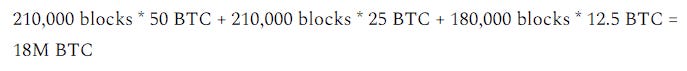A Peer-to-Peer Electronic Cash System
Bitcoin is a purely digital peer-to-peer electronic cash system that enables online payments without the intervention of any middlemen or trusted third-party. This is achieved by solving the double-spend problem with a cryptographic system of digital signatures.
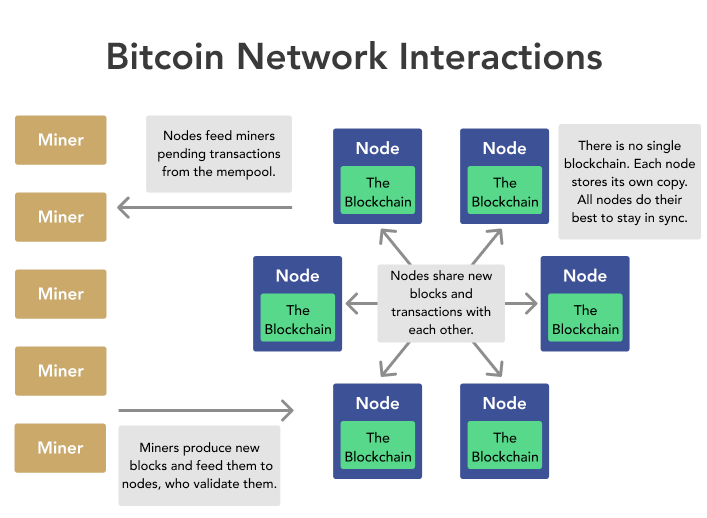
Bitcoin operates on a blockchain, a public ledger of transactions that is maintained by a network of computers distributed around the world. The network timestamps transactions by hashing them into an ongoing chain of hash-based proof-of-work, forming a record that cannot be altered without redoing the proof-of-work chain and becoming the longest chain. The longest chain serves as proof of the sequence of events that have been witnessed by the network. These transactions are verified and recorded by network nodes in a cryptographically verifiable manner. Every time a new block is added to the public ledger, new bitcoins are created through a process called mining.
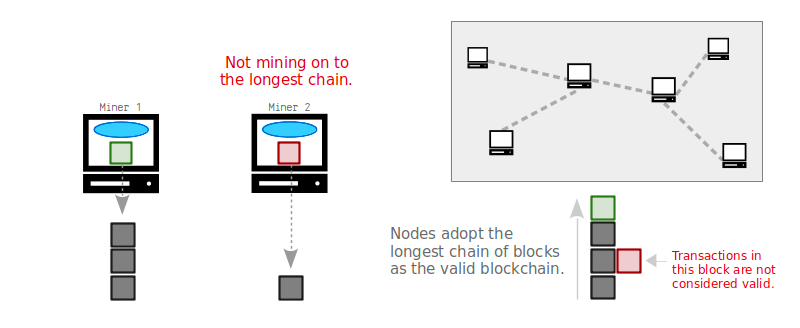
Every node on the network will always adopt the longest chain of blocks they receive as the “official” version on the blockchain.
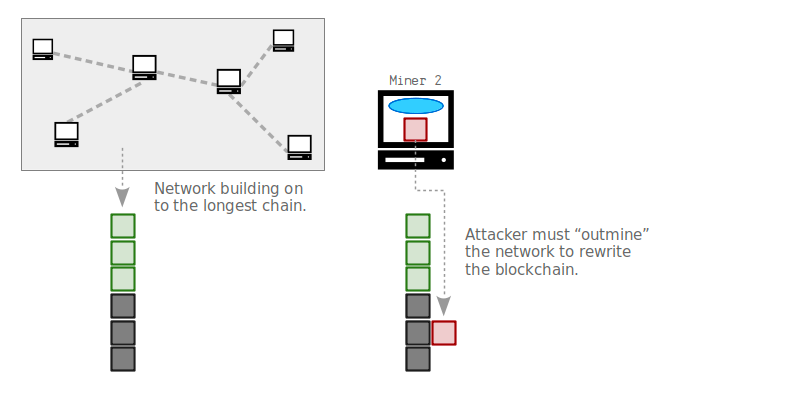
If someone wanted to rewrite the history of transactions, they would need to rebuild a longer chain of blocks to create a new longest chain for other nodes to start building on top of. However, this is only possible if that miner manages to have more computer processing power than the rest of the network combined.
For example, if someone sent you one bitcoin one year ago, the only way to erase that transaction would be to try to rewrite Bitcoin’s history since then, which would require using more energy than Bitcoin used over the entire year since that transaction was first recorded. That would take so long that, by the time it was done, there would likely be another year or more of records to try to catch up with. This process would also be extremely expensive because of the required energy costs. Not only that, but it might be even physically impossible given how much energy that would require.
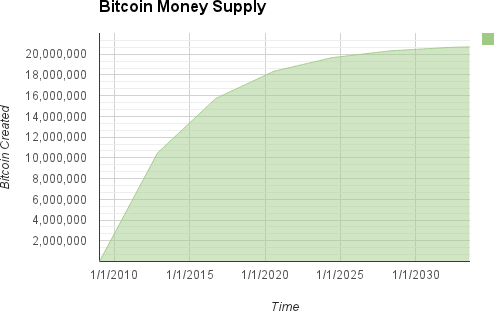
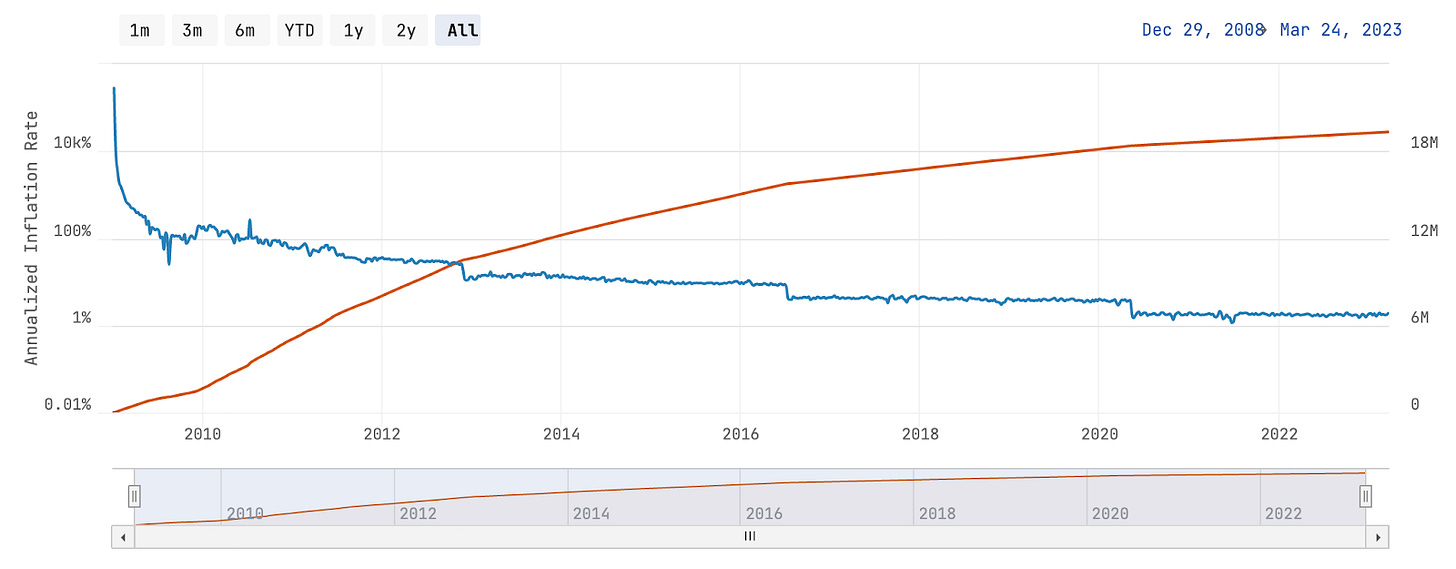
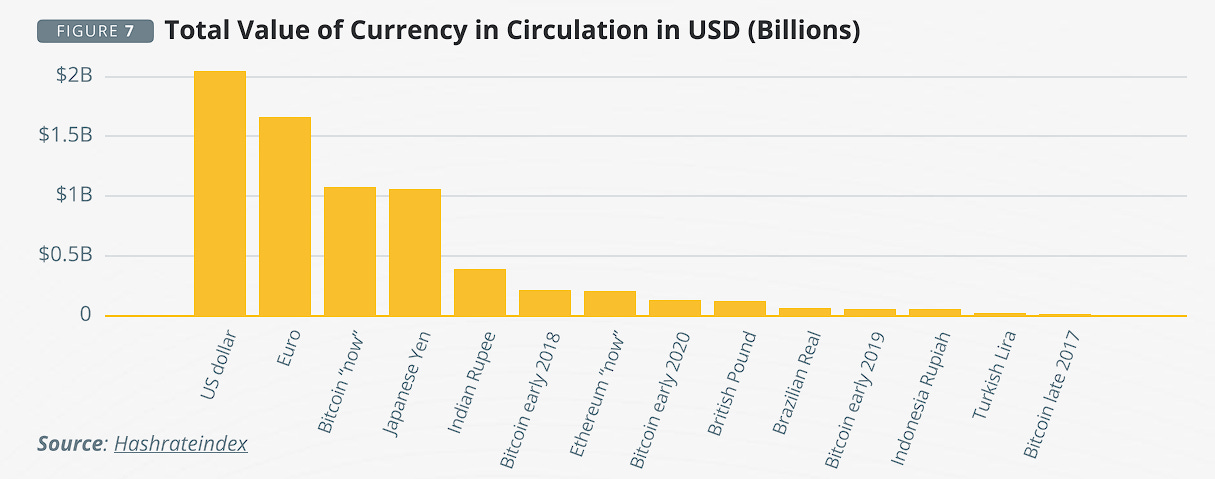
The idea was originally conceptualized in the Bitcoin whitepaper, written by the pseudonymous author Satoshi Nakamoto in 2008. The whitepaper outlines a vision for a decentralized digital currency that operates independently of traditional financial institutions and provides greater control and privacy to users. In this system, a maximum of 21 million bitcoins can be mined. This ensures that the value of Bitcoin is not subject to inflation or arbitrary decisions made by governments or financial institutions.
The Bitcoin network operates as a Proof of Work (PoW) blockchain, where powerful nodes solve complex mathematical problems and earn newly created bitcoins as a reward for keeping the network secure. Through this algorithm, the nodes participating in the network can achieve consensus and prevent fraudulent transactions without the intervention of any trusted third party.
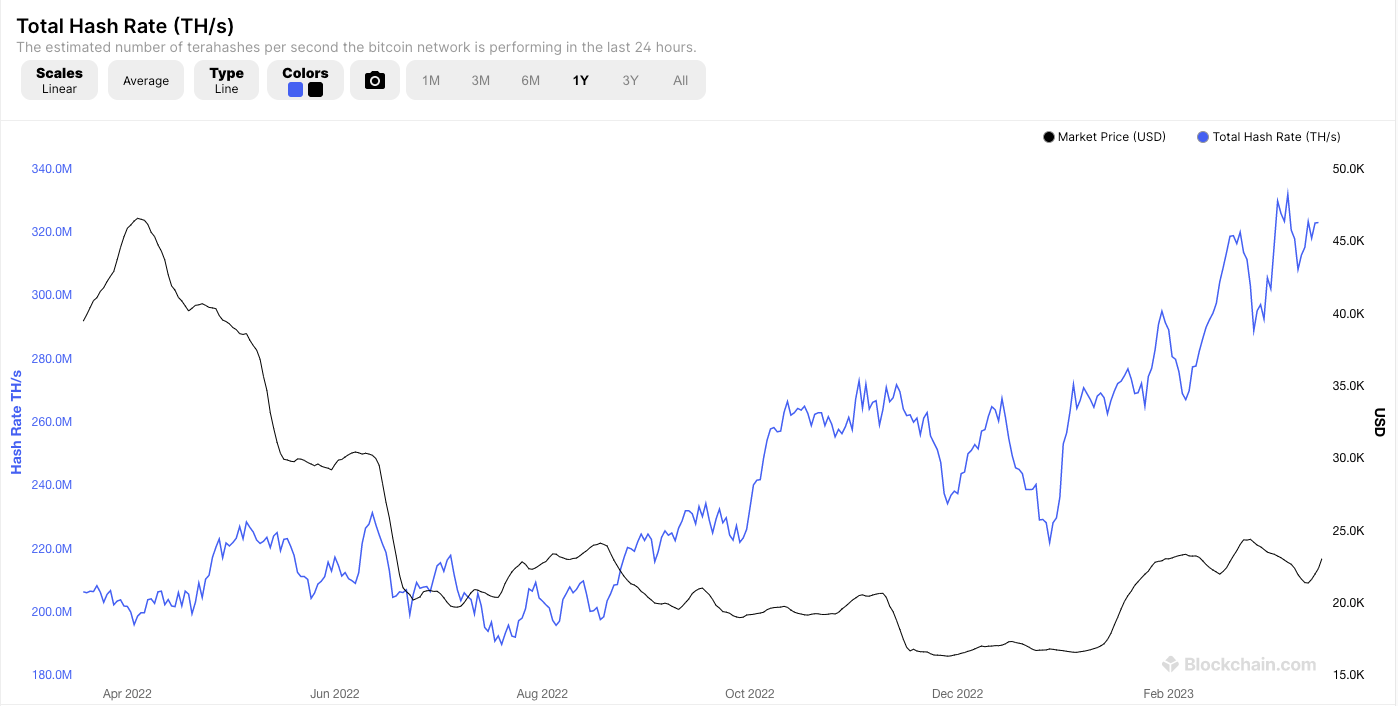
Bitcoin’s hash rate measures the rate of solving the mathematical problem involved in mining transactions, as well as the difficulty changes that take place as more miners enter the network. When more miners enter the market, the difficulty increases to ensure that the number of bitcoins produced remains the same
Bitcoin, is the name of the protocol, a peer-to-peer network, whereas the bitcoin currency is the first application of this innovative distributed computing technology. In fact, Bitcoin represents the culmination of decades of research in cryptography and distributed systems. The protocol introduced four key innovations:
- A decentralized peer-to-peer network – the Bitcoin protocol.
- A public ledger of transactions – the blockchain.
- A set of rules to independently validate the issuance of new currency units – consensus rules.
- A mechanism for reaching global consensus on a decentralized manner – proof-of-work algorithm.
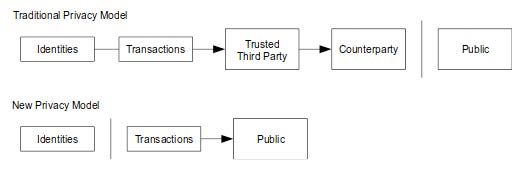
“As an additional firewall, a new key pair should be used for each transaction to keep them from being linked to a common owner. Some linking is still unavoidable with multi-input transactions, which necessarily reveal that their inputs were owned by the same owner. The risk is that if the owner of a key is revealed, linking could reveal other transactions that belonged to the same owner.” – Satoshi Nakamoto
A distributed peer-to-peer system
Bitcoin is a distributed peer-to-peer system where there is no “central server” or point of control. Units of bitcoin are created through a mining process that involves competing against other miners to find solutions to a mathematical problem while processing transactions. Anyone in the network can operate as a miner in order to verify and record transactions on Bitcoin’s public ledger. On average, regardless of how many miners are participating, every 10 minutes a miner can validate the transactions that have taken place in the last 10 minutes and, for doing so, will be rewarded with newly created bitcoin. Essentially, this permissionless participation in the mining process ensures that the issuance of new currency units is decentralized.
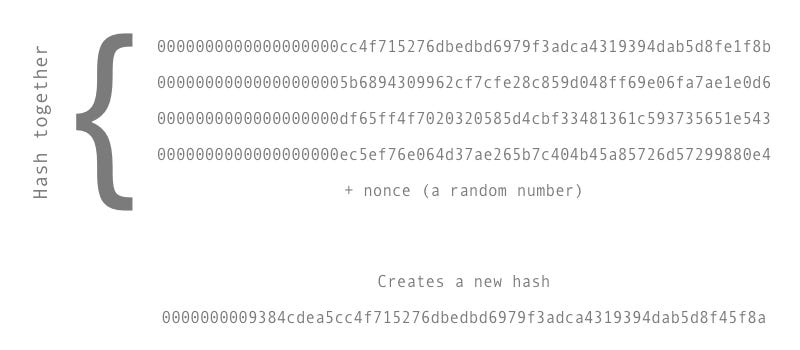
The Bitcoin protocol includes built-in algorithms that regulate the mining function across the network. This is achieved with a difficulty adjustment mechanism. In order to mine Bitcoin, a miner must first download and run Bitcoin mining software on their computer or specialized mining hardware called ASICs. This software/hardware is then used to solve complex mathematical problems known as “hashes.” These hashes involve taking a block of Bitcoin transactions and creating a unique digital fingerprint, known as a hash, that meets certain criteria.
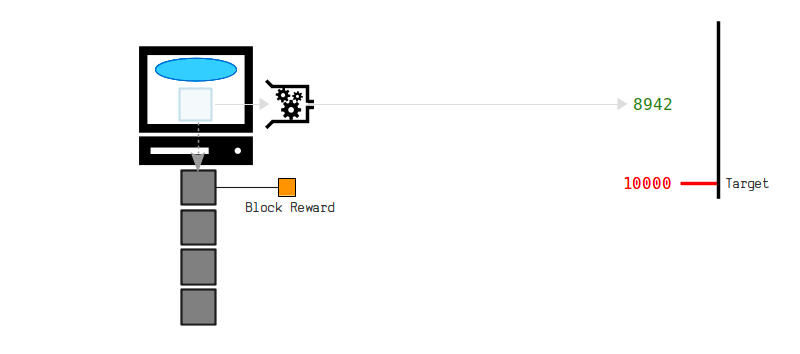
The hash must start with a certain number of zeros to be considered valid. This makes the process of mining more difficult and competitive, while also ensuring that new blocks are created at a predictable rate.
The requirement for a hash to start with a certain number of zeros also means that miners must keep trying different combinations of transactions and nonces until they find a hash that meets the criteria. Since this process involves trial and error, it is essentially a random process that requires a significant amount of computational power.
When a miner successfully solves a hash, they broadcast it to the network, and the other nodes on the network verify that the solution is correct. Once the solution is verified, the miner is rewarded with a certain amount of bitcoins in addition to transaction fees.
In order for a Bitcoin block to be considered valid, its hash must be below a certain target value. This target value is set by the Bitcoin network and is adjusted regularly to maintain an average block creation time of around 10 minutes.
The difficulty of solving these hashes is adjusted regularly in order to maintain a consistent rate of block creation, which is currently around 10 minutes per block. The difficulty adjustment is based on the total computing power of the network, known as the hash rate. If the hash rate increases, the difficulty of the problems increases, and if the hash rate decreases, the difficulty decreases. This ensures that blocks are created at a consistent rate, regardless of the total computing power of the network.
If the difficulty of the hash were too low, blocks would be created too quickly, which could lead to inflation and other issues. On the other hand, if the difficulty were too high, the mining process would become prohibitively difficult, making it difficult for new miners to enter the market.
Money and the Byzantine Generals’ Problem
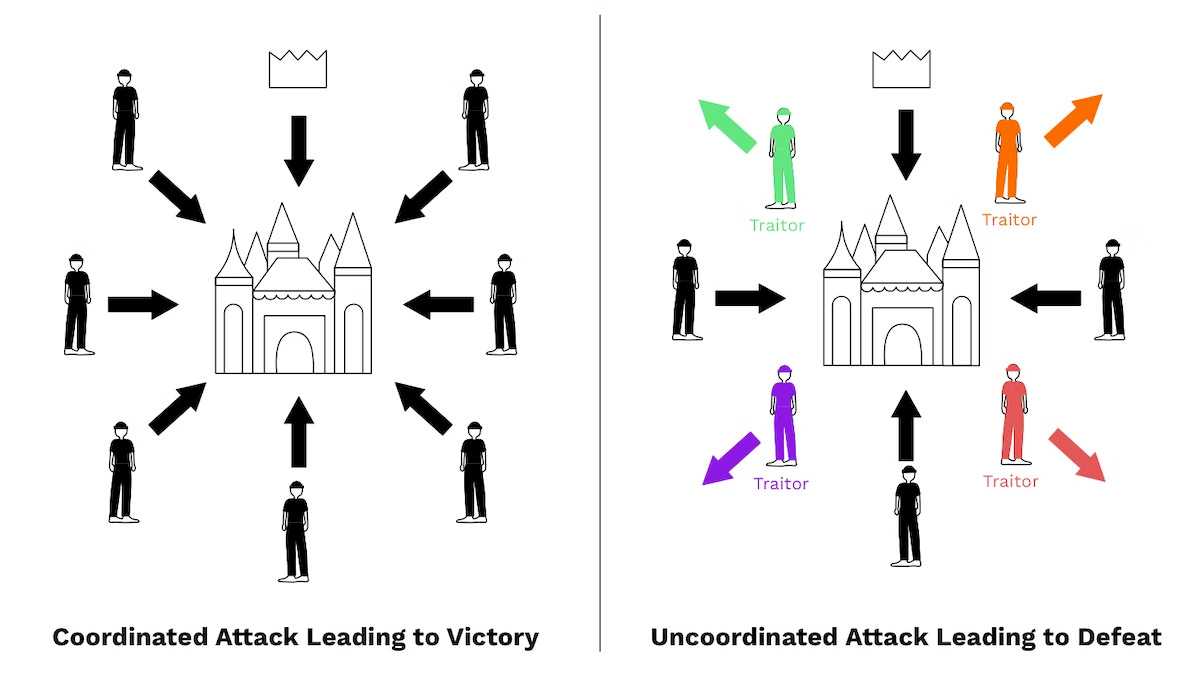
The invention of Bitcoin is also a practical solution to a problem in distributed computing, known as the “Byzantine Generals’ Problem.”
The game theory analogy to the Byzantine Generals’ Problem is that several generals have surrounded Byzantium and they must coordinate and reach a collective decision of when to attack. If all generals attack at the same time, they will win, but if they attack at different times, they will lose. However, the generals have no secure communication channels with one another. Any messages they attempt to send or receive may end up being intercepted.
Only decentralized systems face the Byzantine Generals problem, as they have no reliable source of information as well as no way to verify the information they receive from other members of the network.
This is not the case in centralized systems, where an authority is trusted to publish true information and prevent false or fraudulent information from being spread throughout the network.
For example, in the traditional financial system, banks are trusted to show clients their balances and transaction histories in an honest manner. If a bank attempted to lie or defraud their customers, a central bank or government would then be trusted to rectify such breach of trust. However, centralized systems don’t solve the Byzantine Generals problem, since truth cannot be achieved in a trustless manner. Instead, centralized solutions make the tradeoff of sacrificing trustlessness for efficiency and choose to overlook the underlying problem.
In the context of money, the Byzantine Generals Problem can be related to the problem of achieving consensus in a distributed network like the Bitcoin network. In a decentralized system like Bitcoin, all nodes need to agree on the current state of the network, including which transactions are valid and which blocks have been added to the blockchain.
However, in a decentralized network, there may be some nodes that are not trustworthy or may behave in a malicious manner, just like the traitorous generals in the Byzantine Generals Problem. These nodes could attempt to send conflicting or invalid information to other nodes, disrupting the network and potentially causing problems like double-spending.
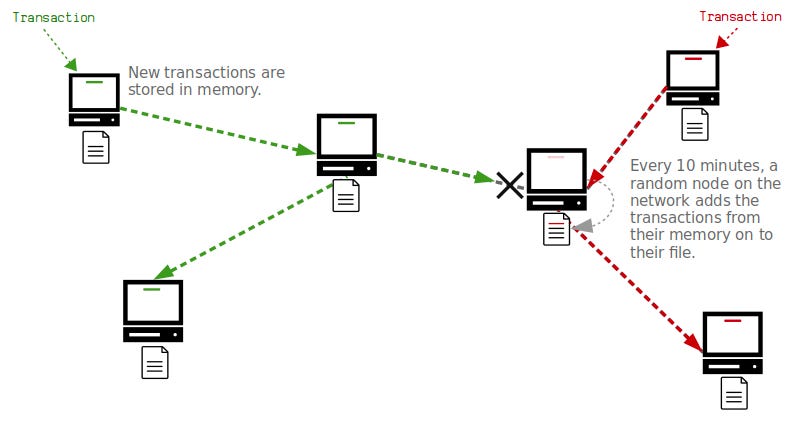
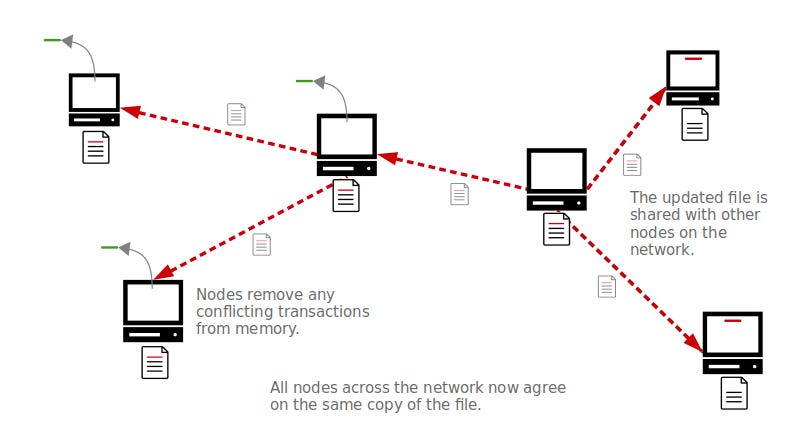
Bitcoin solves this problem by forcing nodes to keep all the transactions they receive in memory before writing them to a file. Next, following a series of 10-minute intervals, a random node on the network will add the transactions from their memory on to the file.
This updated file is then shared with the network, and the rest of the nodes will be able to accept the transactions in the updated file as “correct”, removing any conflicting transactions from their memory. This way, no double-spend transactions will ever be written to the file, and all nodes will be able to update their files in agreement with each other.
To add new blocks to the blockchain, the Bitcoin network uses a PoW consensus mechanism that requires nodes in the network to perform computationally intensive calculations. This ensures that all nodes in the network are incentivized to act in the best interest of the network, which prevents malicious nodes from dominating the network.
The double-spend problem
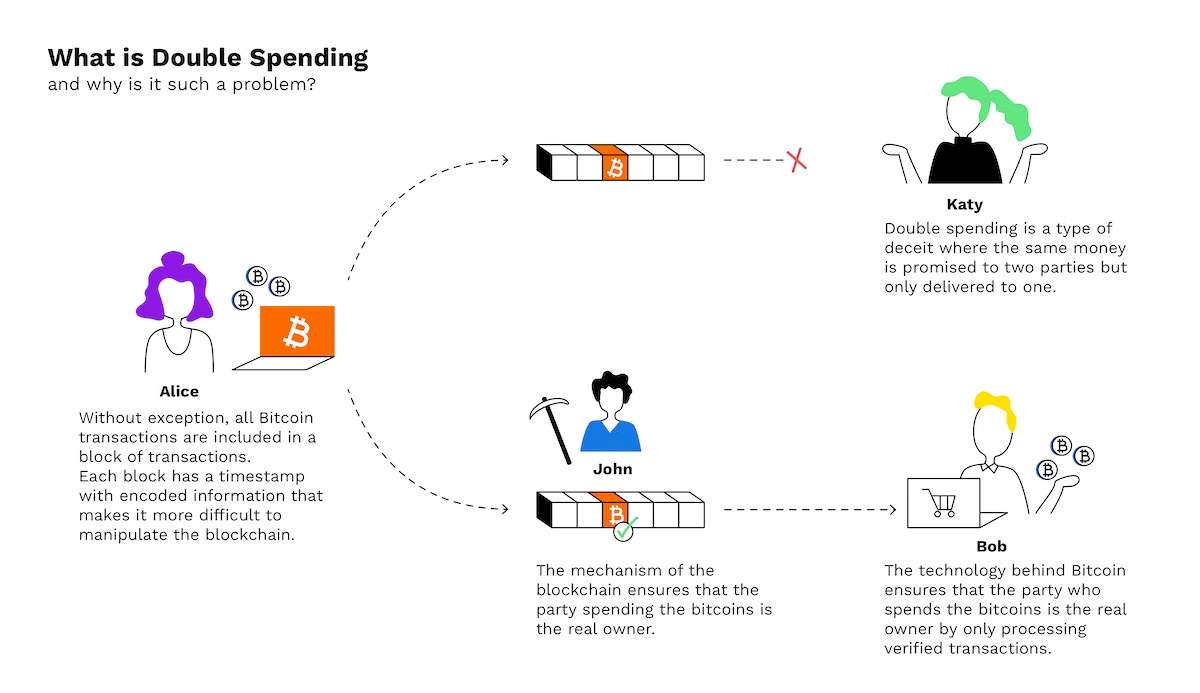
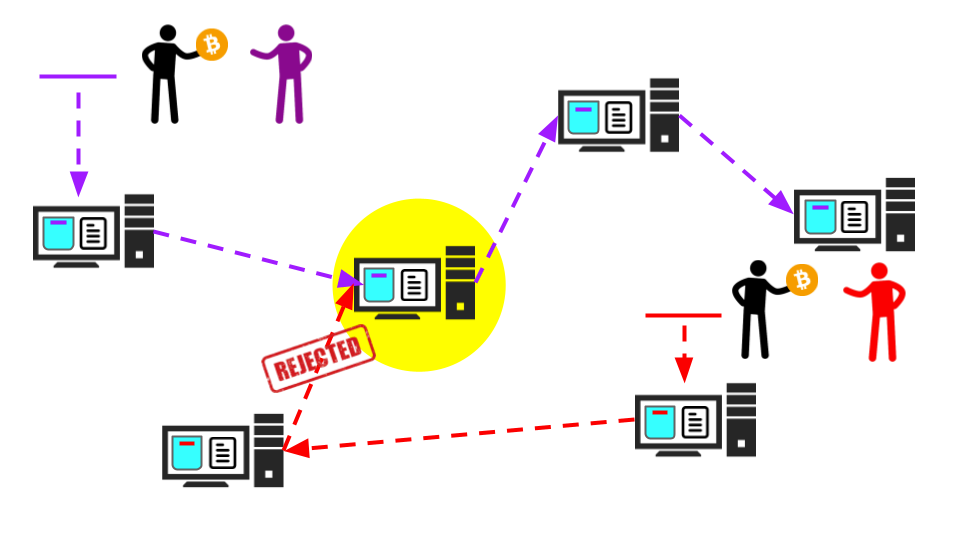
The double-spend problem is a potential issue in digital currency systems, including Bitcoin, where a user attempts to spend the same digital currency more than once.
“When there are multiple double-spent versions of the same transaction, one and only one will become valid.” – Satoshi Nakamoto
Digital objects, like computer files, are easy to duplicate. While this makes digital devices very simple and useful for the average user, costless duplication is not a desirable trait in money. For instance, it would not be desirable to have a monetary system that allowed anyone to duplicate their money at will.
In traditional paper currency or physical cash transactions, double-spending is not a problem. The reason for that is because once a physical currency is handed over, the recipient has the physical money, and the giver cannot spend it again. However, in digital currency systems, it is possible for a user to create a digital copy of their currency and attempt to spend the same currency multiple times.
No single part of Bitcoin can be removed without destroying the whole. Without the blockchain, there wouldn’t be a decentralized way to check for double-spending. Without the block reward halving, the bitcoin supply would expand indefinitely. Without the difficulty adjustment, the mining algorithm wouldn’t have cryptanalytic stability, making it trivial for miners to produce bitcoin more quickly.
To prevent double-spending in Bitcoin, the network uses a distributed ledger, which is the blockchain. When a transaction is initiated, it is broadcasted to all nodes on the network, and miners work to validate and add the transaction to the ledger. Once a transaction is added to the blockchain, it is considered confirmed, and the currency units associated with the transaction are no longer available for spending. If the user attempts to spend the same bitcoin again, the network will reject the transaction, because the transaction’s input has already been spent and recorded on the blockchain. In other words, the blockchain serves as a record of all past transactions, making it impossible to double-spend the same Bitcoin.
While the blockchain is effective in preventing double-spending, it is still possible for a user to attempt to double-spend in a so-called “51% attack,” where a malicious node or group of nodes control more than 51% of the network’s computing power. This gives them the ability to modify the blockchain’s history and double-spend. However, this type of attack is incredibly difficult and costly to execute. For that reason, this is generally not considered a significant risk to the Bitcoin network.
The Bitcoin halving
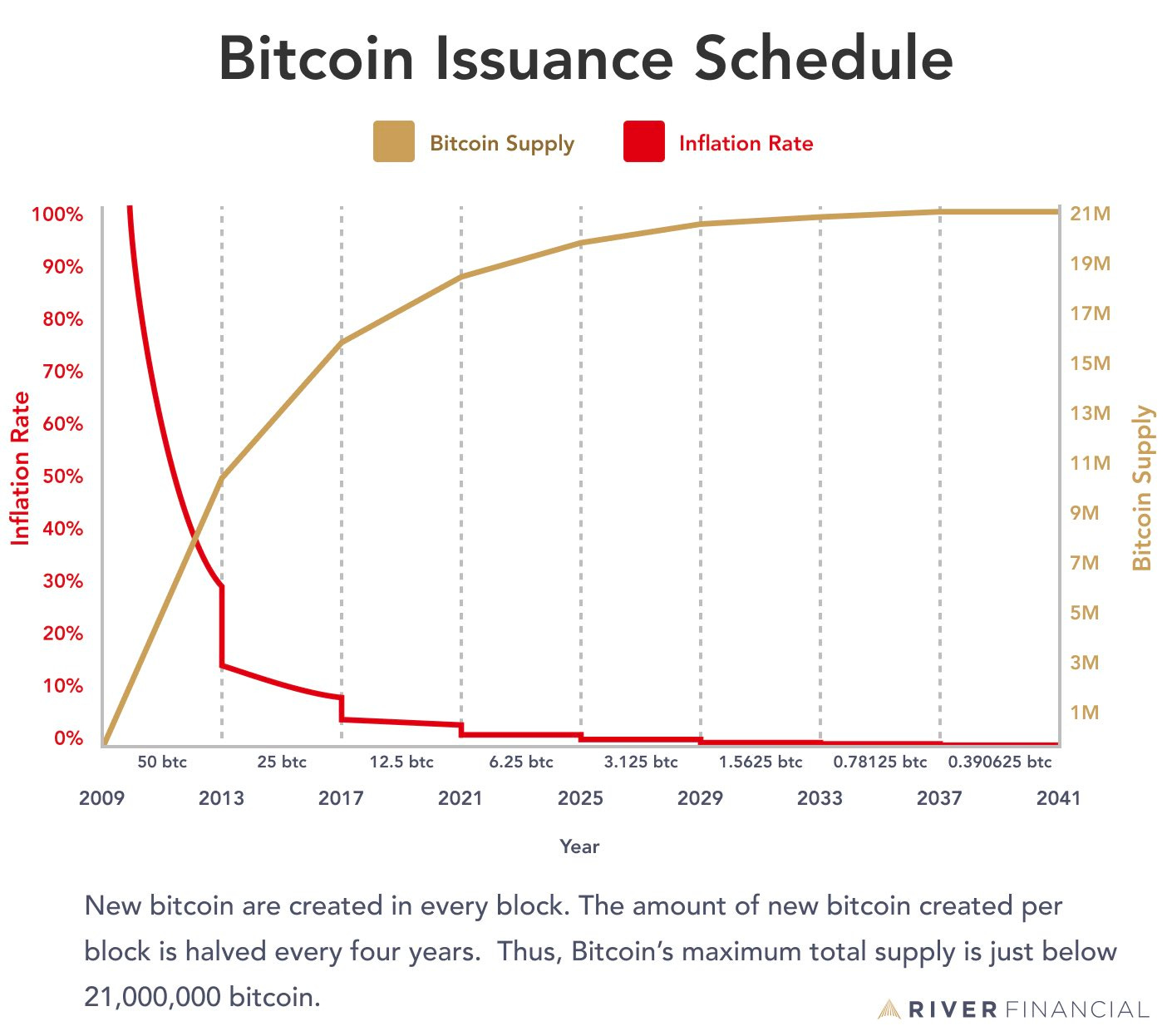
The supply of bitcoin is determined by a low and deterministic inflation rate that trends towards zero over time. This is achieved via an encoded mechanism that halves Bitcoin’s mining rewards roughly every 4 years.
When Bitcoin first launched, the block reward was 50 BTC per block. However, the protocol is designed to cut the block reward in half every 210,000 blocks, which occurs approximately every four years. This way, after 34 halvings, the total supply of bitcoin will cease growing and rest at just below 21 million BTC.
The last new bitcoin will be mined sometime around the year 2140.
