Introduction
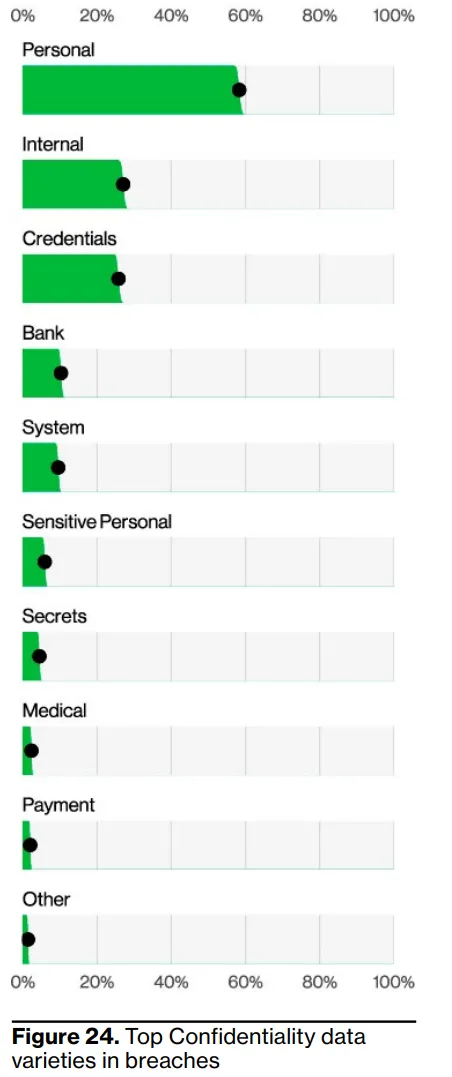
Massive data breaches and identity theft incidents have eroded confidence in centralized ID systems (e.g. LinkedIn data associated with 700 million of its users posted on a dark web forum in June 2021, impacting more than 90% of its user base). Digital trust is breaking and repeated breaches show that a single hacked database can leak millions of confidential user information. While decentralized identity systems remove the reliance on a single point of failure, the rise of AI-driven bots enables Sybil attacks which undermine integrity. Without a reliable “one human, one account” check, fake identities overrun networks and warp incentives.
Humanity proposes a fix to the trust issue in identity systems by offering self-sovereign identity and Sybil resistance. It uses a non-invasive, palm-based biometric authentication system to verify unique personhood, along with advanced cryptography to protect user data. This report examines Humanity Protocol’s design and real-world impact through the lens of decentralized identity: how its palm-scanning and zero-knowledge (ZK) tech stack tackles key DID challenges, what advantages and risks come with its approach, and what upcoming developments might shape its role in the broader movement for privacy-preserving digital identity.
Key Takeaways
- The Case for Decentralized Identity: Centralized identity solutions (from government IDs to CAPTCHAs) suffer from breaches, bot abuse, and intrusive data collection.
- Humanity Protocol’s Unique Approach: A Sybil-resistant identity network using palm biometrics for proof-of-personhood and zk-proofs for privacy.
- Bridging real-world and Web2 data with users’ Human IDs: Users of Humanity Protocol can prove information from Web2 platforms, such as their social accounts, without ever sharing the page itself via zkTLS.
- Privacy and User Control by Design: Biometric data in Humanity’s system is encrypted, sharded across decentralized nodes, and can be deleted by the user at any time.
- Network Effects and Scalable Adoption: Humanity’s smartphone app lowers the barrier to entry by allowing anyone with a standard phone to join. The $H token will serve as the ecosystem’s engine, rewarding participants for verifying and maintaining the network.
