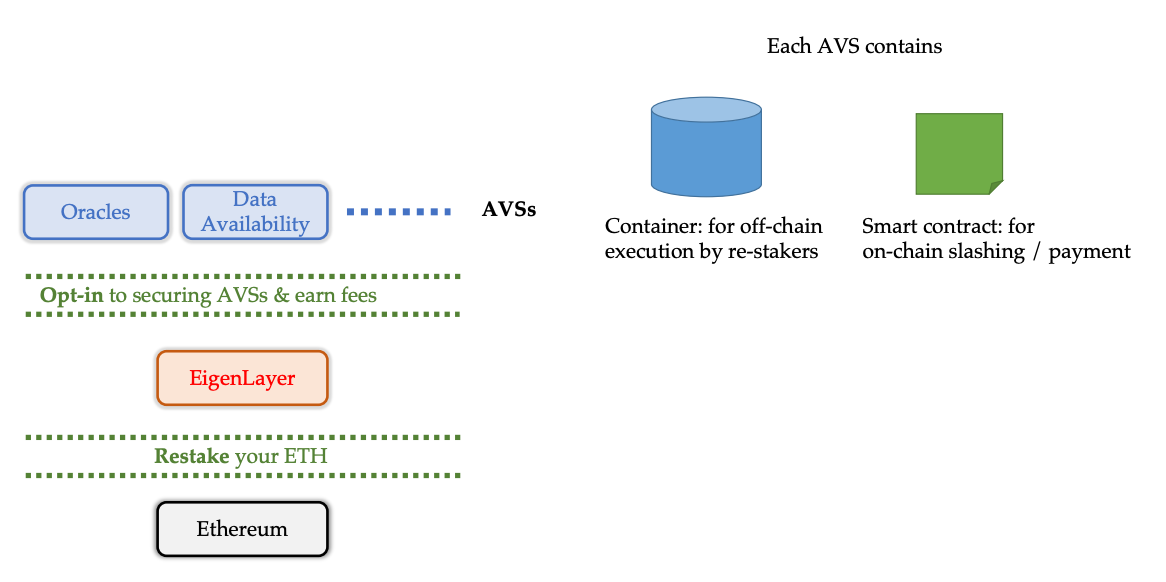
Restaking: Bootstrapping Economic Security
Restaking aims to address the challenges faced by new protocols that require consensus, by lowering the barriers to entry—it doesn’t fundamentally enable new use cases but rather increases competition by enabling permissionless innovation with lower entry costs. In traditional PoS systems, validators stake assets to secure the network. Restaking takes this concept to the next level by allowing the same staked capital to secure additional services. This eliminates the need for new protocols to issue a native token and build security from scratch, instead enabling them to leverage an existing validator set and pool of assets.
With restaking, infrastructure developers no longer need to struggle to recruit and incentivize node operators. They can simply tap into the existing network of validators with capital already staked. This contrasts with the effort of launching a new token with no liquidity and growing it into a large market cap asset—all of this after recruiting a distributed validator set and making sure that they will be committed to operating the network over the long run, for which there needs to be a strong incentive.
Figure 5: A new primitive: restaking
Source: EigenLayer Whitepaper.
While not fundamentally unlocking unique use cases that weren’t possible before, restaking has the potential to greatly extend the scope of blockchain applications that can benefit from pooled security. This includes not only Ethereum-based smart contract dApps but also virtual machines, consensus protocols, and middleware solutions such as oracles, bridges, L2 sequencers, and data availability layers.
The Restaking Wars
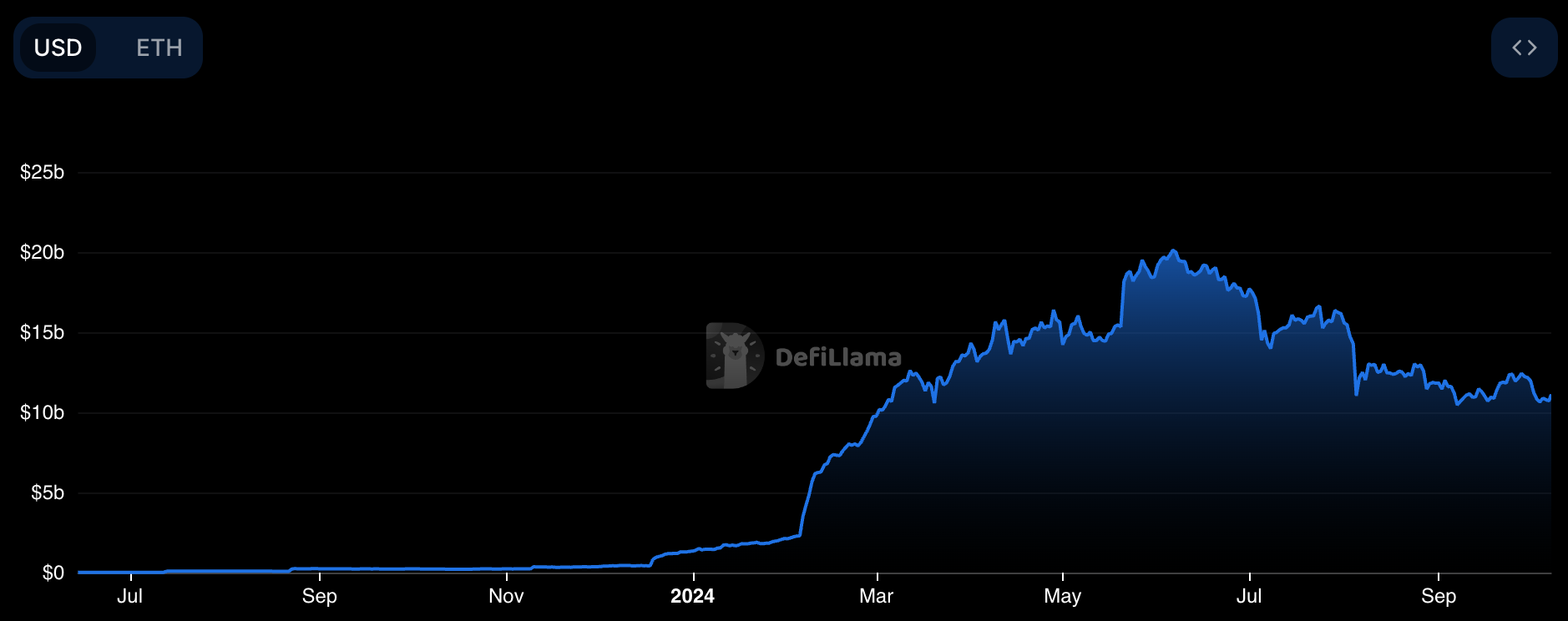
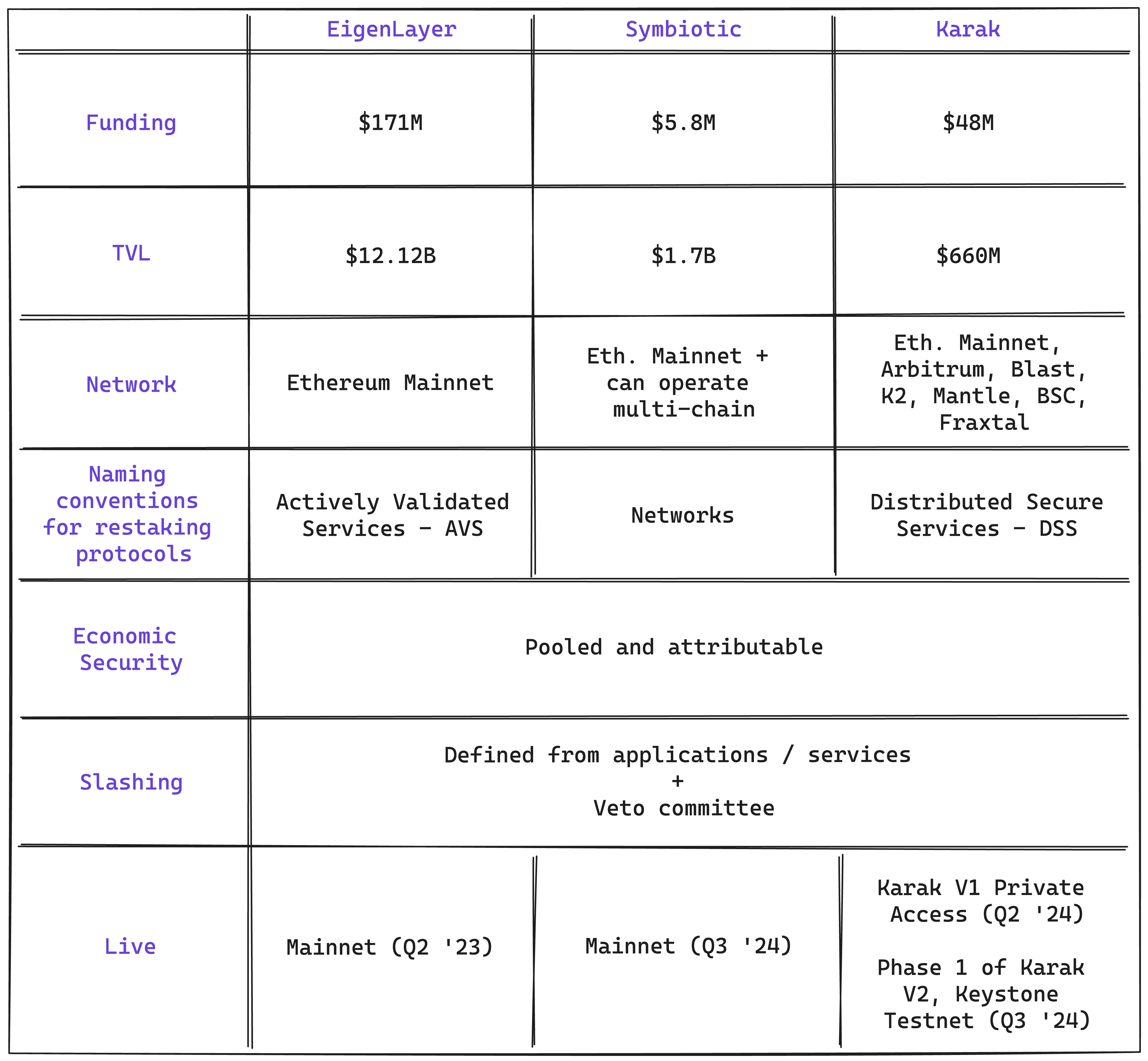
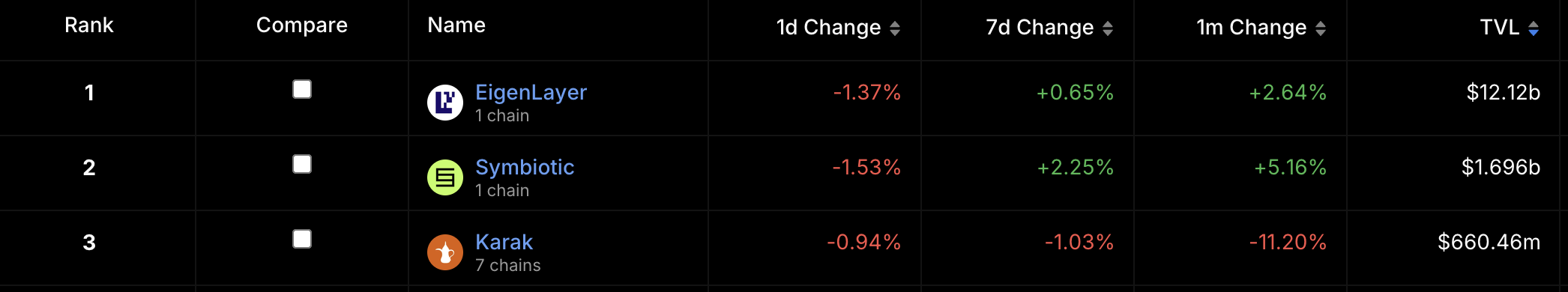
EigenLayer was the first protocol to introduce the concept of restaking. According to tracxn, EigenLayer has raised $171M across three funding rounds, with the most recent Series B in February 2024, led by Andreessen Horowitz (a16z) for $100M. Launched on Ethereum mainnet in June 2023, EigenLayer currently dominates the space with a total value locked (TVL) of $12.12B. However, it didn’t take long for competitors to emerge, with Symbiotic and Karak now being its main rivals. EigenLayer, as the first mover, remains the leader among the three protocols. A key indicator of this leadership is the launch of its native token, $EIGEN, which sets it apart. Announced in April 2024, $EIGEN was initially non-transferable, a decision made by the Eigen Foundation to support long-term adoption of both the token and the protocol. Following this initial phase, $EIGEN became transferable on October 1, and is now trading with a market cap of $700M.