How Bitcoin works
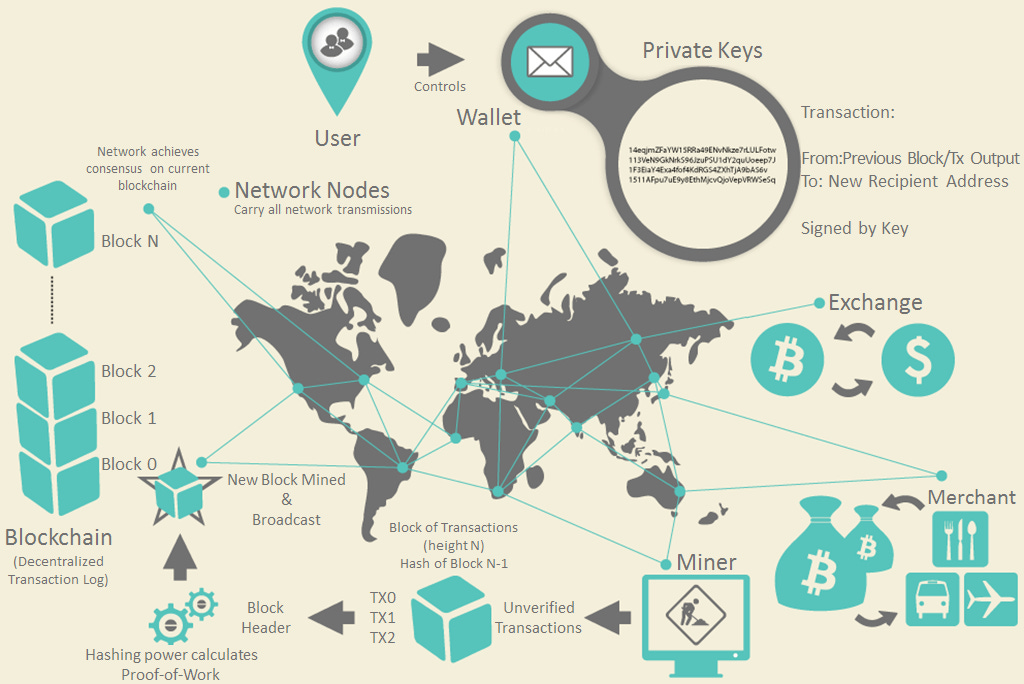
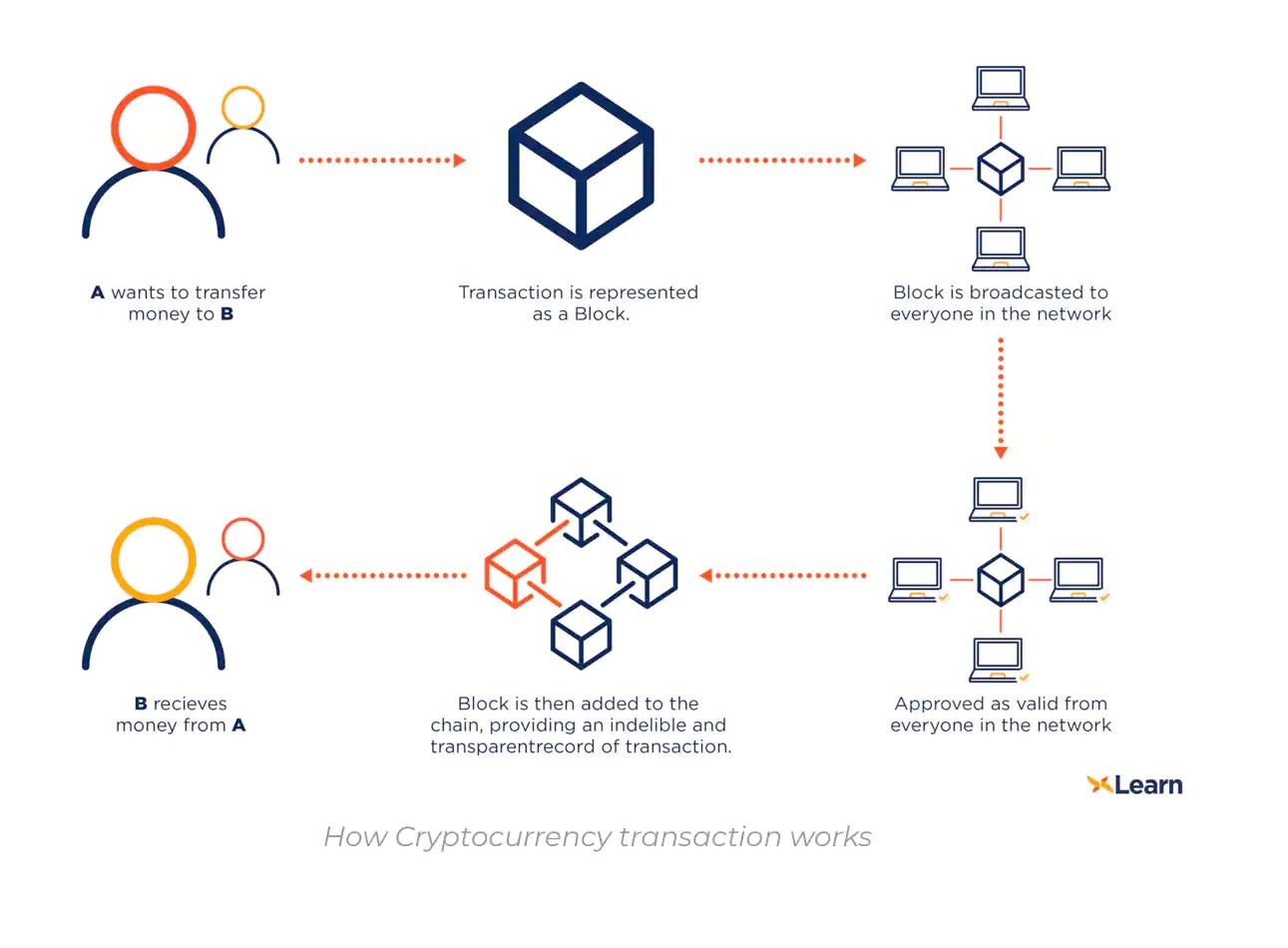
Bitcoin operates using a distributed ledger, the blockchain. The blockchain is a public ledger that records all Bitcoin transactions in chronological order and that is maintained by a network of nodes that validate and confirm transactions.
Once a transaction is confirmed and added to the blockchain, it is considered final and cannot be reversed or altered. This provides a high degree of security and transparency, as all Bitcoin transactions are publicly visible on the blockchain and can be traced back to their origin.
The blockchain
The Bitcoin blockchain is a decentralized, public ledger that records all transactions ever made on the Bitcoin network. It is maintained by a network of computers that run the Bitcoin software and validate transactions by solving complex mathematical puzzles.
Each block in the blockchain contains a record of several transactions that have been verified by the network. Once a block is added to the chain, it cannot be modified or deleted. This means that the entire history of transactions on the Bitcoin network is stored permanently and publicly, making it transparent and immutable.
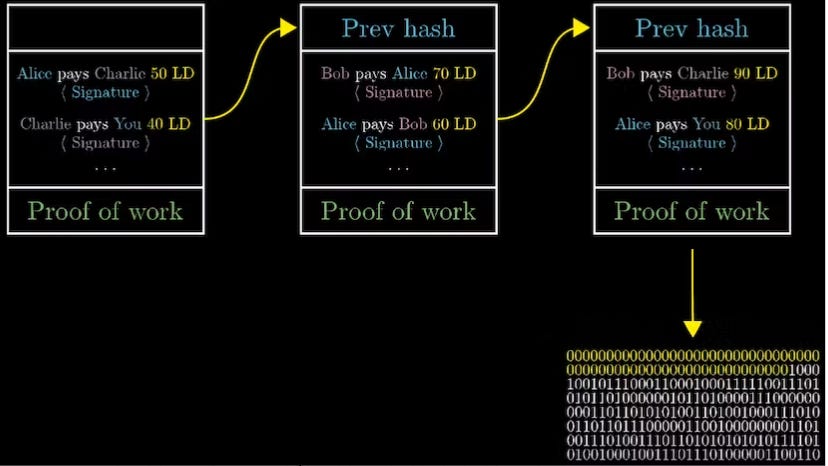
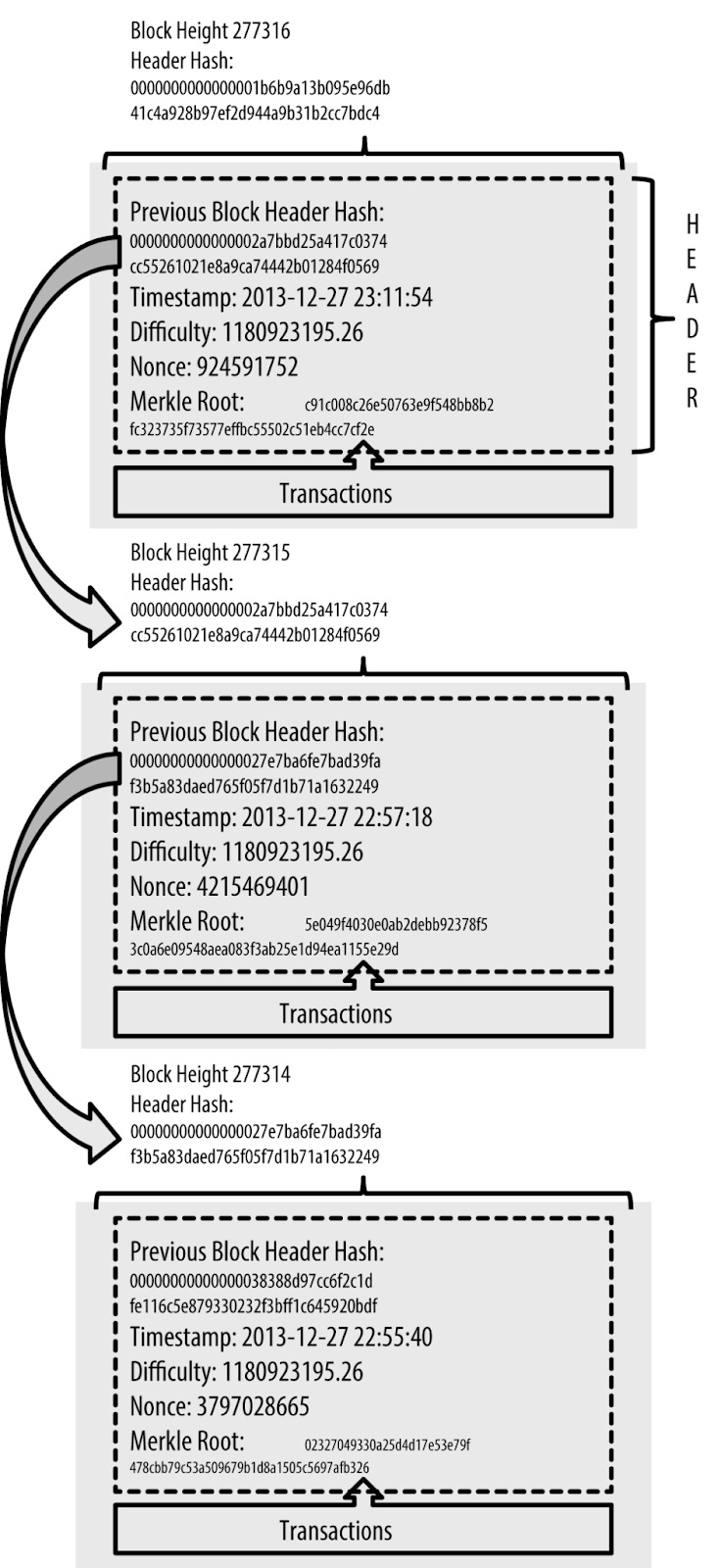
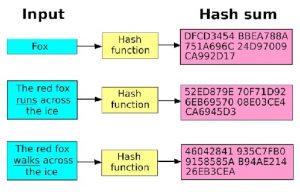
The blockchain acts as a data structure that can be saved as a flat file or database. It is made up of a series of blocks that are linked together using cryptographic hashes. Each block contains a hash (generated using SHA256) of the previous block (known as the parent block), along with a timestamp and a set of transactions.
The hash of each block is unique, and changing any part of a block would require changing the hash of that block as well as all subsequent blocks. This makes it extremely difficult to modify or tamper with the blockchain.
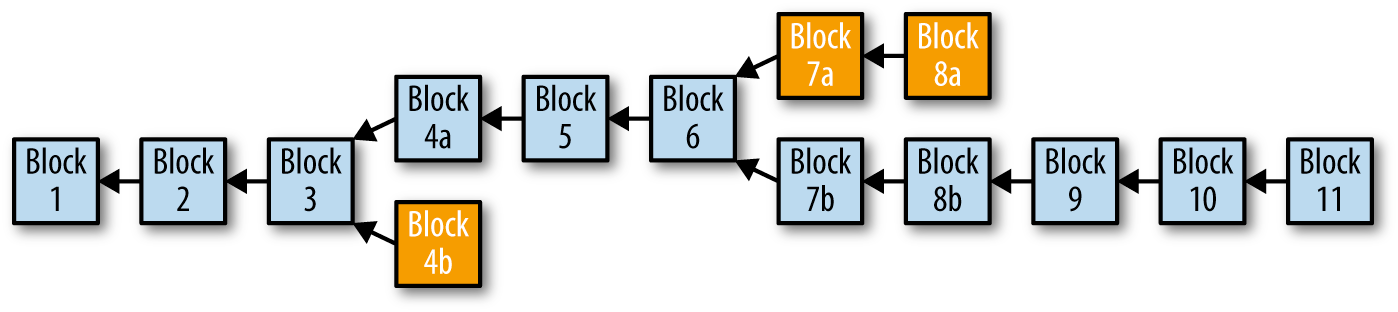
Although a block has just one parent, it can temporarily have multiple children. Each of the children refers to the same block as its parent and contains the same (parent) hash in the “previous block hash” field. Multiple children arise during a blockchain “fork”. This describes a temporary situation that occurs when different blocks are discovered almost simultaneously by different miners. Eventually, only one child block becomes part of the blockchain and the “fork” is resolved (the longest chain wins).
Even though a block may have more than one child, each block can have only one parent. This is because a block has one single “previous block hash” field referencing its single parent.
The structure of a block
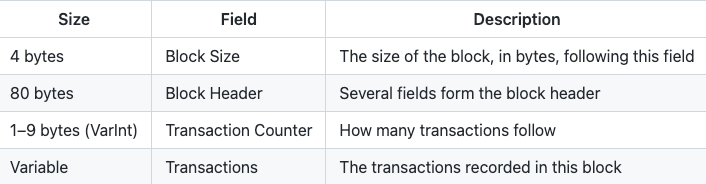
A block is a data structure that aggregates transactions for inclusion in the public ledger. Blocks are made up of a header (containing metadata), followed by a long list of transactions that make up the bulk of its size. The block header is up to 80 bytes in size, while the average transaction is 400 bytes and the average block contains more than 1,900 transactions.
Blocks are mainly identified by either the block hash or the block height.
- The block hash is a digital fingerprint made by hashing the block header twice through the SHA256 algorithm. This results in a 32-byte hash that uniquely identifies a block.
- The block height shows the position of a block in the blockchain. For example, the first block ever created had a height of 0.
The term current block height is also used to indicate the size of the blockchain in blocks at any given time.
The structure of a block header
The block header consists of 3 sets of block metadata:
- Reference to the previous block hash.
- Difficulty, timestamp, and nonce.
- Merkle tree root.
Bitcoin transactions
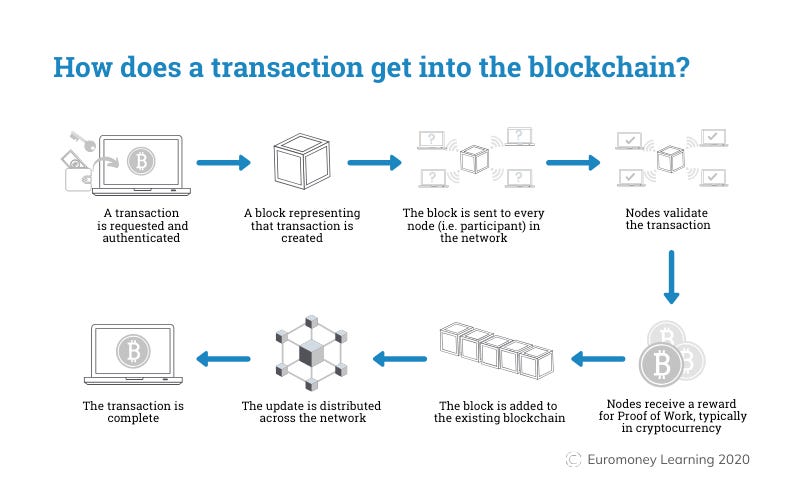
Transactions are the most important part of the Bitcoin system. Everything else is designed to ensure that transactions can be created, propagated, validated, and finally added to the global ledger of transactions (the blockchain).
Bitcoin transactions tell the network that the owner of some bitcoin value has authorized the transfer of that value to another owner. The new owner can now spend the bitcoin by creating another transaction that authorizes the transfer to another owner, and so on, in a chain of ownership.
In Bitcoin, a transaction input is a reference to a previous unspent output (UTXO) that a user wants to spend. In other words, the input of a transaction is the source of the funds that the user wants to use in the transaction. To spend those funds, the user must provide a valid digital signature that proves they are the rightful owner of the UTXO (Unspent transaction output).
“A block header with no transactions would be about 80 bytes. If we suppose blocks are generated every 10 minutes, 80 bytes * 6 * 24 * 365 = 4.2MB per year. With computer systems typically selling with 2GB of RAM as of 2008, and Moore’s Law predicting current growth of 1.2GB per year, storage should not be a problem even if the block headers must be kept in memory.” – Satoshi Nakamoto
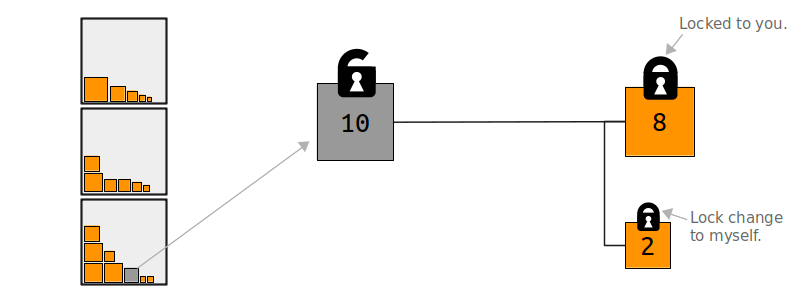
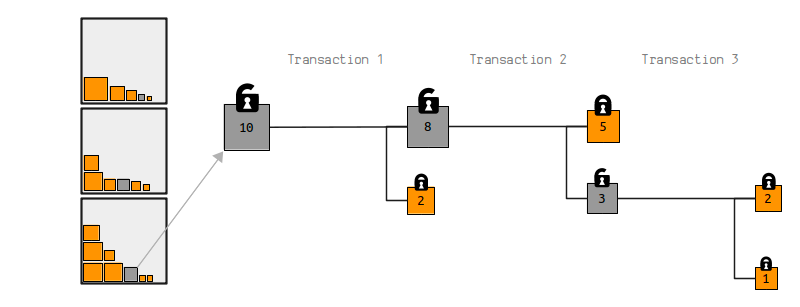
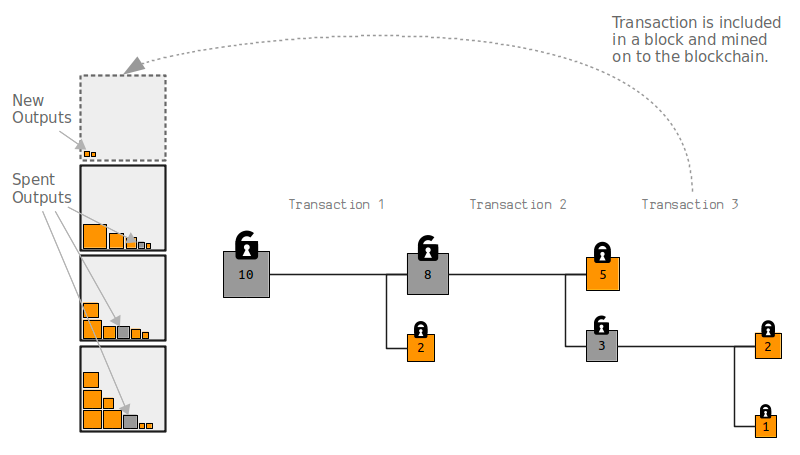
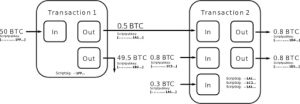
One analogy for thinking about blockchains is that they are a storage facility for safe deposit boxes. These deposit boxes are called outputs, which are just containers that hold various amounts of bitcoin. When you make a Bitcoin transaction, you are selecting some outputs and unlocking them, then creating new outputs and putting new locks on them.
Following this analogy, when you are sending bitcoins to someone, you are actually placing an amount of bitcoins into a new safe deposit box, and putting a lock on it so that only the person that you are sending the bitcoins to can unlock it.
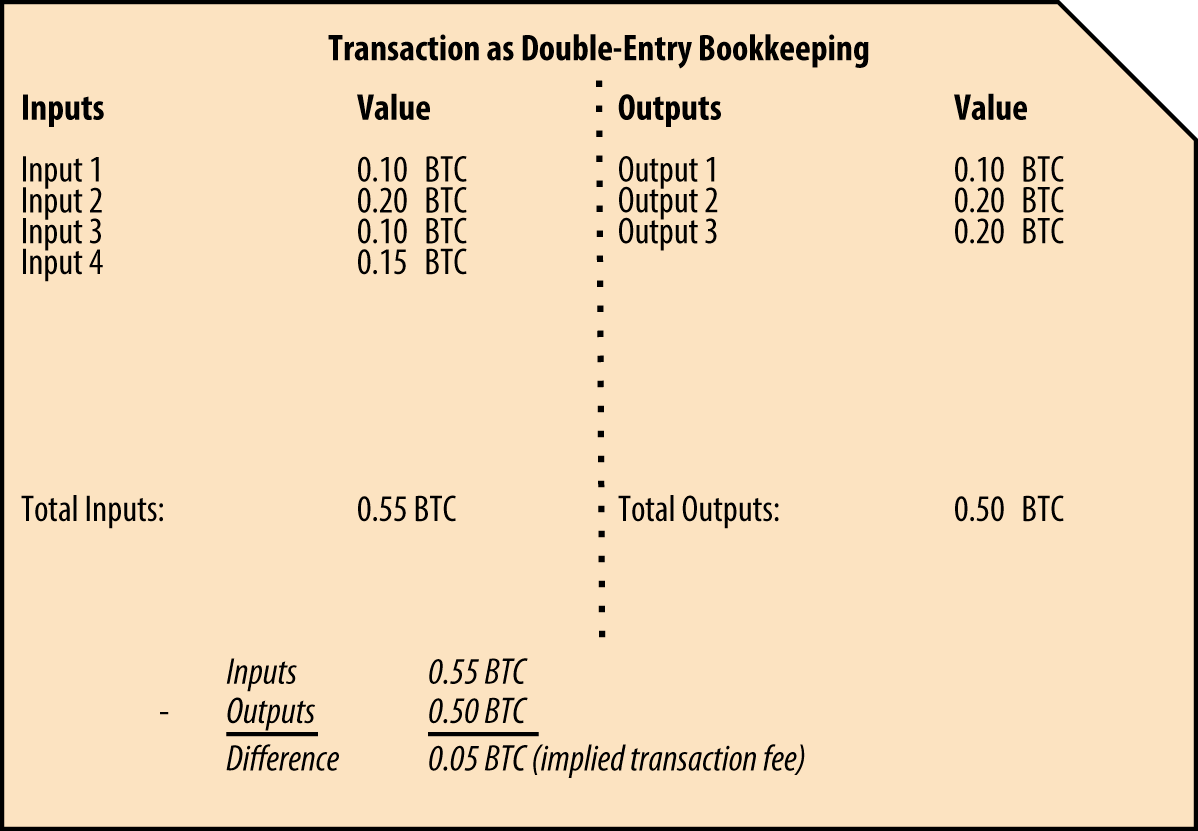
When a transaction is created, it typically has one or more inputs and one or more outputs. Each output specifies the destination address and the amount of bitcoins to be sent to that address. The total value of the inputs must be equal to or greater than the total value of the outputs, otherwise, the transaction will be rejected by the network.
“Bitcoin addresses you generate are kept forever. A Bitcoin address must be kept to show ownership of anything sent to it. If you were able to delete a Bitcoin address and someone sent to it, the money would be lost. They’re only about 500 bytes.” – Satoshi Nakamoto
When the transaction is broadcast to the network, it is validated and confirmed by miners who add it to the blockchain. Once confirmed, the transaction outputs become new UTXOs that can be used as inputs in future transactions.
In some cases, a transaction may include an output that references both an address of the new owner and the address of the current owner. This is typically done for two reasons:
- To send change back to the current owner. When a user spends a UTXO that is larger than the desired amount they want to send, they can create an output that sends the remaining value back to one of their own addresses. This is known as the “change output”.
If you spend $5 in a store but use a $20 bill to pay for the item, you expect to receive $15 in change. The same concept applies to bitcoin transaction inputs. If you purchased an item that costs 5 bitcoin but only had a 20 bitcoin input to use, your wallet would create a single transaction that sends two outputs, one output of 5 bitcoin to the store owner and one output of 15 bitcoin back to yourself as change (less any applicable transaction fee).
The change address does not have to be the same address as that of the input and for privacy reasons is often a new address from the owner’s wallet.
Finally, when a transaction gets mined on to the blockchain, the outputs that were used up (spent) cannot be used in another transactions, and the newly created outputs will be available to be moved on in a future transaction.
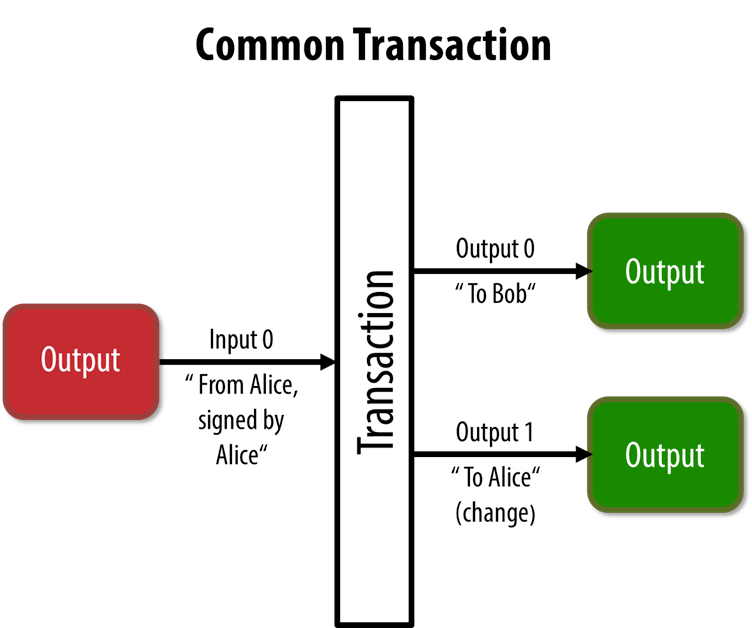
The most common form of a transaction is a simple payment from one address to another, which often includes some “change” returned to the original owner. This type of transaction has one input and two outputs.
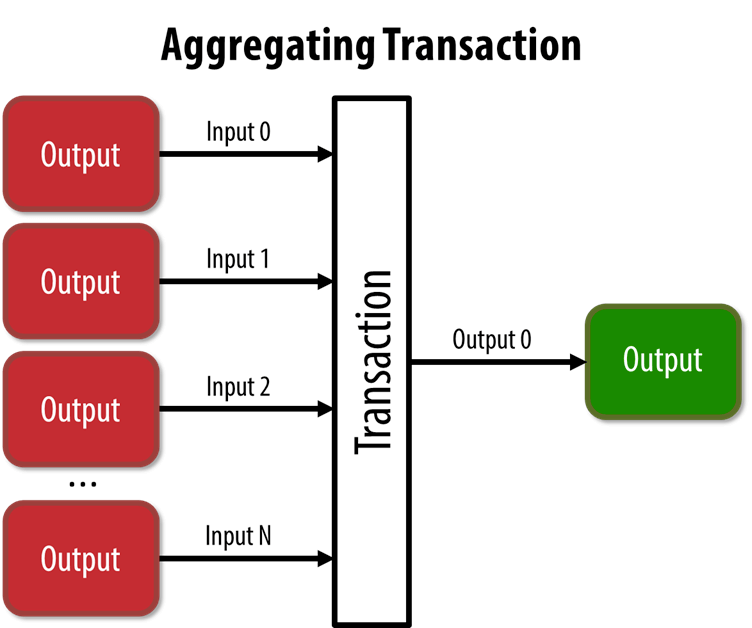
- To consolidate UTXOs. Over time, users may accumulate many small UTXOs in their wallet from previous transactions. This can make it difficult and time-consuming to manage their UTXOs, especially if they want to spend them in a single transaction. To simplify this process, users can create a transaction that includes multiple inputs (i.e., references to multiple UTXOs) and one or more outputs that consolidate the UTXOs into a smaller number of larger UTXOs.
This represents the real-world equivalent of exchanging a pile of coins and currency notes for a single larger note.
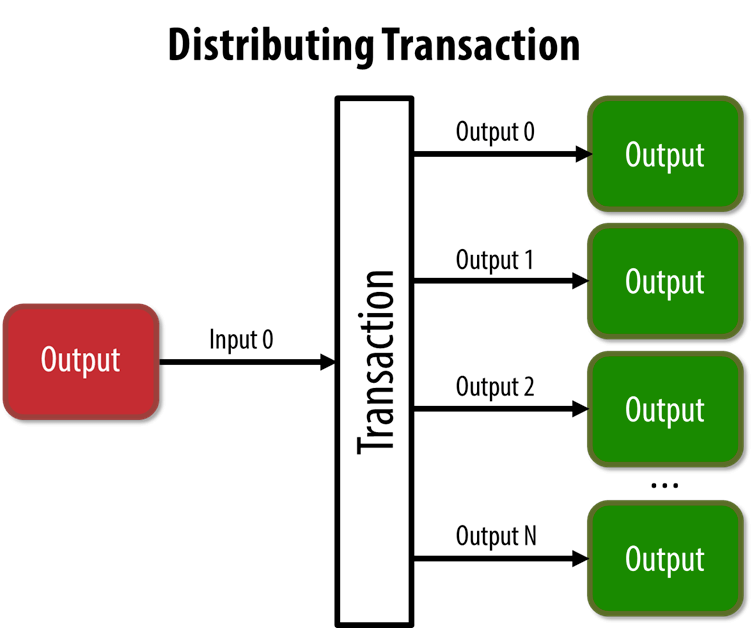
Another common form of transaction is a batched transaction that distributes one input to multiple outputs. This is helpful for saving transaction funds or distributing funds to multiple recipients.
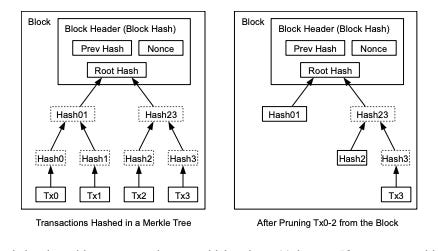
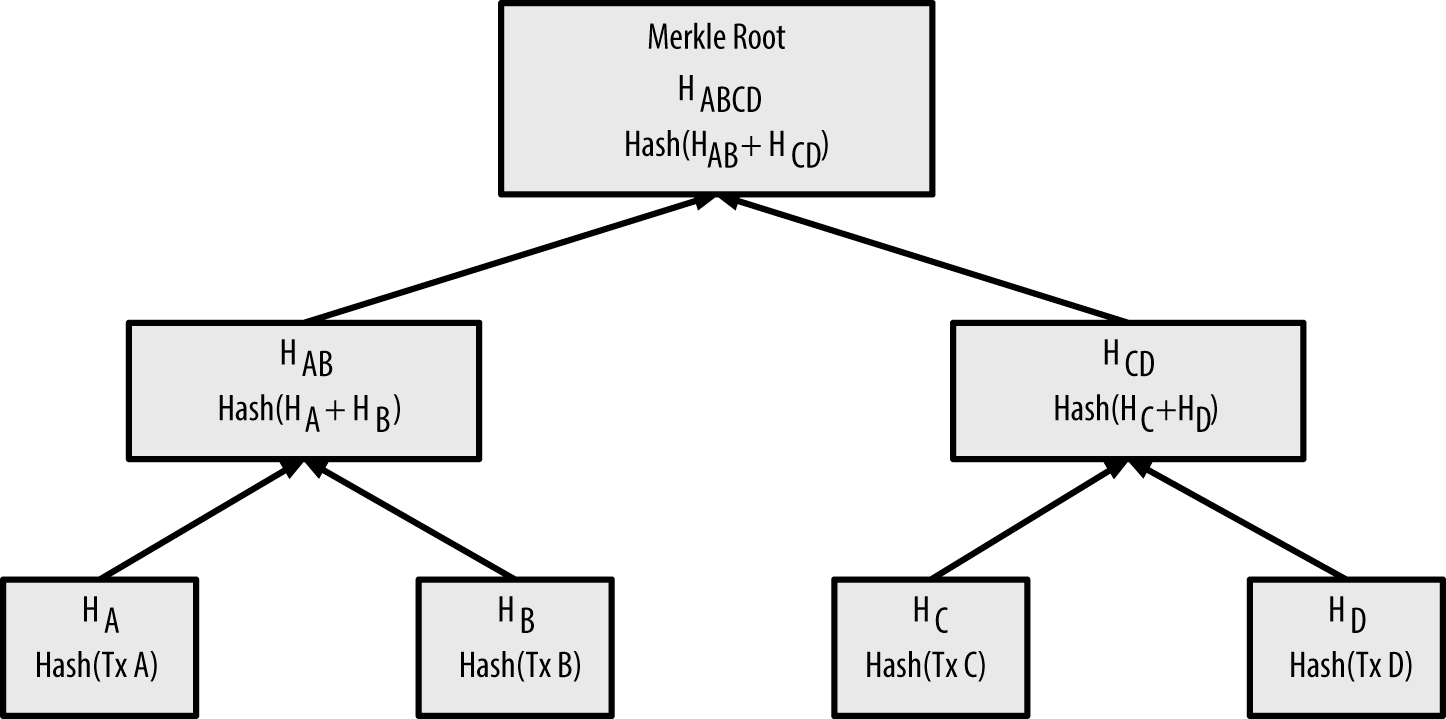
Each block in the blockchain contains a summary of all transactions in the block in a data structure called merkle tree, which serves the purpose of verifying and summarizing the integrity of large data sets with a series of cryptographic hashes.
A Merkle tree is a data structure in which each leaf node represents a single piece of data, in this case, a transaction. The non-leaf nodes represent a hash of the data in their child nodes. The root of the tree, also known as the Merkle root, is a hash of the hash values of all the transactions in the block.
By including the Merkle root in the block header, Bitcoin nodes can efficiently verify that a transaction is included in a block without having to download and validate all the transactions in the block. This is known as a Merkle proof. The Merkle proof only requires the branch of the Merkle tree that contains the transaction, the Merkle root of the block, and the intermediate hashes on the path from the transaction to the Merkle root.
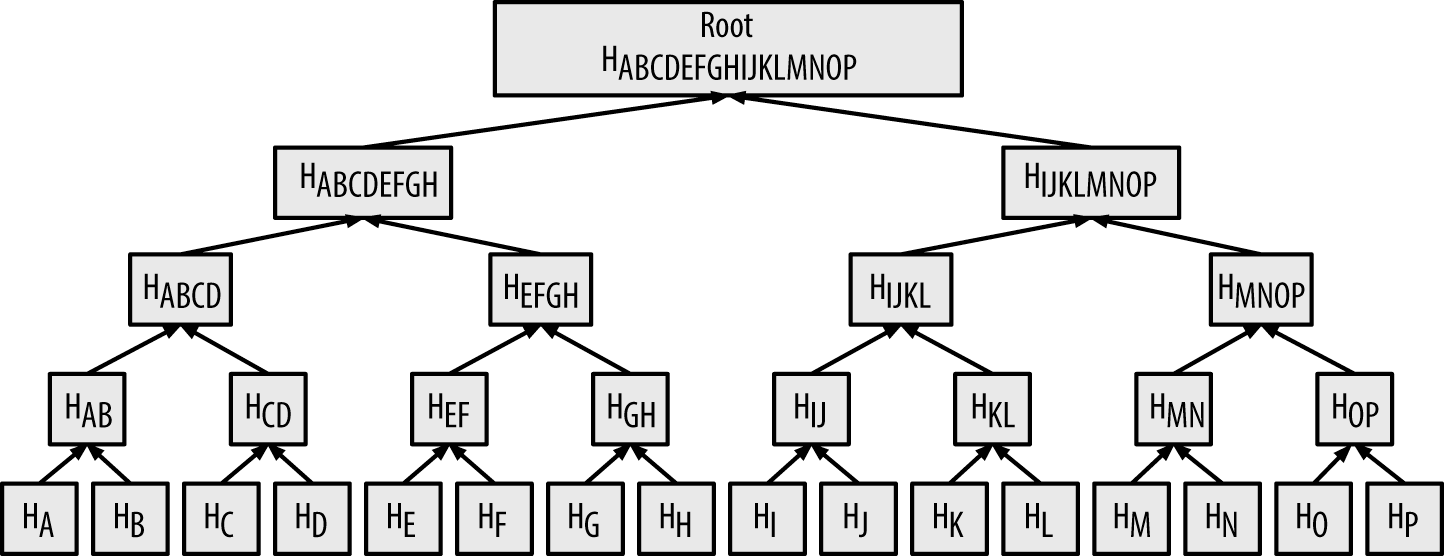
In Bitcoin, it is common to have several hundreds to more than a thousand transactions in a single block, which are summarized by producing just 32 bytes of data as the single merkle root.
To prove that a specific transaction is included in a block, a node only needs to produce log~2~(N) 32-byte hashes, constituting an authentication path or merkle path that connects the specific transaction to the root of the tree.
This is especially important as the number of transactions increases, because the base-2 logarithm of the number of transactions increases much more slowly.
Bitcoin mining
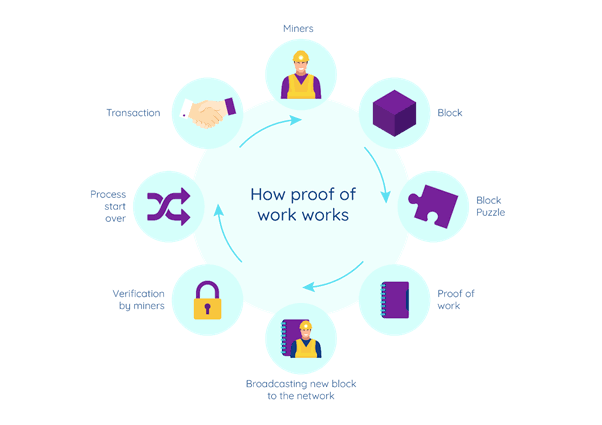
Bitcoin mining is the process of adding new transactions to the Bitcoin blockchain by solving complex mathematical equations. Miners compete to solve these equations, and the first miner to solve the equation and validate the transaction is rewarded with a certain amount of new bitcoins.
The purpose of mining is not the creation of new bitcoin. That’s the incentive system. Mining is the mechanism by which bitcoin’s security is decentralized.
The mathematical equations that miners solve are called “hashes”, and they are created by taking the transaction data and running it through a cryptographic algorithm called SHA-256. Miners do this using specialized computer hardware known as Application-Specific Integrated Circuits (ASICs) that allow them to perform these calculations at a high speed.
In other words, PoW is the bridge between the digital & the physical.
When a miner successfully solves a hash, they create a new block of transactions and add it to the existing blockchain. This block is then verified by other nodes on the network, and if it is found to be valid, it is added to the blockchain and the miner is rewarded with a certain number of new bitcoins as well as any transaction fees associated with the transactions in the block.
Under the hood, PoW mining converts kinetic energy (electricity) into a ledger block. A mining machine repeatedly performs hash operations until it solves a cryptographic puzzle. All hash operations are thrown away except for the one hash that solves it. This one hash, which itself takes very little energy to compute, is a direct representation of the huge ball of energy that was required to produce it. This is the “proof” that the block was minted. In order to rewrite the block, an attacker later would be forced to spend a roughly equivalent number of hash operations as all the hash operations that were originally required.
Satoshi realized that the only real-world asset that can be linked to a computer system in a trustless manner is energy. Everything else, whether it is gold, paper certificates, real estate… introduces a trusted third party because of the inherent disconnect between the digital and the physical world.
Proof of Work is an attempt to solve the oracle problem. By using energy and physics as the base truth, there is no need to make sure that digital and the real-world physical representation of assets remains up-to-date and in sync.
Reverting takes an equivalent number of hash operations, not an equivalent amount of energy. That is because the hash is only a representation of the energy used, not the energy itself. Over time, this representation of energy becomes less & less accurate — as improved hardware becomes more efficient.
The mining process is designed to be difficult and resource-intensive in order to prevent fraudulent activity and ensure the security of the Bitcoin network. The difficulty of the mining process is adjusted regularly by the network to ensure that blocks are added to the blockchain at a consistent rate of approximately one every 10 minutes.