The Need for Decentralized Identity and Sybil Resistance
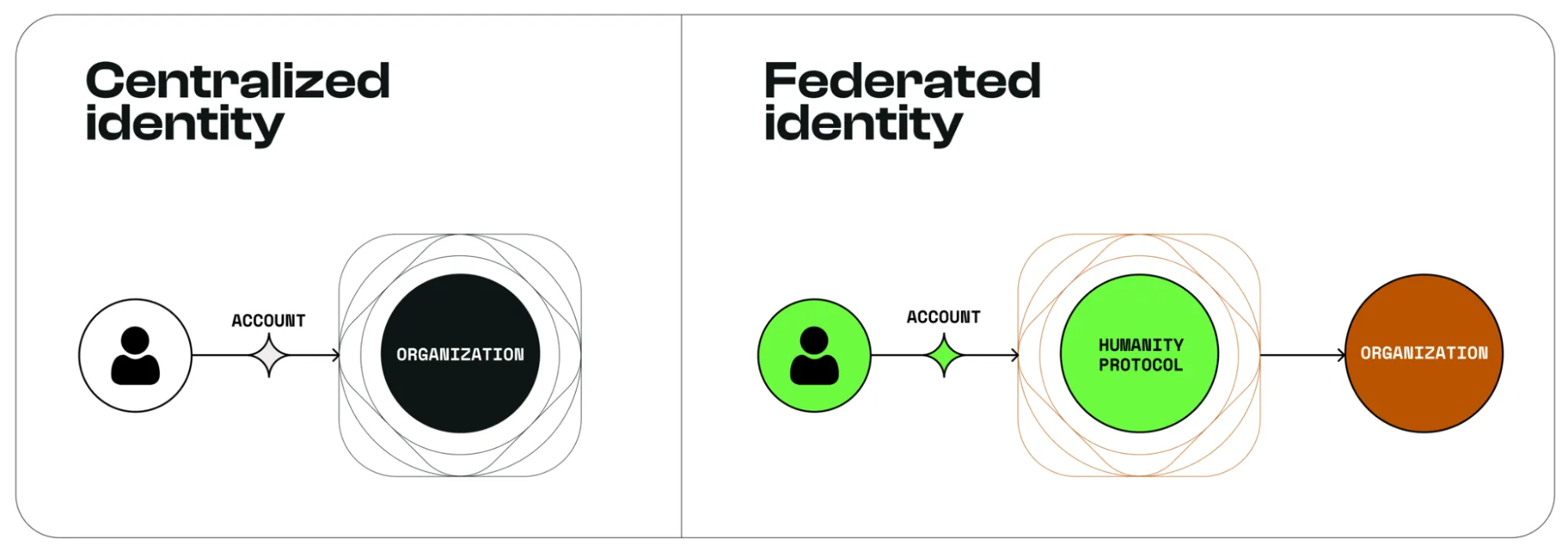
In Web2, dominant platforms like Google and Facebook act as de facto identity providers, harvesting and monetizing user data while exposing individuals to surveillance, breaches, and algorithmic manipulation. Federated identity models (e.g., “Sign in with Google”) deepen reliance on centralized gatekeepers.
Centralized identity systems, while efficient, suffer from critical flaws:
- Vendor Lock-In: Users and applications become dependent on single providers (e.g., AWS Cognito), risking service discontinuation or arbitrary fee hikes.
- Single Points of Failure: Data breaches at centralized custodians.
- Privacy Erosion: Centralized issuers retain full visibility into user activity, enabling mass profiling.
The widespread growth of AI bot usage has also undermined the integrity of online communities, skewing everything from social media statistics to more crypto-native examples like token airdrops. CAPTCHAs that once distinguished humans from machines are rapidly losing efficacy, as advanced bots can now achieve success rates even greater than humans.
In crypto, this problem is rampant. Decentralized networks struggle with botted accounts distorting governance, airdrops, and resource allocation (e.g., bots claiming disproportionate UBI payments). The absence of credible identity frameworks limits Web3’s ability to bridge with traditional systems (e.g., credit scoring, property rights), perpetuating segregation between on-chain and off-chain economies.
Decentralized Identity offers an alternative model where instead of a single authority storing and vouching for everyone’s data, a DID framework lets individuals hold their own verified credentials and present proofs when necessary. A number of early DID projects have explored different methods to establish personhood, but many stumbled due to impracticality or privacy trade-offs.
Humanity Protocol tackles this problem with the promise of a more user-friendly and privacy-preserving solution to the “proof of human” problem. This is achieved by using the unique pattern of one’s palm. By tying identity to a unique biometric trait and anchoring that verification on a public blockchain with cryptographic protections, Humanity delivers Sybil resistance (one human = one identity) for both Web3 and traditional Web2 use cases.