Figure 6: EigenLayer TVL
Source: DefiLlama
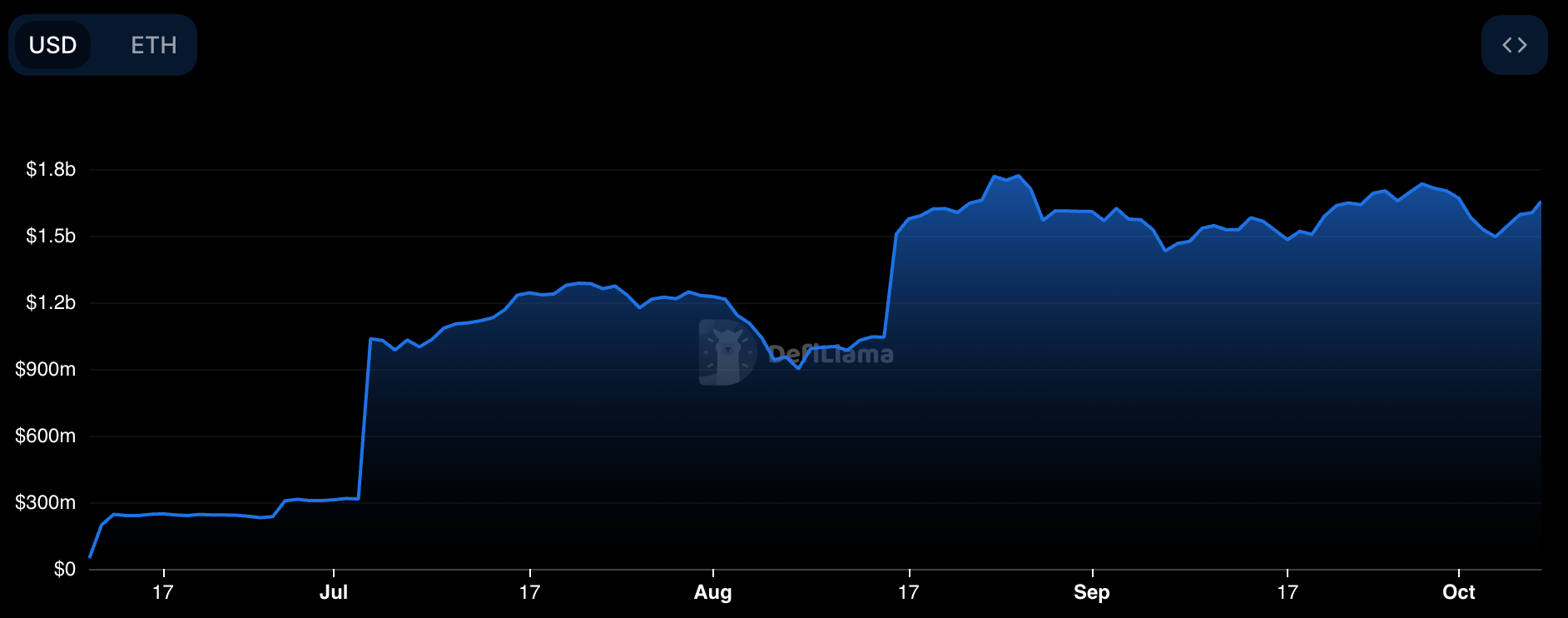
In response to a16z’s investment in EigenLayer, Paradigm backed Symbiotic, positioning it as a direct competitor. In June 2024, Symbiotic secured $5.8M in seed funding from Paradigm and CyberFund–it’s worth noting that Cyber Fund was founded by Lido co-founders Lomashuk and Shapovalov. Symbiotic value proposition lies in its permissionless, modular design, offering greater flexibility and control. Since its launch in June 2024, Symbiotic has achieved a total value locked (TVL) of $1.7B.
Figure 7: Symbiotic TVL
Source: DefiLlama
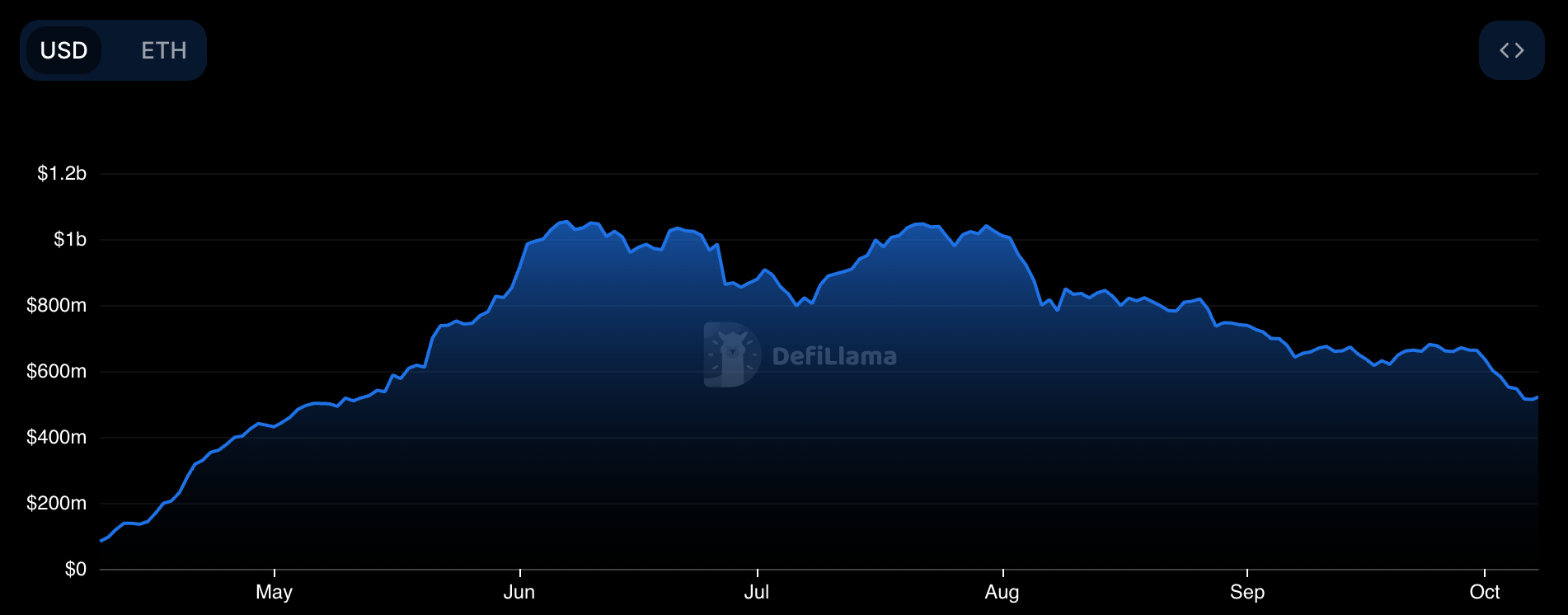
Karak, meanwhile, raised over $48M in a Series A round at a $1B valuation, led by Lightspeed Venture Partners. Other investors include Pantera Capital, Framework Ventures, Bain Capital Ventures, Digital Currency Group, Coinbase, Proof Group, Nima Capital, and Naval Ravikant. Its current TVL stands at $660M.
Figure 8: Karak TVL
Source: DefiLlama
EigenLayer and Symbiotic are both exclusively restaking on Ethereum mainnet, though Symbiotic may eventually expand to other chains. Karak, in contrast, operates across multiple networks, including Mainnet, Arbitrum, Blast, K2 (a Karak-specific L2), Mantle, BSC, and Fraxtal.
Despite their differences in architecture, features, and strategies, these protocols share the common goal of enabling a marketplace for decentralized trust. This is achieved by (1) connecting stakers and infrastructure developers through a unified platform, (2) enabling stakers to provide economic security for new services or applications in exchange for additional rewards, and (3) enhancing security through restaking, rather than fragmenting it.
Figure 9: Restaking Wars: EigenLayer, Symbiotic, and Karak
Source: EigenLayer, Symbiotic, Karak Documentations, Revelo Intel
In this section, we will explore the key aspects of restaking marketplace protocols, including the actors involved, the various types of economic security they enable, the different forms of collateral that have been adopted over time, and the key mechanism used to maintain protocol security, such as slashing. Finally, we will compare the three protocols under some key metrics.