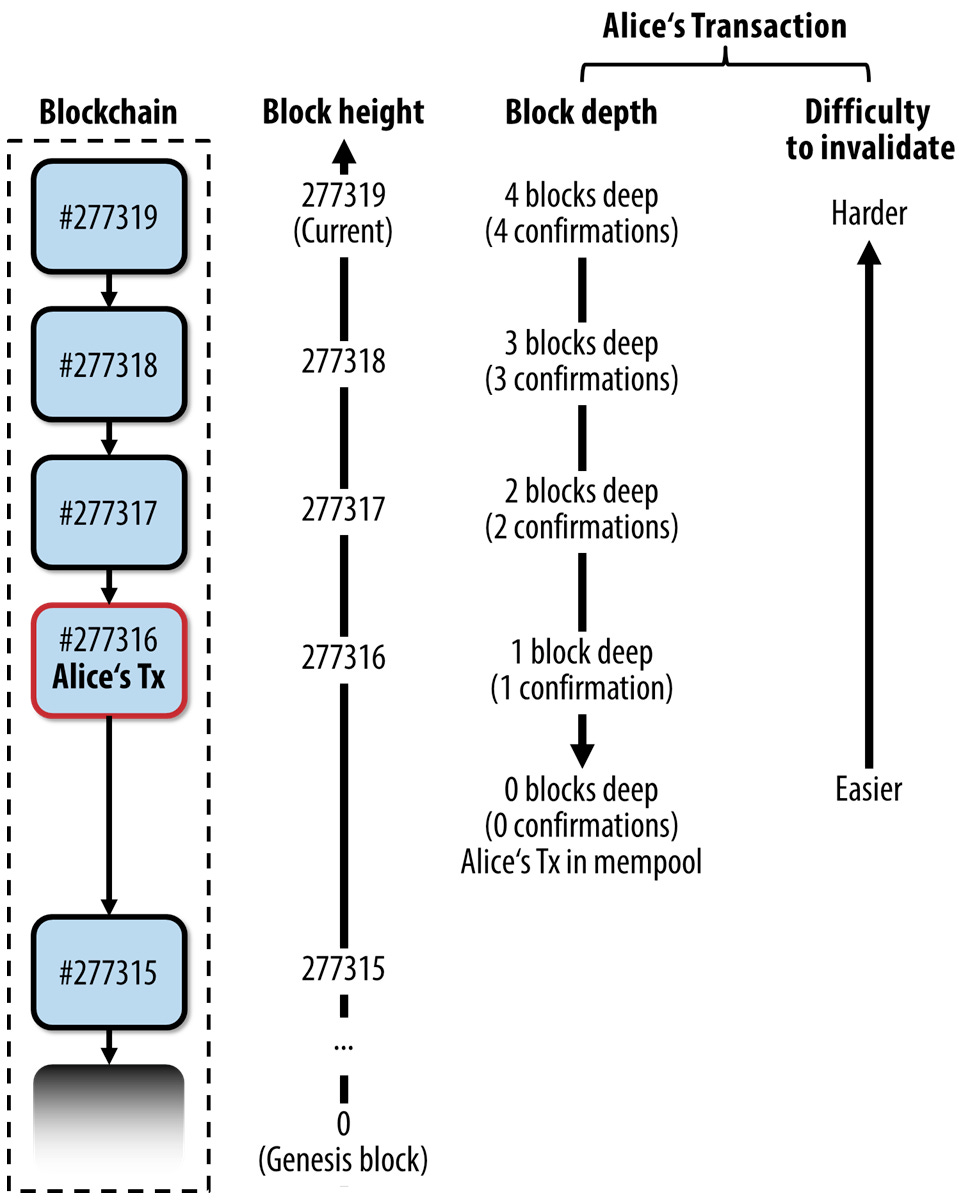
Miners are responsible for validating transactions and including them on the global ledger. On average, a new block is validated every 10 minutes. When these transactions become part of a block that has been added to the blockchain, they are said to be “confirmed”.
However, since different nodes may have different versions of the blockchain, it’s possible for multiple blocks to be mined simultaneously, each containing a different set of transactions. In this case, the network follows the longest chain, which is the chain containing the most proof of work.
The number of confirmations a transaction has refers to the number of blocks added to the blockchain after the block containing that transaction. Each additional block added to the chain after the transaction increases the level of security and decreases the risk of a transaction being reversed or double-spent.
In general, six confirmations are considered sufficient to ensure that a transaction is final and irreversible, although some merchants and exchanges may require more or less depending on their risk tolerance.
Transaction pools
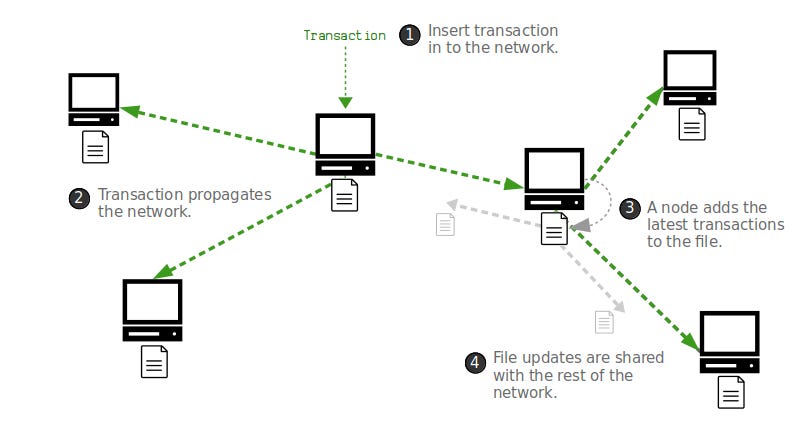
The transaction pool or mempool is a collection of unconfirmed Bitcoin transactions that have been broadcast to the network and that are waiting to be included in a block by a miner.
When a Bitcoin transaction is created and broadcast to the network, it is relayed between nodes until it reaches a miner who will include it in a block. Before the transaction can be included in a block by a miner, it needs to be validated to ensure that it follows the rules of consensus. When this happens, the miner can include it in the next block it mines. However, if the transaction is invalid (insufficient fees, double-spend…), the miner will reject the transaction and it will remain in the mempool until it is either updated and rebroadcasted, or eventually dropped.
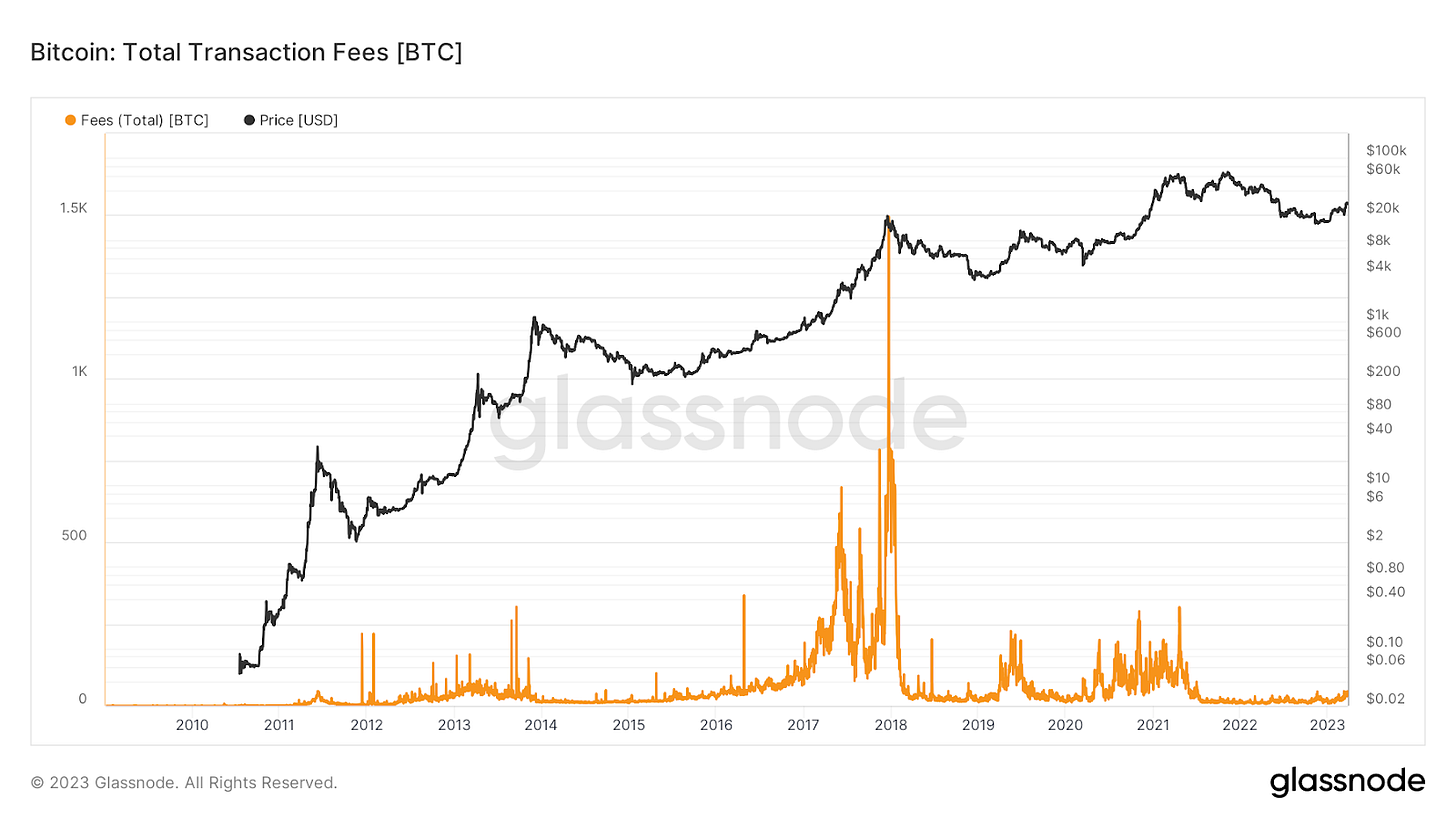
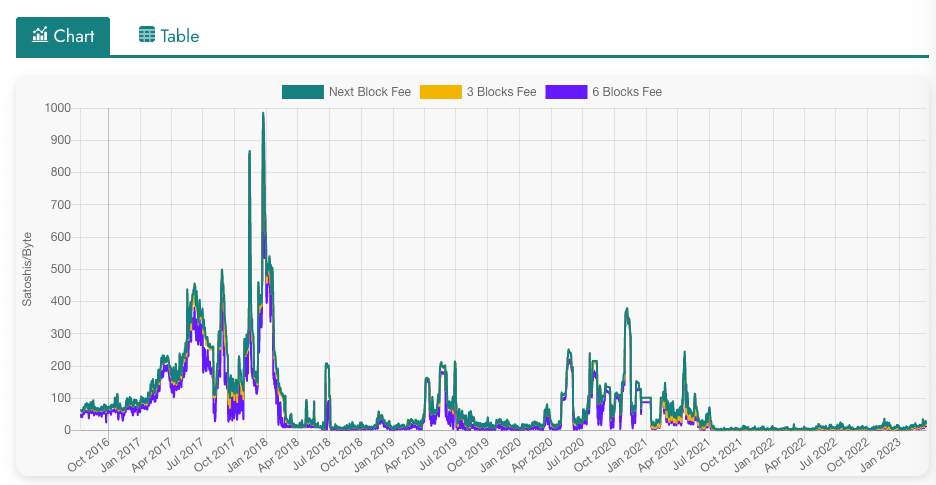
Since the size of each block is limited, not all transactions can be included in the next block. Therefore, transactions that pay higher fees are more likely to be included in the next block, as miners have an incentive to prioritize transactions that offer a higher fee per byte. This competition for block space can lead to temporary spikes in transaction fees during times of high network usage.
Bitcoin core – The reference implementation
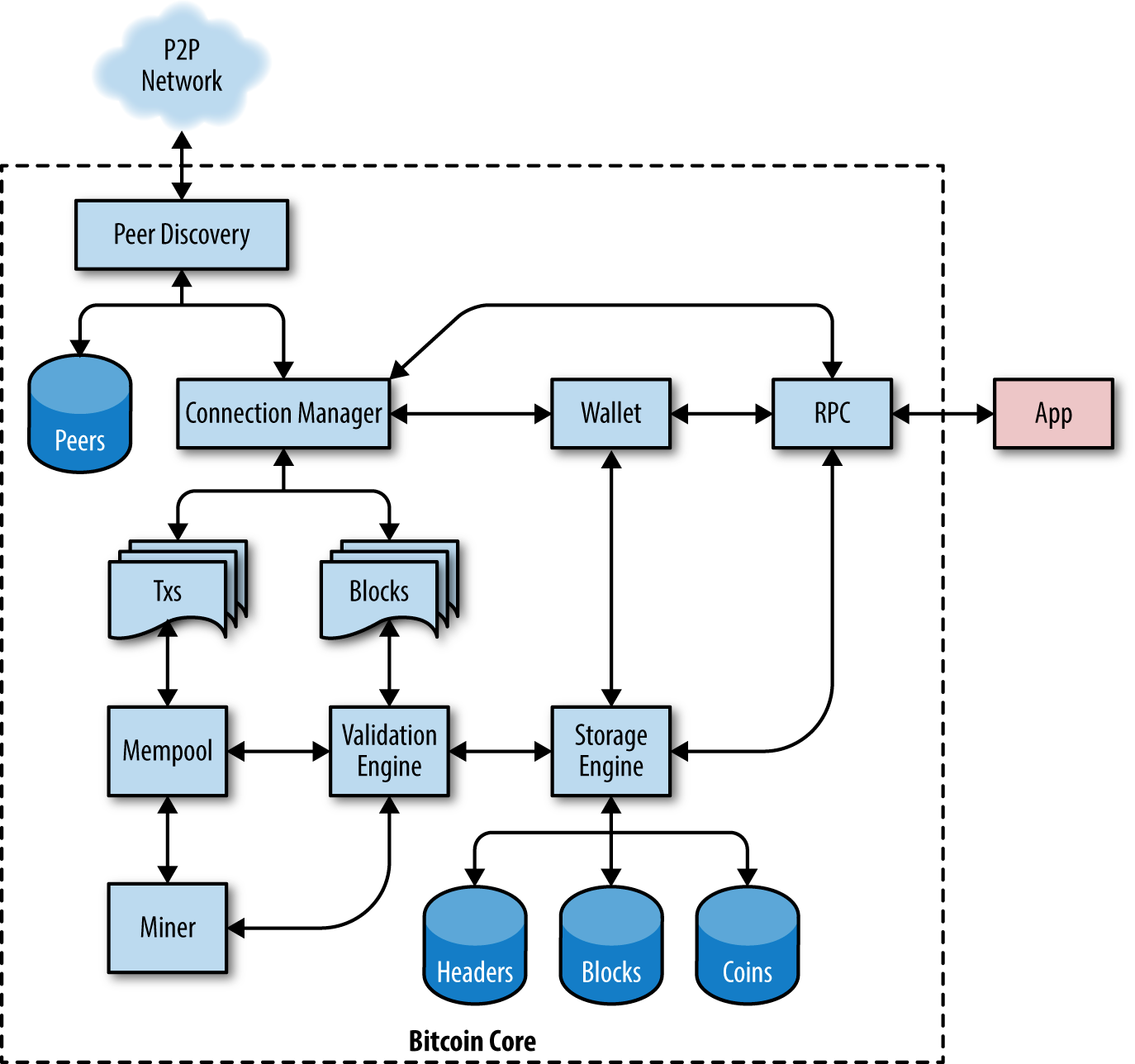
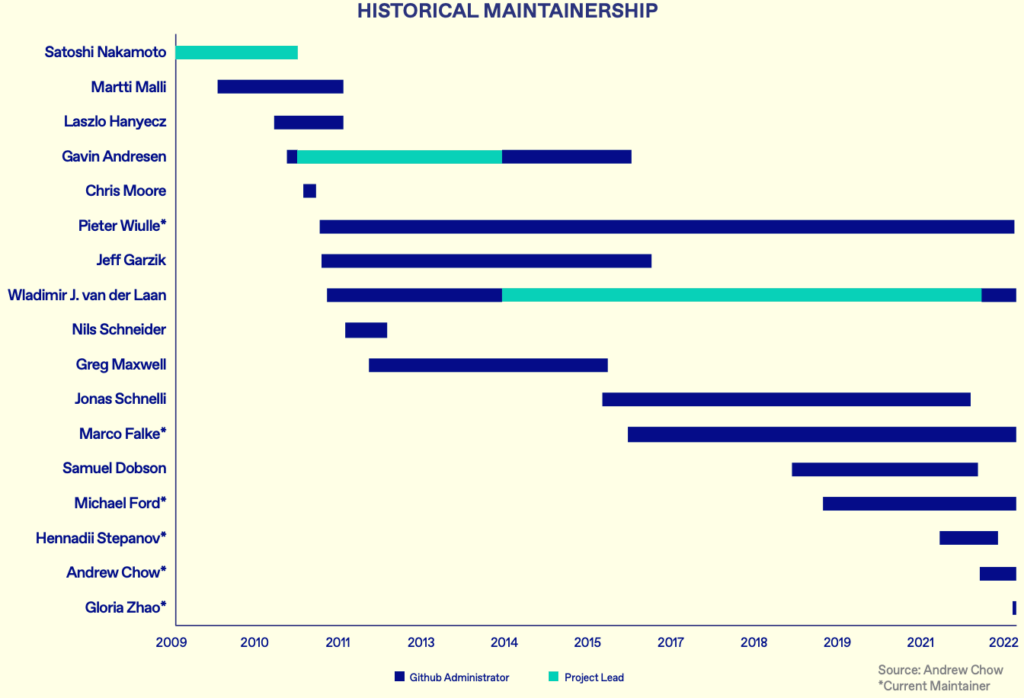
Bitcoin Core is the open-source software that powers the Bitcoin network. It is maintained by a group of developers and is designed to be a full node implementation of the Bitcoin protocol, meaning that it stores a full copy of the blockchain and can independently verify all transactions on the network.
Rather than a focal point of command and control for the development of Bitcoin, the Bitcoin core repository is the technical communication platform.
- In early 2009 the source code for the Bitcoin project was simply a .rar file hosted on SourceForge. Early developers would exchange code patches with Satoshi via email.
- On October 30 2009, Sirius (Martti Malmi) created a subversion repository for the Bitcoin project on SourceForge.
- In 2011, the Bitcoin project migrated from SourceForge to GitHub.
- In 2014 the Bitcoin project was renamed to Bitcoin Core.
From an adversarial perspective, GitHub can not be trusted. Any number of GitHub employees could use their administrative privileges to inject code into the repository without consent from the maintainers. However, Bitcoin Core has a continuous integration system that performs checks of trusted PGP keys that must sign every merge commit. This makes it unlikely that a GitHub attacker would also be able to compromise the PGP key of a Bitcoin Core maintainer.
All upgrades proposed by Bitcoin Core developers are peer-reviewed to ensure that they conform with the ethos of Bitcoin and are free of bugs. Once these requests are reviewed, maintainers implement them on the Bitcoin Core repository.
There are no barriers to entry and anyone can become a Bitcoin Core contributor. Anyone can get started by offering code, reviews of code, or other types of contributions such as text translations.
Who funds Bitcoin Core development?
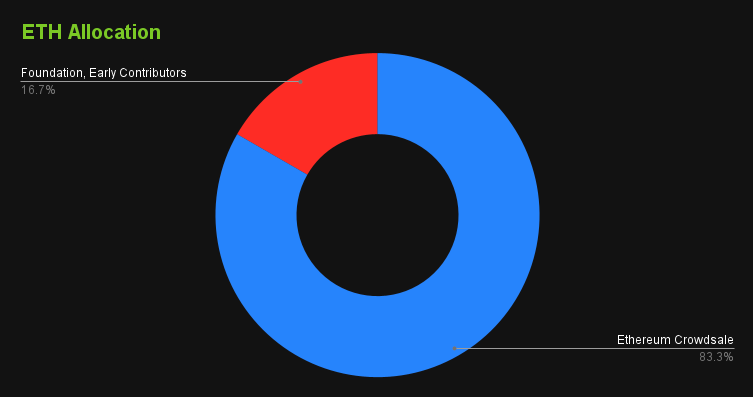
Contrary to Ethereum, Bitcoin did not raise a crowdsale. Its infrastructure and open source software signals that the protocol should be neutral and that its development should be entirely financed by for-profit or government entities.
While the core developers of Bitcoin are volunteers, there are also companies and organizations that support Bitcoin development financially. These companies and organizations may donate funds to support specific development initiatives, provide funding for conferences and events, or offer other forms of support to the development community.
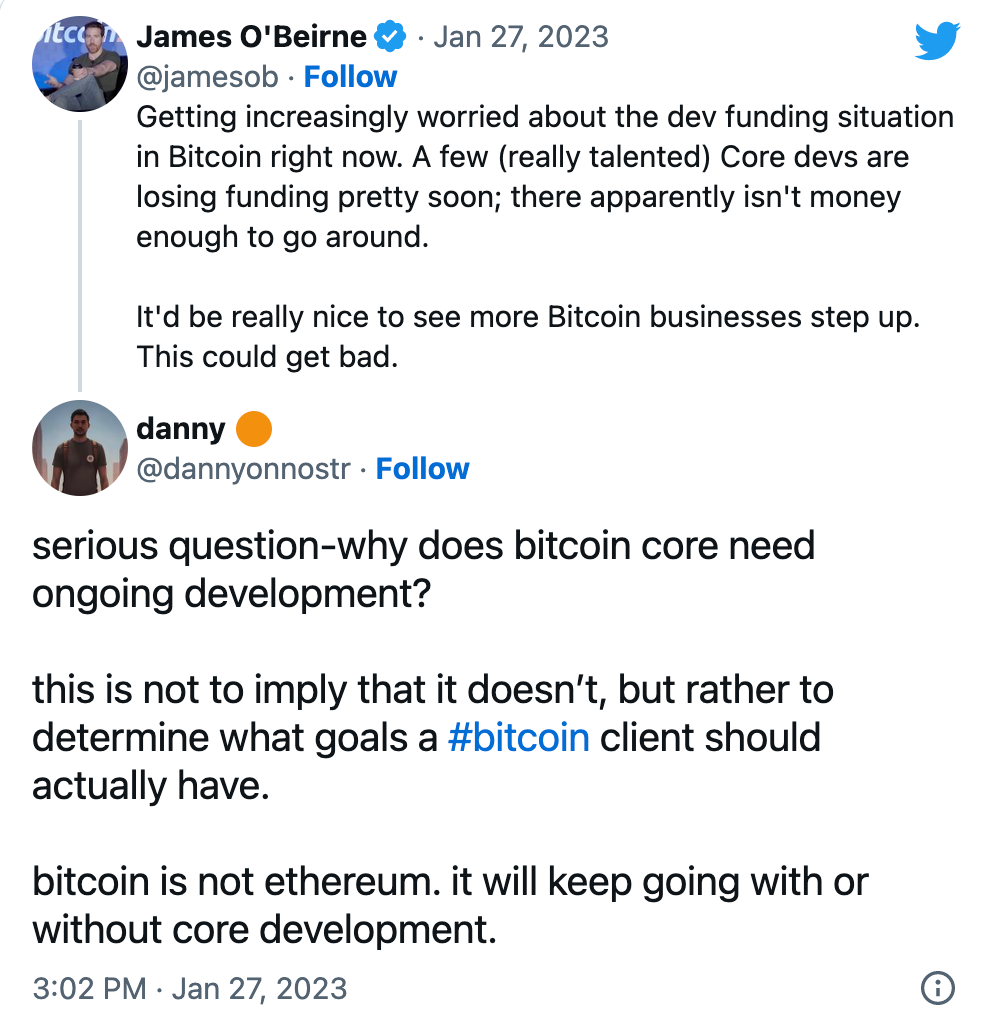
In January 2023, Bitcoin developer James O’Beirne sounded the alarm about the importance of funding open-source efforts.
When the Bitcoin Foundation launched, a grants program funded developers based on an annual budget during 2012 and 2014.
In 2014, some of the Bitcoin developers founded a venture-backed for-profit company called Blockstream, whose developers and employees made significant contributions to Bitcoin’s open source code. In that same year, Chaincode Labs was co-founded by Alex Morcos and Suhas Daftuar as a non-profit Bitcoin research and development center. MIT’s DCI (Digital Currency Initiative) also was a significant contributor.
Moving forward to 2019, the diversity of funding sources improved significantly, with businesses and centralized exchanges starting to be more active.
Some of the companies and organizations that have provided financial support for Bitcoin development include the Bitcoin Foundation, Blockstream, Chaincode Labs, Bitmain, the Human Rights Foundation (HRF) and many others. For instance, Brink was founded in 2020 with the goal of supporting Bitcoin protocol development and the organization runs a year-long fellowship program as well as a developer grant problem. Since then, it has joined Chaincode and the MIT DCI as the major funders.
These organizations may have a vested interest in the success of Bitcoin and its ecosystem. For them, providing financial support for development is seen as a way to contribute to the growth and sustainability of the project.
Assuming 1,000 developers receiving Google’s average $150,000 to $200,000 annual compensation, about $150M to $200M would be required every year to fund development in the entire Bitcoin ecosystem.
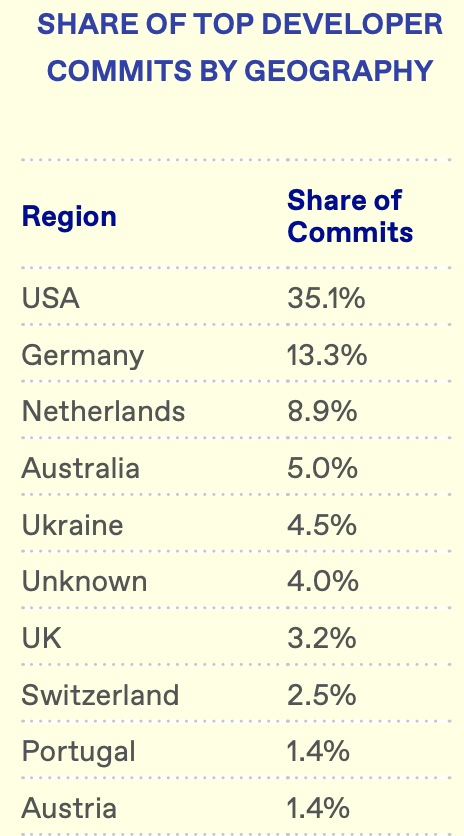
According to a report by New York Digital Investment Group (NYDG), a Bitcoin-focused investment firm, the ongoing maintenance work is being carried out by roughly 40 to 60 active developers every month.
The majority of development work is focused on maintenance and small bug fixes, rather than software upgrades such as Taproot, which are more infrequent but resource-heavy.
With an estimated cost of $200M per year to keep Bitcoin’s code maintained and functioning, the community is worried that the future of Bitcoin’s development is excessively reliant on donations.
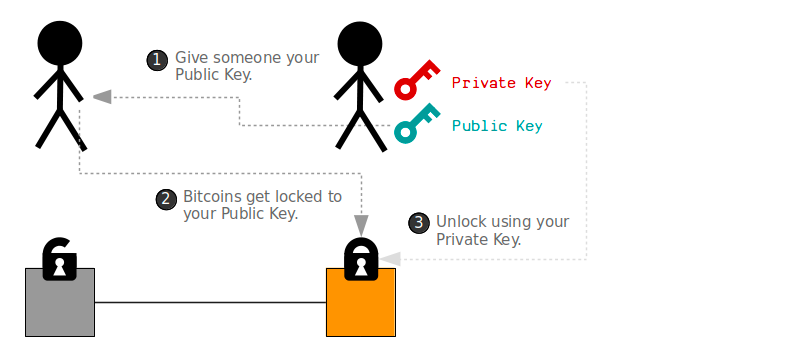
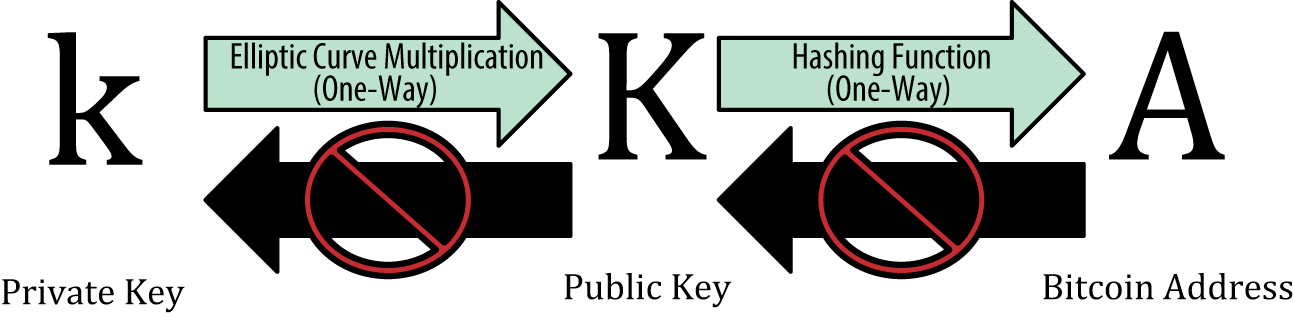
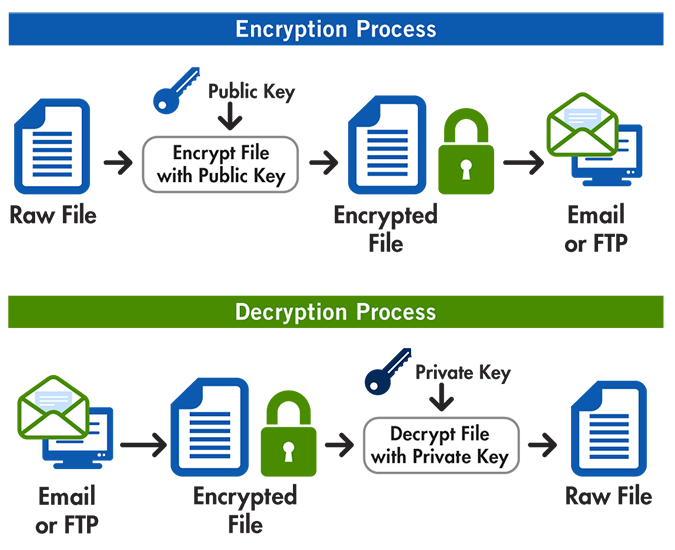
Public-key cryptography
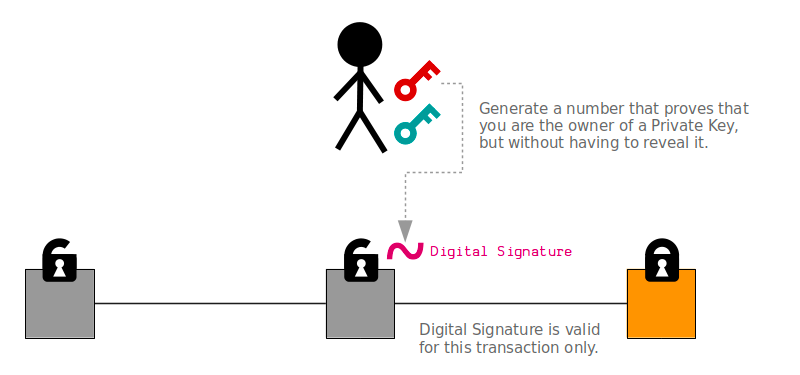
Public key cryptography is a key component of the Bitcoin protocol. It allows users to securely send and receive bitcoins without the need for a trusted third party.
In the context of Bitcoin, each user has a public key and a private key. The public key is a unique identifier that is publicly known and can be used to receive bitcoins, while the private key is a secret that is known only to the owner and is used to sign transactions that spend those bitcoins.
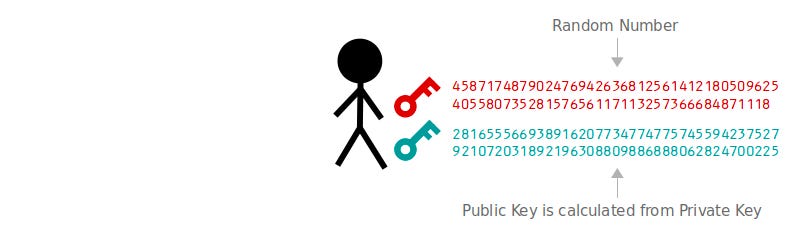
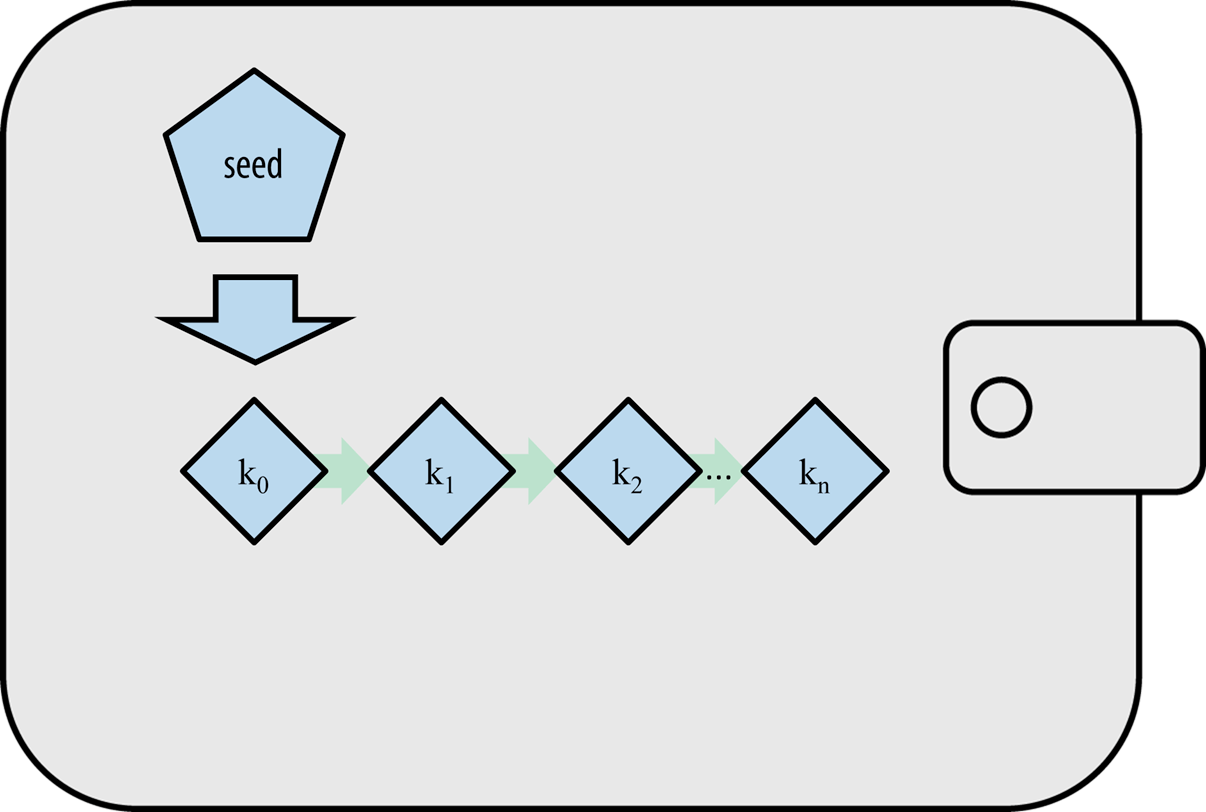
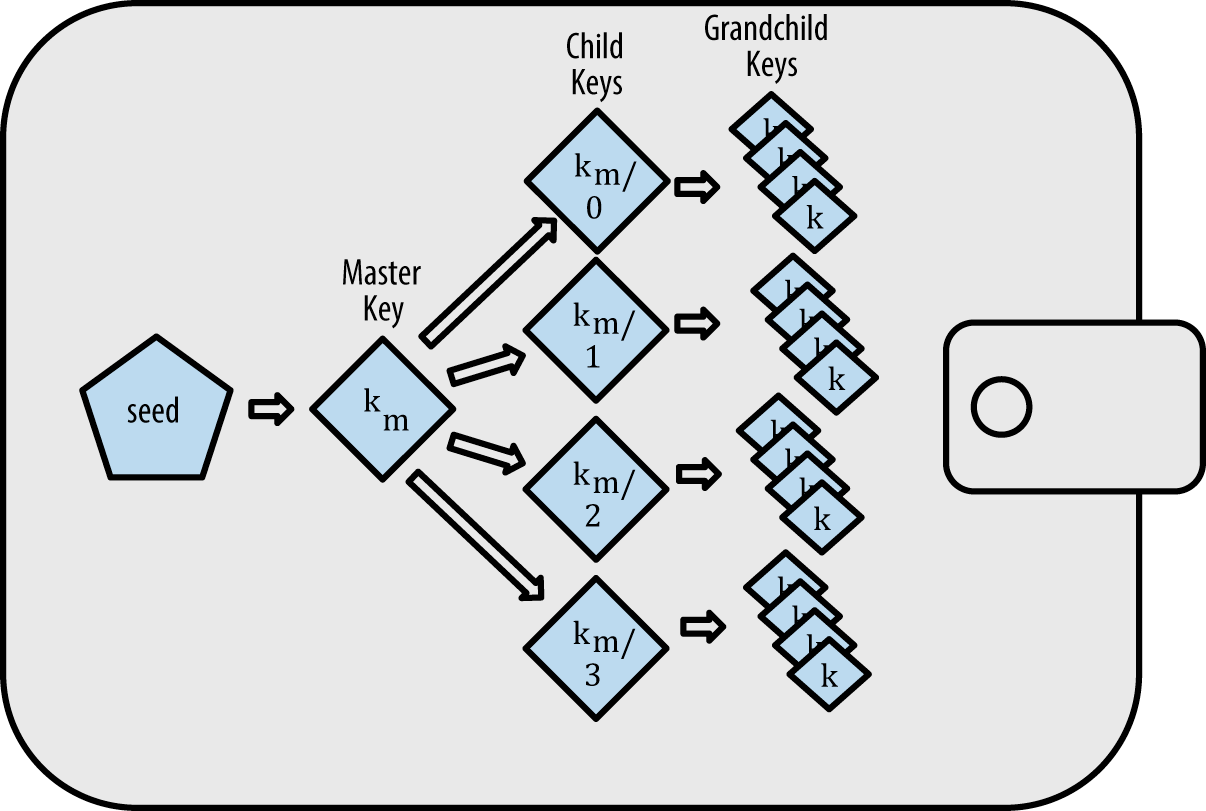
Every wallet contains a set of key pairs, where each key pair consists of a private key and a public key.
- The private key is a random number chosen by the user and kept secret.
- The public key is derived from the private key using elliptic curve cryptography (ECC), which is a one-way function that generates a unique public key from each private key.
In ECC, a private key is a randomly chosen number, and a public key is derived from it using mathematical operations on an elliptic curve. To generate a Bitcoin public key from a private key, the private key is first multiplied by a fixed point on the elliptic curve. The resulting point on the curve is the public key, which is a pair of x and y coordinates. These coordinates are used to create a Bitcoin address through a one-way cryptographic hash function.
The strength of ECC comes from the fact that it is difficult to compute the private key from the public key, making it very secure. In fact, the security of Bitcoin relies on the fact that it is practically impossible to compute the private key from the public key.