Protocol Design: Palm Biometrics and Zero-Knowledge Proofs
Humanity Protocol’s flagship design choice is to use palm biometrics for identity verification. Each user registers by scanning their palm using the Humanity mobile app, which captures a high-definition image of the palm. Worldcoin made headlines by introducing orb-shaped iris scanners to verify humanness, handing out coins in exchange for eyeball scans. While conceptually similar in tying identity to biometrics, Worldcoin’s approach drew criticism for being invasive and centralized.
Humanity Protocol consciously distances itself from such “dystopian” optics, opting for a palm scan that feels more like taking a photo and emphasizing that the biometric data never sits in one centralized silo, thus delivering a high assurance of personhood while ensuring a high level of privacy.
The rationale for palm recognition is that the palm is rich in unique features. Not only the surface palm print (lines, whorls, ridges), but also vein patterns are distinct to each individual. These patterns also remain largely constant throughout one’s life, providing a durable biometric key.

Importantly, Humanity’s use of biometrics strives to be non-invasive in both a physical and a privacy sense. Palm scanning is a contactless and familiar process, which means it can be done quickly via a smartphone camera anywhere in the world, lowering the friction and barrier to entry. Early user feedback highlights the “ease of onboarding” and comfort with palm scans relative to other methods.
The use of zero-knowledge proof (ZKP) technology ensures that users can prove things about their identity without disclosing private data. For instance, the most basic credential might simply return “I am a unique human (and have only one ID in the system)”, solving the Sybil issue.
From KYC and CAPTCHA to Human ID
Humanity Protocol’s philosophy can be seen as a direct response to the failure of legacy identity verification. Consider the standard bank or exchange KYC process: a user uploads government IDs, maybe a selfie, and waits until a centralized service verifies these against pre-existing databases. This process is not only cumbersome and time-consuming, but it also puts users at risk because their personal documents are now stored on someone else’s servers. Data leaks from KYC providers have exposed millions to fraud, and even honest companies often over-collect data (storing more than needed) for self-benefit purposes. Traditional countermeasures like CAPTCHA challenges or phone/SMS verification are increasingly inadequate. CAPTCHAs can be farmed out to click-farms or bypassed by AI, and phone verification can be easily gamed (VoIP numbers, disposable SIMs, or simply one person managing hundreds of phone numbers).
Instead, Humanity Protocol introduces Human ID, which flips the script from “verifying the documents” to “verifying the human”. When additional identification is needed (say, proving nationality or creditworthiness), it can be done by attaching verifiable credentials from trusted issuers (governments, banks) to the Human ID, rather than re-verifying the biometric or exposing all personal data. Human ID also offers better counters to Sybil attacks, since a malicious actor cannot easily create dozens of identities (as they need unique palms). This is not to say abuse becomes impossible. As with any biometric system, there is a hypothetical risk of identity farming (e.g., convincing or coercing real individuals to register and then handing over their credentials). However, that kind of attack is orders of magnitude harder and more detectable than a bot factory generating fake emails or solving CAPTCHAs.
Incentives and Mobile-First Strategy
Even the best identity system is useless without users and verifiers, which creates a chicken-and-egg problem. Humanity Protocol’s rollout strategy recognizes the importance of both UX and incentives in building momentum.
Seamless Mobile Onboarding
A frictionless process is the first-step to adoption. By focusing on a smartphone app for enrollment and verification, Humanity taps into a massive existing infrastructure. Billions of people already have mobile devices with decent cameras. The process of getting a Human ID is designed to be as straightforward as installing an app, creating a wallet, and scanning your palm.
The early response has been encouraging: during the protocol’s debut, 25,000 users signed up within a day, and within a month over 500,000 users had joined the waitlist for an ID. To date, over 6M users have created their Human ID.
Strategic Partnerships
Network effects are also pursued through strategic partnerships and integrations. To date, Humanity Protocol has integrated with leading projects, including Kaito, ApeChain, and OKX Wallet, as well as NASDAQ-listed Prenetics.
The partnership with LayerZero, for instance, hints that Humanity IDs could be used cross-chain where a verified human on Humanity’s L2 might seamlessly prove their uniqueness on Ethereum, Solana, or any network connected via LayerZero.