Main Actors and Roles
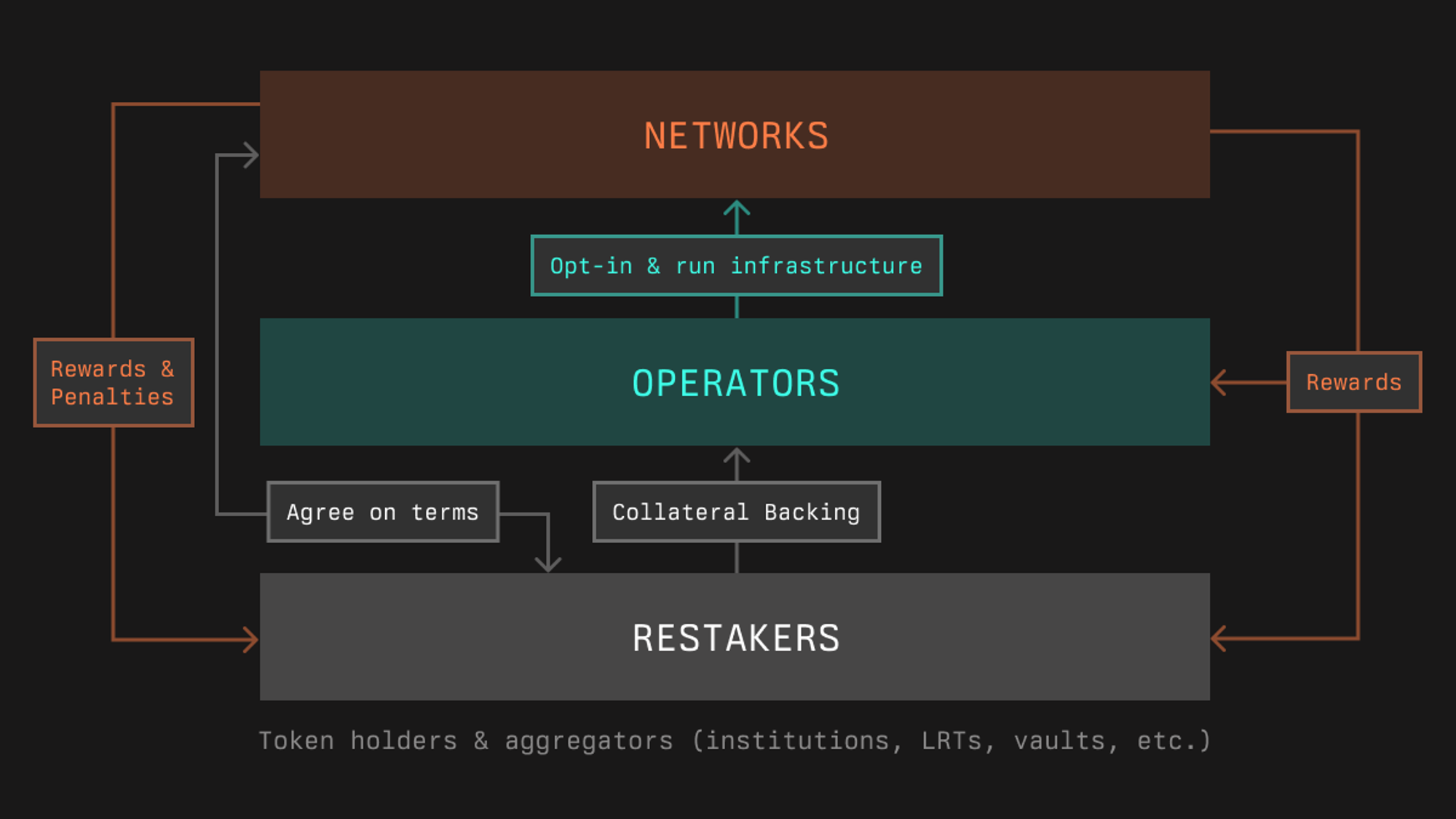
Each restaking protocol uses different labels for the key participants in their ecosystems, but the three primary actors are: (1) restakers, (2) node operators, and (3) services/applications that need to bootstrap economic security.
The drivers and incentives for each participant in restaking are straightforward. Applications are primarily motivated by the ability to rent economic security, allowing them to accelerate their go-to-market strategy. Stakers, on the other hand, are incentivized by the opportunity to earn additional rewards beyond what they receive from standard staking. Node operators facilitate this process by allowing restakers to delegate their stakes to them. These operators opt in to secure various services on the restaking protocol by running off-chain software specific to those services, earning rewards in return for providing the necessary infrastructure.
Thus, applications contribute value to users and the broader Web3 ecosystem, while node operators ensure the security and integrity of these applications by using restakers’ assets. Restakers and operators earn additional revenue by providing security and validation to the applications, which establish their own rules and slashing mechanisms to maintain security and pay fees for these services.
However, as we will explore later, these additional rewards for restakers and operators come with risks that must be carefully considered.
Economic Security Models
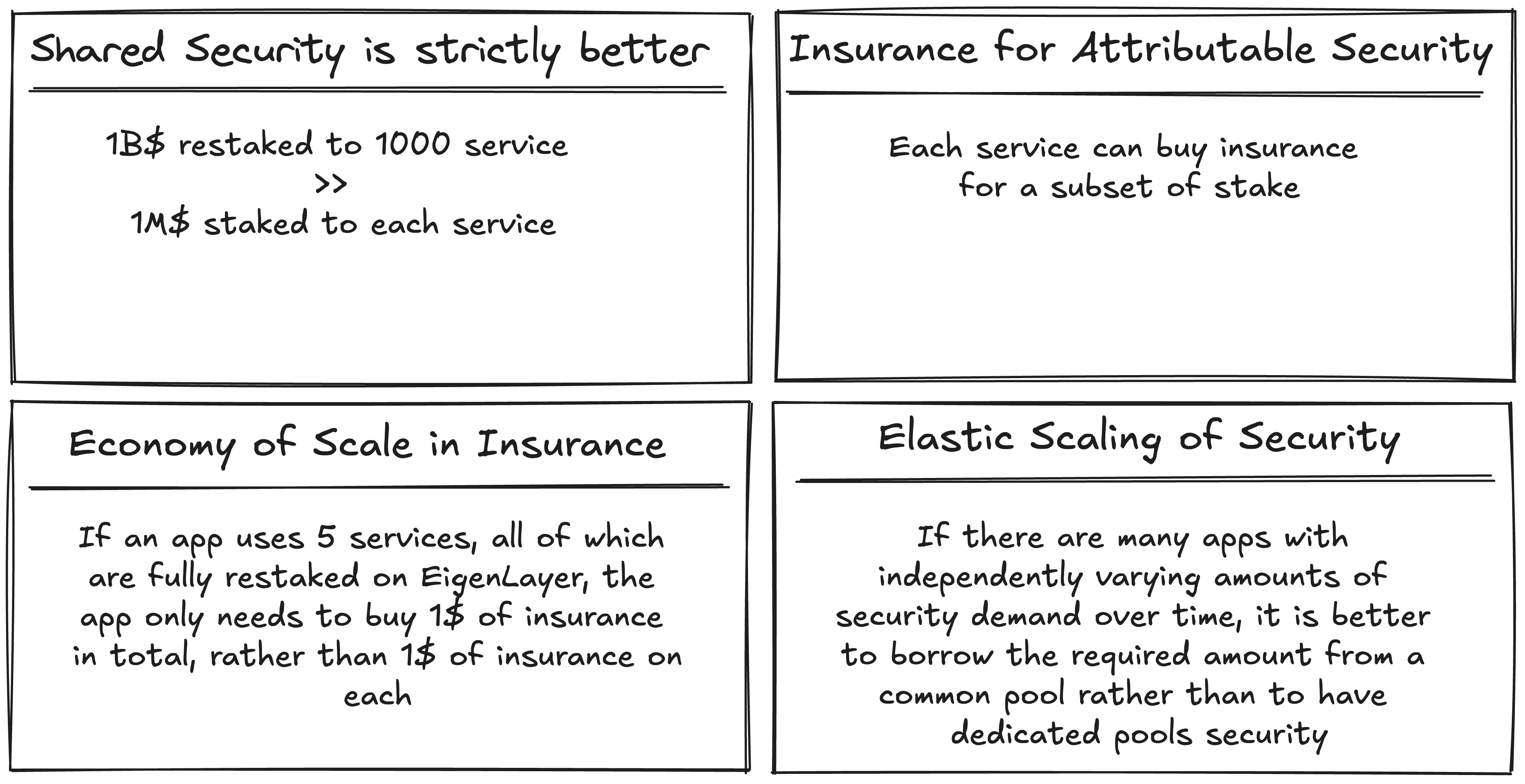
Restaking offers two primary models for achieving economic security: (1) pooled security and (2) attributable security. In the pooled security model, operators restake their assets (e.g., $ETH-backed collateral) across multiple applications simultaneously. If slashed by an application, their funds are burned. In contrast, the attributable security model requires operators to commit a specific amount of value to secure only one application. If slashed, the funds are returned to the application rather than burned.
Pooled security is capital-efficient, enabling applications to access large pools of capital at lower costs. Operators can also earn yields from multiple applications with minimal additional capital. However, this model provides fewer assurances to applications, as an operator’s funds are at risk of being slashed by other applications. In this shared security model, if $10 billion is restaked across 1,000 services, an attacker would need to control a majority of that $10 billion to compromise any single service. While economically efficient, it carries the trade-off of lower security assurances due to potential simultaneous slashing by multiple applications.
Attributable security, on the other hand, offers higher assurances for applications by isolating risk. Operators commit to a single application, and slashing events are specific to that application, reducing the chance of being penalized for the actions of others. This model provides stronger economic guarantees, as applications can recover funds in case of malicious behavior rather than merely penalizing the attacker. It also simplifies risk management for applications by eliminating the complexity of rehypothecation across multiple services, making it easier to calculate the CoC and improving solvency.
However, attributable security demands more diligence from operators, as they must trust the integrity of the application they secure. A malicious application could falsely trigger slashing to steal the operator’s capital. Additionally, attributable security incurs higher costs for applications due to its more focused approach.