Once the public key is generated, a one-way cryptographic hash function is applied to it, resulting in a unique Bitcoin address that is associated with that public key.
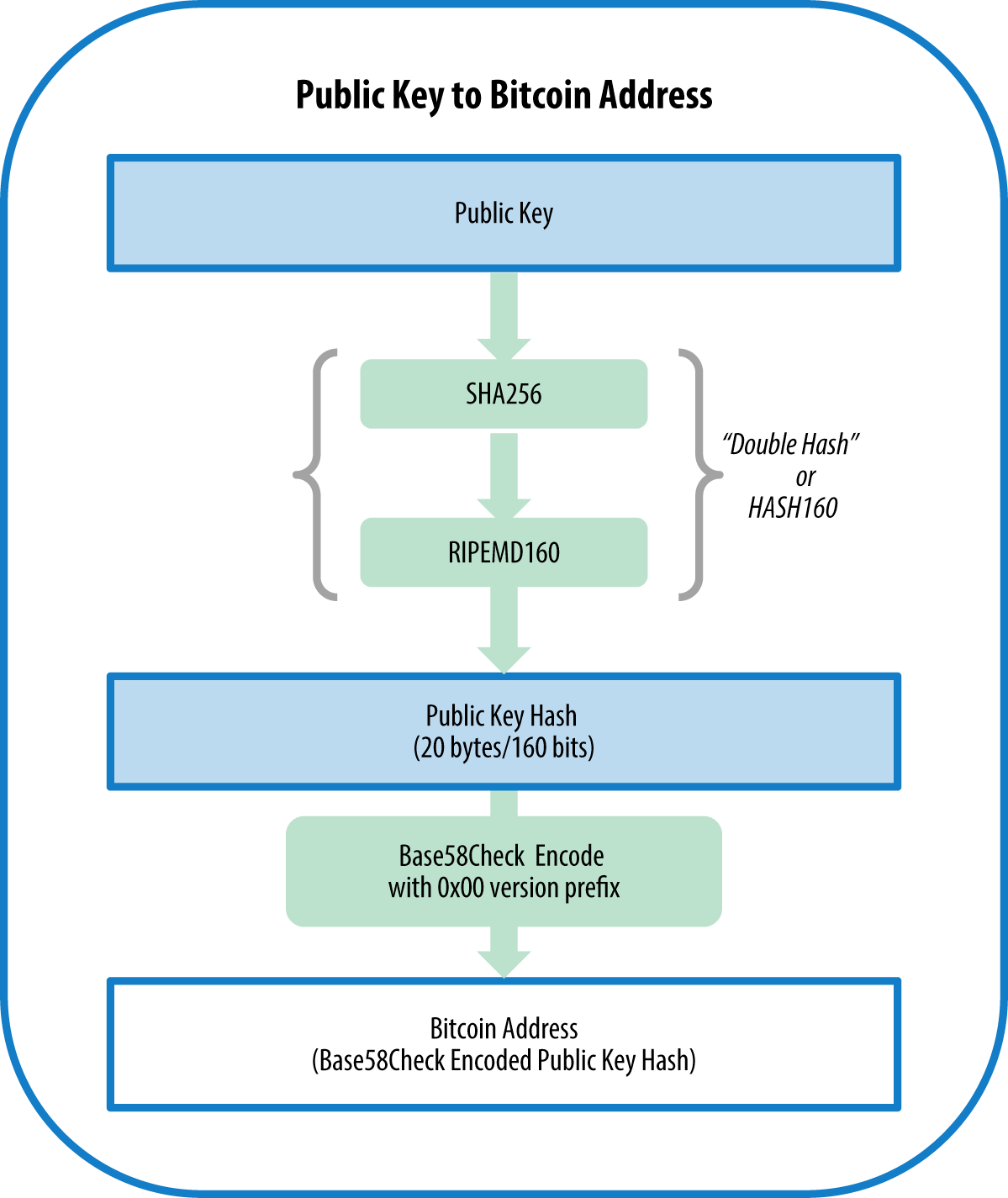
To derive a Bitcoin address from a public key in Bitcoin’s elliptic curve cryptography system, the following steps are taken:
- Start with a public key represented as a point (x, y) on the secp256k1 elliptic curve.
- Concatenate the uncompressed public key prefix 04 to the x and y coordinates to get a 65-byte string.
- Hash the 65-byte string using the SHA-256 algorithm, resulting in a 32-byte hash.
- Hash the 32-byte hash using the RIPEMD-160 algorithm, resulting in a 20-byte hash.
- Prepend a version byte to the 20-byte hash. This byte is used to indicate the type of address being generated (e.g., 0 for a P2PKH address, 5 for a P2SH address).
- Compute the checksum of the version byte and 20-byte hash using the SHA-256 algorithm twice. The first 4 bytes of the second SHA-256 hash are the checksum.
- Append the 4-byte checksum to the 21-byte version byte and 20-byte hash to get a 25-byte binary address.
- Convert the 25-byte binary address to a Base58Check-encoded string to produce a human-readable Bitcoin address.
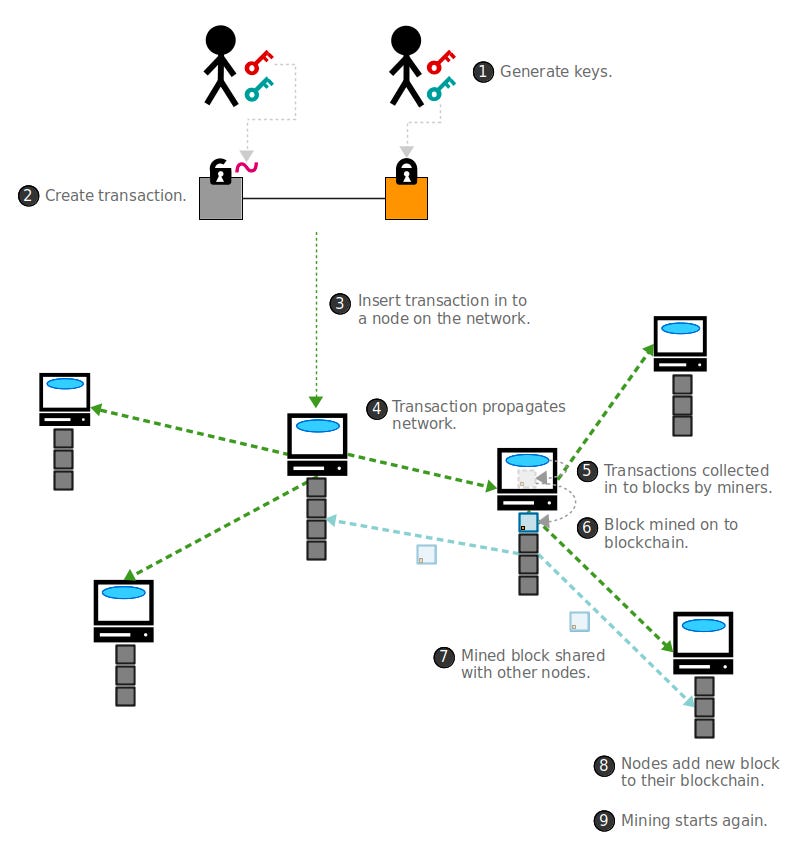
When a user sends bitcoins to another user, they create a transaction that specifies the amount to be sent and the public key of the recipient. This transaction is then signed with the sender’s private key, which proves that they are the rightful owner of the bitcoins being spent.
Next, the transaction is broadcasted to the Bitcoin network, where it is verified by other nodes and miners. The recipient can then use their private key to unlock the bitcoins and spend them as they see fit.
“SHA-256 is very strong. It’s not like the incremental step from MD5 to SHA1. It can last several decades unless there’s some massive breakthrough attack.” – Satoshi Nakamoto
Bitcoin forks
When two parts of the network are following different branches of the blockchain for a short period of time, the blockchain is experiencing a soft fork. This is a natural process that will self-correct when the network reconverges to a common blockchain after which subsequent blocks will be mined.
However, there is another scenario in which blockchains can diverge into two different chains. This is the result of upgrades or changes in the consensus rules of the blockchain and that result in a hard fork where the network does not reconverge onto a single chain.
Hard forks can be used to change the rules of consensus, but they require coordination between all participants in the system. Any nodes that do not upgrade to the new consensus rules are unable to participate in the consensus mechanism and are forced onto a separate chain at the moment of the hard fork.
For software developers, the term “fork” has a different meaning. This occurs when a group of developers choose to follow a different software roadmap and start working on a competing implementation of an open source project.
While a software fork is a necessary precondition, it is not in itself sufficient for a hard fork to occur. For a hard fork to occur, the competing implementation must be adopted and the new rules activated, by miners, wallets, and intermediary nodes.
The blocksize wars
The Bitcoin forks of 2017 were a result of a disagreement among the Bitcoin community about how to scale the Bitcoin network. At the time, the Bitcoin network was experiencing congestion and slow transaction processing times due to a limit on the size of each block in the blockchain. This block size limit had been set at 1 MB since the early days of Bitcoin.
Satoshi Nakamoto never publicly specified why he added a block size limit to the Bitcoin protocol. It has been speculated that he intended it to be an anti-spam measure, to prevent an attacker from overloading the Bitcoin network with artificially large Bitcoin blocks full of bogus transactions. Some have also speculated that he intended for it to be a temporary measure, but it is unclear how temporary or under what conditions he foresaw the block size limit being increased or lifted. The code itself that enforces the block size limit certainly wasn’t temporary.
Some members of the Bitcoin community believed that the block size limit should be increased in order to allow more transactions to be processed per block and to alleviate congestion on the network. However, others believed that increasing the block size would result in centralization of the network, as only the largest and most powerful miners would be able to process the larger blocks.
This disagreement led to a split in the Bitcoin community, with two factions emerging: those who supported increasing the block size, known as Bitcoin Cash (BCH), and those who did not, known as Bitcoin Core (BTC).
In May 2015, Gavin Andressen and Mike Hearn suggested raising the block size limit to 20 MB, which marked the initial effort to increase the limit. However, after consulting with miners, they decided to lower the proposed limit to 8 MB. This was because allowing block sizes larger than 1 MB would have given significant benefits to the largest Chinese miners and pools. It’s worth noting that subsequent improvements were implemented, making the use of 8 MB block sizes secure.
In 2016, during the Hong Kong roundtable consensus, a roadmap was established, which involved implementing SegWit (See section on SegWit) first and then increasing the block size by 2 MB later. However, some individuals believed that the agreement was null and void only a few days after it had been reached. The situation became a protracted stalemate due to Bitcoin Core’s refusal to support a block size increase and miners’ refusal to implement SegWit without being guaranteed a block size increase.
Supports of the small-blocks camp, being upset that the miners did not activate SegWit, proposed the User Activated Soft Fork strategy (USAF), a mechanism in which the activation time of a blockchain soft fork is enforced by the full nodes, which are commonly referred to as economic majority. If someone were to activate the USAF feature in their Bitcoin Core, they would disregard blocks from miners who do not support SegWit. In the event that less than half of the miners were to support UASF, the network would divide into two separate networks: a UASF network and a non-UASF network that would have different perspectives on the history of transactions.
Jeff Garzik and a group of individuals proposed the SegWit2X compromise due to the protracted stalemate and the looming threat of the upcoming UASF catastrophe. Essentially, the SegWit2X compromise was a revival of the Hong Kong roundtable agreement. As a backup plan in case the UASF disaster materialized or the SegWit2X initiative failed for any other reason, the BitcoinABC project was created. However, surprisingly, it split off as a new cryptocurrency called “Bitcoin Cash” on August 1st.
On August 1, 2017, a group of Bitcoin users and miners implemented a hard fork of the Bitcoin blockchain, creating a new cryptocurrency called Bitcoin Cash. The main difference between Bitcoin Cash and Bitcoin was the larger block size limit of 8 MB for Bitcoin Cash, which allowed for faster and cheaper transactions.
Bitcoin sidechains
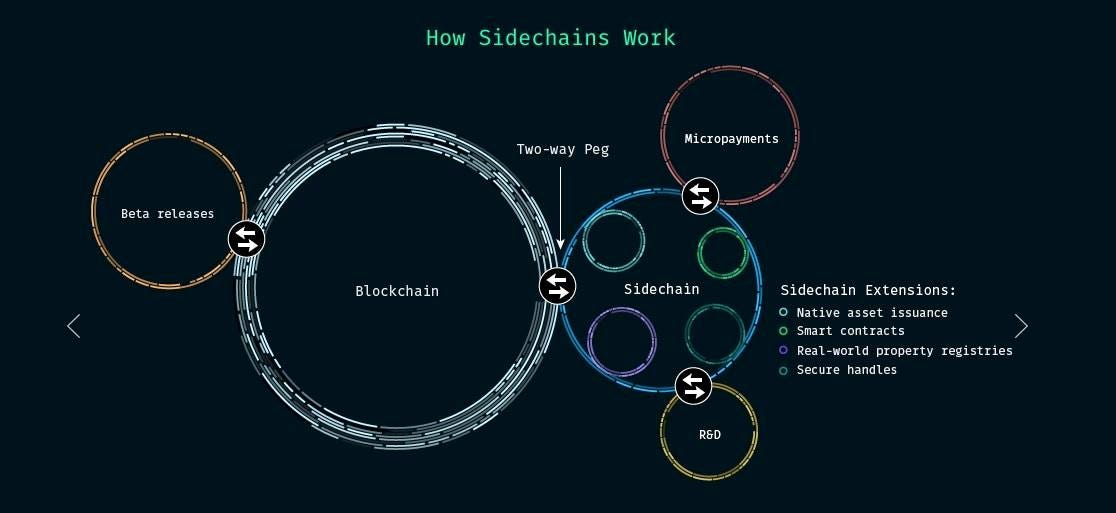
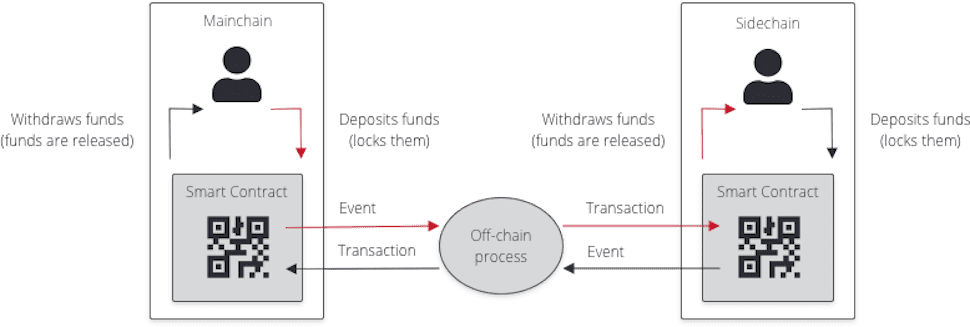
A Bitcoin sidechain is an independent blockchain that can securely transfer bitcoins internal and from/to the Bitcoin network without the need to support its own native token.
The first concept of a sidechain was published in an academic paper in 2014 by Adam Back, the inventor of HashCash and current CEO of Blockstream. In this paper, the authors noted that Bitcoin’s infrastructure was facing trade-offs between decentralization and scalability. As a solution, the paper proposed a new technology, pegged sidechains. This would enable bitcoins and other assets to be transferred between multiple blockchains.
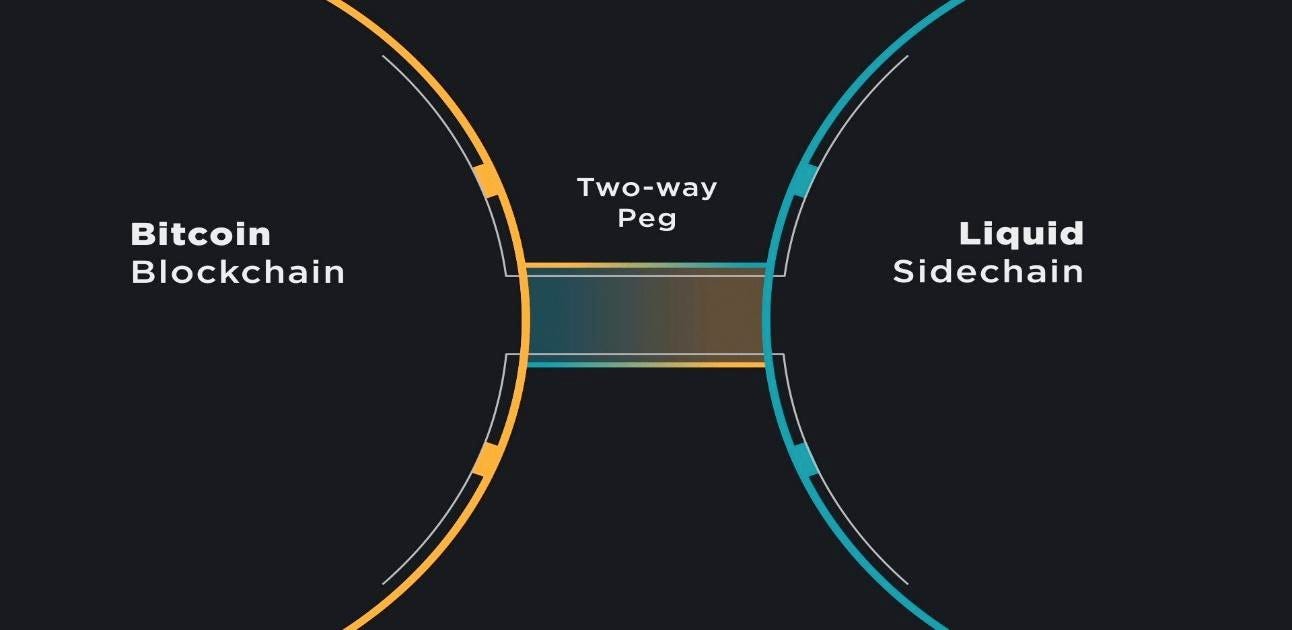
Sidechains are separate networks that connect to another blockchain called the parent blockchain or mainnet. These secondary blockchains have their own consensus protocols as well as the ability to transfer assets to and from the parent chain. To facilitate the back and forth transfer of assets, a two-way peg is required (a tunnel that goes in both directions). Through this mechanism, the assets are not actually transferred. Instead, the assets are locked on the parent chain while the equivalent amount is unlocked in the sidechain.
A series of smart contracts are responsible for making sure that the assets are locked and released in a non-fraudulent mainnet. Once a transaction has occurred, a smart contract will notify the parent chain about the event. After that, an off-chain process will relay the transaction information to a smart contract on the sidechain to verify the transaction.
Some examples of Bitcoin sidechains are Bitcoin’s Liquid Network and RootStock (RSK).
- Liquid’s block discovery time is about one minute, which makes it 10 times quicker than Bitcoin’s 10-minute block time.
- RSK is a sidechain designed for running smart contracts.
Benefits of sidechains
- Scalability from cheaper and faster transactions. This should decongest the main chain, making it faster and cheaper too
- Upgradeability and experimentation for testing new ideas that would not count with the support of the community if they were to be executed on the parent chain.
- Diversification of use cases, such as borrowing and lending.
Drawbacks of sidechains
Since they are independent blockchains, sidechains are responsible for maintaining their own security. That is, a sidechain’s security is not derived from the blockchain it is connected to.
Bitcoin sidechains require their own set of miners as well. A large pool of diverse miners is critical for the security and decentralization of their system. However, growing a new mining ecosystem is not trivial, since miners have no incentive whatsoever to start participating on a new chain when they have access to more lucrative opportunities by mining on other chains.
Bitcoin NFTs
Bitcoin NFTs (Non-Fungible Tokens), are a type of token on the Bitcoin blockchain that represent unique digital assets. These tokens are distinct from regular bitcoin (BTC) and are used to represent one-of-a-kind items such as digital art, collectibles, and even virtual real estate.
Although bitcoins are fungible, they can be marked to be distinguished from other bitcoins.
Unlike regular bitcoin, which is fungible and interchangeable, each bitcoin NFT is unique and can hold significant value depending on the rarity and demand of the underlying asset it represents. NFTs on the Bitcoin blockchain are typically created using protocols such as Counterparty or Omni, which enable the creation of custom tokens with unique properties and features. While the use of Bitcoin for NFTs is less popular than other blockchains like Ethereum, the network still provides a secure and established infrastructure for creating and trading NFTs.
The first NFT collection ever released on Bitcoin was “Rare Pepes”.
One popular open-source protocol built on Bitcoin and that allowed users to represent and manipulate immutable digital assets on top of Bitcoin transactions was Colored Coins. This represented the first stop towards the adoption of NFTs built on top of the Bitcoin network. By using a small amount of Bitcoin as a marker, users could “color” it to represent a specific asset, such as a stock, bond, commodity, or even a real-world asset like a house or a car. This process allowed users to transfer ownership of the underlying asset using Bitcoin’s secure and decentralized network.
A recent example of Bitcoin programmability on Bitcoin is the Bitcoin Ordinals protocol. Through Ordinals, sats are assigned a number in the order they are mined, allowing for exact tracking and verification. Even if a sat moves to a different wallet, its ordinal number stays the same.
Sats, or Satoshis, are the smallest unit of account for bitcoin. A satoshi represents a hundred-millionth of a bitcoin; that is 0.00000001 BTC.
NFTs can also be built on Stacks, which is a Bitcoin layer that brings smart contracts and decentralized applications to the Bitcoin network. Stacks uses a Proof-of-Transfer (PoX) consensus mechanism that connects Stack’s blocks with Bticoin’s blocks by reusing its PoW mechanism. This ensures that every block’s history is resolved and secured by Bitcoin. NFTs powered by Stacks are written in Clarity – the protocol’s novel smart contract language.
Why Bitcoin was Created
The idea of digital cash has a long and rich history. Most notably, a collective known as the cypherpunks wrote at length about digital anonymous cash, how such systems might be realized, and the societal implications of strong cryptography in general. Satoshi Nakamoto published the bitcoin whitepaper on October 31 2008, created the bitcoin genesis block on January 4 2009, and released the bitcoin code on January 8 2009.
Up to this day, the identity of the original creator of Bitcoin has not been revealed. The whitepaper and other early writings by Nakamoto suggest that Bitcoin was created in response to a need for a decentralized, trustless digital currency that could operate without the need for a central authority, such as a government or financial institution.
Bitcoin was created in the context of a growing interest in cryptography, decentralized systems, and digital currencies in the early 2000s. There had been earlier attempts to create digital currencies, such as e-gold and Liberty Reserve, but these systems were centralized and subject to government regulation and intervention.
The development of Bitcoin can also be seen as a response to the 2008 financial crisis, which caused widespread distrust of traditional financial institutions and a growing interest in alternative financial systems. The financial crisis highlighted the fragility of centralized financial systems and the potential for corruption and manipulation. As a result, the idea of a digital currency that could provide greater security, privacy, and control to users was appealing to many people.
“If you don’t believe it or don’t get it, I don’t have the time to try to convince you” – Satoshi Nakamoto
Bitcoin was invented in 2008 with the publication of the whitepaper, titled “Bitcoin: A Peer-to-Peer Electronic Cash System“. Nakamoto’s writings suggest that Bitcoin was intended to address some of the challenges of existing digital currency systems, such as the risk of double-spending and the potential for centralization. By creating a decentralized, trustless system based on cryptography and proof-of-work, Bitcoin offered a new approach to digital currency that was resistant to fraud and manipulation.
In his writings, Nakamoto acknowledged the work of several researchers and projects that had influenced his thinking about digital currencies and decentralized systems, such as Wei Dai’s b-money, Adam Back’s Hashcash, or Nick Szabo’s bit gold.
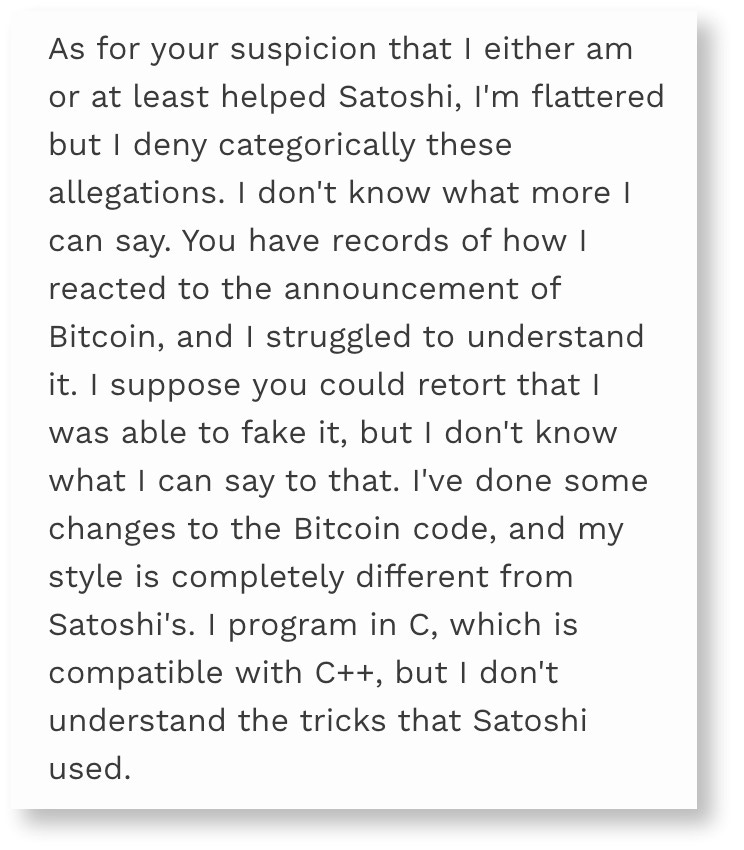
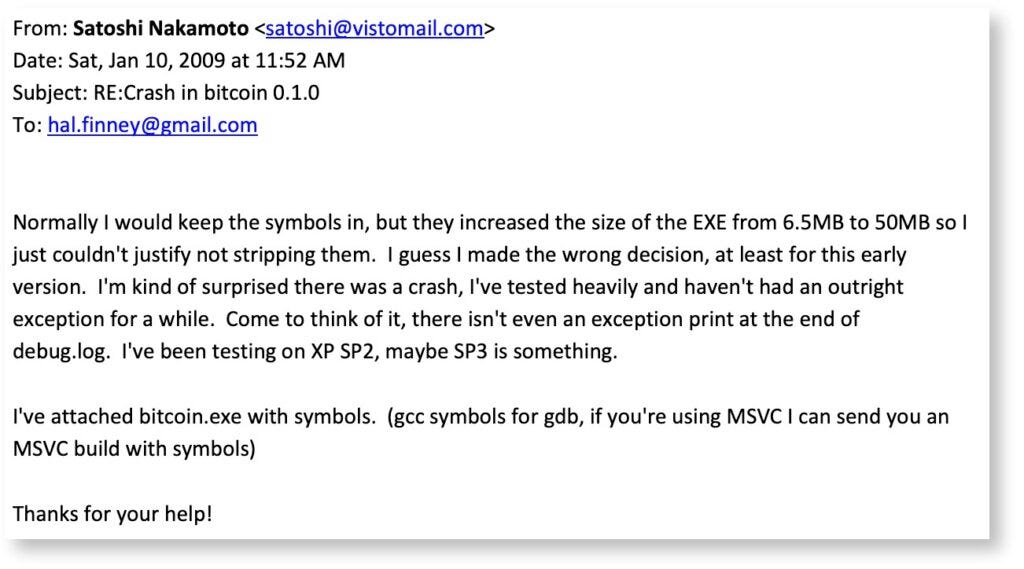
Satoshi had been actively involved in the development of Bitcoin from its inception in 2008 until early 2011, during which time he communicated frequently with the Bitcoin community and worked on improving the Bitcoin protocol.
In April 2011, the pseudonymous creator of Bitcoin, disappeared from the public eye. Satoshi sent an email to one of the Bitcoin core developers, saying that he had “moved on to other things” and that Bitcoin was in good hands with the community. He subsequently stopped posting on forums and communicating with the community, and his true identity and whereabouts remain unknown.
Since then, there have been many theories and rumors about Satoshi’s true identity and why he disappeared. Some speculate that he wanted to maintain his anonymity, while others believe that he may have been pressured by legal or government entities to step away from the project.
Despite his disappearance, Satoshi’s contributions to the development of Bitcoin and the broader cryptocurrency industry are widely recognized, and his ideas and innovations continue to shape the direction of the industry today.
The inspirations behind the origin of Bitcoin
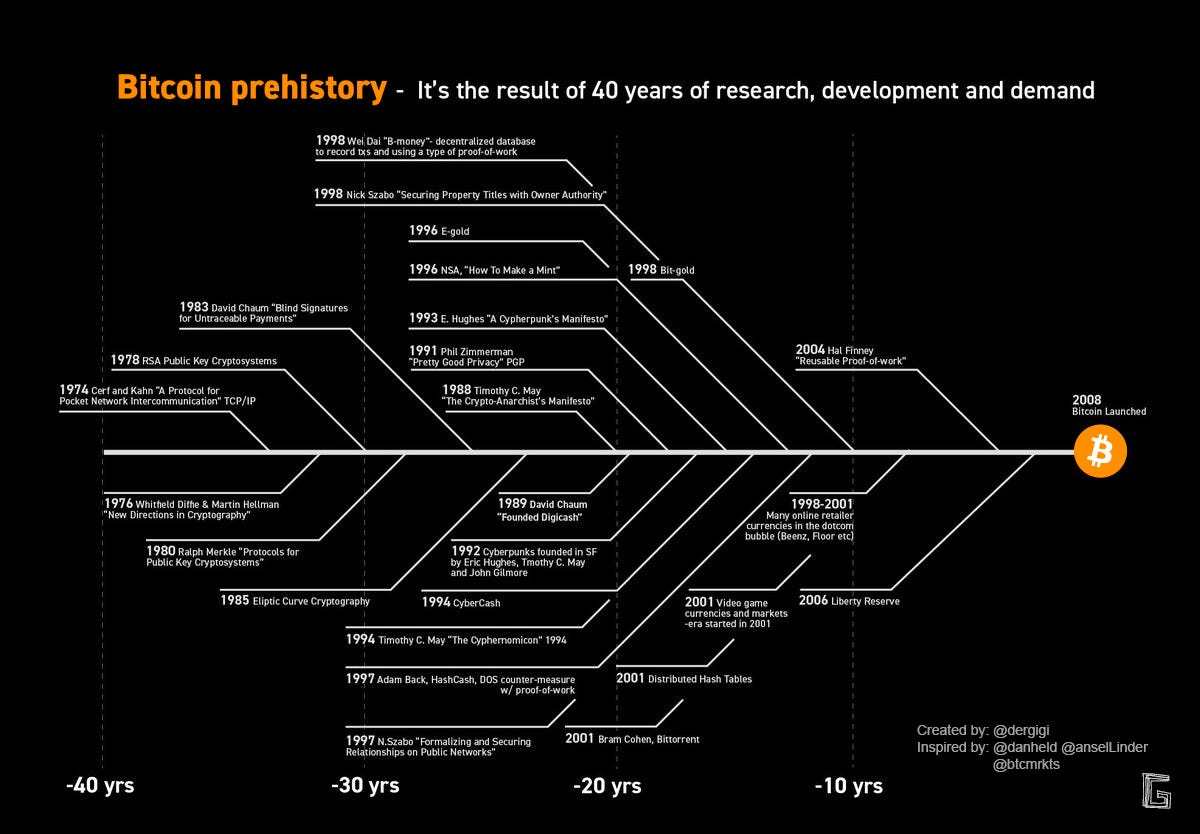
By building Bitcoin, Satoshi was able to build upon technologies and protocols that were invented more than 50 years ago. While 50 years might be a long time in technology, the art of cryptography is way more ancient than that, dating back as far as 1900.
“The root problem with conventional currency is all the trust that is required to make it work. The central bank must be trusted not to debase the currency, but the history of fiat currencies is full of breaches of that trust” – Satoshi Nakamoto
Carl Menger – The Origins of Money
In his famous article, “On the Origins of Money“, Carl Menger explains that the origin of money is not through social or legal means, but rather it emerges naturally through the market. Menger argues that money is not created by the state or any other authority, but rather it is a result of the spontaneous interactions of individuals in the market.
He further explains that money emerged as a result of individuals seeking to trade their goods and services for other goods and services, but found it difficult to find others who have what they need and need what they have. Therefore, they eventually started to trade their goods and services for an intermediary commodity that was widely accepted and could easily be traded for any other good or service. This intermediary commodity eventually became money and was widely accepted in trade.
According to this theory, Menger states that money is not created by the state or any other authority, but rather it emerges naturally as a result of market interactions, and its value is derived from its usefulness in facilitating trade.
David Chaum – Untraceable Electronic Mail
David Chaum was a computer scientist and cryptographer whose inspiration for Satoshi came from his paper titled “Untraceable Electronic Mail, Return Addresses, and Digital Pseudonyms“. This piece is considered to be a groundbreaking work in the field of cryptography and electronic privacy, and laid the foundation for the development of anonymous communication technologies such as Tor and cryptocurrencies like Bitcoin.
The paper introduces the concept of a digital signature, which allows the sender to encrypt a message and authenticate their identity, without revealing their actual identity to the recipient or anyone else. This would be possible with a system that could anonymize messages by routing them through a series of servers in a random order. The paper also discusses the concept of digital pseudonyms, which allow individuals to maintain multiple, anonymous identities online.
Digicash – David Chaum
David Chaum came up with the idea of eCash in 1982, when he suggested the idea of using digital signatures to prove ownership, a principle that is still used in Bitcoin today.
DigiCash was an electronic payment system created by David Chaum in the early 1990s. The system was based on a technology called “blind signatures,” which allowed for secure and anonymous transactions.
This was one of the earliest attempts at creating a digital currency that allowed people to make payments online without having to reveal their identities or financial information. Digicash used digital tokens called “eCash,” which were similar to physical cash in that they could be transferred between parties without the need for a financial institution to facilitate the transaction.
While eCash was cryptographically and technologically interesting, it wasn’t a monetary innovation and ultimately failed because it was operated by a centralized entity: DigiCash Inc., the company founded by Chaum. DigiCash ultimately failed due to a lack of adoption and investment, but it paved the way for the development of other digital currencies, including Bitcoin. After three operational years, the company ended up going bankrupt.
Phil Zimmermann – PGP
The controversy surrounding the U.S. government’s stance on encryption began in the early 1990s when encryption technology started to become widely available to the public. At that time, the U.S. government viewed encryption as a threat to national security because it could be used by criminals and terrorists to hide their communications. As a result, the government tried to limit the use and development of encryption technology.
One of the most significant legal battles over encryption occurred in the 1990s when the government attempted to restrict the export of encryption software. This effort was challenged by a number of individuals and organizations, including Phil Zimmermann, the creator of the popular encryption software PGP.
Zimmermann decided to create PGP to make strong encryption accessible to everyone, with the hope that it would lead to a world where privacy is respected and protected.
For Zimmermann, the motivation for creating PGP was the importance of privacy and how it is threatened by government surveillance and censorship. Before PGP, online privacy was largely inaccessible to the general public due to the high cost and technical expertise required.
In the years that followed the invention of PGP, the U.S. government continued to push for restrictions on encryption technology, but these efforts were met with increasing resistance from the tech industry and civil liberties advocates. The debate came to a head in the aftermath of the September 11th terrorist attacks, when the government again sought to limit the use and development of encryption technology.
In recent years, there has been a growing recognition of the importance of strong encryption for protecting individual privacy and securing online communications. However, there continue to be debates over issues such as encryption backdoors, which would allow law enforcement agencies to access encrypted communications in certain circumstances. These debates highlight the ongoing tension between national security concerns and individual privacy rights.
The Cypherpunk movement
It is not entirely clear if Satoshi Nakamoto was directly influenced by cypherpunks, but the cypherpunk movement and their ideas about privacy, cryptography, and decentralized systems were certainly influential in the broader context of the development of cryptocurrencies.
The word cypherpunk comes from the words cypher and cyberpunk (a genre of science fiction set in a lawless subculture of an oppressive society dominated by computer technology). The word is used to refer to activists that promote the wide use of strong crypto and privacy-enhancing technologies as a route to social and political change. The roots of the word are traced back to the works of David Chaum on anonymous digital cash and pseudonymous reputation systems.
Satoshi’s whitepaper on Bitcoin cited the need for a decentralized digital currency that could function without a central authority, and this idea of decentralization is a core principle of the cypherpunk movement. The use of cryptographic techniques to secure transactions and ensure privacy is also a key component of both cypherpunk philosophy and the Bitcoin protocol.
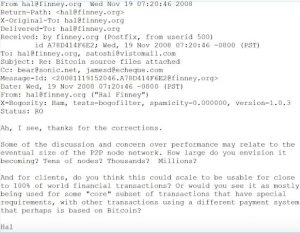
It is also worth noting that many early Bitcoin developers and supporters were themselves cypherpunks, and they brought their ideas and expertise to the development of the cryptocurrency. For example, Hal Finney, who was one of the first people to receive a Bitcoin transaction from Satoshi, was an active cypherpunk and a developer of various cryptographic systems.
The cypherpunk manifesto
After forming the group in 1992, Eric Hughes, Timothy C. May, and John Gilmore created the cypherpunk mailing list to discuss and share their ideas around cryptography, remailers, anonymity, digital cash, and privacy with a wider audience. Years later, Satoshi Nakamoto published the Bitcoin whitepaper on a similar mailing list: the cryptography mailing list.
The cypherpunk manifesto written by Eric Hughes in 1993 is the original political and philosophical statement behind the cypherpunk ideology. The term “cypherpunk” refers to a group of activists who advocate for strong cryptography and privacy-enhancing technologies as a means of promoting individual freedom and limiting government and corporate control. In this paper, Erich Hughes discussed the idea of digital cash, its relation to privacy, and its importance for a free society.
“Since we desire privacy, we must ensure that each party to a transaction have knowledge only of that which is directly necessary for that transaction. Since any information can be spoken of, we must ensure that we reveal as little as possible. In most cases personal identity is not salient. When I purchase a magazine at a store and hand cash to the clerk, there is no need to know who I am.”
The manifesto has been influential in the development of the modern internet and the growth of the privacy and security industries. It has also inspired the work of many activists and organizations who seek to promote digital freedom and individual autonomy in the face of government and corporate surveillance.
The core principles of the cypherpunk manifesto are:
- Privacy is a fundamental right that must be protected through the use of cryptography and other technologies.
- Cypherpunks should work to create and distribute tools that enable individuals to protect their privacy and anonymity online. The reason for that was attributed to the fact that governments and other powerful entities will always seek to control and monitor communications.
- Cypherpunks should be committed to open source software and the free exchange of ideas and information.
- The use of strong encryption and other privacy-enhancing technologies is a form of resistance against authoritarianism and the erosion of civil liberties.
E-gold – Douglas Jackson and Barry Downey
Even though e-gold was not groundbreaking in terms of innovation in the field of cryptography, it was one of the first digital currencies that managed to gain traction before the 2000s. Although others existed before its inception in 1996, e-gold is considered to be the first successful digital currency that became popular enough to have some merchant adoption.
Unlike traditional digital currencies, which were backed by government-issued fiat currencies, e-gold was backed by physical gold held in a vault. Users could exchange their e-gold for physical gold at any time, or use it to make purchases online.
Besides the e-gold tokens backed by gold, other precious e-metals could be acquired: e-silver, e-platinum, and e-palladium.