Beyond raw sign-ups, what will drive sustained adoption is real use cases. Humanity Protocol is positioning its Human ID as a universal login and verification method across Web3 and Web2. Already, we see a few directions:
- Web3 Sybil Protection: DAO governance, token airdrops, and play-to-earn games often suffer from bots or one person exploiting multiple accounts. Projects can integrate Humanity to require a PoH proof for participation. For example, a DAO could mandate that each wallet voting on a proposal has a valid Human ID credential, ensuring one vote per human. In DeFi, protocols considering retroactive airdrops can filter out farming bots by checking for Human IDs, making distribution fairer. This use case directly addresses the “Sybil attack” issue noted in web3.
- Compliance and KYC: Fintech and exchanges could use Humanity to satisfy KYC regulations in a privacy-preserving way. Instead of asking users to upload passports and expose themselves to data leaks, an exchange could accept a ZK proof from the user’s wallet that their Human ID has a “KYC’d” credential from a known provider. Humanity has started partnering in this arena; for instance, they collaborated with Kaito on “Yapper Credentials”
and an education credential program with Open Campus, hinting at a push into both social media verification and academic records.
These partnerships suggest early vertical integrations that bridge into web2 realms like LinkedIn or a jobs platform that could verify a candidate’s degree via their Human ID instead of directly contacting a university.
- Payments and Commerce: The mention of a point-of-sale device and payment experiences with a wave of the hand indicates Humanity’s ambition in the physical commerce space. They envision that your Human ID could also tie into payment methods or at least authentication for payments.
This overlaps with trends like Amazon’s palm-pay system (Amazon One) but with a decentralized twist (you could use it anywhere, not just one company’s stores). If executed, a user could link a crypto wallet or even a credit card token to their Human ID for swift checkout in stores. The benefit is twofold: frictionless UX (no cards/phones needed, just your hand) and fraud prevention (a thief can’t steal your hand like they can a card). For merchants, a Humanity point-of-sales device could authenticate age (for alcohol purchases), loyalty memberships, or event tickets simultaneously with payment, all in one scan, reducing overhead and user hassle.
- Online Identity and Community: On social platforms and gaming, a Human ID could become a badge of authenticity. Verification on social media can be decentralized, an account could show a “Proof of Humanity verified” checkmark on X that tells others this isn’t a bot or sockpuppet. This could dramatically reduce trolling and bot spam if adopted widely. For example, Discord servers requiring Humanity verification to join, or forums giving more weight to posts by verified humans. We might also see one-click sign-on using Human ID for various dApps, similar to “Login with Google” but without Google, the user signs a message with their DID and the dApp checks the Humanity contract.
The protocol’s growth strategy intends to mirror that of a tech startup rolling out a new network: drive user adoption through a compelling free product (the ID app), encourage engagement through rewards, and simultaneously court enterprises/developers to integrate the ID into services. If successful, every additional integration could onboard thousands of new users, and every additional user in turn makes the integration more valuable.
$H Token Utility
Humanity Protocol ($H) is a multi-functional ERC-20 token designed to support a decentralized identity verification network. With a fixed supply of 10 billion tokens, the protocol aims to balance demand through identity attestation services, staking rewards, governance mechanisms, and partnerships with third-party applications.
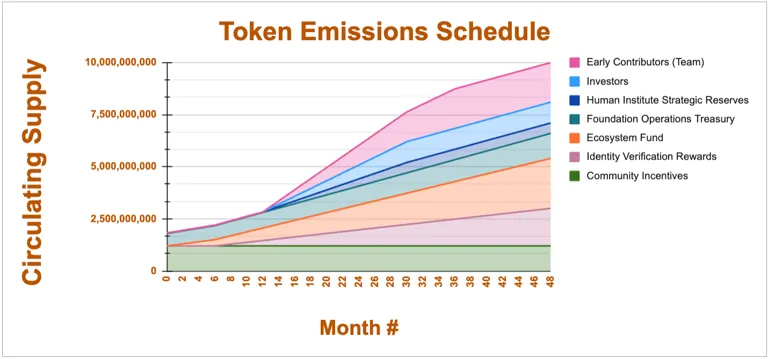
The Humanity Protocol ecosystem is composed of several key stakeholders, each playing a distinct role in the network’s functionality and economic sustainability. These participants contribute to the protocol’s security, governance, and adoption through various mechanisms.