Figure 10: Benefits of pooled and attributable security
Source: EigenLayer Presentation
The key difference between pooled and attributable security lies in the allocation and management of risk. Pooled security maximizes capital efficiency and potential returns by spreading risk across multiple applications, but it introduces systemic risk and requires more complex modeling. Attributable security, while costlier and requiring greater diligence, offers clearer, more predictable guarantees, making it appealing for applications that prioritize minimizing risk and ensuring protocol solvency.
EigenLayer, originally launched with pooled security as its only option, recently expanded its model to include attributable security. According to EigenLayer, this update brings several benefits: (1) greater control over slashing risk, as slashing is isolated to individual applications and operators can limit how much stake any one application can slash; (2) guaranteed slashable stake, since each application knows exactly how much stake is allocated to it; (3) no need for a common veto committee, as each application can define its own slashing and governance mechanisms; and (4) permissionless onboarding of applications, allowing operators to opt in based on their preferences.
Meanwhile, Symbiotic and Karak have been designed since the beginning with more flexible, modular architectures. They allow applications and services to control all aspects of their restaking implementation, enabling participants to opt in and out of shared security arrangements based on their needs. This adaptability gives them the freedom to tailor their security settings to suit specific use cases.
In Symbiotic, applications and services, referred to as Networks, have the flexibility to select their collateral assets, node operators, rewards, and slashing mechanisms. Symbiotic core contracts are non-upgradeable, which helps minimize governance risks and reduces potential points of failure. Furthermore, Symbiotic permissionless design enables any decentralized application to integrate without needing approval. This modular approach allows any network to tap into shared security, providing a flexible and open framework for securing decentralized services.
Figure 11: Symbiotic shared security protocol
Source: Symbiotic Documentation
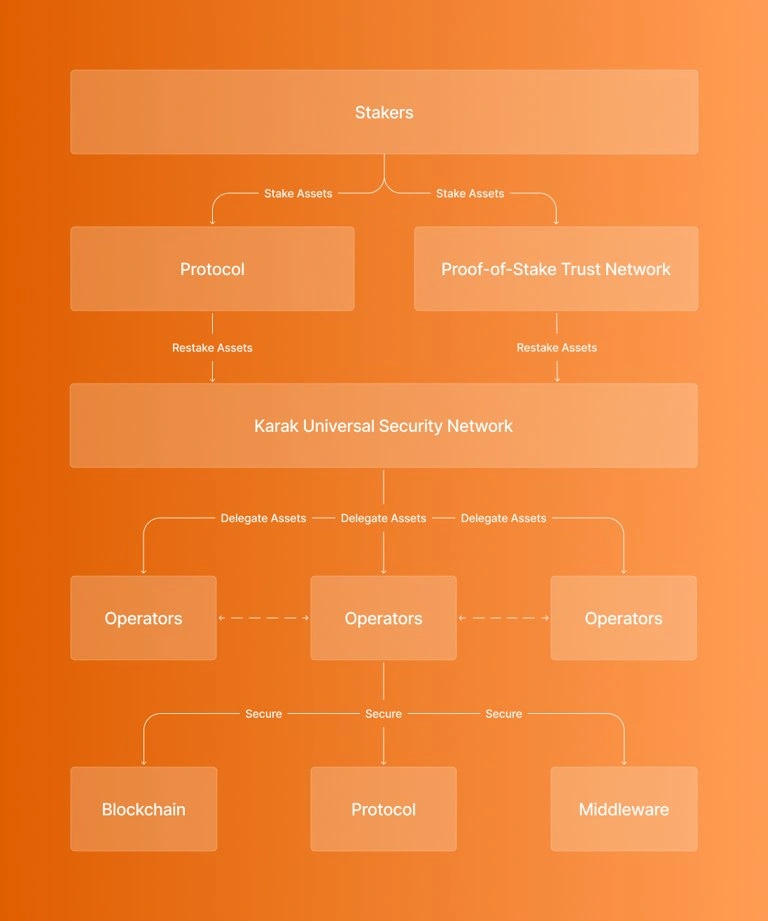
Similar to Symbiotic, Karak operates as a marketplace where developers can incentivize operators to allocate their restaked assets to secure their applications and services. This represents a major improvement over traditional methods where applications often issue highly inflationary tokens as rewards for validators and build a new trust network from scratch. With Karak, developers can attract validators by offering simple, non-dilutive incentives, which significantly reduces both the financial and time investment compared to creating a new trust network.
Figure 12: Karak universal restaking layer
Source: Karak Documentation
Karak’s universal restaking approach also enhances bootstrapping and composability across various networks. By introducing a multi-asset restaking model, Karak helps standardize capital requirements despite the differing staking parameters of individual blockchains, making it easier for projects to tap into shared security resources across ecosystems. Multi-asset restaking offers several benefits. First, it enables users to earn additional rewards by staking a diverse range of assets, thus higher overall returns as users can leverage different staking protocols and yield strategies. Second, it increases security by distributing economic backing across multiple assets, reducing the risk of relying on a single asset–and avoiding a single point of failure. Third, it offers greater flexibility and liquidity benefits, as multi-asset restaking allows users to optimize their staking strategies based on market conditions and personal preferences.
Collateral Types
Initially, restaking was focused solely on extending Ethereum’s economic security, but this is no longer the case. Today’s landscape has evolved to support both $ETH-backed collateral (native $ETH and liquid staking tokens, or LSTs) and non-$ETH-backed collateral for securing applications and services.
EigenLayer, as the first mover in the restaking space, has responded to shifts in the competitive landscape by announcing permissionless token support. This new feature allows any ERC-20 token to be permissionlessly added as a restakable asset, significantly expanding the range of assets that can contribute to decentralized network security. With this update, AVSs – application and services in EigenLayer – can now accept any ERC-20 token as a restaked asset to secure their services. This flexibility enables AVSs to evaluate the supply and utility of various tokens, and create cross-ecosystem partnerships while maintaining strong security standards.
The categories of potential ERC-20 assets include, but are not limited to, native AVS tokens, stablecoins, and BTC-denominated tokens. AVSs can fully customize their crypto economic security profiles, allowing them to use their native tokens to unlock new utility, including improved security functionality and the ability to reward restakers and operators.
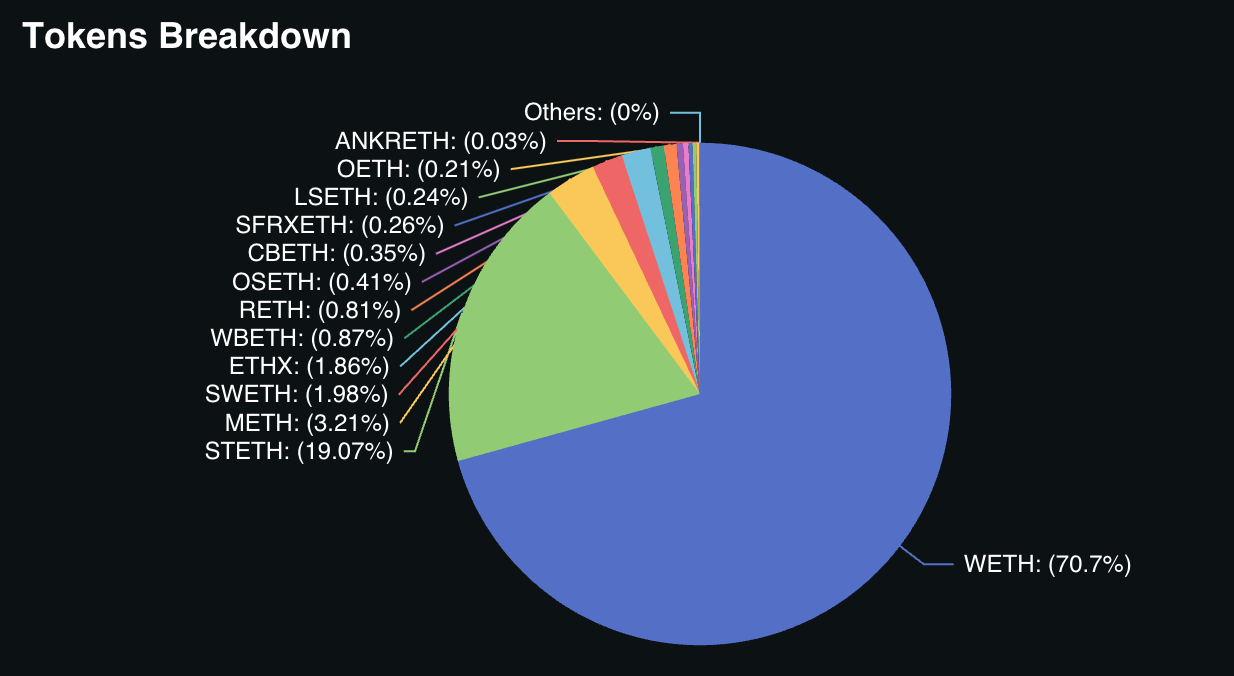
Figure 13: EigenLayer: Restaked tokens breakdown
Source: DefiLlama
Unlike EigenLayer, Symbiotic was designed from the outset with multi-asset support, allowing for direct deposits of any ERC-20 token. In Symbiotic, collateral is an abstraction that represents underlying on-chain assets, which are both chain- and asset-agnostic. This means it can include ERC-20 tokens, Ethereum validator withdrawal credentials, or other on-chain assets like LP positions, without restrictions on which blockchains these assets are held on.
In practice, this allows crypto protocols to implement native staking for their own tokens to enhance network security. For instance, Ethena partnered with Symbiotic to provide cross-chain security for USDe using staked $ENA.