One of the key features of e-gold was its anonymity. Transactions were conducted using pseudonyms rather than real names, making it difficult for authorities to trace the source or destination of funds. This also made e-gold attractive to criminals, who used it for money laundering and other illegal activities. The irreversibility of the transfers also made e-gold an indispensable tool for money launderers, identity thieves, fraudulent “financial” investors, and purchasers of child pornography.
At its peak, e-gold reached 5M users and processed transfers of value in the order of $2B. Similar to eCash, its demise turned out to be the fact that it was run as a centralized service offered by a company: Gold & Silver Reserve Inc. By 2006, e-gold’s corporate governance realized that the website was being used for illegal activities and began blocking accounts. Soon after, it was targeted by the U.S government, who filed a lawsuit claiming that the company was running an unlicensed money transmitting business. In 2007, the U.S. government mandated e-gold to block several accounts with the argument that e-gold was not doing enough to prevent illegal activity by not having a mechanism in place that stopped fraudulent users from just creating new accounts and transferring funds to these new accounts.
Money transmitting businesses are required under U.S. law to receive a license, which also comes with keeping certain legal information on the users that create accounts.
Hal Finney – Digital Cash and Privacy
Hal Finney’s essay, “Digital Cash & privacy” explores the concept of digital cash and the potential impact it could have on society. This article offers an early exploration of the possibilities and challenges of digital cash, which would later become a key inspiration for the creation of Bitcoin.
In the essay, Finney argues that digital cash has the potential to be more private and secure than physical cash, as it can be authenticated and verified without the need for physical exchanges. He also discusses the potential for anonymous transactions, which he believes would have significant benefits for individuals’ privacy and freedom.
Wei Dai’s B-money
In 1998, Wei Dai proposed a digital currency system called “b-money” that used a proof-of-work scheme to prevent double-spending and achieve consensus. Dai’s proposal introduced many of the core concepts that later became key features of Bitcoin, such as proof-of-work, public-key cryptography, and decentralized consensus.
This was one of the earliest known attempts to create a decentralized digital currency system. Each user would have a public key and a private key, similar to Bitcoin’s public-key cryptography. Users would then be able to generate new coins by solving a cryptographic puzzle, similar to Bitcoin’s proof-of-work system. Next, these newly created coins would be broadcast to the network and added to a public ledger.
One key difference between b-money and Bitcoin was that b-money did not have a fixed supply of coins. Instead, new coins would be created in response to demand, based on a predetermined algorithm that took into account the rate of coin creation and the number of users on the network.
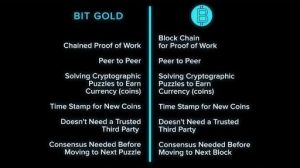
Nick Szabo’s bit gold
In 1998, Nick Szabo proposed a digital currency system called “bit gold”, that used a proof-of-work scheme to create new coins and secure the network. Szabo’s proposal also introduced the concept of smart contracts, which later became an important feature of Ethereum and other blockchain platforms.
At the core of the bit gold system was a proof-of-work algorithm that required users to solve a cryptographic puzzle in order to create new coins. This proof-of-work process also served to validate transactions and prevent double-spending, similar to how it works in Bitcoin.
Bit gold also introduced the concept of a “blockchain,” which was a public ledger of all transactions that had occurred on the network. Each block in the blockchain contained a list of transactions, along with a reference to the previous block in the chain. This made the system resistant to tampering and provided a transparent record of all transactions.
In addition to its use as a currency, bit gold also included a system for creating and enforcing smart contracts. This allowed users to create contracts that would execute automatically based on predetermined conditions, without the need for intermediaries or trusted third parties.
Adam Back’s Hashcash
In 2002, Adam Back introduced a system called “Hashcash” that used a proof-of-work algorithm to limit email spam. Nakamoto used a similar proof-of-work algorithm in Bitcoin to prevent double-spending and achieve consensus.
Hashcash was designed to limit email spam and denial-of-service attacks. This was achieved by requiring users to solve a computational puzzle in order to send an email or request to a server. With this system, the idea was to create a small computational cost for sending an email or request. This would make it impractical for spammers or attackers to send large volumes of messages.
Hashcash works by requiring the sender to include a special header in the email or request that contains a value that satisfies a cryptographic puzzle. This puzzle involves finding a hash value that meets certain criteria, such as having a certain number of leading zeros. As a result, the puzzle is designed to be computationally difficult, so that it takes a certain amount of time and processing power to solve it.
The sender of the email or request must spend a certain amount of processing power to solve the puzzle and find a hash value that meets the criteria. This processing power is known as a “proof-of-work,” and it serves as a kind of digital stamp that verifies that the sender has spent a certain amount of resources to send the message. Once the message is sent, the recipient can use this proof-of-work to verify that the sender is legitimate and that the message is not spam or an attack.
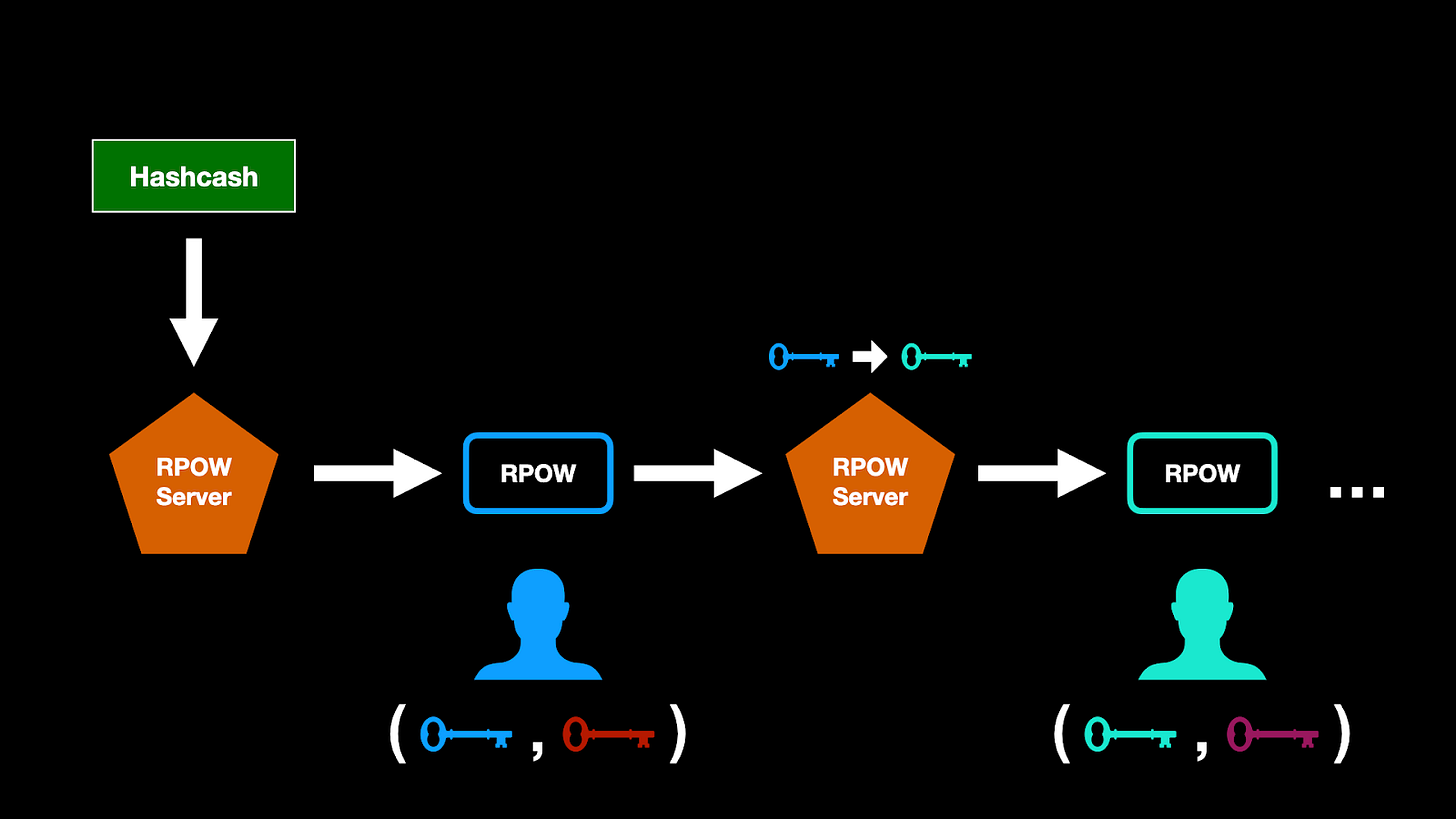
RPOW – Hal Finney
RPOW stands for Reusable Proof of Work, and was pioneered by Hal Finnery in 2004, who found a way to make the proof-of-work tokens from Adam Back’s hashcash reusable.
The system would receive hashcash as a PoW token, and in exchange create RSA-signed tokens called reusable proof-of-work (RPOW) tokens. These RPOW tokens could then be transferred from person to person and exchanged for new RPOWs at each step. In this framework, each RPOW token can only be used once, but since it gives birth to a new one, it is as though the same token can be handed from person to person.
With RPOW, a user can create RPOW tokens via the RPOW client software, twitch takes a proof-of-work string as generated by the Hashcash software invented by Adam Back. This string is signed by the user’s private key and subsequently registered by a RPOW server, which records that this token belongs to the user’s private key. The user can then pass that token on to someone else by signing a transfer order to another user’s public key.
Hal Finney’s implementation was a practical solution to the double-spend problem. Since POW tokens themselves are just hashes (bits of information) that can be double spent, they are not a good representation of money. However, with the concept of RPOW servers, Hal Finney introduced central, but trust-minimized authorities that can cryptographically determine a chain of ownership.
RPOW also introduced a series of rules:
- No inflation. This is explained in the sense that any RPOW server will only create RPOW tokens equal in value to incoming POW and RPOW tokens. Since users can create new proof-of-work tokens via Adam Back’s hashcash, inflation in terms of new supply coming into the system can and will always happen.
- No backdoors. This rule alludes to the transparency of the system, which everyone can observe and inspect at all times.
- Privacy protection. Hal often advocated for the user of Tor to connect to RPOW servers. In his writings, he also pointed out that “the owner is the enemy” and that “the programmer is the enemy”. This serves as a reminder for users that any system that facilitates trust-minimized exchanges of money needs to be set up and operate under an adversarial mindset.
Similar to Hashcash, RPOW was one of the systems that was actually implemented. However, probably due to the effort required to run RPOW servers, as well as the lack of incentives to do so, Finney’s reusable proof-of-work tokens never gained traction and the project was eventually discontinued.
Running Bitcoin
The Bitcoin network started in 2009, based on a reference implementation published by Nakamoto and since revised by many other programmers.
The phrase “running Bitcoin” typically refers to the act of running a Bitcoin node or client on a computer or server. At that time, Bitcoin was still an experimental technology, and only a small number of individuals were actively using and developing it. To participate in the network, users had to run a Bitcoin client or node, which would download and store a copy of the blockchain and allow the user to send and receive Bitcoin transactions.
The steps to run a network as follows:
- New transactions are broadcast to all nodes.
- Each node collects new transactions into a block.
- Each node works on finding a difficult proof-of-work for its block.
- When a node finds a proof-of-work, it broadcasts the block to all nodes.
- Nodes accept the block only if all transactions in it are valid and not already spent.
- Nodes express their acceptance of the block by working on creating the next block in the chain, using the hash of the accepted block as the previous hash.
“Once the latest transaction in a coin is buried under enough blocks, the spent transactions before it can be discarded to save disk space. To facilitate this without breaking the block’s hash, transactions are hashed in a Merkle Tree, with only the root included in the block’s hash. Old blocks can then be compacted by stubbing off branches of the tree. The interior hashes do not need to be stored.” – Satoshi Nakamoto
Relevant network upgrades
Segregated witness
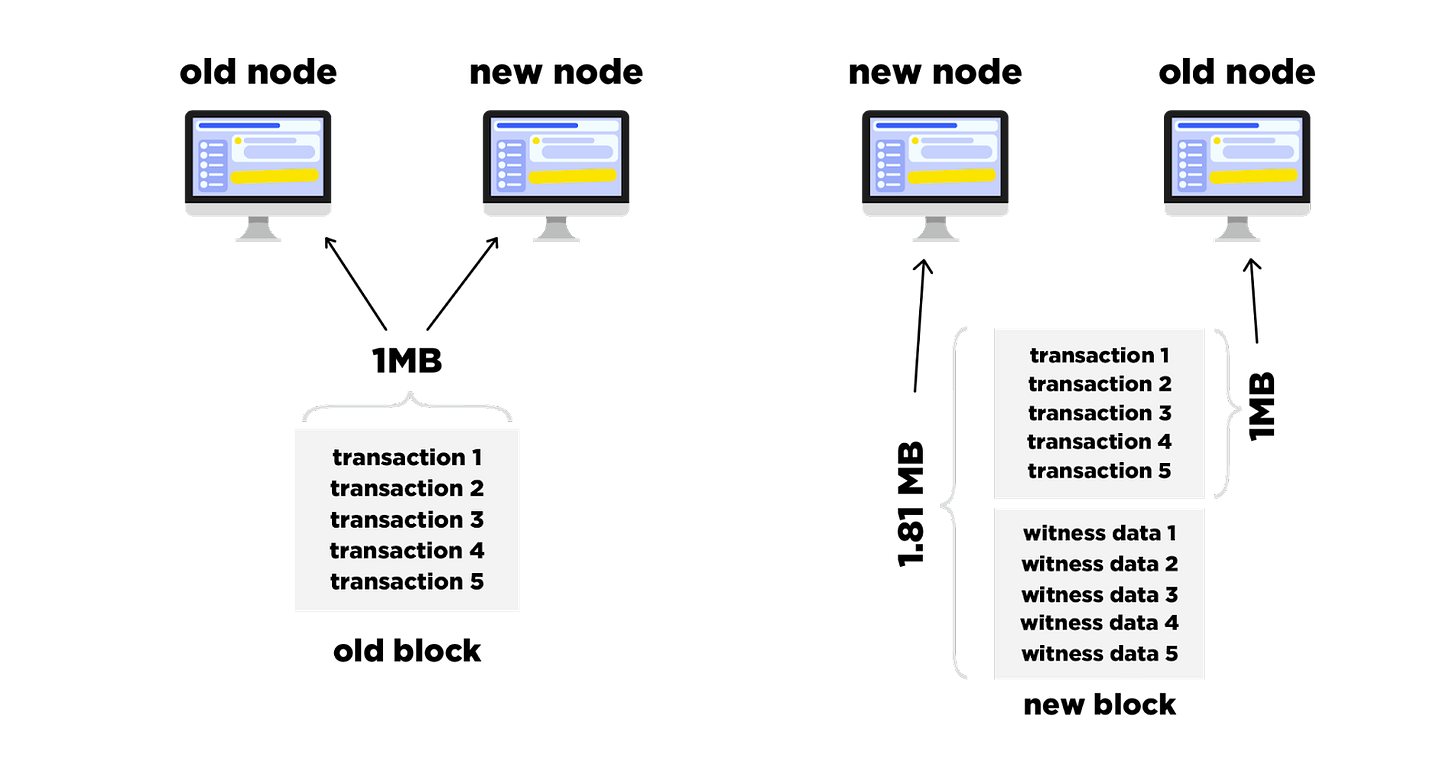
Segregated Witness (segwit) is an upgrade and soft fork to the consensus rules of the network that was activated on Bitcoin’s mainnet on August 1st, 2017. The main purpose of SegWit was to increase the transaction capacity of the Bitcoin network by removing the signature data, also known as the witness data, from the main part of the transaction, thus reducing the size of the transaction.
In a Bitcoin transaction, there are two parts: the transaction data, which includes information about the sender, the recipient, and the amount of Bitcoin being transferred, and the signature data, which proves that the transaction is legitimate and was authorized by the owner of the Bitcoin being spent.
With SegWit, the signature data was separated from the transaction data and moved to a new data structure called the “witness“. This helps to free up space in the Bitcoin blocks, which can then be used to include more transactions. This architectural change had noticeable effects on the security, scalability, and performance of the network.
Some of the most notable features introduced by the upgrade include:
- Transaction malleability. This is an issue that affects how transactions are identified and tracked on the network. In simple terms, this refers to the ability of an attacker to modify the transaction ID of a transaction before it is added to a block. This can cause issues such as delays in confirming transactions, difficulty in tracking transactions, and even potential double-spending attacks. SegWit helped solve this issue by separating the transaction data from the signature data in a block, effectively making the signature data no longer part of the transaction ID. With this upgrade, transaction hashes become immutable by anyone other than the creator of the transaction. This greatly improves the implementation of many other protocols that rely on advanced bitcoin transaction construction, such as payment channels, chained transactions, and lightning networks.
- Script versioning. Prior to SegWit, any change in the transaction structure, including changes in the scripts, would invalidate the transaction. With SegWit, the witness contains the scriptSig and witness data, which is used to verify the transaction. Since the witness data is separated from the transaction data, it becomes possible for scripts to be updated without invalidating the transaction.
- Network and storage scaling. By separating the transaction signature data, or “witness,” from the transaction data, more transactions could fit into each block without increasing the block size, which would have led to longer confirmation times and higher fees. With SegWit, nodes can prune the witness data after validating the signatures, or ignore it altogether when doing simplified payment verification. In fact, the witness data doesn’t need to be transmitted to all nodes and does not need to be stored on disk by all nodes.
- Signature verification optimization by reducing the algorithmic and computational complexity involved of signature functions to O(n). Before SegWit, the complexity of data-hashing computations increased exponentially, O(N^2) with the number of signature operations, which introduced a significant burden in the performance of all nodes verifying signatures.
- Offline signing improvements. Prior to the upgrade, offline signing devices, such as a hardware wallet, would have to verify the amount of each input before signing a transaction. This was achieved by streaming a large amount of data about previous transactions. With SegWit, that data becomes part of the hash that is signed and, therefore, there is no need for any offline device to sign the data.
Taproot
Taproot was a protocol upgrade that aimed to enhance the network’s privacy, security, and flexibility. It was the most important network upgrade since the activation of Segwit in 2017. Even though it was not as controversial as SegWit, this introduced significant improvements to the protocol. The Taproot upgrade was fully activated on the protocol on November 14, 2021.
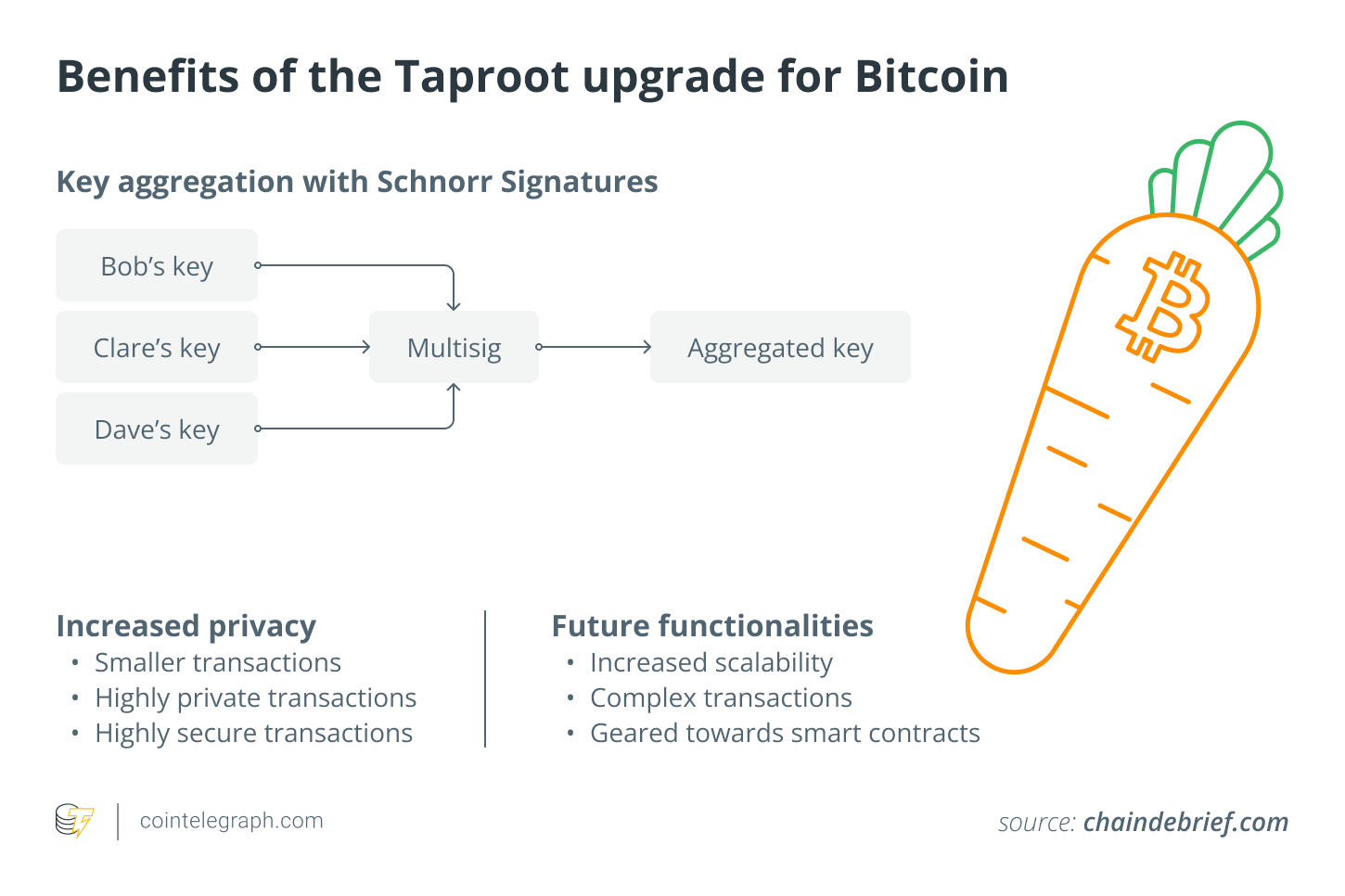
The upgrade proposed a new transaction format that would allow users to combine multiple conditions for spending their bitcoin in one single transaction. This reduces the transactions’ size and cost.
One of the most significant features of the Taproot upgrade is its ability to hide the details of a transaction’s smart contract execution by combining multiple conditions into a single hash. This enhances user privacy by making it harder to determine the exact details of a transaction, such as the type of smart contract being executed or the specific conditions required for spending the funds. To achieve that, the Taproot upgrade allowed for multiple and complex signatures to be aggregated and verified together, rather than individually.
Taproot also has benefits for Bitcoin’s network scalability by allowing for more complex smart contracts without increasing the size of the transaction. By reducing the size of transactions, it can increase the network’s capacity and reduce transaction fees.
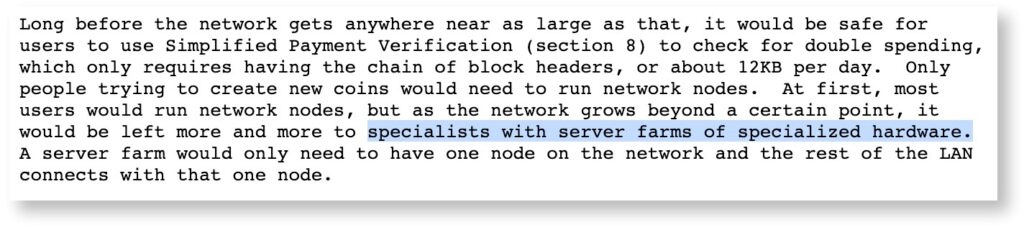
“I anticipate there will never be more than 100K nodes, probably less. It will reach an equilibrium where it’s not worth it for more nodes to join in. The rest will be lightweight clients, which could be millions.” – Satoshi Nakamoto
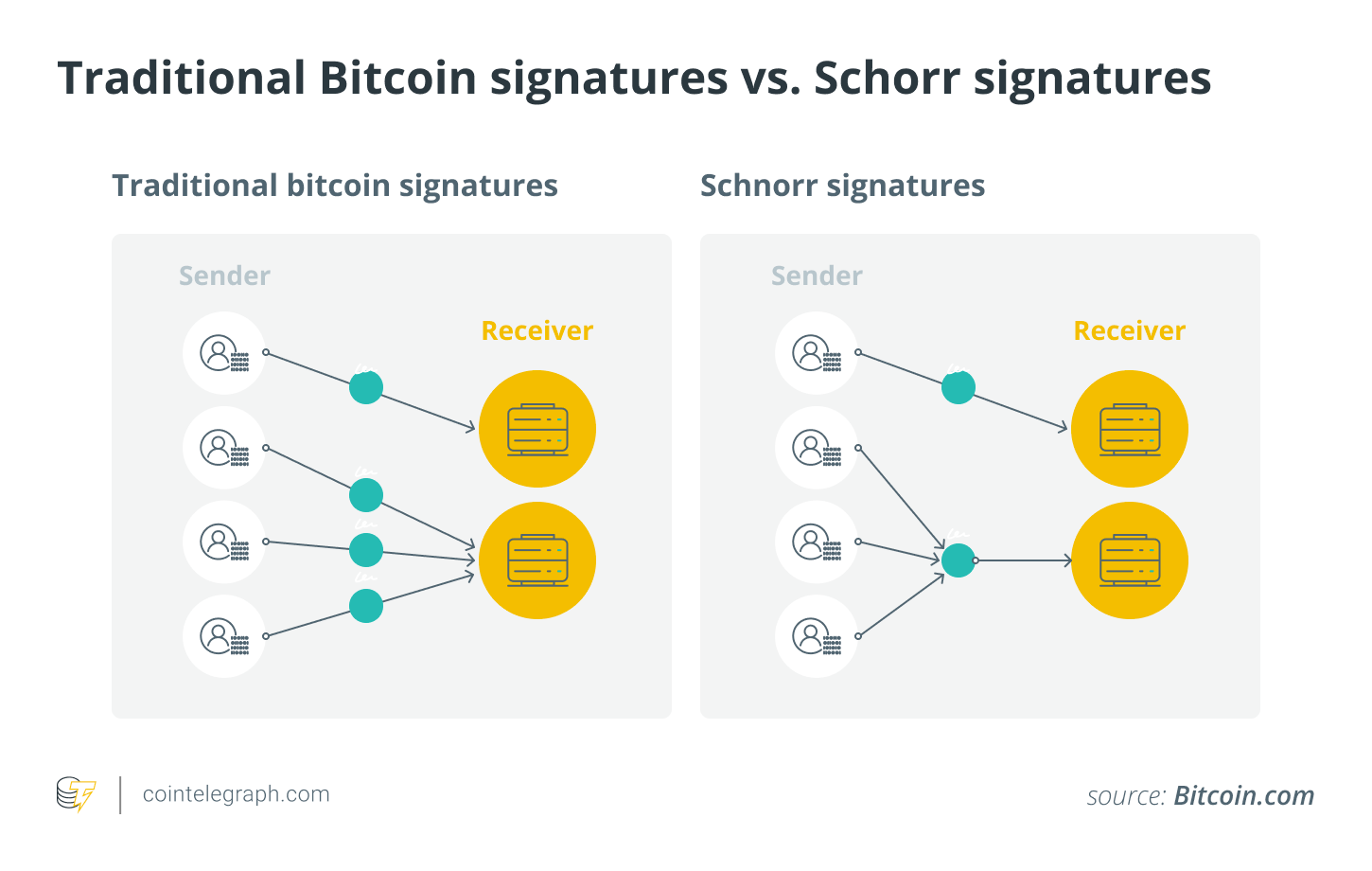
The main change was the implementation of Schnorr signatures. These signatures are considered more secure than ECDSA (Elliptic Curve Digital Signature Algorithm). Specifically, they are resistant to certain types of attacks, such as side-channel attacks and multisignature attackers.
Schnorr signatures are also more efficient in terms of computation and storage requirements and can be used to enable more private transactions.
Using the Protocol
Unlike traditional currencies, bitcoin is entirely digital. In a sense, it is the perfect form for transferring value on the internet. It is a fast, secure, and borderless way for buying and selling goods, transferring money to other people or organizations, or extending lines of credit.
Bitcoin is a distributed peer-to-peer system where there are no physical or even digital coins per se. Instead, these coins are implied in transactions that transfer value from a sender to a recipient. To participate in the network, users hold keys that allow them to prove ownership of bitcoin and sign transactions to transfer and spend their bitcoin. These keys are stored in a digital wallet under the custody of the user.
Choosing a Bitcoin wallet
Since Bitcoin is a protocol, users need a client application that allows them to interact and communicate with the Bitcoin system. The most used and common way to interface is with a Bitcoin wallet.
When a user wants to send Bitcoin, they use their Bitcoin wallet to create a transaction and broadcast it to the Bitcoin network. When a user wants to receive Bitcoin, they provide their Bitcoin wallet address to the sender.
Bitcoin wallets use public key cryptography to secure network transactions. Each wallet has a public key and a private key. The public key is used to receive bitcoin, while the private key is used to sign transactions and send bitcoin. To remain secure, users should always keep full control and ownership of their private key.
There are several types of Bitcoin wallets, including desktop wallets, mobile wallets, web wallets, and hardware wallets. Each type of wallet has its own advantages and disadvantages. For that reason, choosing a wallet is highly subjective and depends on the use and user expertise.
- Desktop wallets are installed and run on a user’s personal computer. They can be downloaded and installed on most operating systems, including Windows, Mac, and Linux. Typically, these wallets store a user’s private keys on their local computer. As a result, one potential disadvantage of desktop wallets is that they can be vulnerable to malware or hacking attacks if the computer is not properly secured.
- Mobile wallets are designed to be used on a smartphone. These wallets offer a convenient way to manage Bitcoin on-the-go and can be used to send and receive Bitcoin payments easily. They are compatible with most mobile operating systems, such as IOs and Android, and they offer features such as QR code scanning to allow users to make payments on physical stores. While most mobile wallets use a combination of PIN codes, passwords, and biometric authentication, such as fingerprint or face recognition, to secure the wallet, the private keys are stored on the device. As a result, one potential disadvantage of mobile wallets is that they may be vulnerable to hacking attacks or malware if the device is not properly secured.
- Web wallets are accessible through a web browser and can be hosted by third-party service providers. One advantage of web wallets is that they are accessible from any device with an internet connection. This makes them a convenient option for users who need to manage their Bitcoin holdings from multiple devices or locations. However, this convenience comes with a trade-off in security, since a user’s private keys are stored on a remote server, which is managed by a third-party service provider.
- Hardware wallets are special purpose hardware devices that can handle all Bitcoin-related operations on specialized hardware. When a user wants to send Bitcoin from a hardware wallet, they connect the device to a computer or mobile device and initiate the transaction. The transaction is then signed by the hardware wallet and transmitted to the Bitcoin network, providing a secure and tamper-proof way to initiate transactions. Since the private keys are stored on the device, the loss of the wallet can result in the loss of the user’s Bitcoin holdings. To mitigate that risk, hardware wallet manufacturers include a recovery seed phrase, which can be used to recover a user’s private keys in the event that the device is lost or damaged.
The word “wallet” can be used to describe different things in Bitcoin. At a high level, a wallet is an application that serves as the interface that allows users to interact with the protocol in order to access their funds, manage their keys and address, track their balances, create and sign transactions… More narrowly, Bitcoin developers often use the word “wallet” to refer to the data structure that is used to store and manage a user’s keys.
A distinction can also be made between wallets based on whether the keys they contain are related to each other or not.
- Non-deterministic wallets, also known as random wallets, generate a new private key for every new transaction. This makes it difficult to keep track of multiple addresses and transactions. For that reason, random wallets are not widely used anymore, as they are less secure and less convenient compared to deterministic wallets.
- Deterministic wallets use a single seed to generate a hierarchy of keys. This means that all of the keys (and addresses) in the wallet can be derived from the initial seed, which makes it much easier to keep track of multiple addresses and transactions.
- Hierarchical Deterministic wallets, or HD wallets, are a specific type of deterministic wallet that allow for the creation of an infinite number of key pairs. HD wallets use a master seed to generate a tree-like structure of keys, allowing for the creation of new key pairs as needed. This makes HD wallets more flexible than other types of deterministic wallets, as they can generate new addresses on the fly and still be able to track all transactions associated with a single wallet. For instance, the tree structure can be used to express additional organizational meaning, such as when a specific branch of subkeys is used to receive incoming payments and a different branch is used to receive change from outgoing payments.
Mnemonic words (BIP-39)
Modern Bitcoin wallets provide users with a mnemonic or seed phrase. This consists of 12-24 English words, selected randomly by the software, and used as the basis for the keys that are generated by the wallet. This phrase can be used by users to restore all the transactions and funds in their wallet in the case of an event such as a lost mobile or hardware device, a software bug, memory corruption…
The BIP-39 standard defines a set of 2048 words, each represented by a unique 11-bit number. To generate a seed phrase, a random sequence of words is selected from the list of 2048 words.
The number of words selected determines the strength of the seed phrase. For example, a 12-word seed phrase provides 128 bits of entropy, which is considered secure for most purposes.
Bitcoin multisignatures
In Bitcoin, a multisig or multi-signature address is a Bitcoin address that requires multiple signatures in order to spend the funds associated with it.
In order to create a multisig address, multiple public keys are required, along with a set number of required signatures. For example, a 2-of-3 multisig address would require three public keys and two of those keys to sign off on a transaction in order for it to be valid.
Multisigs in Bitcoin are implemented using a type of script called Pay-to-Script-Hash (P2SH) that enables the creation of more complex transactions than the standard Pay-to-Public-Key-Hash (P2PKH) script. P2SH allows a transaction to be locked to a specific script, and that script can be a multisig script that requires multiple signatures to spend the funds.
While a multisig transaction does involve the use of a script, it is not considered a smart contract in the traditional sense. Smart contracts typically involve more complex logic and can execute more than one transaction based on certain conditions. Multisigs are generally considered to be a basic type of script that allows for increased security and control over funds.
Bitcoin nodes
Bitcoin nodes are the backbone of the Bitcoin network. They are computers that run Bitcoin software and help to verify transactions and maintain the integrity of the network by enforcing the rules of consensus. These nodes store a copy of the blockchain and communicate with each other through the Bitcoin protocol. By running a node, users are capable of verifying bitcoin balances without relying on a trusted third party.
When a new transaction is initiated, nodes on the network validate the transaction by checking its authenticity, ensuring that the sender has sufficient funds, and verifying that the transaction adheres to the rules of the Bitcoin protocol. Also, when a new block is added to the blockchain, nodes validate the block to ensure that it adheres to the consensus rules. If a block is found to be invalid, nodes on the network will reject it, ensuring that only valid blocks are added to the blockchain.
There are several different types of nodes on the Bitcoin network:
- Full nodes store a complete copy of the blockchain.
- Pruned nodes store a subset of the blockchain that includes the latest transactions.
- Light nodes, also known as SPV or Simplified Payment Verification nodes, do not store a copy of the blockchain but instead rely on full nodes to validate transactions.
Why run a full node?
- To independently verify the state of the network as well as the bitcoin supply.
- To prevent double spending of bitcoin.
- To participate in the Bitcoin protocol without relying on intermediaries.
- To make the network more robust. As more nodes validate transactions, the network becomes more resistant to certain types of attacks.
Because all nodes check, no miners can cheat the system. If all nodes didn’t check you’d have to rely on the ones that do check.
User security best practices
- Use a strong and unique password for all Bitcoin-related accounts, and consider using a password manager to generate and store passwords.
- Enable two-factor authentication (2FA) on all accounts that support it. 2FA adds an extra layer of security by requiring a second factor, such as a code generated by a mobile app or sent via text message, in addition to your password.
- Keep your software and devices up to date with the latest security patches and updates. This includes your computer, mobile device, and any wallets or other software that you use to manage your Bitcoin.
- Use a hardware wallet to store your bitcoin. Hardware wallets will store your private keys and are not connected to the internet, making them much more secure than software wallets.
- Diversify risks and don’t hold all your bitcoin in a single wallet.
- Consider using multisignature wallets, especially if you are a business or store large amounts of bitcoins. The signing keys should be stored in a number of different locations and under the control of different people. In a corporate environment, for example, the keys should be generated independently and held by several company executives, to ensure no single person can compromise the funds. Multisignature addresses can also offer redundancy, where a single person holds several keys that are stored in different locations.
- Be cautious of phishing scams and other forms of social engineering. Hackers may try to trick you into giving up your private keys or other sensitive information by posing as a legitimate service provider or using other tactics.
- Keep your private keys and seed phrases in a safe and secure location, and never share them with anyone else. Your private keys are essentially the keys to your Bitcoin, so it’s important to keep them safe and secure at all times.
Why does Bitcoin have value?
Bitcoin’s value is derived from its use as a decentralized digital currency. The network is not backed by any physical asset or government. Instead, it has some attributes that are usually associated with money: unit of account, medium of exchange, and store of value.
“The price of any commodity tends to gravitate toward the production cost. If the price is below cost, then production slows down. If the price is above cost, profit can be made by generating and selling more. At the same time, the increased production would increase the difficulty, pushing the cost of generating towards the price.” – Satoshi Nakamoto
Some people argue that Bitcoin has intrinsic value due to the energy and resources required for mining and securing the network, while others argue that its value is purely extrinsic and derived from market demand. Ultimately, Bitcoin’s value is determined by the collective perception and trust of its users, as well as its potential to disrupt traditional financial systems.
The article “Shelling Out: The Origins of Money” by Nick Szabo discusses the concept of money and its origins. Szabo argues that money is a social construct that emerged from a need for trust and cooperation between individuals. He believes that money originated from the use of shells as a medium of exchange, and over time, evolved into more sophisticated forms of currency such as gold and paper money.
Scarcity
Bitcoin is designed to be a scarce asset. Only a maximum limit of 21 million bitcoins will ever exist. This scarcity creates a sense of scarcity value, similar to other valuable assets like gold.
Dictionaries usually define scarcity as ‘a situation in which something is not easy to find or get’, and ‘a lack of something’.
Bitcoin is the only asset in the universe that has a mathematical scarcity. Elements like gold are naturally scarce on Earth; however, there are trillions of dollars worth of gold floating around on asteroids in our solar system that may one day be accessible to humans, significantly inflating the gold supply.
As demand for bitcoin increases while the supply of available units remains fixed, the scarcity of the asset contributes to its perceived value.
The principle of supply and demand suggests that when the supply of a particular asset is limited, while the demand for that asset is high, the price of that asset will increase.
“A rational market price for something that is expected to increase in value will already reflect the present value of the expected future increases. In your head, you do a probability estimate balancing the odds that it keeps increasing.” – Satoshi Nakamoto
Nick Szabo quotes
“What do antiques, time, and gold have in common? They are costly, due either to their original cost or the improbability of their history, and it is difficult to spoof this costliness. [..] There are some problems involved with implementing unforgeable costliness on a computer. If such problems can be overcome, we can achieve bit gold.” — Szabo in a 2005 blog post titled “Antique times, gold and bit gold“
“Precious metals and collectibles have an unforgeable scarcity due to the costliness of their creation. This once provided money the value of which was largely independent of any trusted third party. [..][but] you can’t pay online with metal. Thus, it would be very nice if there were a protocol whereby unforgeably costly bits could be created online with minimal dependence on trusted third parties, and then securely stored, transferred, and assayed with similar minimal trust. Bit gold.” — Szabo in a 2005 blog post titled “Bit gold”.