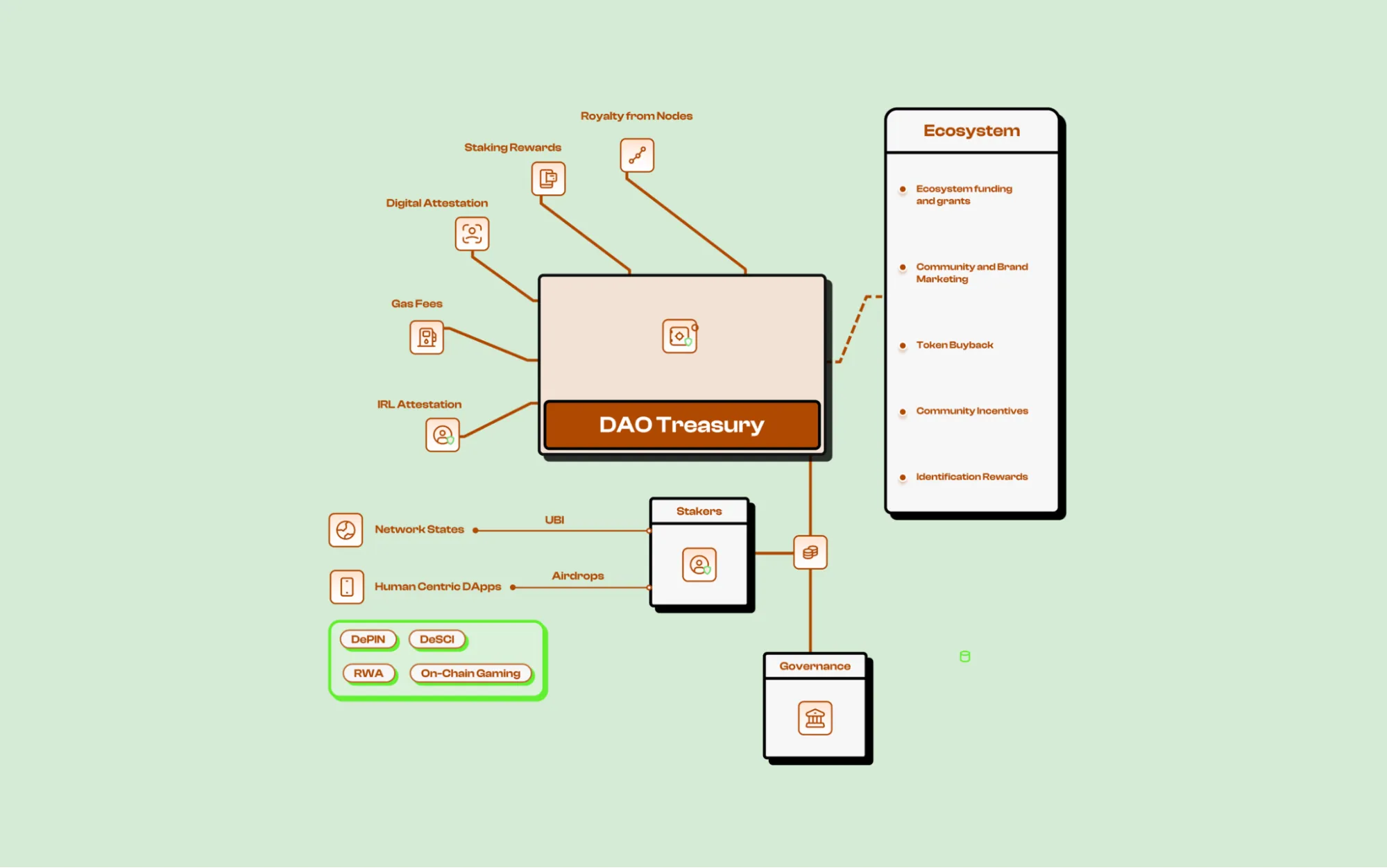
Primary Stakeholders:
- End Users: Individuals who engage with the network by verifying their identity, participating in governance, and utilizing ecosystem applications. These users benefit from secure identity verification and may receive incentives for their engagement. 12% has been allocated as rewards for user onboarding.