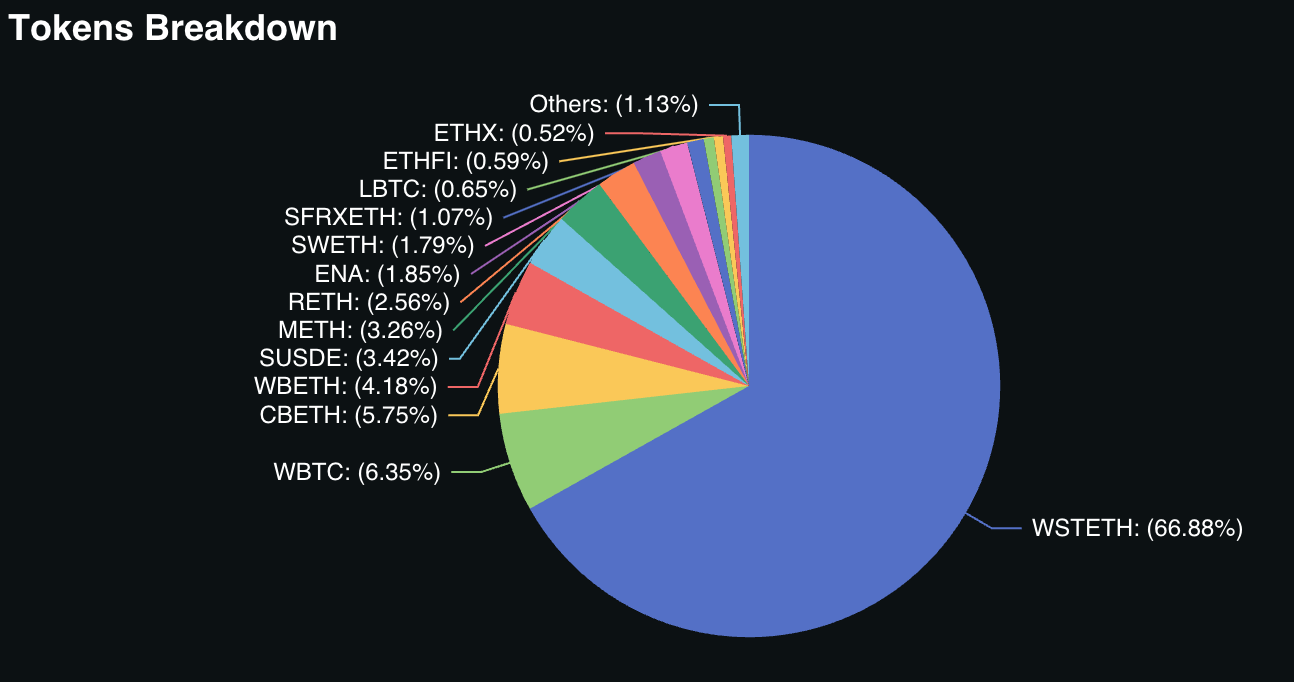
Figure 14: Symbiotic: Restaked tokens breakdown
Source: DefiLlama
Karak’s value proposition, much like Symbiotic’s, is to offer economic security using a variety of assets beyond $ETH. The key advantage here is that many assets have lower opportunity costs compared to $ETH, giving Distributed Secure Services (DSS)—the applications and services looking for economic security—a more viable path to sustainable yields. In an $ETH-only environment, DSSs must compete with all other $ETH yield opportunities while presenting a new risk profile. Karak, however, enables users to repurpose their staked assets to extend the security of Ethereum and other trust networks to additional applications.
While Karak supports restaking stablecoins, LSTs, and $ETH, it also strategically allows restaking of LRTs that have already been restaked on EigenLayer. This allows users to earn rewards from LRTs, EigenLayer, and Karak simultaneously, offering farmers the ability to maximize their returns by stacking rewards across multiple protocols.
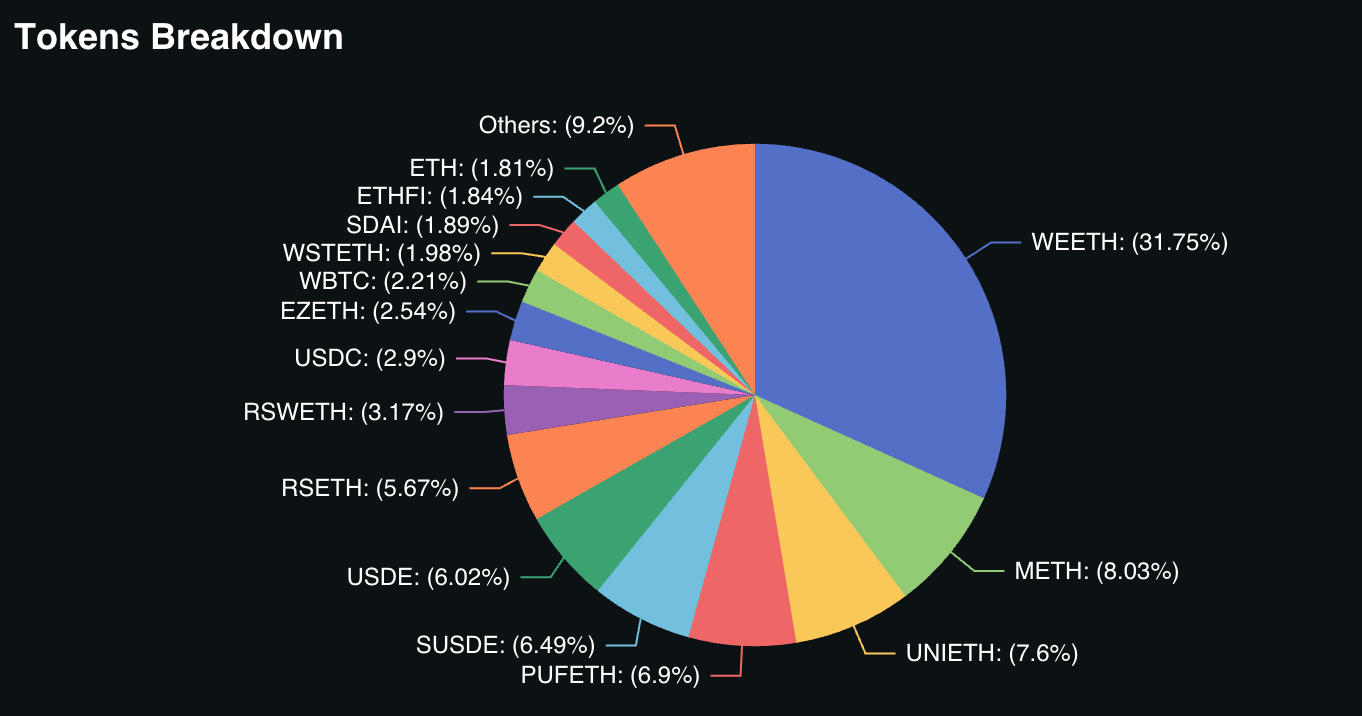
Figure 15: Karak: Restaked tokens breakdown
Source: DefiLlama
Slashing
Validating the operations of a service is not without risks. The crypto economic security of a service secured via restaking relies on detecting and penalizing (slashing) malicious actions, which acts as a deterrent. For example, in PoS chains like Ethereum, validators are penalized for misconduct, with penalties ranging from minor (e.g., missed votes) to severe (e.g., prolonged inactivity or equivocation). Restaking protocols apply similar penalties to operators to maintain service reliability and discourage malicious behavior. Restakers must trust their chosen operators for both honesty (avoiding slashing offenses) and competence (avoiding penalties for inactivity), akin to how individuals select staking services on Ethereum. However, operators vary in the types of services they validate, and each service comes with its own level of risk. As with yield, risk accumulates, making it critical to choose the right operators to minimize exposure. A key benefit of slashing is that it significantly raises the CoC for any potential adversary.
In EigenLayer, launching an AVS involves deploying an off-chain container that operators download and run, along with an on-chain contract that defines the slashing and payment terms. AVSs establish their own rules and slashing mechanisms through an interface called the Slasher Manager, ensuring security and defining fees for the services provided. For example, in a Data Availability module, restakers in EigenLayer are compensated whenever data is stored. In exchange, they are subject to slashing conditions enforced through proof-of-custody mechanisms, ensuring that restakers maintain the integrity of the service they are securing.
Figure 16: Launching an AVS on top of EigenLayer
Source: EigenLayer Whitepaper.
However, operators depend on AVS developers to accurately code both the client software and the on-chain slashing conditions. If there are bugs or issues in the AVS software, operators face the risk of missing potential fee payments or, in the worst case, being slashed for their entire stake. Recognizing the significant value at risk, EigenLayer introduced safeguards before full implementation. A key safeguard is the veto committee, a trusted entity agreed upon by restakers, operators, and AVS developers. This committee has the authority to reverse slashing that occurs due to non-malicious behavior, removing the sole reliance on AVS developers and ensuring operators and restakers are not unjustly penalized due to software bugs.
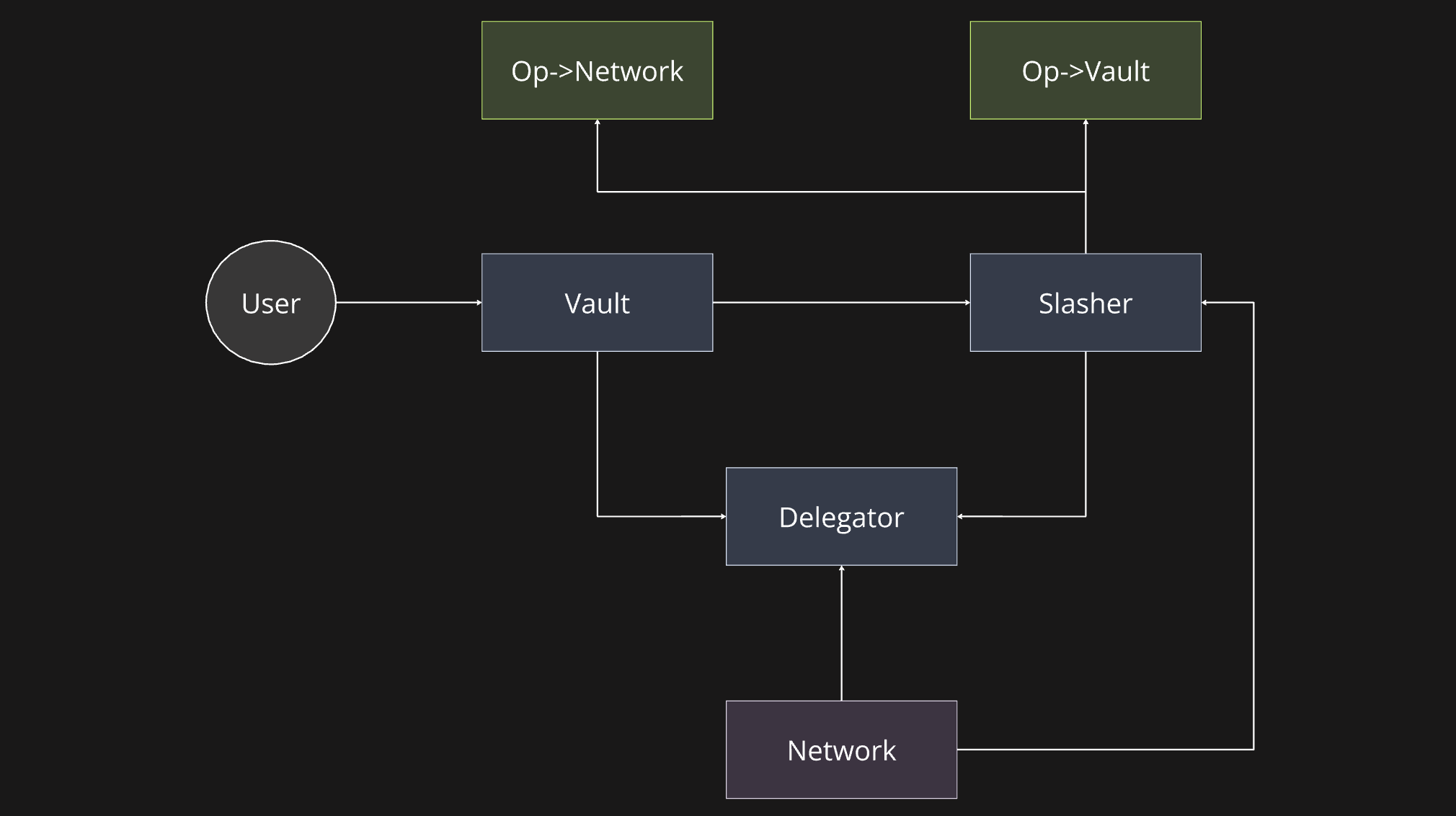
In Symbiotic, slashing logic is managed through the optional Slasher module, which includes two types of slashing: instant and veto-slashing. Instant slashing is executed immediately upon receiving a valid request. The system validates slashing requirements by ensuring the operator is opted into the vault—the delegation and restaking management layer of Symbiotic—and is actively interacting with the Network. If these conditions are met, the operator is recognized as a participant in the network, and slashing can proceed. This process ensures that only operators who have opted in and are engaged with the network can be penalized, reducing the risk of unjust slashing.