Decentralization
Bitcoin is not controlled by any central authority or government. By operating on a decentralized network of nodes that collectively validate and record transactions, Bitcoin provides users with benefits such as:
- Increased security, because it is more difficult for any one entity or authority to control or manipulate the system.
- Increased privacy, because there is no central authority collecting and storing user data.
- Resilience, because the network can continue to operate even if some nodes go offline or are compromised.
- Auditability, because all transactions are stored on a public ledger that is visible to anyone.
“Governments are good at cutting off the heads of centrally controlled networks like Napster, but pure P2P networks like Gnutella and Tor seem to be holding their own.” -– Satoshi Nakamoto.
Transparency
As a transparent and public ledger that records all transactions on the network, anyone can view and audit the current and past states of the network. This offers benefits such as:
- Accountability. Because all transactions are publicly recorded, it is more difficult for individuals or organizations to engage in fraudulent or illegal activities on the network without being caught.
- Trust. Because the protocol provides a clear and verifiable record of all transactions on the network.
- Efficiency. Because the blockchain eliminates the need for intermediaries or third parties to verify transactions.
Monetary policy
- Fixed supply limited to 21 million coins.
- Predictable inflation. Unlike fiat currencies, where central banks can adjust the money supply at will, Bitcoin’s inflation rate is predetermined and will decrease over time. This predictability makes it easier for investors and users to plan and make informed decisions about the currency.
- Decentralized control. No one entity can manipulate or control the currency.
- Consensus-driven. Changes to Bitcoin’s monetary policy require consensus among the network of nodes and miners, ensuring that any changes are made in a transparent and democratic manner.
“Banks must be trusted to hold our money and transfer it electronically, but they lend it out in waves of credit bubbles with barely a fraction in reserve. We have to trust them with our privacy, and trust them not to let identity thieves drain our accounts. Their massive overhead costs make micropayments impossible.” – Satoshi Nakamoto
Portability
Unlike traditional forms of currency, which are often subject to restrictions and regulations when being moved across borders, Bitcoin can be sent to anyone, anywhere, at any time, with relatively low transaction fees.
This is enhanced by the fact that it can be stored in digital wallets on various devices, such as smartphones, laptops, and hardware wallets. This means that users can carry their Bitcoin with them wherever they go, without the need for physical cash or cards.
Divisibility
The divisibility of bitcoin makes it a practical and versatile form of currency. Bitcoin can be divided into very small units, with the smallest unit of a bitcoin being a Satoshi (0.00000001 BTC). This level of divisibility allows for precise and accurate transactions, even for very small amounts.
Divisibility is also important because it enables the currency to be used for a wide range of transactions, from small purchases to large-scale investments. It also makes it possible for Bitcoin to be used in situations where traditional forms of currency may not be practical or possible, such as micropayments, online purchases, and cross-border transactions.
Security
Bitcoin transactions are secured by the use of cryptography and a decentralized network of nodes that validate and confirm transactions. This makes it difficult to counterfeit or double-spend bitcoins, making them more secure than traditional forms of payment.
Utility
Bitcoin has a number of practical uses, such as being used as a means of payment or as a store of value.
It can be used to purchase goods and services, send money internationally, and invest in as an asset.
Additionally, its decentralization and anonymity can be appealing to those who value privacy and independence from centralized financial institutions.
It is also extremely difficult to censor bitcoin transactions. Anyone with an internet connection and that agrees to pay the network’s fee, has freedom to transact with anyone on the network.
Revenue Streams
Block rewards are critical to incentivizing miners in the early years, but as the block reward shrinks in size, miners will need to draw revenue from transaction fees. These rewards are the incentive for miners to use processing power in order to try and add a new block of transactions onto the blockchain.
The block reward is the combination of the block subsidy and all transaction fees paid by transactions in a specific block.
The block subsidy is the amount of newly created bitcoin in each block. This amount is halved every 210,000 years (roughly 4 years).
Miners receive transaction fees in addition to block rewards for processing network transactions. Because of this, the profitability of mining is also impacted by the level of transaction fees, which may change depending on network activity and other elements.
Mining revenue is calculated by multiplying the amount of bitcoins that have been mined by the market price of BTC. As a result, the amount of revenue made by a cryptocurrency mining business fluctuates based on the price of BTC, the difficulty of the mining process, the price of electricity, and the effectiveness of the mining equipment being utilized.
Economics
In terms of mining, competition has increased as more miners have entered the market, making it more challenging and less viable for individual miners to produce income. As a result, large mining corporations have grown increasingly popular as a result, as they can take advantage of economies of scale to lower costs and boost profitability. These mining pools operate using specialized mining hardware in order to improve their performance.
Mining pools aggregate pool members’ hashes and submit successful proof of work to the network. The rewards are distributed to contributing miners proportionally to the amount of work performed.
At the same time, governments from all over the world are becoming more interested in regulating the cryptocurrency market and mining operations, especially due to environmental concerns. Some nations have embraced cryptocurrency mining and made advantageous regulatory settings for miners, while others have taken a more antagonistic attitude, restricting or even prohibiting mining operations.
Mining hash rate
The chart shows an estimate of how many hashes per second bitcoin miners are performing on the network.
Estimate = difficulty * 232 / time.
The bitcoin network has a global block difficulty that adjusts every 2016 blocks (~2 weeks) based on a target time of 10 minutes per block. As difficulty increases, more hashpower must be added to have the same statistical chance of finding a block. The time between bitcoin blocks can vary dramatically if there is a large increase or decrease in hashpower within this 2 week period.
Total Bitcoin supply
HODL Waves
The HODL waves show the amount of bitcoin in circulation grouped into different age bands (each band is represented with a different color). The chart shows the total supply of bitcoin in the market at any given time by normalizing the supply distribution.
This visualization highlights what different market participants are doing with their bitcoin. For example, sharp increases in lower age coins being held indicate that a lot of older bitcoins are being sold by people who have held them for a long time, and are now being bought up most likely by new participants in the market.
Stock-to-flow model
The stock-to-flow model is a price forecasting tool. It creates a line on the chart above that shows an estimated price level based on the number of bitcoins available in the market relative to the amount being produced (mined) each year. The score on the stock to flow line is the forecasted price for bitcoin at that particular time.
As the amount of bitcoins to be mined decreases over time, the stock to flow number (s2f ratio) increases, due to the decreasing supply available on the market. That is why this model is forecasting that the price of Bitcoin will increase in the future.
Note that the stock-to-flow model treats Bitcoin as being comparable to commodities and precious metals such as gold, silver, or platinum. These are known as ‘store of value’ commodities because they retain value over long time frames due to their relative scarcity.
Pi Cycle Top indicator
The Pi Cycle Top Indicator has historically been effective in picking out the timing of market cycle highs. It uses the 111 day moving average (111DMA) and a newly created multiple of the 350 day moving average, the 350DMA x 2.
For the past three market cycles, when the 111DMA moves up and crosses the 350DMA x 2 we see that it coincides with the price of Bitcoin peaking.
This indicator attempts to predict the point where the price of BTC will peak before pulling back.
The Pi Cycle Top is useful to indicate when the market is very overheated (so overheated that the shorter term moving average, which is the 111 day moving average, has reached a x2 multiple of the 350 day moving average). Historically it has proved advantageous to sell Bitcoin at this time in Bitcoin’s price cycles.
Fear and greed index
The fear and greed index identifies the extent to which the market is becoming overly fearful or overly greedy.
The idea is that when the market is generally overly fearful, it may indicate that Bitcoin is cheap/undervalued at that time and could present a good buying opportunity. The reverse also applies, meaning that when the Fear and Greed Index is signaling market participants are extremely greedy, it may indicate the price of Bitcoin is too high above its intrinsic value and it could be a good time to sell.
Bitcoin profitable days
The chart below shows the number of days in Bitcoin’s traded history where holding Bitcoin has been profitable relative to today’s price.
This indicator demonstrates how Bitcoin price has accelerated over its lifetime as it becomes adopted by more and more people around the world.
MVRV Z-Score
The MVRV Z-Score is a bitcoin chart that uses blockchain analysis to identify periods where Bitcoin is extremely over or undervalued relative to its ‘fair value’.
To do that, it uses 3 metrics:
- Market value (blue line) shows the current BTC price multiplied by the number of coins in circulation (market cap).
- Realized value (orange line) takes the price of each BTC when it was last moved (i.e. the last time it was sent from one wallet to another wallet) and then adds up all those individual prices and takes an average of them. It then multiplies that average price by the total number of coins in circulation.
- Z-score (red line) is a standard deviation test that pulls out the extremes in the data between market value and realized value.
The MVRV Z-score has historically been very effective in identifying periods where market value is moving unusually high above the realized value. These periods are highlighted by the z-score (red line) entering the pink box and indicating the top of market cycles.
This indicator also shows when the market value is far below the realized value, which is highlighted by the z-score entering the green box.
Bitcoin exchange reserves
Bitcoin distribution by addresses
The average amount of bitcoin held by addresses ranges from 0.000001 to 0.1 bitcoin.
There are only 5,577 addresses with a significant amount of Bitcoin amounting to around $10 million.
Of the top 10 biggest BTC wallets, 4 are linked to known entities such as Binance and BitFinex, while the rest are anonymous.
Bitcoin miner pool distribution
The majority of miners are under Foundry USA, followed by AntPool, F2Pool and Binance.
Bitcoin nodes geographical distribution
It can be seen that despite regulation uncertainties and difficulties, the majority of Bitcoin nodes are still from the United States, amounting to 29.99%. Germany has roughly half of the nodes compared to the United States at 13.56%, with the rest of the other countries presenting single digit percentages.
Network fees
In the Bitcoin network, fees are paid to incentivize miners to include transactions in the blocks they mine. Miners prioritize transactions with higher fees since they earn more money for their efforts. As a result, fees are not fixed and can vary depending on the number of transactions waiting to be processed and the amount of competition for block space.
When creating a Bitcoin transaction, the sender can specify a fee they are willing to pay in satoshis per byte (sat/B). The higher the fee, the faster the transaction is likely to be confirmed. If the fee is too low, the transaction may not be confirmed for a long time or may never be confirmed at all.
Wallets often have a feature that automatically calculates an appropriate fee based on the current network conditions. Some wallets may allow users to manually set the fee.
Note that higher fees do not necessarily guarantee faster confirmations, as there may be other factors at play such as network congestion or low hash rate.
Operating Expenses
Miners usually exert sell pressure on the market by selling the block rewards to cover their high operating costs. When these rewards are cut in half, sell pressure may also decrease, yielding a price rise.
Before the advent of specialized bitcoin mining software, early miners used their personal computers and were able to generate a profit. As a result, the equipment and operating costs were negligible. Over time, more professional bitcoin mining centers emerged to provide users with more computing power. In 2013, a China-based computer hardware manufacturer called Canaan Creative released the first set of ASIC (Application-specific integrated circuits) for bitcoin mining. As individuals started competing against more powerful mining rigs with more computing power, the mining profits started getting slashed by the growing expenses for computing equipment, higher energy costs, and the continued difficulty for mining.
Nowadays, Bitcoin mining remains a profitable activity for some individuals and corporations. Mining equipment is accessed more easily, although its costs vary from a few hundred dollars up to about $10,000. To remain competitive, these businesses try to lower their energy requirements, thus bringing down their overall costs.
In order to compete against big mining centers, individuals can join mining pools, where a group of miners will work together and share the rewards. Even though the overall reward decreases when it is distributed between multiple participants, the combined mining power means that mining pools stand a much greater chance of adding the next block to the chain.
The costs associated with participating in Bitcoin mining can be broken down into the following categories:
- Hardware costs associated with specialized ASICs.
- Energy expenses due to the substantial quantity of electricity that is required to run the computing equipment.
- Cooling costs, since the heat produced by mining equipment needs to be dispersed in order to keep the machinery in good condition.
- Maintenance and repair costs.
View a higher resolution version of this map.
- It takes an estimated 1,449 kilowatt hours (kWh) of energy to mine a single bitcoin. That’s the same amount of energy an average U.S. household consumes in approximately 13 years.
When evaluating a bitcoin miner’s total cost of production relative to their competitors it is important to consider whether or not the company owns its own infrastructure or relies on a hosting provider through co-location.
If a miner largely operates machines through co-location then it will likely have lower depreciation expense than a company that owns its own infrastructure and thus has to depreciate it. Over time, as miners’ margins decrease, vertically integrated miners will have better cost to mine since they have longer-term control over power costs.
Definitions for costs estimation
- The Marginal cost of production represents the electricity and hosting costs to produce 1 bitcoin. However, this does not capture the capital expenditure on mining equipment.
- The marginal cost of production for a publicly traded Bitcoin miner is calculated by dividing the cost of revenues (excluding equipment depreciation expenses( by the number of bitcoins mined during a period of time
- The direct cost of production includes depreciation expenses in the calculation in order to give a sense of how much a miner is spending on ASICs. When derived from filings, this figure may also include depreciation of hosting facilities for their machines, depending on the level of detail included in the filing.
- The direct cost of producing a bitcoin is calculated by adding the cost of revenues and the depreciation expenses from the income statement and then dividing by the number of bitcoins mined during a period of time.
- The total costs of production account for the overhead of running the business, including the payroll of employees. This calculation excludes any non-cash or one-time expenses, such as impairments on marketable securities or employee-based stock compensations.
- The total direct and indirect cost of producing a bitcoin for a publicly traded bitcoin miner is calculated by adding the cost of revenues, depreciation expenses, and administrative expenses and dividing by the number of bitcoins mined during a period of time.
- The cost of production margins are calculated by dividing the difference between the cost of production and the average market price of bitcoin through a period of time by the average market price of bitcoin.
- For example, if a publicly traded mining company’s total cost of production margin is 30%, then they are able to generate bitcoin at a 30% discount to the average market price of bitcoin based on their full expense load.
How many bitcoins have been lost?
Diving into one of the earliest backups of Bitcoin’s code shows that the supply was effectively set at 21M BTC. Bitcoin’s codebase does not contain any checks that BTC’s supply does not exceed 21M. Instead, the software checks that each block doesn’t claim more than the prescribed number.
The mining of block 600,000 was celebrated by the community as a milestone towards the end of the inflation process for Bitcoin. Applying the supply formula to get supply value at block 600,000 on October 19, 2019 gives 18M BTC.
However, Pieter Wuille, Bitcoin Core developer, mentioned that the actual supply as of block 600,002 was 17,999,854.82192702 BTC. As a result, there was a shortage of BTC, which can be attributed to the following reasons:
- Probably Lost
- Genesis coins
- Duplicate Coinbase transactions
- Unclaimed rewards
- OP_RETURN outputs
- Assumed Lost
- Bogus addresses
- Bugs
- Zombie coins
- Encumbered coins
Genesis Coins
Bitcoin’s ledger is made of a set of “unspent outputs” otherwise referred to as the Unspent Transaction Outputs set, or UTXO set. Summing up those outputs’ BTC values give you the Bitcoin supply as seen by a full node. For example, Bitcoin’s first block, the genesis of its history, contains a transaction minting 50 BTC.
However, this transaction’s 50 BTC output isn’t included in the UTXO set. It’s still unclear whether it was an oversight or done on purpose. The result is that those 50 BTC are not present in Bitcoin’s ledger, even if they are visible in a transaction included in the main chain.
Duplicate Coinbase transactions
Another oversight from Bitcoin’s designer is the handling of duplicate transactions. While at first glance, it doesn’t seem possible for them to occur (as they contain digital signatures and references to previous transactions which makes them unique), it is still possible to create duplicate transactions.
The easiest transactions to duplicate are the coinbase transactions, which are the first transactions of every block and allow the miner to claim their block reward (the company Coinbase is named after these coinbase transactions), because they do not contain digital signatures or references to previous transactions. If a miner were to create a coinbase transaction paying out the exact same amount of BTC to the same addresses and with the same extra nonce (a small space of the coinbase transaction used to help mining), the transaction would be identical.
Coinbase transactions are a special type of transaction that signal the creation of new currency units as part of the block rewards process. In other words, each coinbase transaction is responsible for transmitting the newly minted coins to the miner who has resolved the block. Thus, the total base value of a transaction coinbase, contains only and exclusively new currencies that have never been in the blockchain.
This happened twice in Bitcoin’s early history:
- Transaction d5d2..8599 was the Coinbase output for blocks 91,812 and 91,842
- Transaction e3bf…b468 was the Coinbase output for blocks 91,722 and 91,880
In each case, the second time the transaction was included, its outputs overwrote the previous ones. The result is that the two overwritten outputs are not in the UTXO set. Those 100 BTC are not in Bitcoin’s ledger. While appearing like an innocuous oversight, Russell O’Connor identified this as an attack vector back in 2012. Leveraging duplicate transactions, an attacker could remove other user’s past transactions from the ledger.
In response to this, BIP-30 was introduced in 2012 to forbid new duplicate transactions to be included until the older transaction’s outputs are all spent. However, the handling of the existing duplicates was not changed and they still remain in the chain to this day.
Later in 2012, BIP-34 also made duplicating coinbases much more difficult as they now had to include the height of the block they are part of.
Unclaimed rewards
Another set of provably lost coins is linked to the verification of coinbase transactions by full nodes.
The Bitcoin protocol mandates that the miner of a valid block can credit themselves with a protocol-defined reward plus the fees from the transactions included in that block. Each full node checks that miners don’t try to claim more than they are allowed. However, they do not care if the miner claims less than their share.
Obviously, claiming less than their allotted reward would not be rational behavior from miners, but it has happened a surprisingly large number of times. The first time it occurred was at block 124,724 in May 2011 and the last time thus far at height 564,959 in late February 2019.
The most notable cases are listed in this table:
| Block Height | Unclaimed BTC |
| 501726 | 12.5 BTC |
| 526591 | 6.25 BTC |
| 164441 | 1.75780069 BTC |
Broadly, this behavior happened in 3 distinct episodes, totaling 1,221 anomalies. The following chart shows the number of blocks that did not claim their full reward, bucketed by 1000 blocks:
One very intense episode occurred around height 162,000. Another more prolonged one occurred from 180,000 to 230,000 and a last one around block 530,000.
According to Bitcointalk user midnightmagic, the first instance was done on purpose as a tribute to Satoshi Nakamoto, on a suggestion of Bitcoin developer Matt Corallo. For the other cases, given the amounts lost by some miners, they are most likely attributable to bugs in the software used by miners to create the coin generation transaction.
OP_RETURN Outputs
There’s a special type of Bitcoin transaction output called OP_RETURN. They allow users to embed data in the blockchain (up to 80 bytes per output at the moment) without bloating the UTXO set (those outputs do not get added to the UTXO set − they are considered provably unspendable).
While the great majority of such outputs are created with a value of 0 satoshis, some aren’t. As of block 600,000, there were 3.723039 BTC sent to OP_RETURN outputs, making them unspendable forever, and not part of Bitcoin’s supply.
Bogus Addresses
Prior to the standardization of OP_RETURN outputs, there was no easily accessible, provable way to burn Bitcoin. As a result, users resorted to “bogus addresses”, which is an address that does not have a known private key.
When creating a Bitcoin address, the process usually starts from a known private key, that is then transformed to derive the public key address it corresponds to. This process makes it very difficult to generate custom “vanity prefixes” (i.e. vanity public keys) − you basically have to “mine” private keys to find ones whose address starts with the desired prefix.
However, in the case of bogus addresses, there’s no desire to ever actually spend from the address, so there’s no need to know what the private key is. Therefore the bogus address can start with any prefix (if it can be written using the Base58 alphabet). However, the last characters will be random (by design, the last characters of an address are a checksum to prevent typos).
While it is impossible to draft a complete list of bogus addresses, we can list some notable ones:
| Address | Balance | Comment |
| 1BitcoinEaterAddressDontSendf59kuE | 13.22477678 | Well known bogus address |
| 1CounterpartyXXXXXXXXXXXXXXXUWLpVr | 2130.87057997 | Counterparty burn |
| 1111111111111111114oLvT2 | 69.10002337 | Smallest address possible |
Just those 3 addresses account for 2213.19538012 BTC lost as of block 600,000.
In theory, those coins are not lost forever − someone could find a private key for them. However, the only known way to find a private key given only an address is to randomly guess until you find the right combination (i.e. through bruteforce). In practice, the chance of that happening in the lifetime of our universe is pretty slim.
Bugs
Beneath the beautiful veneers of today’s wallets, there are critical pieces of code responsible for crafting, signing and broadcasting our transactions to the Bitcoin network. Nowadays, it’s rare to find debilitating bugs in them, but that wasn’t always the case.
In November 2011, MtGox fell victim to a bug in this part of their software. They sent 2609.36304319 BTC to a bogus script, with no known way to spend it. The bogus script was what would happen if you tried to send money to an “empty” public key with software not programmed to detect that this is not desirable.
There have been other similar bugs in other assets that rendered coins unspendable, most notably in Ethereum with the Parity self-destruct issue (513k ETH lost).
Zombie Coins
Another source of lost coins are the ones that haven’t moved in many years. As it’s impossible to know whether their owners still have the keys or don’t, they are often called “zombie coins”, neither alive nor dead. With this category, we leave the domain of quasi-certainty about whether the coins are truly lost.
To stay conservative in our estimate, we’ll only count coins last touched before Bitcoin was traded on the first exchanges (July 2010). The rationale is simple: people that acquired Bitcoins before they could be traded away had less of an incentive to back up their wallets as the perceived value of Bitcoins (at the time) was very low.
At block 600,000, there were 1,496,907.88000 BTC last touched prior to July 2010. According to various estimates, Satoshi Nakamoto purportedly owns more than half of those coins due to their status as the dominant miner for most of Bitcoin’s very early history.
The last time coins last touched prior to July 2010 were moved was in July 2019, when 150 BTC were spent.
Overall, since the 2013 bull run, those coins have been very rarely spent. Given the price appreciation from 2013 to now, either the owners of those coins are very long-term oriented holders, or they don’t have access to these coins.
Encumbered Coins
There’s one final category of coins that could be considered lost, or at least out of circulation for the time being: known stolen coins. Until the advent of better mixing solutions (which is effectively similar to money laundering, making it much more difficult to follow the money trail), they will be difficult to insert back into circulation, especially for very large amounts.
There’s been many major hacks and thefts over Bitcoin’s history, but two jump to mind as “out of circulation” – the 2011 theft of 80k BTC from MtGox and the 2016 theft of 120k BTC from Bitfinex.
In March 2011, 79,956 BTC were withdrawn from MtGox’s wallet, and have not been touched to this day. As of today, it’s the 6th richest address.
The reason why this haul (worth $73k at the time it was stolen, $700M today) was never spent is unknown. Most likely, the thief is unable to access the private key.
In August 2016, Bitfinex lost 119,756 BTC to a hack. To this day, very few of these stolen coins have been moved and only 22 BTC were recovered. As of block 600,000, the addresses where the stolen coins were sent to still held 117,091.31922097 BTC.
Governance
Bitcoin governance refers to the mechanisms and processes through which changes to the Bitcoin protocol are proposed, debated, and implemented. Unlike traditional forms of governance, such as centralized decision-making by a government or corporation, Bitcoin governance is meant to be decentralized and relies on the consensus of its users.
There is no central authority that governs the Bitcoin network, so changes to the protocol are proposed and discussed by the community of users and developers. Changes are implemented through a process known as a “soft fork” or a “hard fork”, which requires a majority of users to adopt the new protocol rules.
Bitcoin is also based on the principles of open source software development, where anyone can contribute to the codebase and propose changes. However, due to the decentralized nature of the Bitcoin community, governance can be challenging and often contentious, as different groups may have conflicting interests and ideas about how the protocol should evolve.
The Bitcoin governance process maintains a set of verification rules. At a high level, this long set of verification rules covers syntax, data structures, resource usage limits, sanity checks, time locking, reconciliation with the memory pool and main branch, the coinbase reward and fee calculation, and block header verification. Most of these rules were inherited from Satoshi Nakamoto, although some have been added or amended to address bugs and denial-of-service vulnerabilities.
Proposals
When a researcher has discovered a solution to a problem, they share their proposed changes with other protocol developers, either in the form of an email to the bitcoin-dev mailing list, a formal white paper, and/or a Bitcoin Improvement Proposal (BIP).
Implementation
In the Bitcoin network, proposals are executed through a process called “rough consensus.” This means that proposals are discussed and debated among the community of developers, miners, and users until a general agreement is reached on the direction to take. There is no formal voting process, but proposals that are generally agreed upon are implemented by developers who create and release new versions of the Bitcoin software.
Changes to the Bitcoin protocol are proposed in the form of “Bitcoin Improvement Proposals” (BIPs), which are submitted to the community for discussion and review. If a proposal gains enough support and is deemed to be technically feasible and beneficial for the network, it may be implemented in a new version of the software. However, the implementation of a proposal ultimately depends on whether the community adopts the new version of the software or not.
While there is no central authority governing Bitcoin, there are various organizations and individuals that have significant influence on the network. These include developers who contribute to the core Bitcoin software, mining pools that collectively control a significant portion of the network’s hash power, and exchanges and other businesses that provide services to Bitcoin users.
Risks
The security model of Bitcoin is based on the decentralized network of nodes and miners, as well as the underlying cryptographic protocols used to secure the system.
In terms of the network, Bitcoin relies on a decentralized system of nodes and miners to validate transactions and maintain the integrity of the blockchain. Nodes are responsible for relaying transactions and blocks to each other, and verifying their validity, while miners are responsible for adding new blocks to the blockchain through the process of mining. The decentralized nature of the network means that there is no single point of failure or control, and no single entity can manipulate the system without consensus from the network.
However, there are some other risks that have an impact on Bitcoin’s integrity:
- Security risks. While the Bitcoin protocol is designed to be secure, there have been instances in the past where exchanges and wallets have been hacked, resulting in the loss of user funds. Most of the time, this is not an inherent problem of the protocol itself, but rather the result of users that trust third parties with their own funds due to the responsibility that comes with keeping one’s funds under custody. However, Bitcoin is still exposed to malware and hacking attempts that might disrupt the network.
- Regulatory risks: Bitcoin is decentralized and operates independently of any central authority. This has made it difficult for regulators to create laws that apply to Bitcoin. The lack of regulation often means that Bitcoin is more susceptible to scams and fraud.
- Price volatility: The price of Bitcoin can be extremely volatile, with large fluctuations occurring over short periods of time. This makes it difficult for businesses and individuals to use Bitcoin as either a store of value or medium of exchange.
- Mining centralization: The mining process for Bitcoin relies on a decentralized network of nodes to validate transactions and generate new coins. However, in recent years, there has been a concentration of mining power in the hands of a few large mining pools. This has raised concerns about the centralization of the Bitcoin network.
- Energy consumption: The mining process for Bitcoin requires a significant amount of energy. This has led to criticism of Bitcoin for its environmental impact.
- Adoption risks: While Bitcoin has gained significant adoption in recent years, it is still not widely used as a medium of exchange and its use comes mostly from speculation. This limits its usefulness as a currency and makes it more vulnerable to speculative bubbles.
Security
The core principle in Bitcoin is decentralization, and this has important implications for security. As a permissionless and censorship-resistant system, Bitcoin pushes the responsibility and control of the network to the users. Because security of the network is based on Proof-of-Work, not access control, the network can be open and no encryption is required for network traffic.
Contrary to payment networks that have to be secured end-to-end in order to ensure that no intermediaries can compromise the payment traffic, Bitcoin is dramatically different. A bitcoin transaction authorizes only a specific value to a specific recipient and cannot be forged or modified. It does not reveal any private information, such as the identities of the parties, and cannot be used to authorize additional payments. Therefore, a bitcoin payment network does not need to be encrypted or protected from eavesdropping. In fact, you can broadcast bitcoin transactions over an open public channel, such as unsecured WiFi or Bluetooth, with no loss of security.
The architecture of Bitcoin is very different from traditional software systems from a security point of view. In traditional systems, the security architecture is built upon a concept called the root of trust. As these systems become more complex, they are more likely to contain errors, which makes them more vulnerable to security compromises. The root of the trust concept ensures that most of the trust is placed within the least complex part of the system. However, this is not the case in Bitcoin. Bitcoin’s consensus mechanism creates a trusted public ledger that is completely decentralized. Ultimately, the only thing that should be explicitly trusted is its fully validated blockchain
Nevertheless, Bitcoin is not immune to security risks, such as:
- 51% Attacks: A 51% attack occurs when a single miner or group of miners controls more than 51% of the total computing power of the Bitcoin network. This would give them the ability to manipulate the blockchain, approve fraudulent transactions, and potentially double-spend bitcoins.
- Sybil Attacks: A Sybil attack is a type of attack where a single user or group of users creates multiple identities or nodes to control the network. This could be used to manipulate the network by approving fraudulent transactions or to prevent valid transactions from being approved.
- Malware and Hacking: Malware and hacking are significant risks to the Bitcoin network. Malware can be used to steal private keys, while hackers can attempt to exploit vulnerabilities in wallets, exchanges, and other components of the network.
- Centralization of Mining: The centralization of mining is a concern because it gives a small group of miners control over the network. This could potentially lead to censorship or manipulation of transactions.
- Quantum Computing: The development of quantum computing could pose a threat to the security of the Bitcoin network. This is because quantum computers could potentially break the cryptography that is used to secure the network.
The rules of consensus and the cryptography used by Bitcoin have been working since inception, which is a good indication that the concept and software architecture are well designed. However, minor security flaws have been found and fixed over time in various software implementations. Like any other form of software, the security of Bitcoin software depends on the speed with which problems are found and fixed. The more such issues are discovered, the more Bitcoin is gaining maturity.
There are often misconceptions about thefts and security breaches that have impacted exchanges or businesses. None of these events involve Bitcoin itself being hacked, nor reveal any inherent flaws in the protocol; just like a bank robbery doesn’t mean that the US dollar is compromised.
Bitcoin security flaws and vulnerabilities
The computational power behind the bitcoin blockchain can be explained as a function of the difficulty adjustment and rate of release of the blocks. This metric is a good insight into the security behind the Bitcoin blockchain. The higher the hash-rate, the more secure the network is.
The value overflow incident – August 15, 2010
The value overflow incident that occurred on August 15, 2010 was caused by a software bug that allowed a miner to create a block with an invalid transaction. Due to this bug, a miner managed to create 184 billion bitcoins, which was far beyond the maximum limit of 21 million bitcoins set by the Bitcoin protocol. This caused the Bitcoin network to reject the block and temporarily halt the creation of new blocks, leading to a brief period of uncertainty and concern among Bitcoin users.
To resolve the incident, the Bitcoin community agreed to a soft fork that would change the software code to fix the bug and restore the integrity of the blockchain. Within 5 hours of the discovery, a new version of the client was published. This version contained a soft-forking change to the consensus rules that rejected output value overflow transactions (as well as any transaction that paid more than 21 million bitcoins in an output for any reason).
Although many unpatched nodes continued to build on the “bad” block chain, the “good” block chain overtook it at a block height of 74691, at which point all nodes accepted the “good” blockchain as the authoritative source of Bitcoin transaction history.
The bad transaction no longer exists for people using the longest chain. Therefore, the bitcoins created by it do not exist either.
Potential security vulnerability in Windows version of Bitcoin-Qt
A critical vulnerability was discovered in the Bitcoin-Qt versions 0.5 through 0.6 on Windows, which could allow attackers to crash the process and possibly execute remote code. Bitcoin users were advised to upgrade to version 0.5.3.1 or 0.6rc4 to address the vulnerability. The vulnerability did not affect the command-line bitcoin daemon, Mac, or Linux versions of Bitcoin-Qt, or versions prior to 0.5.
CVE-2012-2459: Critical Vulnerability (denial-of-service)
A denial-of-service vulnerability that affected all versions of Bitcoin and Bitcoin-Qt. It was reported and fixed. An attacker could isolate a victim’s node and cause the creation of blockchain forks.
As a result, the latest version 0.6.2 has been released and users are strongly advised to upgrade. Backports for older releases, including 0.5.5 and 0.4.6, are also available for those who cannot upgrade to version 0.6.2.
15 May 2013 Upgrade Deadline
Bitcoin users were advised to upgrade to version 0.8.0 or later, install an up-to-date “backport” release, or modify a file and restart bitcoin before May 15, 2013. Failure to do so could result in being out of sync with the rest of the Bitcoin network, making it impossible to receive bitcoins, and risking being the victim of a “double-spend” attack. A recommendation was made to upgrade to version 0.8.1 before the 15th of May to avoid any issues. Solo miners or mining pool operators were provided with notes on how to upgrade safely.
If you cannot upgrade to any of the above, you can still avoid the problem. Create a file called DB_CONFIG in the bitcoin data directory, containing this line: set_lk_max_locks 537000
Android Security Vulnerability
The Android component responsible for generating secure random numbers has critical weaknesses, rendering all Android wallets generated to date vulnerable to theft. Bitcoin Wallet, blockchain.info wallet, BitcoinSpinner and Mycelium Wallet are among the affected apps. Updates have been prepared for these apps to address the vulnerability, and key rotation is necessary to re-secure existing wallets.
- Bitcoin Wallet: Update 3.15 can be installed from Google Play or Google Code. Key rotation will occur automatically soon after you upgrade. The old addresses will be marked as insecure in your address book. You will need to make a fresh backup.
- BitcoinSpinner: Update 0.8.3b can be installed from Google Play or Google Code. On startup it will advise you on how to proceed.
- Mycelium Bitcoin Wallet: Update 0.7.0 can be installed from Google Play or mycelium.com. A wizard will guide you through the process of moving your bitcoins to newly generated addresses, and put the old keys into archive mode.
- blockchain.info: Update 3.54 can be installed from Google Play. Version 3.54 and above includes an automatic re-keying wizard. Simply update to the latest version and follow the onscreen instructions. Please make a fresh wallet backup after the process completes.
If unable to update the Android app, users can send their bitcoins to a Bitcoin wallet on their computer until the app can be updated.
OpenSSL Heartbleed vulnerability
Bitcoin Core software versions 0.9.0 and earlier are affected by a bug in the OpenSSL library that can disclose memory to remote attackers. The bug is known as Heartbleed and more information can be found at
http://heartbleed.com/
. Users are urged to upgrade to version 0.9.1 of Bitcoin Core, which is linked with OpenSSL version 1.0.1g. If using official binaries, users can check the OpenSSL version in the Debug window of the Bitcoin Core GUI. Self-compiled versions and Ubuntu PPA users should update their system’s OpenSSL. Android version 4.1.1 is also vulnerable to Heartbleed, and users of Bitcoin Wallet on an Android phone should upgrade to version 3.45 or higher.
Some Miners Generating Invalid Blocks
A planned upgrade in 2015 affected the confirmation scores of Bitcoin transactions received after 2015-07-15 12:00 UTC for certain software users. Users should be aware of the following:
- Lightweight (SPV) wallet users should wait an additional 30 confirmations more than you would normally wait. Electrum users, please see this note.
- Bitcoin Core 0.9.4 or earlier users should wait an additional 30 confirmations more than you would normally wait or upgrade to Bitcoin Core 0.10.2.
- Web wallet users should wait an additional 30 confirmations more than you would normally wait, unless you know for sure that your wallet is secured by Bitcoin Core 0.9.5 or later.
- Bitcoin Core 0.9.5 or later users are unaffected. (Note: upgrade to 0.10.2 is recommended due to denial-of-service vulnerabilities unrelated to this alert.)
Miners are advised to switch to a pool that properly validates blocks or switch to Bitcoin Core 0.10.2 if solo mining.
Vulnerability in UPnP library used by Bitcoin Core
Users could either:
- turn off the checkbox in the GUI under Options → Network → Map port using UPnP (see above)
- add the line upnp=0 to their Bitcoin.conf file
- add -upnp=0 to the command line options
It was recommended to upgrade to a version of Bitcoin Core at least 0.10.3 or 0.11.1. These versions upgraded the library to a non-vulnerable version, as well as disabled UPnP by default to prevent this problem in the future.
Versions before 1.9.20151008 of the miniupnpc library are vulnerable to a buffer overflow in the XML parser during initial network discovery. The vulnerable code triggers at startup of Bitcoin Core if UPnP is enabled. Details of the vulnerability can be found here.
Releases starting from 0.10.3 and 0.11.1, and the upcoming 0.12.0 still shipped with a patched version of the library, but no longer enabled the functionality by default.
With UPnP turned off, the node will still connect to 8 other peers on the Bitcoin network in order to receive new blocks and transactions. However, it will not accept incoming connections from other peers unless the user manually enables port forwarding on their router. In order to do that, please follow these instructions.
0.13.0 Binary Safety Warning
Bitcoin.org has warned that state-sponsored attackers may target the binaries for the upcoming Bitcoin Core releases, and that they do not have the technical resources to defend against such attacks. Bitcoin.org has repeatedly asked the Bitcoin community, especially the Chinese community, to exercise caution when downloading binaries from their website. If the community does not take necessary precautions, downloading malicious software could lead to the loss of all coins, or participation in attacks against the Bitcoin network. The website has stated that Chinese services such as pools and exchanges may be most at risk due to the origin of the attackers.
The hashes of Bitcoin Core binaries are cryptographically signed with the key belonging to Bitcoin Core maintainer Wladimir J. van der Laan. Additional signatures from other developers can be found in the github signatures repository.
It was strongly recommended that users download Wladimir’s key from multiple sources in addition to Bitcoin.org for comparison purposes. For example, users can cross reference Bitcoin.org’s copy with the bitcoin-dev mailing list where Wladimir signed a message containing the key’s fingerprint (01EA5486DE18A882D4C2684590C8019E36C2E964), but are strongly encouraged to seek out other sources as well in order to make sure users are verifying download with the correct key. Furthermore, it was recommended that verifying downloads using signatures from multiple developers using the github signatures repository.
It is always a best practice to securely verify multiple signatures and hashes before running any Bitcoin Core binaries. This is the safest and most secure way to ensure that the binaries users are running are the same ones created by the Core Developers.
Beware of Bitcoin’s possible incompatibility with some major services
In 2017, several prominent businesses such as Coinbase, Xapo, and BitPay, agreed to adopt and implement a hard fork of Bitcoin, scheduled for November, which was not supported by the majority of users and developers. This agreement led to the creation of an alternative currency (altcoin) which is incompatible with Bitcoin, BCH or Bitcoin Cash. The signatories of this agreement believed that the new altcoin would eventually become Bitcoin, which turned out to be a wrong assumption. Users were advised not to store BTC on these services as their BTC may be renamed or replaced entirely with the new altcoin. The recommended way to protect BTC is to download the latest version of Bitcoin Core and transfer out any BTC stored on the signatory services. Users who don’t want to install Bitcoin Core are advised to use wallets like GreenAddress, Electrum or TREZOR, but avoid making transactions until well after the hard fork.
Notice of Required Upgrade to 0.16.3
A new release, version 0.16.3, was made available for download on bitcoin.org. Users were advised to update their nodes as soon as possible due to a severe bug that was fixed in this release. However, stored funds were never at risk, even if the bug had been fully exploited. Nonetheless, there was a small possibility of a chain split, which could cause confirmed transactions with less than 200 confirmations to be reversed. Users were advised to avoid this risk by updating to version 0.16.3 and verifying the authenticity of the download with GPG using the signing key and release signatures.