- Identity Validators: Participants who stake $H tokens to issue and verify identity credentials. Their role is crucial in maintaining network integrity, and they earn a share of verification fees as compensation.
- zkProofer Node Operators: Responsible for running verification proofs that validate credentials. These operators receive rewards in return for their computational efforts, which support the protocol’s trust architecture. 18% of token supply is allocated as a base incentive pool for node operators.
- Third-Party Applications: External platforms that integrate with the Humanity Protocol to utilize identity verification and attestation services. These applications contribute to network activity and may receive onboarding incentives for participation.
- Humanity Protocol Foundation: Manages various aspects of the protocol, including operational costs, partnerships, and community incentives. The foundation also plays a role in maintaining liquidity and supporting ecosystem development.
- Governance Participants: $H token holders who participate in governance by voting on key protocol decisions. Their involvement ensures decentralized decision-making and long-term network sustainability.
The interaction between these stakeholders establishes an interconnected ecosystem where each participant benefits from and contributes to the overall functionality of the Humanity Protocol. As adoption grows, the collective engagement of these groups is expected to drive network expansion and enhance the token’s utility.
Challenges and Risks
While Humanity Protocol presents a promising framework, it also faces a set of significant challenges and risks on the road to broad adoption. These include technical, social, and regulatory factors:
Convincing ordinary users to scan their biometrics for a blockchain project is unfamiliar to them. Even though palm scanning is less intrusive than other methods, some portion of the population will have privacy concerns or misunderstandings about how their data is used. Humanity must maintain transparency and education, clearly conveying that users can delete their data and that it’s stored securely in shards (not in a big centralized database). The early testnet success is a good sign, but scaling from tech-savvy early adopters to potentially less tech-oriented populations could reveal a new set of UX challenges.
Metadata leakage is one concern, where even if the content of credentials is private, the act of using one’s ID could create metadata (timestamps, frequency of use, etc.) that might be analyzed to infer information about the person. Humanity Protocol will need to consider techniques like anonymous credentials or rotating pseudonymous IDs to ensure that usage doesn’t erode privacy over time. Moreover, decentralized storage of data means pieces of a user’s encrypted biometric live on nodes around the world; ensuring those nodes are secure and handling data in compliance with various jurisdictions’ laws (GDPR, etc.) is complex.
Ultimately, the success of Humanity Protocol partly hinges on whether it can establish itself as a standard before alternatives catch up. If dApps and companies have multiple options, network effects become even more important. The value of a Human ID increases with usage, if users don’t find many places to use their ID, they may lose interest. Avoiding the fate of being just a “cool demo” means quickly demonstrating real utility which depends not just on Humanity’s own tech, but also on the broader acceptance of DID standards, verifiable credentials, and ZK-proofs in mainstream (web2 and web3) applications. This is a societal shift that could take time, and there is a risk that users get disengaged if tangible benefits (like easier logins, financial rewards, community access) don’t materialize steadily.
Conclusion
Humanity offers a bold new offering in the DID space with its unique palm vein biometrics which provide a high-assurance yet user-friendly proof of personhood, and zero-knowledge cryptography ensures that this proof can be utilized in a privacy-preserving, self-sovereign manner.
By addressing the shortcomings of traditional identity systems from the insecurity of centralized databases to the frustration of CAPTCHAs, Humanity offers a compelling value proposition: one digital identity per human that you control, which can be universally verified without revealing who you are. In an era where data breaches are rampant and AI-generated fakes are a growing threat, this approach could fill a critical gap in digital infrastructure.
The execution of its roadmap will determine if they can truly live up to its vision. It sits at the intersection of cutting-edge tech and sensitive societal issues, which means success will depend not just on engineering, but also on governance, community building, and trust that is not isolated to the crypto native world but also real-world integrations.
Disclosure
Alea Research is engaged in a commercial relationship with Humanity and this report was commissioned as part of that engagement.
Members of the Alea Research team, including those directly involved in the analysis above, may have positions in the tokens discussed.
This content is provided for educational purposes only and does not constitute financial or investment advice. You should do your own research and only invest what you can afford to lose. Alea Research is a research platform and not an investment or financial advisor.