Figure 17: Symbiotic: the Slasher module
Source: Symbiotic Documentation
On the other hand, veto-slashing in Symbiotic is handled through the use of Resolvers. Resolvers are contracts or entities that have the authority to veto slashing incidents forwarded by networks, and they can be shared across multiple networks. The use of Resolvers is determined by terms set by the networks and accepted by vaults providing collateral to operators. A vault can assign multiple Resolvers—or none at all—to cover different portions of its collateral. For example, 10% of collateral might have no resolver, while 40% is covered by Resolver A and 50% by Resolver B. These Resolvers, such as committees, might oversee specific networks. Decentralized dispute resolution frameworks like UMA, Kleros, or reality.eth can also act as Resolvers, adding flexibility to the slashing process.
Moreover, it’s possible to require a quorum of Resolvers to approve or veto a slashing incident, providing additional security guarantees for participants in the Symbiotic protocol. This multi-resolver and quorum system enhances the overall reliability of the protocol and ensures that slashing incidents are thoroughly evaluated, reducing the risk of unjust penalties.
Figure 18: Symbiotic: Resolvers’ architecture
Source: Symbiotic Documentation
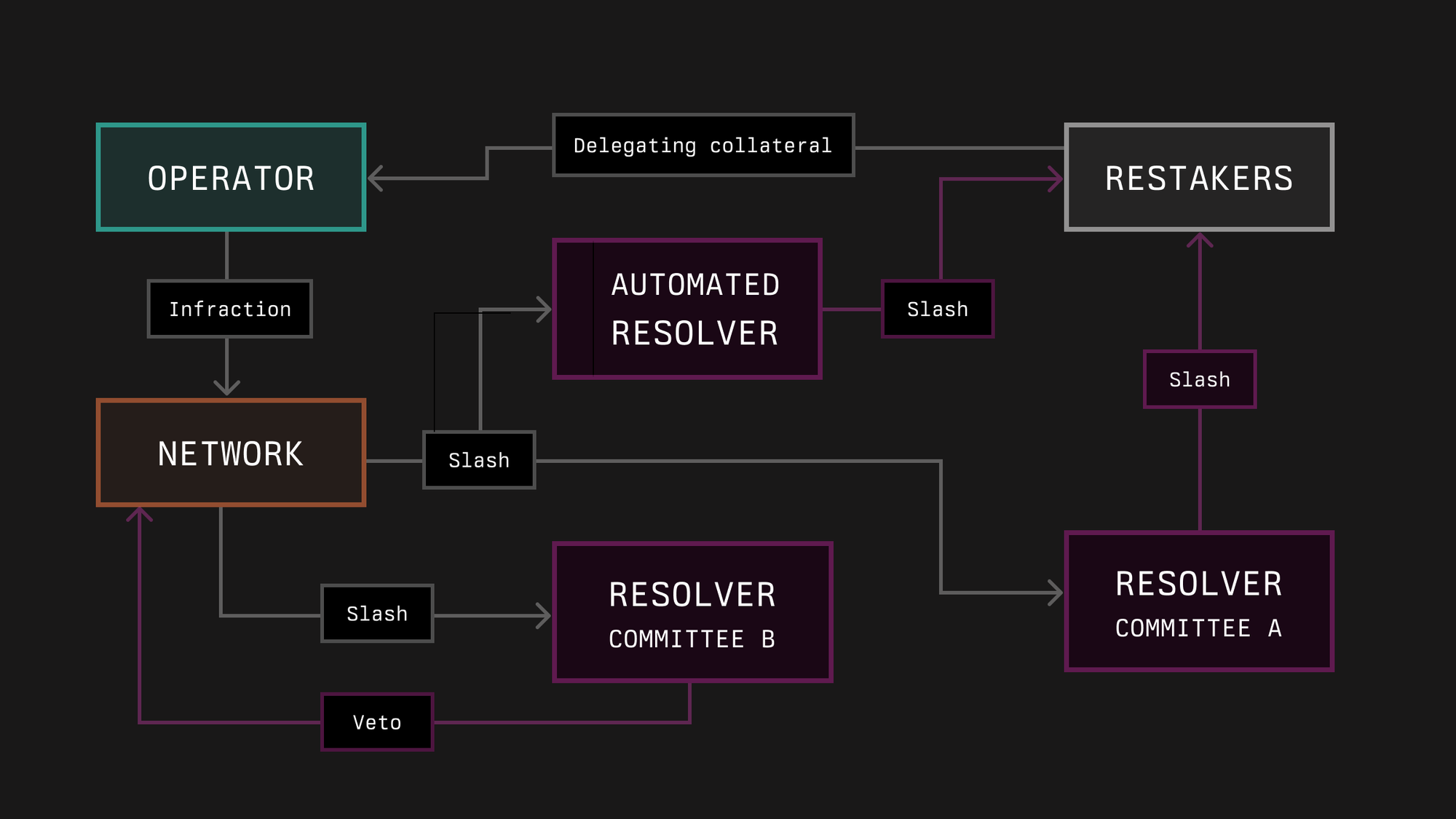
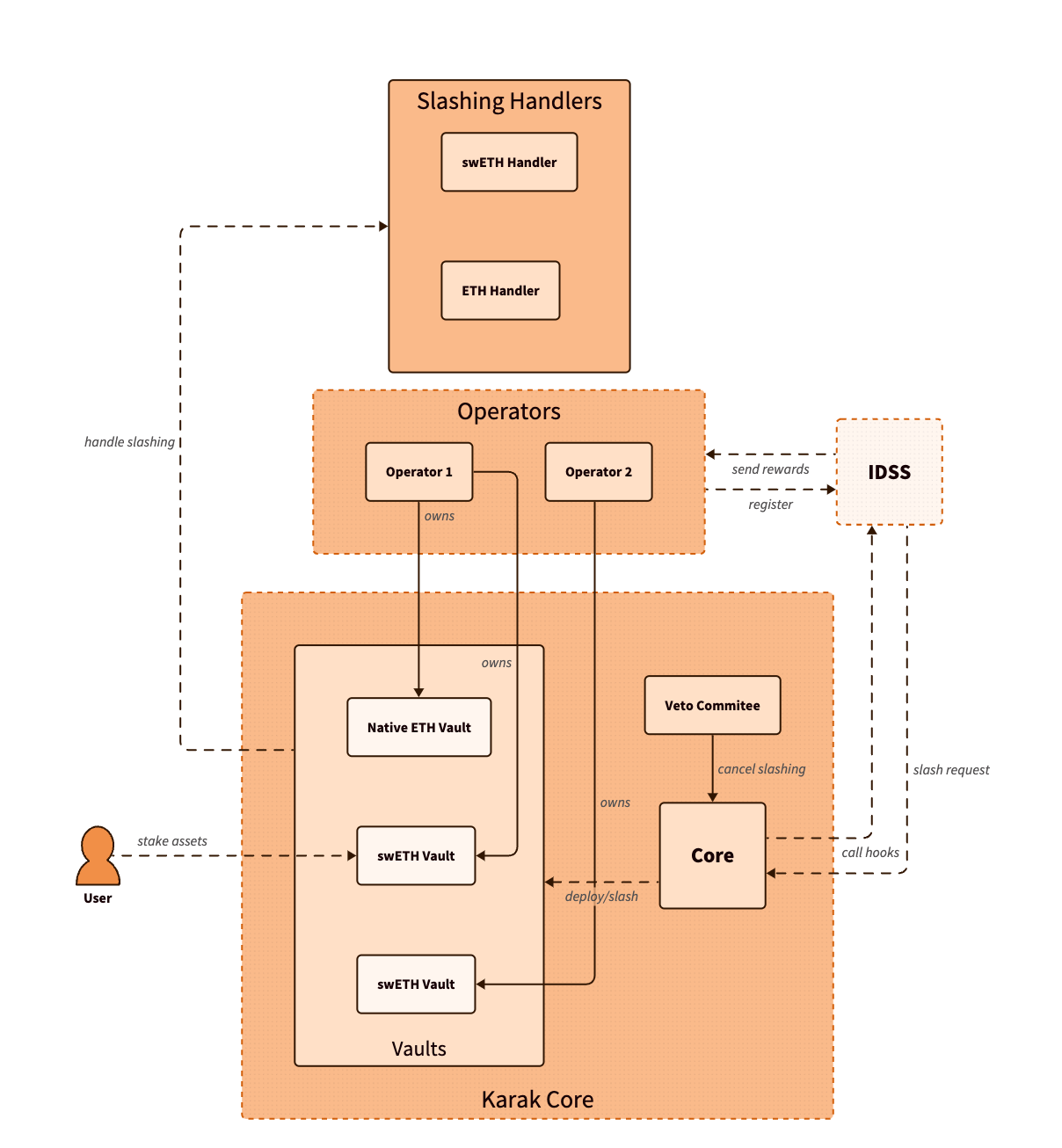
In Karak, Distributed Secure Services (DSSs), or applications, have the authority to slash vaults staked to them if they believe an operator has failed to perform its duties properly. To prevent unjust slashing, a veto committee can intervene if they determine the slashing was unfair, giving them the power to veto the slashing event. DSSs must set a maximum slashable percentage, which can only be configured once. They are entitled to slash the vaults staked by operators but are subject to a cooldown period of two days after each slashing request per operator, providing a buffer to prevent excessive or hasty slashing actions.