Below is a summary of the required action items:
- You should not run any version of Bitcoin Core other than 0.16.3. Older versions should not exist on the network. If you know anyone who is running an older version, tell them to upgrade it as soon as possible.
- It’s not necessary to immediately upgrade older versions if they are currently shut down. Cold-storage wallets are safe.
- Consider transactions with fewer than 200 confirmations to have a low probability of being reversed (whereas usually there would be essentially zero probability of transactions having six or more confirmations being reversed).
- Please watch for further news. If a chain split happens, additional actions may be required.
More information: CVE-2018-17144 Full Disclosure
Who is Satoshi Nakamoto?
The first bitcoin was mined on January 3, 2009, by a pseudonymous author known as “Satoshi Nakamoto”. The pseudonym was already a familiar name among cryptography enthusiasts like computer scientists and hackers long before the Bitcoin boom.
Three years after publishing the Bitcoin whitepaper and mining the Genesis block, Nakamoto sent an email to another Bitcoin developer on April 23, 2011, saying that he had “moved on to other things,” and that the cryptocurrency’s future was “in good hands.” Since then, there has been no communication from Nakamoto’s previously known email addresses.To this day, the identity of the person or group of people behind the whitepaper and the actual software is still unknown. Bitcoin remains open-source and no one has the power to own or control it in its entirety.
Over the years, a few individuals have been suspected of being the man behind the elusive pseudonym. Even though Nakamoto’s name is Japanese, and he stated in 2012 that he was a man living in Japan, most of the speculation has involved software and cryptography experts in the United States or Europe.
Nakamoto stated that work on the writing of the code for Bitcoin began in 2007. Months later, on August 18, 2008, he or a colleague registered the domain name bitcoin.org. On October 31 of the same year, Nakamoto published a white paper on the cryptography mailing list at metzdowd.com, describing a digital cryptocurrency, titled “Bitcoin: A Peer-to-Peer Electronic Cash System”. On January 9, 2009, the version 0.1 of the Bitcoin software was released, marking the beginning of the genesis block of bitcoin (block number 0), which had a reward of 50 bitcoins.
“The nature of Bitcoin is such that once version 0.1 was released, the core design was set in stone for the rest of its lifetime” – Satoshi Nakamoto
Embedded in the transaction of the Genesis block is the text: “The Times 03/Jan/2009 Chancellor on brink of second bailout for banks”, citing a headline in the UK newspaper The Times published on that date.
Nakamoto continued to collaborate with other developers on the bitcoin software until mid-2010, making all modifications to the source code himself. He then gave control of the source code repository and network alert key to Gavin Andresen, and transferred several related domains to various prominent members of the bitcoin community.
Dorian Nakamoto
In 2014, Newsweek journalist Leah Mcgrath Goodman published an article titled “The face behind Bitcoin”. This was an attempt to reveal Nakamoto’s identity. The journalist identified Dorian Nakamoto as the elusive Bitcoin creator.
This cited similarities between the two Nakamotos, including mathematical skill, Japanese descent and political leanings. At the time, Dorian Satoshi Nakamoto was a 64 years old living in Temple, California. Despite his expertise on computer engineering, Dorian denied any involvement with Bitcoin and dismissed any published quotes as a mere misinterpretation on the reporter’s part.
Later, Satoshi Nakamoto confirmed on an online Bitcoin forum that they are not Dorian Nakamoto — putting an end to the rumors.
Adam Back
Adam Back is a British computer scientist and cryptographer. He is best known as the creator of Hashcash, a proof-of-work system used to prevent spam and denial-of-service attacks, which was proposed in 1997 and later served as an inspiration for Bitcoin’s mining mechanism.
He is a classic cypherpunk and advocate for encryption technologies. Adam Back stands out for his expertise on distributed systems and mastery of C++. He was also one of the first two people to receive an email from Satoshi Nakamoto, although these emails have never been made public. This is the reason why many suspect that Adam could be Satoshi. Other reasons point to the British idioms used by both Satoshi and Adam as well as his writing style and C++ proficiency.
Nevertheless, Back only appeared in the BitcoinTalk in 2013, where he introduced himself and stated that does not own any bitcoin.
Back has denied being Nakamoto but remains a vocal advocate for privacy and has spoken out against government surveillance and the erosion of civil liberties. He is also known for his research on distributed systems, writing several papers and articles on the subject.
However, there are counter arguments against Adam being Satoshi. Despite being referenced in the Bitcoin white paper, Adam did not show much interest or have strong opinions about Bitcoin. He remained largely uninvolved until the first bull cycle in 2013, when he suddenly appeared and introduced himself on BitcoinTalk. While he claims to have no ownership of Bitcoin at that time, his writing style suggests an attempt to take some credit for Bitcoin’s success by applying lessons learned from Hashcash.
Hal Finney
Hal Finney is often associated with the figure of Satoshi Nakamoto. He was a programmer and prominent cryptographer who also became one of the first people to receive and work with Bitcoin software when it was first released in 2009. On January 12, 2009, he received their first bitcoin transaction with a value of 10 BTC from Satoshi Nakamoto himself.
Finney was one of the first people to respond to Satoshi’s post on the cypherpunks mailing list and one of the first to download and run bitcoin software. There is also speculation that he might also have been the second miner on the network.
Hal Finney lived in the same town and was a close neighbor of Dorian Nakamoto, which further added to the speculation that he may have been Bitcoin’s creator. Some have even theorized that Finney may have been a ghostwriter on behalf of Nakamoto, or that he simply used his neighbor Dorian’s identity as a “drop” or “patsy whose personal information is used to hide online exploits”.
Most reports use a 1993 forum post as evidence that Hal Finney was aware of how a technology based on cryptocurrency could be built. This concept is explained using trading cards as an analogy, similar to the modern principle of NFTs.
In March 2013, Finney posted on a Bitcoin forum, BitcoinTalk, a publication called “Bitcoin and me (Hal Finney)”, where he states that he was essentially paralyzed and mentions that amyotrophic lateral sclerosis (ALS) disease was causing his ability to code to be slower but that he would continue coding and working on an experimental software called bcflick, which was used to strengthen the security of Bitcoin wallets.
Finney was a well-known and frequently cited cryptographer. Hal Finney was even hired by Phil Zimmerman to work on PGP, where he coded up the benchmark PGP 2.0 implementation. He had won notable challenges to break Netscape’s SSL encryption as well. This goes against the commonly accepted fact that Satoshi was an amateur cryptographer
Satoshi had a peculiar coding style in C++, which is an object-oriented programming language built as an extension of the C programming language. C uses similar rules, but is ultimately a more rigid language used for system applications and low-level programming applications. However, Hal Finney was a C programmer with limited experience in C++, and his contributions to Bitcoin were mostly weighted towards security and auditing what Satoshi had already written.
Hal Finney played an important role as an auditor of the code.
Contrary to Satoshi, Hal Finney did not seem too favorable to the idea of competitive mining and excessive emissions either.
In that regard, Satoshi’s response alluded to the libertarian ideology of the code behind Bitcoin.
This is also reinforced by Satoshi’s advocacy for Bitcoin to move into server farms with specialized hardware. In that regard, Satoshi envisioned the need for the industrialization of nodes and hashing power.
Finney also seemed to be in contradiction with such an industrialization process due to the environmental impact of large scale mining operations.
During the last year of his life, Hal Finney’s family received anonymous calls demanding an extortion fee of 1,000 bitcoin. They became victims of swatting.
Swatting is a hoax where the perpetrator calls up emergency dispatch using a spoofed telephone number and pretends to have committed a crime in the hopes of provoking an armed police response to the victim’s home.
Hal Finney died in 2014 at the age of 58 due to amyotrophic lateral sclerosis.
Nick Szabo
In December 2013, blogger Sky Grey linked Nick Szabo to the Bitcoin whitepaper using an approach that he described as stylometric analysis. Szabo was the original creator of bit gold, one of the precursors of Bitcoin. He is also known to have been interested in the use of pseudonyms in the 1990s.
Szabo has a peculiar style of commenting code that was brought up on Reddit multiple times to point out similarities with Satoshi’s style.
Szabo was a computer scientist that also showed proficiency in C++ coding. Bit Gold shared some similarities with Bitcoin as well, since it used P2P networking to enable a financial network for transactions
Stylometry is the application of the study of linguistic style, usually applied to written language and used to attribute authorship to anonymous or disputed writers.
I a May 2011 article, Szabo stated about the Bitcoin creator: “Myself, Wei Dai, and Hal Finney were the only people I know of who liked the idea (or in Dai’s case his related idea) enough to pursue it to any significant extent until Nakamoto (assuming Nakamoto is not really Finney or Dai).”
Craig Wright
Craig Wright is an Australian computer scientist who, in 2016, auto-proclaimed himself as Satoshi Nakamoto. However, up until today, he has not proved to be the owner of the private keys that would link his identity to any of Satoshi’s wallets.
Wright has publicly stated that he chose the family name “Nakamoto” in honor of the Japanese philosopher Tominaga Nakamoto (1715-1746), whom Wright learned about from his Japanese martial arts instructor, and the accompanying given name “Satoshi” after the Pokémon character Satoshi, because his name was anglicized as “Ash”, and thus “Satoshi” represents the current financial system that must be burned into ash in order to make way for cryptocurrency.
More specifically, on December 8, 2015, Wired published an article noting that Craig Wright “either invented bitcoin or is a brilliant hoaxer who very badly wants us to believe he did”. At that time, Craig took down his Twitter account and neither he nor his ex-wife responded to press inquiries. That same day, Gizmodo published a story with evidence supposedly obtained by a hacker who broke into Wright’s email accounts, claiming that Satoshi Nakamoto was a joint pseudonym for Craig Steven Wright and computer forensics analyst David Kleiman, who died in 2013. This claim was supported by Jon Matonis (former director of the Bitcoin Foundation), and bitcoin developer Gavin Andresen.
A number of prominent Bitcoin community members still remained unconvinced by the reports and raised the possibility that the evidence provided was an elaborate hoax. In May 2019, Wright started using English libel law to sue people who denied he was the inventor of Bitcoin and who called him a fraud. In that same year, he also registered US copyright for the bitcoin white paper and the code for Bitcoin 0.1, although the United States Copyright Office issued a press release clarifying that Craig was not officially recognized as Satoshi Nakamoto, as they primarily work to determine whether a work is eligible for copyright and do not investigate legal ownership, which, if disputed, is determined by US courts.
Paul Le Roux
Paul Solotshi Calder Le Roux was born in South Africa and worked as a software developer before moving to the United States in 2007, where he founded a digital pharmaceutical company which was used to manufacture and distribute prescription drugs to customers all over the world. He also created several offshore companies which he used to launder money from his criminal activities and is the creator of the encryption software E4M and he is also speculated to be one of the creators of TrueCrypt.
There is not full evidence to prove that Le Roux was one of the men behind TrueCrypt. However, E4M was a predecessor to it. In fact, TrueCrypt was developed by a team of anonymous engineers who chose to give their work away for free. To this day, no one has identified anyone as the original creators.
Evan Ratliff wrote a book about Paul Le Roux called The Mastermind.
In early 2011, Satoshi vanished from the public eye to focus on other endeavors. At roughly the same time, Le Roux moved away from his software development career and became a leader of a criminal cartel. During this period, he faced setbacks with his unlawful global pharmaceutical enterprise, RX Limited, when the US government and the DEA imposed restrictions on its distribution.
The fact that Le Roux had to go into hiding at the same time as Satoshi’s disappearance suggests another striking similarity between the two.
The first evidence linking Paul Le Roux to Satoshi Nakamoto comes from his own words. In an email sent to a friend in 2008, just one month before the Bitcoin whitepaper was published, Le Roux wrote, “I’ve been working on a new form of electronic money. It’s a bit like BitCoin, but much more advanced.” The first counterargument is that Le Roux was only referring to a concept, and not necessarily to the idea of Bitcoin that we know today. Also, despite his background as computer scientist and cryptographer, it is worth noting that Le Roux is not a native English speaker, which raises some doubts as to whether or not he was the author of the original whitepaper.
Other speculative theories refer to fact patterns associated with dates. For example, in March 2012, the DEA (Drug Enforcement Association) raided one of Le Roux’s businesses in Oskosh Wisconsin . One month later, in April 2012, Satoshi sent his last email.
In September 2012, Le Roux was arrested in Liberia and, since then not a single sat belonging to Satoshi has moved.
In much recent time, during the Kleiman v Craight Wright trial and its filing, a motion for a protective order and the filing had a significant number of redactions. However, there was one unredacted footnote in Wright’s filing called “Document 187,” which was the URL to Paul Le Roux’s Wikipedia page, which led to the suspicion that Le Roux was possibly Bitcoin’s creator and somehow Wright obtained access to the criminal’s hard drives.
However, there are some counter-arguments against Le Roux being Satoshi, which are that the email he sent to his friend was sent a month before the release of the first Bitcoin whitepaper, indicating that he may have been referring to a different concept rather than the Bitcoin we know today.
Secondly, Le Roux is currently serving a long prison sentence, and if he were indeed the creator of Bitcoin, he would have had reasons to conceal his identity to avoid arrest.
Lastly, the Bitcoin whitepaper was written in English, which is not Le Roux’s native language. This raises questions about his ability to produce such a sophisticated document.
Other candidates
Michael Clear, Dr. Vili Lehdonvirta
In a 2011 article in The New Yorker, Joshua Davis claimed to have narrowed down the identity of Nakamoto to a number of possible individuals, being Michael Clear and subsequently Dr. Vili Lehdonvirta.
Clear was a young graduate student in cryptography at Trinity College in Dublin. He was also recognized as the best undergraduate in computer science at Trinity in 2008. He was then employed by Allied Irish Banks in 2009 to enhance its currency-trading software, and he co-wrote an academic paper on peer-to-peer technology. The paper used British spelling, and it was evident that Clear had a good grasp of economics, cryptography, and peer-to-peer networks.
Clear had been programming computers since he was ten and he could code in a variety of languages, including C++, the language of bitcoin.
While Clear had denied that he was Satoshi, he had identified Dr. Vili Lehdonvirta as a possible suspect.
Lehdonvirta was a Finnish researcher at the Helsinki Institute for Information Technology, had previously worked as a video game programmer and was currently researching virtual currencies. Clear believed that Lehdonvirta would be a good match for Nakamoto.
However, he had no background in cryptography and limited C++ programming skills.
Neal King, Vladimir Oskman, Charles Bry
In an 2011 article, by Fast Company, written by Adam L. Penenberg, he had discovered a patent application titled “Updating And Distributing Encryption Keys Invention”, for a “system and method for providing secure communications”, filed on August 15 2008, which was 3 days before the domain bitcoin.org was registered. The patent was filed by Neal King, Vladimir Oksman and Charles Bry, with numerous patent applications over the years.
All 3 are also listed on multiple patent applications related to encryption, nodes and networks.
Another coincidence was that the Bitcoin.org domain was registered by a Finnish provider based in Helsinki, which Bry had traveled to six months prior.
However, all 3 have denied being Satoshi, with King offering the most detailed response, in that the technical topics between his patent application and Bitcoin, “are very different, excepting that both relate to authentication to some extent.” He claims he “had never heard of Bitcoin until this question came up,” and had to look up Bitcoin on Wikipedia, concluding that, “It’s not a very good idea: Nakamoto’s algorithm is a solution in search of a problem.”
Shinichi Mochizuki
On May 18 2013, Ted Nelson, an American pioneer of information technology, philosopher, and sociologist, posted a Youtube Video containing his speculation on the identity of Satoshi.
He speculated that Mochizuki, a research professor of Mathematics at Kyoto University, was Satoshi.
Mochizkui had published a proof of an important conjecture of Mathematics, the ABC conjecture in August 2012. This included a vast new system of mathematical structures that nobody had heard of, including inter-universal Tyco Miller theory and Roubini IDEs, which has been described as a “beguilingly simple number theory problem that had stumped mathematicians for decades”.
He also had a number of impressive accomplishments and accolades such as proving Grothendieck’s conjecture on anabelian geometry in 1996, and being invited to speak at the International Congress of Mathematicians.
Mochizuki was also the class salutatorian at Princeton (ranked before the Valedictorian), which meant that he had to have a good grasp of the English language too.
However, counter-arguments against Mochizuki being Satoshi is the fact that he has a glaring lack of known background in computers, coding, and cypherpunk ethos and knowledge.
Gavin Andresen, Jed McCaleb
In a 2013 article, by Vice, written by Alec Liu, it was speculated that either Gavin Andresen or Jed McCaleb could be Satoshi.
Andresen, who is the lead developer of the Bitcoin project, also holds the position of chief scientist on the board of the Bitcoin Foundation, and is considered by many to be the equivalent of Linux’s Linus Torvalds.
However, Andresen has denied being Satoshi, saying he has a different coding style than Satoshi does.
Jed McCaleb is a UC Berkeley dropout and co-founded Mt. Gox. McCaleb also founded eDonkey in 2000, one of the largest (and technically revered) peer-to-peer file-sharing networks at the time. He would go on to develop Ripple, what he believes to be an improved iteration of the Bitcoin concept that addresses some of these flaws.
The Genesis Files
How Hal Finney’s Quest for digital cash led to RPOW
Upon the internet’s public release in the early 1990s, Hal Finney was aware that cyberspace presented not only exciting new possibilities but also potential risks. With the shift towards digital communication, there was a risk of anyone’s conversations being monitored. This was a threat to people’s privacy and human freedom. This was particularly true for financial transactions, as money was also becoming digitized. Consequently, anonymous payments could eventually become obsolete in a world that was rapidly digitizing.
In a 1993 essay, Finney had explained, “Dossiers could be built up which would track the spending patterns of each of us. Already, when I order something over the phone or electronically using my Visa card, a record is kept of exactly how much I spent and where I spent it. As time goes on, more transactions may be done in this way, and the net result could be a great loss of privacy.”
Similar to physical currency such as banknotes and coins that one carries in their pocket, Finney believed that the internet required an untraceable form of money that could facilitate anonymous transactions.
Indeed, having foreseen many of the same problems as Finney, cryptographer David Chaum had come up with a design for digital cash, called eCash. Finney soon found himself promoting Chaum’s project to his fellow Extropians (a group of cypherpunks), at one point authoring a seven-page explainer for Extropy, the magazine at the heart of the movement.
During the same period in 1992, Finney was invited by Timothy May to join a group of tech-savvy and privacy-focused individuals in the Bay Area. The group, which included Eric Hughes, a former employee of DigiCash, was made up of hackers, computer scientists, and cryptographers who sought to enhance online privacy by harnessing the power of cryptography. They named themselves the Cypherpunks and focused on creating and distributing software as their main tool. Their motto became “Cypherpunks write code.”
Finney was a skilled programmer who was instrumental in the Cypherpunks’ early successes. He helped develop the first remailer and was a significant contributor to PGP. He also organized a contest to break Netscape’s SSL encryption. However, Finney’s main interest was always digital cash, and he reviewed electronic cash proposals on the Cypherpunk mailing list. He focused on privacy features and was always available to offer his insights on digital cash.
Adam Back proposed Hashcash in 1997, which introduced the “proof-of-work” system as a solution to counter spam. This system presented the potential for a new type of unbacked digital cash. Nick Szabo and Wei Dai also developed digital cash proposals based on proof of work, but they were never implemented due to some weaknesses. In the meantime, DigiCash, a company focused on digital cash, filed for bankruptcy. By the early 2000s, the Cypherpunk movement dissolved, and the dream of digital cash seemed to fade away.
In 2004, Finney proposed a digital currency system called Reusable Proofs of Work (RPOW) that used Hashcash’s proof-of-work system for currency generation. Unlike Szabo and Dai, who didn’t implement their digital cash proposals into software, Finney coded an RPOW prototype and advertised it on a website featuring an RPOW logo in comic book style.
Finney created a prototype for his digital currency system RPOW, which used a proof-of-work system for currency generation. However, for the system to work without trust, Finney hosted the RPOW server on a secure hardware component, the IBM 4758, which allowed for “trusted computing.” This prevented Finney from cheating by adjusting the RPOW software and ensured users did not have to trust the server operator.
And thus, RPOW was born.
How David Chaum’s ECash spawned a Cypherpunk dream
David Chaum, a computer science professor at Berkeley University, designed tools to realize digital privacy, including privacy-preserving technologies like Tor, which he first published in 1981, Chaum’s paper “Untraceable Electronic Mail, Return Addresses, and Digital Pseudonyms”. In addition, he wanted to design a privacy-preserving digital currency.
In 1982, Chaum had already designed a solution for an anonymous payment system for the internet, which he published in his paper “Blind signatures for untraceable payments.” At the heart of Chaum’s digital money system lies his innovation of “blind signatures.” Public key cryptography uses key pairs consisting of a public key and a private key. Alice can sign data by combining it with her private key, generating a signature that can be checked against her public key by Bob or anyone else. A blind signature adds another step by having Bob scramble the data with a random number, creating a seemingly random string of numbers that Alice can sign without knowing the original data. The resulting blind signature can be checked against Alice’s public key and the scrambled data, as well as the original, unscrambled data.
Chaum used blind signatures to create a digital money system, eCash. In this system, Alice Bank is a regular bank, and Bob wants to buy something from Carol. Bob creates digital banknotes by himself and sends them to Alice Bank. Alice Bank then blind signs each scrambled banknote, and sends them back to Bob. Bob can now use the original unscrambled banknotes to pay Carol by simply sending them to her. As Carol receives the banknotes, she should forward them to Alice Bank. Alice Bank checks that she indeed blind signed each of the banknotes and that the same banknotes haven’t already been deposited by someone else to ensure they haven’t been double-spent. This solution provides privacy in payments, and it was new in digital form.
In 1990, David Chaum founded DigiCash in Amsterdam, specializing in digital money and payment systems, including the flagship project eCash. DigiCash’s eCash system allowed for private digital payments and was the company’s most significant project.
In the mid-1990s, eCash, the digital cash system developed by DigiCash, gained interest from major banks and corporations, including Deutsche Bank, Credit Suisse, Visa, and Microsoft. However, despite the attention, DigiCash struggled to secure lucrative deals, and by 1996, it had new leadership and moved its headquarters from Amsterdam to Silicon Valley. Despite these changes, eCash failed to catch on with the public, and the project did not receive a significant push from the banks that were experimenting with the technology. Ultimately, DigiCash failed to achieve its full potential.
Despite the failure of DigiCash and eCash, David Chaum’s work inspired a group of cypherpunks, including DigiCash contributors like Nick Szabo and Zooko Wilcox-O’Hearn. This group proposed alternative digital currency systems throughout the 1990s and early 2000s, with the dream of electronic cash still alive. In 2008, Satoshi Nakamoto proposed Bitcoin to be the de-facto successor of the cypherpunk mailing list, about 10 years after DigiCash’s demise.
How Adam Back’s HashCash inspired Bitcoin’s motor block
In 1997, Adam Back, a British cryptographer and contributor to the Cypherpunks mailing list, proposed a “partial hash collision based postage scheme” for emails, which he called Hashcash. This proposal did not receive much attention initially, but it introduced the concept of proof of work, which would later become the foundation for cryptocurrencies such as Bitcoin.
It started in the early 1990s, with the rise of email leading to the problem of spam. To solve this problem, Dr. Cynthia Dwork and Dr. Moni Naor proposed a system in their 1992 white paper “Pricing via Processing or Combatting Junk Mail.” This solution was called “proof of work” and required users to show that their computer performed work, proving that they spent real-world resources. However, this proposal never gained much traction outside of a small circle of computer scientists.
Then, the Cypherpunks, a group of privacy activists with a libertarian bent, started to organize through a mailing list around the same time that Dwork and Naor published their white paper. They utilized the science of cryptography to work toward their goals of privacy-enhancing technologies. Back, who was a frequent contributor to the Cypherpunks mailing list and was involved in various discussions related to privacy, cryptography, and libertarianism, started to establish himself as one of the more active participants. He was particularly interested in developing electronic cash systems that could provide greater privacy and anonymity for users.
However, Back was not aware of Dwork and Naor’s proof-of-work proposal, but he had similar ideas to counter spam and discussed them on the Cypherpunks mailing list. Back suggested that using PGP encryption would add some overhead to the spammer, making it difficult for them to encrypt many messages per second. Back’s contributions to the mailing list and his work on electronic cash systems would eventually lead to the development of Hashcash and the proof of work system, which would become the basis for the mining process used in cryptocurrencies like Bitcoin.
By 1997, when the Cypherpunks mailing list had grown to thousands of subscribers, Back submitted his Hashcash proposal.
Hashcash was a proof-of-work system proposed to counter spam and abuse of anonymous remailers. It used hashing, a cryptographic technique that takes data and turns it into a seemingly random number, to formalize the metadata of an email as a protocol, which includes adding a random number called a nonce. The metadata, along with the nonce, is then hashed, and the binary version of the hash must start with a predetermined number of zeroes for it to be considered “valid.” The sender must keep trying different nonces until they find a valid combination, which requires computational resources, making it a proof-of-work system. Hashcash is more random than Dwork and Naor’s proposal, as it allows for slower computers to find a correct solution faster some of the time, unlike the puzzle-based solution proposed by Dwork and Naor.
However, it was not widely adopted despite being implemented in Apache’s open-source SpamAssassin platform and Microsoft’s “email postmark” format. Despite that, Hashcash introduced a new concept of virtual scarcity without relying on a central party, which is a prerequisite for money. Despite not functioning as a full-fledged cash, Hashcash served as a basis for research in the digital-money realm, leading to several notable digital-money proposals that followed.
Ultimately, of course, proof of work became a cornerstone for Bitcoin, with Hashcash as one of the few citations in the Bitcoin white paper.
How Wei Dai’s B-Money was like a first draft for Bitcoin
Wei Dai always had an interest in philosophy and politics. He was inspired by the writings of Timothy May, a “founding father” of the Cypherpunk movement, while studying computer science in the 1990s. He was particularly drawn to the crypto-anarchy ideology espoused by May, which held that cryptography and software could better provide and safeguard political and economic freedom than any system of government.
In the mid-1990s, he actively participated in the Cypherpunks mailing list, engaging in discussions about various topics such as digital reputation systems, privacy, and anonymity. He made a number of proposals, including trusted timestamping and a secure file-sharing system, which established him as a prolific contributor to the Cypherpunk community, despite his anonymity.
In November 1998, after graduating from university, Dai announced an idea that would make him famous: “efficient cooperation requires a medium of exchange (money) and a way to enforce contracts.” He proposed a protocol that would allow untraceable pseudonymous entities to cooperate with each other more efficiently by providing them with a medium of exchange and a method of enforcing contracts. He named his proposal “B-Money” and hoped it would make crypto-anarchy a practical possibility.
Dai proposed two alternative solutions to traditional digital money systems which use a central ledger. In the first solution, all participants maintain separate copies of the same ledger consisting of public keys with amounts attached to them, preventing any single entity from blocking transactions while offering a level of privacy to users. This decentralized approach is intended to avoid government regulation and control.
However, he realized that his first b-money solution was impractical as it did not solve the double-spending problem. The issue was that it made heavy use of an anonymous broadcast channel that was synchronous and unjammable. Thus, Dai came up with a second b-money solution that consisted of two types of users: regular users and servers. Only servers, linked through a Usenet-style broadcast network, would maintain the b-money ledgers. This consisted of a system where servers maintained the ledgers, while regular users transacted. This proposal resembles what would be called a proof-of-stake system today.
Dai also added an early version of a smart contract solution, which involved depositing funds in a special account without a dispute resolution system encoded. Instead, in case of disputes, different users or servers could adjust their ledgers differently, leaving the state of ledgers on the network out of consensus.
Eventually, did not expect b-money to take off in a big way and was disillusioned with crypto-anarchy by the time he finished writing up the proposal. Nonetheless, b-money was an important precursor to the development of blockchain and cryptocurrencies and eventually ended up as the first reference in the Bitcoin white paper.
How Nick Szabo’s Bit Gold was inches away from inventing Bitcoin
Nick Szabo was born in 1965 in the United States to Hungarian parents who had fled the Soviet regime after World War II. He grew up in the state of Washington and later moved to California. In the 1990s, Szabo became involved in the Cypherpunk movement, attending in-person meetings in the Bay Area organized by its founding members, including Timothy May and Eric Hughes. Szabo’s interests in cryptography and digital currency would lead him to create his own digital currency, which he called “bit gold.”
Like the other Cypherpunks, Szabo was concerned with the receding guarantees of privacy in an upcoming digital age and took action to stem the tide where he could, but also went beyond that. He was also interested in developing digital forms of money that could operate without the need for central authorities. He was a vocal opponent of the Clipper chip, which was proposed in the 1990s as a way for law enforcement to have access to encrypted communications. Szabo argued that the chip would undermine privacy and security, and he worked to raise awareness of the issue among the general public. Ultimately, the Clipper chip was not widely adopted due in part to the efforts of Szabo and others in the Cypherpunk community.
Szabo realized that in order for smart contracts to be effective, they needed a native cryptocurrency that could be used to incentivize participants to follow through with their obligations. This would create a system of self-enforcing contracts that could operate independently of any government or central authority. He called this hypothetical currency “bit gold.” The idea was that each bit of this currency would be created through a process of solving complex mathematical problems, similar to how gold is mined from the earth. But smart contracts were only part of the puzzle. The second tool Szabo needed in order to realize his “Galt’s Gulch” was possibly even more important: money.
Szabo believed that money was a crucial component for the creation of a stateless, non-violent society. He saw money as a means to enable trade and cooperation without relying on any centralized authority or intermediary. In his essay “Shelling Out: The Origins of Money,” Szabo explained how the use of money has been embedded in human nature, and he identified the qualities that make certain objects better suited to serve as money than others. He also showed interest in free banking, a monetary system in which private banks issue their own currency, not tied to any particular state, and let the free market decide which currency to use.
Indeed, the risks associated with centralized systems would become a recurring theme in Szabo’s work. As he continued to develop his ideas around smart contracts and decentralized systems, he became increasingly convinced that centralized authorities represented a point of vulnerability that could be exploited by both external and internal actors. In contrast, he believed that decentralized systems, where trust was distributed across the network rather than concentrated in the hands of a few individuals or organizations, represented a more secure and robust way of organizing human affairs.
Szabo wanted to create a new form of money that did not depend on trust in any third party, and he sought to create a digital gold that was both digital and scarce, with its value accurately approximated by simple observations or measurements.
Eventually, Szabo created Bit Gold in 1998, but he described it publicly in 2005. Bit Gold was a proposed digital money scheme that consisted of a combination of solutions, some of which resembled previous electronic cash concepts. The central property of Bit Gold was proof of work, which required computing power to produce unforgeable proofs of work. This represented the unforgeable costliness that he was looking for in a digital currency.
In the 2000s, Szabo earned a law degree to better understand the legal and contractual implications of his ideas for the online world. He also began publishing his ideas on his blog, “Unenumerated,” which covers a wide range of topics. In 2008, Szabo returned to the idea of Bit Gold and began working on a first implementation of the concept.
However, the idea of bit gold was never fully realized, but it laid the foundation for the development of Bitcoin, which was created over a decade later.
Characteristic features of Satoshi
- Satoshi’s last email was sent in April 2011, and the last forum post in March 2014. When discussing technical matters, Satoshi never revealed any personal information, although there are certain times when he provided commentary on banking issues, especially related to the fractional reserve banking system.
- His email address was satoshin@gmx.com. This is the address he used to tell the world’s media that they had mistaken him with Dorian Nakamoto.
- The timestamps of Satoshi’s first posts have been used to infer that he was most likely located in the United Kingdom, the East Coast of the United States, or the West Coast of the United States. Stefan Thomas, a Swiss software engineer and active community member, graphed the timestamps for each of Nakamoto’s bitcoin forum posts (more than 500); the chart showed a steep decline to almost no posts between the hours of 5 a.m. and 11 a.m. Greenwich Mean Time. This was between 2 p.m. and 8 p.m. Japan Standard Time, suggesting an unusual sleep pattern for someone supposedly living in Japan. As this pattern held true even on Saturdays and Sundays, it suggested that Nakamoto consistently was asleep at this time.
- Nakamoto was known to spell things like “favour” (with a “U”) rather than the American “favor” (without the “U”). This has led some to believe that Nakamoto either hails from or attended school in the United Kingdom.
- The use of British English is also present in Bicoin’s open source code as well as in forum posts. Examples are the expression “bloody hard”, terms such as “flat” and “maths”, and the spellings “grey” and “colour”.
- Satoshi’s reference to the Times British newspaper in the Genesis Block also reinforces the thesis that he might have a British origin.
- None of the bitcoins that have been associated and linked to Satoshi’s wallets have ever moved. In fact, none of these Bitcoins have ever been taken out of any of their wallets or transferred to anybody else.
- Satoshi is heavily presumed to not have been a professional coder or cryptographer. As an example, Satoshi used an elliptic curve secp256k1 which is a very particularly uncommon curve. Most professional cryptographers would have chosen a curve that confirmed to NIST standards. When asked about it, Satoshi replied that he had asked a lot of people and that he was told this was a good choice.
- Satoshi was a Windows user. He even asked Laszlo Hanyecz to code up Bitcoin on MacOS because he didn’t even have a Mac to work on.
Bitcoin core developers
The Bitcoin Core development team controls code changes into Bitcoin Core’s GitHub repository. However, the development process is open-source, and anyone can participate by proposing changes or commenting on proposed changes. Changes are reviewed by the core developers, and if they are deemed appropriate, they are merged into the codebase. The process is transparent and open to the public, with discussions and decisions taking place on various communication channels, such as mailing lists, GitHub, and IRC. Ultimately, the community of Bitcoin users and miners decides whether to adopt any changes to the codebase through a process of social consensus.
In terms of corporate structure, there is no no particular concept of “Bitcoin core developers” in the sense of privileged people. Open source prompts a meritocracy where developers earn trust from the community over time. The hierarchical roles are only in place for practical purposes, in order to ensure a proper release cycle and code review process.
Bitcoin core contributors: https://github.com/bitcoin/bitcoin/graphs/contributors
Contributing to Bitcoin Core
Bitcon core is an open-source project and anyone is welcome to contribute towards its development, whether it is in the form of peer reviews, testing, or patches.
Whether a pull request is merged into Bitcoin Core is a decision that will be made by the maintainers of the project. They will take into consideration if a patch is in line with the general principles of the project, if it meets the minimum standards for inclusion, and will judge the general consensus of contributors.
As a rule of thumb, all pull requests must:
- Have a clear purpose and demonstrable use case.
- Be peer-reviewed.
- Have unit tests, functional tests, and fuzz tests.
- Follow code style guidelines (C++, functional tests).
- Not break the existing test suite.
- Change the relevant code comments and documentation when the behavior of the code changes.
Patches and upgrades that can change Bitcoin consensus rules are considerably more involved, since they affect the entire ecosystem and must be preceded by extensive mailing list discussions as well as a numbered BIP (Bitcoin Improvement Proposals).
Anyone may participate in the peer review process by engaging in discussions and comments on ongoing pull requests. Typically, reviewers will review the code for errors, suggest improvements, as well as test out the change set and provide feedback on the technical merits of the patch.
In general, if a code review does not warrant the review effort that is required, the pull request is likely to be rejected. In that case, it is up to the author to convince reviewers about why those changes are relevant and should be added to the codebase.
The first review is known as a conceptual review, where the reviewer leaves one of the following comments:
- Concept (N)ACK, which means “I do (not) agree with the general goal of this pull request”.
- Approach (N)ACK, which means “I do (not) agree with the approach of this change”.
All NACKs must include a rationale explaining why the change is not worthwhile.
After the conceptual review, an actual code review takes place, which is followed by a description explaining how the reviewer has proceeded to do the review. Project maintainers also reserve the right to weigh the opinions of peer reviewers. These maintainers are developers and reputable members in the Bitcoin community who have demonstrated clear domain expertise and experience.
As most reviewers are themselves developers working on their own projects, the review process can be quite lengthy and might even take several months. There might be a number of reasons for it:
- It might be due to a feature freeze due to upcoming releases. In these periods, only bug fixes are taken into consideration. Therefore, all pull requests suggesting new features will not be prioritized until after the release.
- It might be because the changes being suggested are not appealing to the general public (changes too much code, breaks code conventions, does not adhere to the developer notes, could be dangerous or insecure…
- It might be due to the complexity of code changes. When that happens, it is recommended to use the “git blame” command in order to notify the developers who previously worked on that piece of code to review the changes.
Coding conventions: https://github.com/bitcoin/bitcoin/blob/master/doc/developer-notes.md
Bitcoin core PR Review Club weekly meeting:
https://bitcoincore.reviews/
Repository for GUI-related issues: https://github.com/bitcoin-core/gui
“Being open source means anyone can independently review the code. If it was closed source, nobody could verify the security. I think it is essential for a program of this nature to be open source” – Satoshi Nakamoto
Bitcoin’s MIT license
Bitcoin Core development team
Additional Information
How Satoshi messed up his math
In section 11 of the Bitcoin whitepaper, Satoshi Nakamoto explained that an honest mining majority will always outrun a dishonest minority. According to this statement, this would ensure that transactions are practically irreversible once they have sufficient confirmations. This would solve the classic double-spend problem.
However, as first explained by the Israeli mathematician Meni Rosenfeld back in 2012, Satoshi made some simplified assumptions. For example, while Bitcoin mining is a random process, Satoshis did not fully consider that honest miners can be just as lucky as dishonest miners. Cyril Grunspan, mathematician at École Supérieure d’Ingénieurs Léonard de Vinci, and Ricardo Pérez-Marco, mathematician at the French National Center for Scientific Research, iterated over the original research by Meni Rosenfeld and published a new paper that corrected Satoshi’s mistake.
Satoshi had made a wrong assumption: that honest miners use exactly as much time to find a block as they would on average. This is only a rough approximation of reality, since the time used by honest miners to mine a block is not deterministic and, therefore, the distribution of the number of blocks that could be mined by an attacker would follow a negative binomial distribution instead of the assumed Poisson law.
In other words, the Bitcoin whitepaper assumes that two factors are needed to estimate how irreversible a transaction is. Satoshi rightly assumed that the share of total hash power available to the attacker is one factor. This explains that, as an attacker controls more hash powers, more confirmations are needed. He also rightly assumed that the number of confirmations is another factor: the more confirmations a transaction has, the more secure it is. However, Grunspan and Perez-Marco came up with a third factor: the deviation from the average mining time, which can be described as how lucky honest miners are in finding blocks. If they are very lucky, and find blocks faster than the average, their chain will probably be further ahead; the attacker will have had less time to secretly mine an alternative chain. On the other hand, if the honest miners are unlucky and find blocks slower than the average, they will probably be less far ahead and the attacker will have had more time to mine an alternative chain.
The figure above shows the probability of a successful double spend, as a function of the attacker’s hahrate for different values of the number of confirmations (in logarithmic scale).
Despite this breakthrough, the basic premise of the whitepaper still holds up. Bitcoin works as intended. This piece of research showed that the probability of double spends drops exponentially to zero as the honest mining majority finds more blocks. In other words, it becomes increasingly difficult for minority attackers to catch up and overtake the honest majority.
The outcome is that the security assumptions stated in the original whitepaper needed to be tweaked a bit. Rather than just accounting for the amount of hash power an attacker has and the number of blocks the attacker is behind, the deviation from the average mining time needs to be accounted for as well. This information could be relevant for monitoring risk.