Figure 19: Karak: protocol architecture
Source: Karak Documentation
Key Metrics
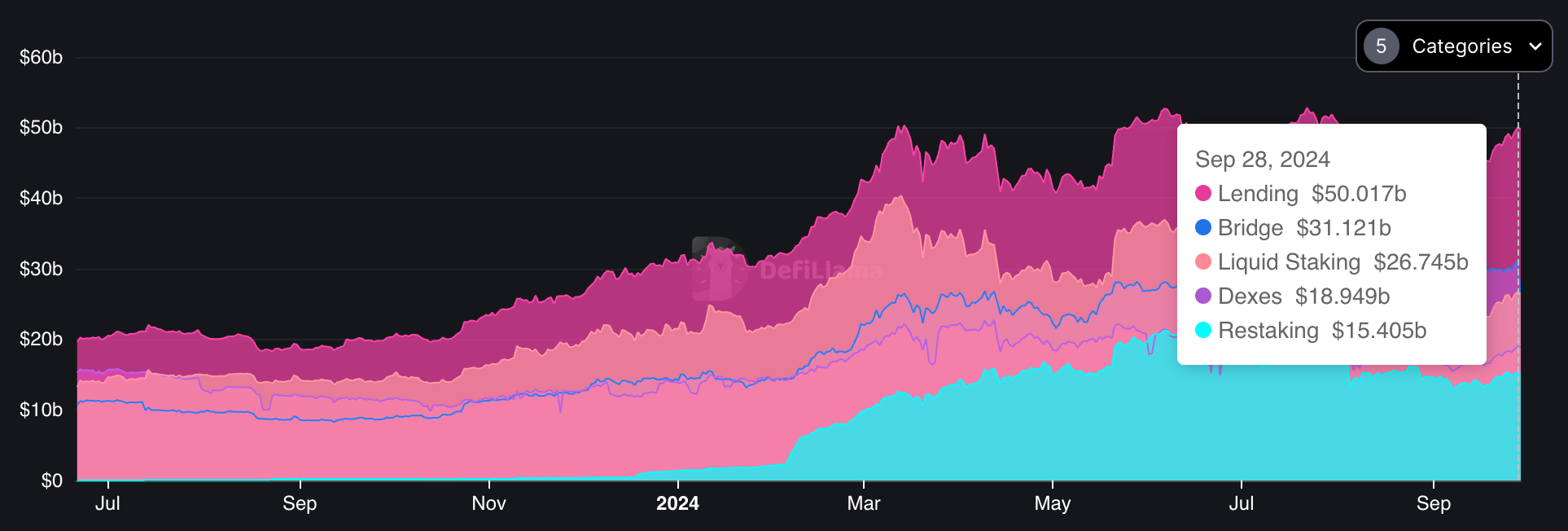
As of now, the combined TVL of the 10 restaking protocols tracked by DefiLlama stands at $15.4B, placing it fifth among other categories. This is a significant achievement for a service that launched just over a year ago, beginning with EigenLayer.
Figure 20: Top 5 categories by TVL
Source: DefiLlama. As of September 28, 2024.
Within the restaking category, the top three protocols—EigenLayer, Symbiotic, and Karak—make up 94.4% of the total TVL, amounting to $14.54B.
Figure 21: Top 3 restaking protocols by TVL
Source: DefiLlama. As of September 28, 2024.
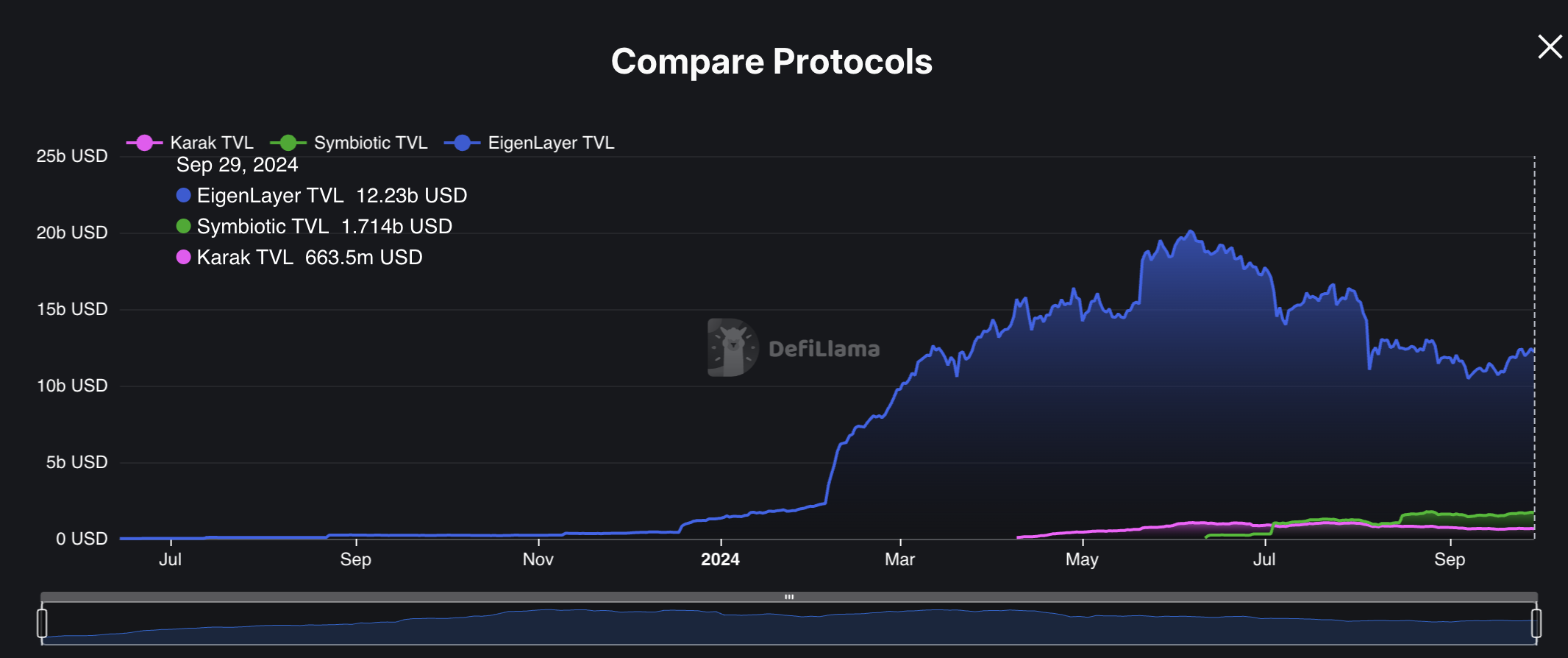
Despite EigenLayer still leading with over $12B in TVL, both Symbiotic and Karak—launched only a few months ago—have quickly gained significant TVLs of 1.71B and 664M respectively, positioning themselves as EigenLayer’s main competitors. Notably, they achieved this growth during a period when EigenLayer’s TVL has been steadily declining from a peak of approximately $20B to its current $12.2B.
Figure 22: Symbiotic and Karak: EigenLayer’s main competitors
Source: DefiLlama. As of September 28, 2024.
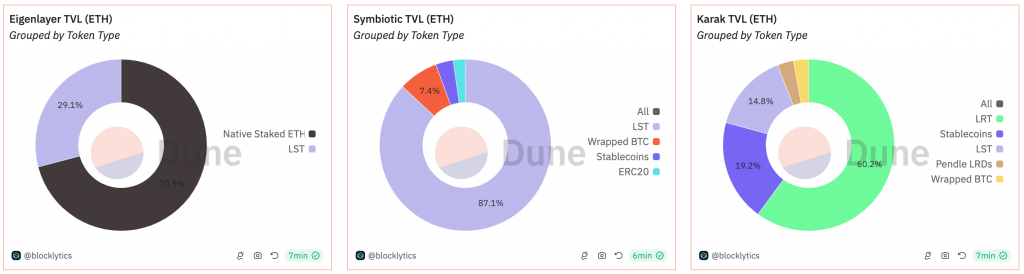
Another key metric to examine is the market share of tokens restaked in each protocol. As mentioned earlier, while both Symbiotic and Karak were designed with multi-asset support from the start, EigenLayer only recently decided to follow suit.
When analyzing TVL ($ETH) grouped by token type, there are notable differences between the three restaking protocols. EigenLayer’s token distribution is heavily dominated by native restaking, which accounts for 70.9% of its TVL, with LSTs making up the remaining 29.1%. In contrast, Symbiotic market share is overwhelmingly led by LSTs, which account for 87.1% of its TVL, followed by wrapped $BTC (7.4%) and stablecoins. Karak, on the other hand, is dominated by LRTs, which make up 60.2% of its TVL, with stablecoins and LSTs sharing a similar portion of the restaked assets.
Figure 23: Top 3 restaking protocols – Token type TVL market share
Source: dune.com. As of September 28, 2024.
Restaking and Collateral Selection
As highlighted in the paper “How much should you pay for restaking security?”, an application’s economic security is closely tied to the price stability of its collateral. A drop in the collateral’s market value can make it more profitable for attackers to exploit the application, as lower collateral prices reduce the capital needed to corrupt the network (e.g., controlling 51% of the collateral). This makes the network more vulnerable as the economic incentive for operators to validate truthfully decreases in line with falling collateral values.
Given this, $ETH-backed collateral is generally seen as providing stronger economic security due to its lower volatility, deeper liquidity, larger market cap, and overall greater accessibility. In contrast, non-$ETH-backed collateral, such as governance tokens, carries higher risks for application security. These tokens are often more volatile, exposed to governance risks, may have lower liquidity, and are not as widely accessible as $ETH, making applications more vulnerable to attacks.
Given these assumptions, using native $ETH as collateral ties an application’s security directly to Ethereum’s security and value, which is broadly recognized as the most credible neutral blockchain. Other collateral types, such as LSTs, LRTs, or newly issued native assets, introduce varying levels of risk depending on their primary and secondary market liquidity. Therefore, for applications considering a mix of non-$ETH-backed assets (e.g., native tokens) alongside $ETH/LST collateral to secure their networks, it’s crucial to evaluate the cost versus security trade-offs within each dual-staking framework.
A well-designed dual-staking framework can help address some of the security challenges posed by non-$ETH-backed assets. This model uses two tokens to secure the same restaking service, where one token, such as $ETH, provides external economic stability due to its lower volatility, deeper liquidity, and accessibility. By doing so, the network can mitigate the risk of a death spiral—where a decline in the native token’s value weakens network security—since $ETH collateral maintains a baseline of economic security, even when the native token’s price falls.
From the perspective of economic security, restaked assets like $ETH and LSTs may offer a cheaper and more secure solution than using native application-specific tokens. This is particularly relevant for applications requiring a high degree of trust and security, such as bridges. Consider the number of existing $ETH token holders and stakers, which expands the Total Addressable Market (TAM). However, for many crypto projects, the ability to issue and use native tokens as incentives is a fundamental driver of value creation. Thus, while using restaked assets can complement a project’s security framework, it shouldn’t cannibalize the value of native tokens. The decision on which assets to use should ultimately align with whatever best supports the application’s functionality and business goals.
In the end, developers will have the flexibility to choose from a variety of restakable assets based on their unique needs. Some may opt for single-asset restaking with $ETH or liquid staking tokens (LSTs), while others might rely solely on their own token or a mix of assets like $ETH and stablecoins. The key here is the optionality offered by the underlying marketplace, allowing users and protocol builders to tailor their approach based on factors such as desired economic security, utility for governance tokens, liquidity, and the number of token holders.
Major Risks and Concerns
Restaking has attracted over $20 billion in capital in 2024 alone, serving as one of the fastest capital formation events within the history of cryptocurrency. Restaking protocols, such as EigenLayer, Symbiotic, and Karak, offer opportunities for users to earn additional yield on already-staked assets and expand options for developers, but they also introduce numerous risks and concerns. The main concern, and a common misconception, about restaking is that it involves rehypothecation or leverage. However, as we will explore, restaking does not equate to leverage in the traditional sense.
Risks
In traditional finance, rehypothecation implies that depositors no longer have direct control over their assets and they are subject to liquidity and counterparty risks, leaving them vulnerable to potential losses. However, restakers in protocols like EigenLayer retain full control over their staked tokens and can decide what AVSs they want to validate. This means that the protocol is not using the restaked assets to get involved in financial activities such that small price movements could result in liquidations. Although the concept of rehypothecation does not directly apply to restaking, there are still risks to be considered. In fact, when assets are restaked across multiple protocols, the exposure to slashing or losses is magnified. If assets are compromised in one protocol, the damage reverberates across all others where they have been staked, increasing the network’s vulnerability to systemic failures. For example, with Karak allowing the restaking of EigenLayer’s LRTs, a slash of these assets on EigenLayer would also affect the restaked assets on Karak. The depegging event of ezETH illustrates the risks of holding LRTs, which could face liquidity issues or value fluctuations.
Leverage refers to the use of borrowed funds to increase the potential return on an investment. For restaking protocols, however, the reference to leverage often points to the fact that operators can run multiple AVSs at the same time, previously referred to as pooled security model (i.e. same amount of capital at risk but earning yield from multiple places). EigenLayer notes that this is not the same as “leverage” in the traditional sense. When you are restaking you have skin in the game and you get slashed if you don’t operate properly. However, the pooled security model still comes with its own risks. In particular, it may lead to systemic risks, as a failure in any one service can have a widespread impact on the entire network. When an operator is slashed, the losses don’t just affect the original stake but also extend to all services that rely on that stake, which implies that services themselves indirectly bear risk from other services. The worst-case outcome is a cascading attack. This is where slashes in one service impacts other services that are pooled via common node operators. If a malicious node operator is willing to be slashed in order to earn a profit from corrupting the network, groups of services can be attacked sequentially until the entire network’s stake is slashed. Different works, such this one, demonstrated that this can happen given an adversary can attack arbitrarily large groups of services and if the network is not sufficiently overcollateralized.
Another significant concern is the potential for restaking to overload Ethereum’s social consensus. In particular, Vitalik Buterin has warned that major issues arising from restaking could lead to a strain on the Ethereum community’s ability to reach consensus, especially if a network fork is seen as a necessary solution to resolve these problems.
As restaking gains popularity, the risk of centralization becomes another increasing concern. Large validators and liquid staking providers may dominate the restaking process, centralizing power and increasing the risk of coordinated attacks or large-scale failures.
Another potential issue is that, if the same stake is restaked at several services by the same operator, the cumulative gain from malicious behavior may exceed the loss from slashing. One way to prevent this risk is to use the attributable model in addition to pooling. This way the CoC would be greater and the service would have the guarantee to be able to slash the attributable portion if needed.
Vulnerabilities in the smart contracts governing restaking protocols could lead to the loss of staked funds. This risk is particularly relevant as new layers of risk are added on top of each other, using Zach Rynes words: “A liquid restaking token that is backed by liquid staking tokens deposited in a restaking protocol which rehypothecates staked $ETH”.
Moreover, stakers who engage in restaking are exposed to greater slashing risks. They must rely on their chosen operators not only for honesty—ensuring they avoid slashable offenses—but also for competence in maintaining uptime and avoiding inactivity penalties. This mirrors the challenges faced when selecting staking services on Ethereum. However, restaking operators may validate for a variety of services, each with its own level of risk. As a result, choosing the right operator becomes critical in managing exposure, as the risks involved, like the rewards, are cumulative. This increased responsibility requires operators to be more vigilant than ever, as any failure in their duties could result in slashing and significant financial losses.
Finally, It is also worth mentioning the risk of invalid slashing, which includes both slashing honest nodes, as well as not punishing a malicious one. Of these, slashing honest nodes is more serious. For instance, imagine the damage of an application incorrectly slashing all the $ETH that’s been restaked into it. This is also why most restaking protocols provide different measures, such as withdrawal delay or veto committees, to manage these situations.
Concerns
Restaking allows users to increase their yields by participating in additional services. Restaking, however, doesn’t inherently produce yield; returns depend on the success and incentives of the services integrated into the protocol. This reliance raises concerns about sustainability, especially when services hold large amounts of restaked $ETH without clear demand or utility. Without solid yield mechanisms, the incentive for participants to keep their assets in restaking protocols diminishes, emphasizing the importance of balancing risks and rewards. Additionally, since these services aren’t profitable at inception, they must rely on inflating their own token supply to pay for staked $ETH. Incentive misalignments could arise, leading to participants selling these tokens to accumulate more $ETH. This creates both dilution and a net drain on the protocol as revenue exits their ecosystem to reward $ETH stakers. Given these premises, as these yields are often subsidized by native token issuance rather than generated through sustainable revenue, concerns about long-term profitability are raising.
Additionally, there’s a risk that the TVL across restaking protocols could outstrip the actual security needs of the protocols, leading to a drop in yields. This could undermine the economic models of restaking platforms.
Another concern is that while restaking can improve the economic security of a network, liquidity fragmentation between multiple restaking protocols may lead to a lack of confidence for developers and users regarding which protocols and assets are the most secure.
Conclusion
Restaking protocols such as EigenLayer, Symbiotic, and Karak represent a transformative approach to securing decentralized applications by leveraging existing staked assets for multiple services. These protocols allow developers to access pooled economic security, providing a faster go-to-market strategy while offering stakers and node operators additional revenue streams. However, restaking introduces a new layer of complexity in the crypto economic model, requiring careful consideration of risks, including systemic vulnerabilities, slashing, and liquidity fragmentation.
The emergence of different models—pooled versus attributable security—has provided flexibility for both developers and validators. While pooled security offers capital efficiency and broader participation, it introduces systemic risks that can impact multiple services simultaneously. In contrast, attributable security isolates risk to specific applications, offering stronger guarantees but at higher costs and operational diligence. The expansion of collateral types beyond $ETH and the introduction of multi-asset support have further diversified restaking opportunities but also heightened the need for careful risk management. The balance between security and incentives highlights the complexity of ensuring sustainable, long-term economic security for applications and their users.
In conclusion, restaking protocols present significant opportunities but must be approached with caution. Developers must weigh the benefits of additional security and rewards against the potential systemic risks and economic trade-offs.
References
@blocklytics, (2024) Ethereum Restaking (Eigenlayer, Symbiotic & Karak). Dune.com | Link
@ManoppoMarco, (2024) What happens when every token gets restaked? Published on X | Link
Deb S., Raynor R., Kannan S., (2024) STAKESURE: Proof of Stake Mechanisms with Strong Cryptoeconomic Safety. Published on arXiv | Link
Deshpande S., (2024) Pushing Boundaries of Trust. Decentralised.co | Link
EigenLayer, (2024) Coming Soon: Permissionless Token Support on EigenLayer. EigenLayer Blog | Link
EigenLayer, (2024) Introducing the EigenLayer Security Model: A Novel Approach to Operating and Securing Decentralized Services. EigenLayer Blog | Link
EigenLayer Documentation | Link
eOracle, (2024) Cryptoeconomic Security. eOracle Documentation | Link
Hydrogen Labs, (2024) Anzen Protocol: Optimizing operator payments on EigenLayer. Whitepaper | Link
Llama Risk, (2024) Current State of Symbiotic | Link
Gauntlet T.C., Pai M., (2024) How much should you pay for restaking security?. Published on arXiv | Link
He M., (2024) Restaking Collateral Health. Gauntlet | Link
Karak Documentation | Link
Revelo Intel, (2024) EigenLayer – Decentralized Trust Marketplace | Link
Symbiotic Documentation | Link
Disclosures
Revelo Intel is not engaged in a commercial relationship with EigenLayer, Symbiotic, and Karak and this report was not paid for or commissioned in any way. Members of the Revelo Intel team, including those directly involved in the analysis above, may have positions in EigenLayer, Symbiotic, and Karak or any other protocols discussed in this report.
This content is provided for educational purposes only and does not constitute financial or investment advice. You should do your own research and only invest what you can afford to lose. Revelo Intel is a research platform and not an investment or financial advisor.