As an example, if a merchant always waits for six confirmations before sending his goods to a customer, that means that, on average, they are comfortable with a level risk that is 60 minutes on average. But sometimes he’ll have to wait for two hours before six blocks are found. If that happens, the double-spend risk is also higher. So for the same level of security, he’ll actually have to wait for a seventh confirmation. While if the confirmations come in much faster, he should be fine even with five confirmations.
“Satoshi was a genius, but he was not a mathematician” – Grunspan
How Bitcoin Revived the Cypherpunk Revolution
The definition of a cypherpunk tends to vary based on whom you ask, but the generally accepted definition of a cypherpunk is anyone who uses strong cryptography in an effort to enact social or political change. The cypherpunks first came to prominence via the cypherpunks mailing list in the ‘90s. Their philosophy is best described by The Crypto Anarchist Manifesto, by Timothy C. May.
Bitcoin is a cypherpunk’s dream. It represented a working form of digital cash that many cypherpunks had failed to create in the past. Bitcoin changed the view of what is technically possible in the world today, and it did so at a time when the philosophies of the cypherpunks were starting to die off.
The Genesis Block
In Bitcoin’s first block, Satoshi included the headline “The Times 03/Jan/2009 Chancellor on brink of second bailout for banks”, possibly as a timestamp for the launch of the network, but also as a commentary on Bitcoin’s role in the economy.
Bitcoin Pizza Day
The Bitcoin Pizza Day is a celebratory day on May 22nd, which marks the first real-world transaction involving bitcoin. On May 22nd, 2010, a man named Laszlo Hanyecz paid 10,000 bitcoins for two pizzas from Papa John’s (~$41). This transaction is now recognized as the first real-world purchase using Bitcoin as a currency, and has since become a celebrated event within the cryptocurrency community.
This happened when Bitcoin was only a year old and trading for less than a penny. However, up until that day, no one had ever spent bitcoin on anything. At the time, Satoshi was still active on Bitcointalk, where he communicated and shared notes with other enthusiasts.
Although Laszlo’s popularity is largely attributed to this anecdote, he is an active developer with large contributions to the field of GPU mining. His contributions include building and deploying the first macOS Bitcoin Core release.
“A trade happens because both parties think they’re getting a good deal. I felt like I was beating the internet, getting free food. I was like, ‘Man, I got these GPUs linked together, now I’m going to mine twice as fast. I’m just going to be eating free food; I’ll never have to buy food again.”
The first halving
The first halving in Bitcoin’s history occurred on November 28, 2012, when the block reward was reduced from 50 BTC to 25 BTC. The event was significant because it marked the first time the reward for mining a block was cut in half, which had an impact on the supply and inflation rate of Bitcoin. However, this was a relatively small event in the grand scheme of Bitcoin’s history.
The 2013 Bitcoin fork
In March 2013, a software bug caused a fork in the blockchain, resulting in two separate versions of the Bitcoin software running at the same time. The bug was the result of a coding oversight for the upgrade of the Bitcoin software from version 0.7 to 0.8. For 6 hours, two versions of the Bitcoin ledger existed simultaneously. This led to temporary confusion and a drop in the Bitcoin price of about 24%. 25 transactions were created in an erroneous chain that was later abandoned when developers decided to switch back to version 0.7. Bitcoin developers contacted major exchanges and mining pools and made the switch back to the old version. The bug was quickly fixed and the blockchain was reverted to a single version with the help of the majority of the Bitcoin community.
Even if developers had not intervened, the 2013 fork would have probably resolved on its own, when more and more miners moved to version 0.8.
The Mt Gox theft
MtGox was a Bitcoin exchange based in Tokyo, Japan, that was launched in 2010. It quickly became one of the largest Bitcoin exchanges, handling over 70% of all Bitcoin transactions in 2013. However, in 2014, MtGox filed for bankruptcy after approximately 850,000 Bitcoins (worth around $450 million at the time) were stolen or lost from the exchange.
The founding story took place between 2006 and 2010. In late 2006, Jed McCaleb aspired to build a website for users of the Magic The Gathering Online tradable card game, to let them trade “Magic: The Gathering Online” cards like stocks. One year later, in 2007, he purchased the domain name mtgox.com, short for “Magic: The Gathering Online Exchange”. The service went live for approximately until Jed moved on to work on other projects, having decided that pursuing this business was not worth his time. However, in 2010, McCaleb found out about Bitcoin on Slashdot and decided that the Bitcoin community needed an exchange for trading Bitcoin and regular currencies.
McCaleb started running the exchange until he sold the exchange to Mark Karpeles in March 2011. At the time, Mt. Gox was plagued with security issues that would become its downfall. The 2011 hack came just a few months after Mark Karpelès purchased the exchange. The hacker, upon access, artificially altered the nominal value of Bitcoin all the way down to one cent and then transferred 2,000 BTC from Mt. Gox customer accounts onto the exchange. These Bitcoins were sold, and in the brief moment that Bitcoin appeared to be worth a single penny, 650 were purchased.
The 2011 hack was a brief but severe setback for Mt. Gox, but the exchange put in new security measures and stabilized, becoming the largest exchange by 2013. These security measures, however, weren’t enough and it is believed that there was an ongoing theft that was the result of a long-running hack or series of hacks that allowed the attacker(s) to slowly siphon off large amounts of Bitcoin over time.
The loss of these funds severely affected the price of Bitcoin at the time and caused a great deal of controversy and speculation within the cryptocurrency community. In early February of 2014, Mt. Gox stopped Bitcoin withdrawals. A few weeks later, all trading was stopped.
After filing for bankruptcy, MtGox’s assets were seized by a Japanese court, and its CEO, Mark Karpeles, was arrested and charged with embezzlement and fraud. The bankruptcy proceedings and the investigation into the theft of the Bitcoins from MtGox lasted several years and affected the trust and reputation of Bitcoin as a whole.
Silk Road
The Silk Road case was groundbreaking, as it was one of the first large-scale cases involving Bitcoin and dark web marketplaces. It highlighted the challenges that law enforcement agencies face when trying to investigate and prosecute illegal activities on the Internet.
Silk Road has been a fixture in Bitcoin’s history since the currency first caught the attention of mainstream media. It was an online marketplace for goods where users could transact in a permissionless manner using Bitcoin. The website had an Ebay-like interface, and allowed for buying and selling drugs, pirated digital goods, weapons, books on topics such as computer hacking and drug manufacture, counterfeits and forgeries, fake passports, and government IDs… Payments were facilitated by an escrow system that mixed all incoming and outgoing coins in order to obscure their origin. This granted its users complete anonymity, on top of the fact that the website was hosted and operated as a “hidden service” on the Tor network, also known as the “dark web”. Silk Road was run by a user who was known to others only as “Dread Pirate Roberts”.
The Tor network, also known as The Onion Router, is a free and open-source software designed to enable anonymous communication online. The network is composed of volunteers who operate servers and relays, and its main purpose is to protect users’ privacy and security by preventing anyone from tracking their online activity, including their location and the websites they visit.
Tor works by encrypting and routing internet traffic through a series of relays, making it difficult for anyone to identify the original source of the data. This makes Tor a popular tool for whistleblowers, journalists, activists, and others who need to protect their online identity and communications.
Tor attracted different profiles of users for different reasons. Some were looking for a safe and convenient way to buy and sell illegal items, others were looking for cheaper goods, and others would be simply following an ideological belief, particularly around libertarianism and the belief that the government should not control the freedom of Internet users.
Silk Road first truly broke into the public eye on June 1, 2011, when an article on gawker.com made a detailed review of the service. A few days later, the US government caught on, and senators Charles Schumer and Joe Manchin called for the website to be shut down immediately, proclaiming that “Never before has a website so brazenly peddled illegal drugs online” and “by cracking down on the website immediately, we can help stop these drugs from flooding our streets.”
One of the factors contributing to Silk Road’s cohesive community and initial success was the high level of trust. Scams are a serious problem on the darknet because of the anonymity of the participants and the fact that going to the police for help necessarily implies confessing to a crime. At the time, Silk Road was one of the few places that attempted to counteract this with a reputation system and a built-in escrow service.
The default way of making transactions in Silk Road is that the buyer sends his funds not to the seller directly but to the escrow system. When this happens, the system notifies the seller that it has received and is holding the funds. Once the buyer receives the product, he notifies the escrow system that the transaction was successful, and the seller gets his money.
One major controversy among the service’s users is that of morality. There have been instances of people putting up images that constitute child pornography in some jurisdictions but are acceptable in others. There have also been requests for credit card skimming devices, which were not allowed under “Silk Road law”, but which some people believed were no more immoral than counterfeits and drugs. Weapons were another concern. In such cases, Dread Pirate Roberts eventually resolved that particular issue with the middle-of-the-road option of banning them from Silk Road itself but allowing them on a specifically designed sister site called “The Armory”. Services such as theft and contract killing were banned from Silk Road and The Armory entirely, although some Silk Road users would point buyers interested in such goods to a competing site with no moral restrictions at all, Black Market Reloaded.
“Bitcoin would be convenient for people who don’t have a credit card or don’t want to use the cards they have, either don’t want the spouse to see it on the bill or don’t trust giving their number to “porn guys”, or afraid of recurring billing.“ – Satoshi Nakamoto
In May 2013, Silk Road was taken down for a short period of time as a result of a sustained DDoS attack. One month later, it was reported that the DEA had seized 11.02 bitcoins, worth $814 at the time, which the media suspected was a result of a honeypot. The FBI claimed that the real IP address of the Silk Road server was found via data leaked directly from the site’s CAPTCHA and that it was located in Reykjavík, Iceland.
Dread Pirate Roberts was arrested on October 2 2013 in Glen Park Library, a branch of San Francisco’s public library. The person behind the pseudonymous username, Ross Ulbricht, was indicted on charges of money laundering, computer hacking, conspiracy to traffic narcotics, and attempting to have 6 people killed. Even though prosecutors alleged that Ulbricht had paid $730,000 to others to commit the murders, none of the murders actually occurred. Ultimately, Ross was not prosecuted for any of the alleged murder attempts.
The FBI seized 26,000 bitcoins from accounts on Silk Road, worth approximately $3.6 million at the time. The FBI would hold the bitcoins until Ulbricht’s trial finished, after which the bitcoins would be liquidated. Days later, the FBI reported that it had seized 144,000 bitcoins belonging to Ulbricht, worth $28.5 million at the time. One year later, the U.S. Marshals Service sold 29,657 bitcoins in 10 blocks in an online auction, estimated to be worth $18 million. Another 144,342 bitcoins which had been found on Ulbricht’s computer were kept (roughly $87 million). Famous venture capital investor Tim Draper bought the bitcoins at the auction with an estimated worth of $17 million, to lend them to a bitcoin start-up called Vaurum which is working in developing economies of emerging markets.
Ulbricht’s trial began on 13 January 2015 in a federal court in Manhattan, where he admitted being the founder of Silk Road but that he had transferred control of the site to other people soon after he founded it. The jury ended up convicting Ulbrich of charges such as engaging in a continuing criminal enterprise, narcotics trafficking, money laundering, and computer hacking.
Two federal agents, DEA agent Carl Mark Force IV and Secret Service agent Shaun W. Bridges, were also arrested and convicted for corruption and stealing bitcoin during the Silk Road investigation. Force had used an alias and stolen bitcoins from Ross, while Bridges had stolen additional bitcoins from Silk Road during the investigation. Both agents were sentenced to prison for their crimes. Additionally, two former agents who had worked on the investigation, Chris Tarbell and Andrew Jones, went on to work for private companies offering cryptocurrency-related services.
In his letter to the judge before his sentencing, Ulbricht admitted that he had committed his actions through libertarian idealism, but also acknowledged that he made a “terrible mistake” that “ruined his life”. May 29, 2015, he was sentenced to five concurrent sentences, including two life imprisonments without parole and was ordered to forfeit $183 million.
- February 2011: Silk Road is launched.
- June 2011: The first drug transaction is completed on Silk Road.
- August 2013: Ross Ulbricht is arrested in San Francisco and charged with drug trafficking, money laundering, and computer hacking offenses.
- October 2013: The FBI seizes the Silk Road website and shuts down the marketplace.
- November 2013: Silk Road 2.0 is launched by a different group.
- December 2013: The FBI arrests Blake Benthall, the alleged operator of Silk Road 2.0.
- November 2014: Ross Ulbricht is found guilty on all counts related to the operation of Silk Road.
- May 2015: Ross Ulbricht is sentenced to life in prison without the possibility of parole.
- November 2015: The Silk Road auction takes place, in which the U.S. Marshals Service sells 50,000 bitcoins seized from Ross Ulbricht.
Wikileaks
Wikileaks is a non-profit organization that was founded in 2006 by Julian Assange. The Australian editor and cypherpunk activist founded Wikileaks with the main purpose to publish classified and sensitive information from anonymous sources. This would promote transparency and hold governments and other organizations accountable for their actions.
Four years later, Wikileaks became well-known for publishing a large number of classified U.S. government documents, including diplomatic cables and military records, that were leaked by former U.S. Army intelligence analyst Chelsea Manning. The release of these documents caused controversy and raised questions about government secrecy and the role of whistleblowers.
In response to the publication of the classified documents, various payment processors and financial institutions, including Visa, Mastercard, PayPal, and Bank of America, cut off their services to Wikileaks. This made it difficult for the organization to receive donations and continue its operations. This is where Bitcoin comes in as a censorship-resistant alternative for fundraising and donations. Since then, bitcoin has become associated with Wikileaks and other organizations that have faced financial censorship or government pressure to shut down their operations.
“Overnight practically, PayPal, Visa, Mastercard, they just shut off WikiLeaks from 97% of its revenue which came through (donations via the platforms). And how was it done? It was done completely extralegally. It was a phone call from a few senators in the U.S. to these companies, and they just shut it off.” – Stella Assange
One of the latest posts of Satoshi Nakamoto in 2010 made a direct reference to the emerging story of Wikileaks:
“The project needs to grow gradually so the software can be strengthened along the way. I make this appeal to WikiLeaks not to try to use Bitcoin. Bitcoin is a small beta community in its infancy. You would not stand to get more than pocket change, and the heat you would bring would likely destroy us at this stage.” – Satoshi Nakamoto
“ It would have been nice to get this attention in any other context. WikiLeaks has kicked the hornet’s nest, and the swarm is headed towards us.” – Satoshi Nakamoto
After reading these comments, Assange confirmed that the WikiLeaks team had looked into the matter and that they agreed with Nakamoto. As a result, they decided against accepting bitcoin donations at such an early date, giving the cryptocurrency more time to mature and establish itself as an alternative method of payment.
“Bitcoin is an extremely important innovation, but not in the way most people think. Bitcoin’s real innovation is a globally verifiable proof publishing at a certain time. The whole system is built on that concept and many other systems can also be built on it. The blockchain nails down history, breaking Orwell’s dictum of ‘He who controls the present controls the past and he who controls the past controls the future.” – Julian Assange
The first Bitcoin ETF
In the United States, the first Bitcoin ETF was approved in October 2021, allowing investors to gain exposure to Bitcoin through a regulated financial instrument traded on a major stock exchange. Prior to that, some countries such as Canada and Europe had already approved Bitcoin ETFs.
The first Bitcoin ETF was approved for trading on the Toronto Stock Exchange on February 18, 2021. This represented the most significant level of adoption of cryptocurrencies by the traditional banking and finance system to date.
CoinJoins
History of CoinJoin
In 2013, Bitcoin Core contributor Gregory Maxwell introduced the idea of CoinJoin as a solution to the poor privacy of Bitcoin transactions. However, it wasn’t until August of that year that he launched a multi-signature escrow bounty fund to incentivize the development of a practical CoinJoin tool. Shortly thereafter, Bitcoin developer Amir Taaki and programmer Martin quickly built an early version of a CoinJoin mixing tool, which allowed users to contribute a fixed amount of Bitcoin and create a transaction returning the same amount of funds back to each of them.
By merging multiple transactions into a single transaction, it becomes unclear which address belongs to which user, breaking the multiple-input heuristic which is often used for blockchain analysis. This improves privacy for both individuals and businesses who use Bitcoin.
This simple tool was just the beginning, as Taaki and a small group of like-minded Bitcoiners started a crowdfunding project to realize a privacy-focused wallet with a CoinJoin mixer built in. The project raised over $50,000 from more than 1,000 donors around the world and the team met in Milan to design the wallet with a group of programmers. However, the project attracted controversy as it was promoted as a money laundering tool, with the name “Dark Wallet” referring to the FBI’s warning that strong encryption could make the internet “go dark”.
In 2014, unSystem released Dark Wallet’s first alpha software, a user-friendly Chrome extension featuring several privacy tools, including stealth addresses and hierarchical deterministic wallets. The wallet also included a CoinJoin tool that allowed users to merge transactions and gain privacy. Dark Wallet’s alpha release attracted mainstream media attention and was even noticed by the Islamic State, who showed interest in using the wallet to hide their tracks. Despite this, the unSystem team continued to develop the wallet without concern.
Development of the Dark Wallet continued throughout 2014, with the alpha 8 version released in 2015. The wallet featured several privacy tools, including stealth addresses and a CoinJoin tool. However, funds were running low, and the project’s public face, Taaki, left to fight in Syria. The lead developer, Martin, also disappeared, causing development to stall. Nevertheless, the project served as an inspiration for other privacy-focused developers, and the unSystem group emphasized Bitcoin’s anti-establishment roots and created a first-generation set of Bitcoin privacy tools.
Then, Chris Belcher designed JoinMarket, a CoinJoin application, after realizing that few users offered their coins to be mixed in the Dark Wallet alpha release. Two other privacy-focused wallets, Samourai Wallet and a project by privacy researcher Adam Ficsór, also included various privacy tools. Samourai Wallet and Ficsór’s project announced in mid-2017 that they were working on a mixing tool inspired by Maxwell’s original CoinJoin post, which would let dozens of users mix their coins at once.
CoinJoin has become a standard privacy tool and is being used by Samourai Wallet’s “Whirlpool,” Wasabi Wallet, and JoinMarket. Advancements in techniques such as PayJoin, SNICKER, and Knapsack mixing are expected to further enhance the potential of CoinJoin. Taaki, the face of the Dark Wallet project, has reunited with its lead developer Martin and has set up an academy in Barcelona to inspire the creation of projects that promote privacy and autonomy, which may include a revival of Dark Wallet.
How it works
A CoinJoin is a trustless method for combining multiple Bitcoin payments from multiple spenders into a single transaction. This makes it more difficult for outside parties to determine which spender paid which recipient or recipients. Unlike many other privacy solutions, CoinJoin transactions do not require a modification to the Bitcoin protocol.
In Bitcoin, each input is an output from a past transaction, and the protocol makes sure that the inputs exist and are spendable, and that the sum of the output values is less than or equal to the sum of the input values (any excess represents fees that are paid to miners).
In the illustration above, the second transaction spends coins which are assigned to two outputs. To understand CoinJoins, we start off by negating the assumption that both outputs belong to the same party. Usage in a single transaction does not prove common control, and this is what makes CoinJoin possible: the signatures inside a single transaction are completely independent of each other. This means that it’s possible for Bitcoin users to agree on a set of inputs to spend, and a set of outputs to pay to, and then to individually and separately sign a transaction and later merge their signatures. The resulting transaction is not valid and will not be accepted by the network until all signatures are provided.
As a more practical example, when you want to make a payment, you could find someone else who also wants to make a payment and make a joint payment together. Doing so will not significantly increase your level of privacy,, but it can make your transaction smaller and easier on the network (lower in fees). From the outside, such a transaction is indistinguishable from a transaction created through conventional use.
Example of a 2-party CoinJoin transaction: https://chain.localbitcoins.com/tx/c38aac9910f327700e0f199972eed8ea7c6b1920e965f9cb48a92973e7325046
Example of a 3-party CoinJoin transaction: https://chain.localbitcoins.com/tx/92a78def188053081187b847b267f0bfabf28368e9a7a642780ce46a78f551ba
There are some considerations that users must account for:
- There are fees associated with the execution of CoinJoin transactions.
- You should avoid using centralized mixers, as they actually take control of your Bitcoin for a period of time.
After performing a CoinJoin, it is recommended to be aware of future spending habits:
- Check how you label your UTXOs before spending.
- Avoid merging UTXOs when possible.
- Label your change outputs.
- Make a CoinJoin for every spend.
While mixing can be done through a server-based model or a decentralized model, the main issue with the server-based model is that the server controller can access the participants’ data, while the decentralized model lacks liquidity. JoinMarket is a marketplace for CoinJoin transactions that allows users to offer spots for a small fee or buy access to CoinJoin transactions. Samourai Wallet also offers a CoinJoin imitation feature to throw off blockchain analysis.
Drawbacks
CoinJoin can mix inputs and outputs effectively, but it may not be enough to protect privacy if the amounts being sent and received are revealing. If the amounts of inputs and outputs are easily connected, it can still be possible to trace transactions.
For example, If one input sends 4.9 bitcoins, another input sends 2.7 bitcoins and a third input sends 0.8 bitcoins, while one output receives 4.9 bitcoins, one receives 2.7 bitcoins and a third receives 0.8 bitcoins, then it’s simple to connect inputs to outputs.
Another risk associated with CoinJoin transactions is the possibility of Sybil attacks where seemingly multiple participants can be controlled by a single entity monitoring the transaction. There is no easy solution to this problem, but as more genuine users mix their coins, the possibility of successful Sybil attacks decreases.
Lastly, CoinJoin is still not widely adopted by wallets and the available implementations like JoinMarket require special software and fees. Therefore, it is still a hassle for users to use it.
Confidential transactions
Bitcoin is not entirely anonymous since Bitcoin addresses can be linked to real-world identities. Analyzing the public blockchain, monitoring the unencrypted peer-to-peer network, and complying with KYC or AML regulations can provide insights into who is using Bitcoin and for what purposes.
To enhance privacy, it is possible to hide the amount of bitcoins transacted. An early version of this concept then referred to as “bitcoins with homomorphic value,” was first proposed in 2013 by hashcash inventor and current Blockstream president Dr. Adam Back. The idea was later picked up by Bitcoin Core and Blockstream developers Gregory Maxwell and Dr. Pieter Wuille and Blockstream mathematician Andrew Poelstra. This eventually led to the implementation of Confidential Transactions in Blockstream’s testnet-sidechain, Alpha.
Confidential Transactions use cryptographic techniques like Borromean ring signatures and Pedersen commitment schemes to hide transaction amounts from anyone except the sender and receiver. However, masked amounts can still be used for certain types of calculations without being revealed. This allows nodes to verify that no bitcoins were created without knowing the actual amount sent. The mining fee is always visible, but other amounts can be made visible if desired.
It can also be implemented in Bitcoin through a soft fork, with upgraded and non-upgraded nodes staying in sync by using an “anyone-can-spend” address as an intermediate step. Old nodes would see this as a regular address, while new nodes would recognize it as part of a Confidential Transaction and require the correct signature. As long as most nodes follow the new rules, the bitcoins on the anyone-can-spend address would be secure.
An “anyone-can-spend” address to cloak transaction amounts is also used by Confident Transactions. New nodes recognize this as a Confidential Transaction, but old nodes see it as a zero-bitcoin transaction. This doesn’t cause issues because bitcoins received through a Confidential Transaction can only be spent in the same way and are temporarily locked up in the anyone-can-spend address. To spend them normally, they must first be sent back to the anyone-can-spend address. As a result, the anyone-can-spend address acts as a cloaking device and makes subsequent transactions invisible to all nodes until the bitcoins are sent back to the address.
Confidential Transactions can help mask the amounts in Bitcoin transactions, but they are not a complete solution for privacy. One potential weakness is that the sending and receiving addresses are still visible. To obfuscate where the bitcoins really went, false negatives can be created and Confidential Transactions can be combined with CoinJoin. Also, Confidential Transactions are only effective if widely used, but they are quite resource-heavy and cost significantly more than typical transactions. The large size of Confidential Transactions also poses a challenge for scalability and decentralization.
However, keeping scalability in mind, Blockstream has been focused on making Confidential Transactions as efficient as possible. When Confidential Transactions is combined with CoinJoin, it becomes much more difficult to censor transactions as a miner because there is more difficulty associated with identifying the individuals behind specific transactions.
Finally, not everyone agrees that Bitcoin should be more private or fungible, which could complicate any potential soft forks to implement these changes.
Privacy in Bitcoin
Bitcoin is not a protocol optimized for privacy. The only privacy that exists in Bitcoin comes from pseudonymous addresses, which are fragile and easily compromised through reuse, “taint” analysis, tracking payments, IP address monitoring nodes, web-spidering, and many other mechanisms.
“Bitcoin is still very new and has not been independently analyzed. If you’re serious about privacy, TOR is an advisable precaution.” – Satoshi Nakamoto.
The Bitcoin blockchain is completely public and anyone can go to a block explorer and look up any transaction, analyze it, and start building a picture of an entity’s spending habits. This is exactly what blockchain analytics firms do. Using a series of assumptions, they can cluster transactions together to follow the movements of a given entity across the chain.
CoinJoins are one of the most effective privacy tools. The way these transactions are constructed makes it very difficult to know exactly which transaction output belongs to which of their input owners. A proper CoinJoin implementation completely breaks all deterministic links with the coins’ pre-CoinJoin history. At best, anyone can look at the transaction and hypothesize with a series of plausible scenarios, but they can never be 100% sure.
Enhancements to Bitcoin that have improved privacy
There have been multiple upgrades to Bitcoin that have improved overall privacy.
Segregated Witness
The Segregated Witness upgrade in 2017 made performing advanced scripting updates to the Bitcoin codebase significantly easier. The upgrade improved Bitcoin users’ transaction privacy by enabling future updates such as the addition of Schnorr Signatures and support for sidechains.
Schnorr signatures are a method of signing Bitcoin transactions that was recently added to Taproot as part of an upgrade. Unlike ECDSA signatures, Schnorr signatures allow for the consolidation of multiple signatures into a single one, enhancing privacy and making multi-signature and smart contract transactions more accessible and affordable. They not only improve transaction privacy but also facilitate scaling by reducing the size of multi-signature transactions.
Taproot
Taproot is a 2021 upgrade to the Bitcoin Core codebase with the goal of improving transaction privacy while reducing the amount of data required to complete sophisticated sidechain transactions, resulting in significant fee reductions. Additionally, the privacy benefit will be extended to apps that make use of time-locked contracts, such as CoinSwap, which combines Bitcoin transactions to obscure the origin and destination of the transaction.
Similar to this is how the Lightning Network, a second-layer network for aggregating off-chain transactions, operates. Taproot will encrypt these applications. Taproot combines Schnorr signatures with Merkelized Abstract Syntax Trees (MAST) — a technique for concealing a smart contract’s unexecuted branches. It enhances privacy and scalability by removing data from the blockchain.
Taproot enhances the privacy of transactions on sidechain protocols such as the Lightning Network, CoinSwap, multi-signature, and smart contracts by making them appear identical to standard single-signature on-chain transactions.
Lightning Network Privacy Enhancements
Lightning Network is an off-chain transaction solution. Its security approach is almost identical to that of on-chain Bitcoin transactions.
- Lightning transactions are not recorded on a publicly accessible ledger.
- Lightning transactions employ onion routing.
- Lightning transactions do not allow for the mixing of inputs and cannot be clustered.
Lightning Network transactions are fast and cost-effective compared to on-chain transactions. Two-way payment channels are created between nodes and transactions are routed through these channels. Transactions can also be routed through intermediary nodes, allowing for indirect connections between nodes. These transactions occur off-chain and are not broadcasted to all network nodes or recorded in a public blockchain, providing greater privacy and protection against adversarial attacks. The Lightning protocol uses onion routing to conceal the identity of intermediate nodes and prevent them from discovering the length or position of the route.
Segregating and labeling UTXOs
In Bitcoin, it is recommended for users to avoid reusing their wallet addresses. Also, it is a good practice to keep your Bitcoin separated from one another. This process is called segregation and can be achieved with wallets that support a feature known as coin control. For example, if you are holding 1 BTC split between two UTXOs of 0.5 BTC and you want to transfer 0.6 BTC, this transaction would result in your wallet combining those 2 UTXOs together in order to create an output that pays 0.6 BTC and you would be left with a change of 0.4 BTC (minus fees). However, we could imagine a hypothetical scenario where one of your 0.5 BTC was a change output from a blacklisted service, and the person you are transferring the funds to is a regulated entity that is actively performing on-chain analysis. In that scenario, they could refuse access to their service, block your account, or report your identity to the authorities.
The only tradeoff that comes with labeling your UTXOs and practicing coin control is the minimal extra overhead and steps required to do so. If you do not label and specify which UTXOs you want to spend in a transaction, your wallet will automatically do it for you
Running your own node
In Bitcoin, if you are not running your own node to verify your transactions, then you are trusting someone else’s node and abiding by their rules, which could be allowing false transactions to hit your wallet, leading you to believe you are receiving Bitcoin when in reality you are not.
From a privacy perspective, trusting someone else’s node means that they can see every transaction you send, every transaction you receive, all of your balances and, in some cases, even the addresses in your wallet.
Utilize multiple addresses
Bitcoin is a financial system that operates independently from traditional banking. It allows users to hold money without relying on a third party, putting the responsibility of asset security and accessibility on the user. Setting up a Bitcoin account on a home computer is simple and quick, allowing users to create unlimited distinct accounts. To protect privacy, it is recommended to create a unique Bitcoin address for each payment received, and have various wallets available for different purposes. Decoupling individual transactions is crucial to maintaining privacy, as individuals sending money do not know about additional Bitcoin addresses or their use.
Bitcoin Privacy Tools: Mixers, Tumblers, and Blenders
This is an established method for severing the transaction graph. Additionally, “tumblers” or “washers” are used to refer to them. A user sends bitcoins to a mixing service, which in exchange for a fee sends the user different bitcoins. Theoretically, a party observing the blockchain would be unable to connect incoming and outgoing transactions.
Tumblebit
TumbleBit is a 2016 anonymous payment protocol that is backward compatible with the current state of the Bitcoin protocol. TumbleBit allows parties to conduct transactions through an untrusted tumbler. Nobody knows who paid who during the TumbleBit epoch, not even the Tumbler. This is accomplished via a cryptographic mechanism in which the server facilitates the exchange of private digital signatures.
Anyone interested in privacy or Bitcoin will find the protocol extremely interesting. Because hundreds of users can perform this concurrently, transaction anonymity is maintained, as a large number of transactions (> 500) can be settled on the blockchain using only two transactions.
CoinSwap
CoinSwap is a non-custodial privacy technique for Bitcoin based on the concept of atomic swaps. CoinSwaps may appear to be identical to any other blockchain transaction. They make it possible for bitcoins to teleport undetectably to any other address on the blockchain. Non-CoinSwap transactions would benefit, as a large-scale blockchain analyst, such as one employed by a transaction surveillance company, can never be certain that ordinary transactions are not CoinSwaps. Additionally, they occupy a small amount of block space relative to the amount of privacy they provide.
CoinSwaps necessitate a high degree of interaction between the parties involved, which can make designing this type of system challenging while avoiding denial-of-service attacks. Additionally, they have aliveness and non-censorship requirements, which means that the entities participating must always have unrestricted access to the Bitcoin network; if the internet goes down for days or weeks, half-completed CoinSwaps may result in the theft of one party’s funds.
CoinJoin
CoinJoin is a simple protocol that enables strangers to pool their transactions. As the transaction will contain the inputs and outputs of multiple users, this helps conceal the destination address to which a single user sends data. Coinjoin transactions are a subset of Bitcoin transactions in which multiple individuals or entities collaborate to create a single transaction that incorporates all of their inputs. It accomplishes this by violating the heuristic of common input ownership and utilizing Bitcoin’s inherent fungibility within transactions.
This technique has been possible since the inception of Bitcoin and cannot be blocked except in the same way that any other Bitcoin transaction can be blocked. By looking at a transaction, it is impossible to determine for certain whether it is a CoinJoin or not. CoinJoins are non-custodial in nature, as they can be conducted without one party stealing another party’s bitcoins.
The Cantillon effect and the Nakamoto effect
The Nakamoto effect, or Cantillon effect 2.0 refers to the disruptive impact that the introduction of Bitcoin can have on the global economy. This is a testament to how decentralized systems could reshape the world, such that those who live closer to a fixed supply immutable monetary policy such as Bitcoin can receive value creation benefits in a Bitcoin world, rather than being rewarded for privilege, status, or geography.
In this context, Bitcoin is a response to the Cantillon effect, which describes the fact that new fiat money is created at almost zero cost and given to specific parties, usually banks. When this happens, a series of privileged players, mostly banks, have an opportunity to spend this money on goods and assets whose price has not yet reflected the increase in the money supply. This allows them to buy goods at a discounted rate. As the new money flows from central banks to private banks to investors to ordinary citizens, prices gradually begin to reflect the increase in the money supply. However, by the time ordinary citizens experience the increased money supply, they will be buying goods at higher prices. As a result, the flow of new money through the economy is beneficial to parties that receive the funds first, and less beneficial to those that receive it later on.
The Cantillon effect occurs when the central bank pumps money into the economy in order to reinflate asset prices during a period of debt deflation (and subsequent recession). Despite the central bank’s efforts, the beneficiaries of freshly produced money will often spend it on commodities and other associated assets rather than fighting the ongoing deflationary trend in debt markets.
The Nakamoto effect is a theory that has been posed as an alternative to the traditional central banking system. In Bitcoin, every ‘miner’ on the network has an equal shot at earning a reward of newly-created bitcoins every 10 minutes
- The emission rate is known beforehand by all stakeholders, meaning that everyone understands that a specific number of new bitcoins are released every 10 minutes and that this amount halves every 4 years. There is no central point of control and this monetary policy cannot be arbitrarily changed.
- There is a cap on the number of coins that will ever be released, 21 million BTC.
- The mining process with which new coins are released into circulation is open to the public. Anyone with the necessary hardware and source of energy can participate in maintaining the shared ledger and earn the newly released coins.
How Fiat could fall and Bitcoin Thrive
The story of fiat began in the 17th century, with the debut of paper money on the modern world scene. Initially, this paper money was backed by some form of commodity money, like gold or silver. Carrying and holding paper was simply more reliable and far more convenient than holding the actual precious metals that backed them. Over time, however, the government or bank in charge of printing the money issued more paper than it had metal to back it. Whether or not this was the “right” thing to do is a matter of debate, but once the devaluation process began, it inevitably spiraled, with more and more bills being issued at less and less value.
Gold is cumbersome to use as a medium of exchange. And while it is true that you can store a large amount of value in a relatively small package of gold, it isn’t very practical. This is the reason why the term coinage was invented. This would make it possible to mint coins in lower denominations that are more portable and interchangeable. However, the first episodes of currency debasement under this system date back to the fall of the Roman Empire. Caesar decided to start clipping coins. They would take a clip out of the sides of the coins (figure 5) and melt down these snippets into freshly minted coins while expecting people to maintain the belief that their purchasing power hadn’t diminished. Then they started diluting the mix of metals in the coinage further and again expected the citizens not to notice/care.
Soldiers demanded far higher wages as the quality of the coins diminished.
“Banks must be trusted to hold our money and transfer it electronically, but they lend it out in waves of credit bubbles with barely a fraction in reserve. We have to trust them with our privacy, trust them not to let identity thieves drain our accounts. Their massive overhead costs make micropayments impossible.” – Satoshi Nakamoto
For instance, a study of fiat currencies in the 20th century found that there were 56 episodes of hyperinflation. Another study found that the average life expectancy for a fiat currency is 27 years: 20 percent failed through hyperinflation (37 currencies experience hyperinflation in the 20th century), 21 percent were destroyed by war, 12 percent were destroyed by independence, 24 percent were monetarily reformed, and only 23 percent are still in circulation.
Of those that remain in circulation, all have lost huge amounts of their original value as measured in commodity money like gold or silver. Founded in 1694, the British pound Sterling is the oldest fiat currency in existence. At the ripe old age of 325 years, it must be considered a highly successful fiat currency. Yet, the British pound was originally defined as 12 ounces of silver, so it’s worth today is about half of 1 percent of its original value.
Similarly, the U.S. dollar was taken off of the gold standard in 1971, when it was 1/35th an ounce of gold. By 2011, it had already lost 97 percent of its value.
One of the main ways in which this devaluation took place is that governments were forced to print money to finance wars. Once one government started doing this, it became a classic prisoner’s dilemma and others had to follow suit. It would be better for everyone if no one fired up the presses, but as soon as one ruler or government warmed them up, then everyone else had to keep up or they risked being conquered.
As a matter of fact, part of the reason why Germany lost World War I and suffered worse inflation of their currency than the Allies was that the German and Austrian bond market was much less developed than the French, English and American markets, which had access to far more capital. Unable to raise money through bond issuances, Germany was forced to print money faster than other powers to finance their war effort.
It’s also worth noting that, in a democratic society, politicians are often unwilling to raise taxes or balance the budget because of the expected voter anger. For them, inflation and the devaluation of the currency are preferable because they constitute a hidden tax. On top of that, the consequences of poor decisions about monetary policy can take decades to show up, while politicians’ terms only last a few years – kicking the can down the road to finance their constituents and the projects of their favorite donors is also a way for them to get re-elected.
Nations and central banks that issue fiat currencies have often historically run into issues ranging between runaway inflationary spells and deflationary debt collapses (e.g., global central bank QE programs were used to defeat this). In the vast majority of cases, government-sanctioned central bank policies ultimately favor inflationary price outcomes that mostly benefit and grow the size, power, and wealth of those entities which tend to be closest to fiat currency creation. Typically governments, central banks, large commercial banks, lobbying corporations, financiers… are the entities who have first access to fiat currency and credit.
Ultimately, all the reasons for devaluation boil down to mismatched incentives between the people in control of the monetary policy and the individuals holding the currency.
One of the fathers of modern central banking is John Law, whose theories warned that poorly managed monetary policies can end with a vanishing middle class, fiat currency hyperinflation, mass violence, political upheaval, and emerging strong-man military dictatorships.
Since abandoning the gold standard, the world has seen more and deeper bank crises than ever before.
Instead of decisions about the monetary system, like a bailout or quantitative easing, Satoshi envisioned Bitcoin as a more robust monetary system, with a more distributed power structure that would make it impossible for a single individual or small group of individuals to act unilaterally.
The Bitcoin standard
- Bitcoin cannot be printed or debased, since it has a fixed limited supply of 21 million BTC.
- The transparency of the blockchain makes it possible to see how much is in circulation at any moment in time.
- There is a deflationary scheduled reduction every 4 years.
- Distributed software and distributed ledger based on a consensus system such that every transaction is verifiable.
- Bitcoin transactions are permissionless and borderless. The Bitcoin software can be downloaded by anybody worldwide.
- No counterparty risk. If you keep the seed phrase of a Bitcoin wallet secret and the transaction has enough confirmations, then nobody can take them from you no matter what.
Adopting Bitcoin
Bitcoin is gaining mainstream acceptance as a digital asset and means of exchange, with major companies like Microsoft, PayPal, and Starbucks accepting Bitcoin payments. Adoption is not limited to industrialized countries, as users based in the Middle East and North Africa received $566 billion in cryptocurrency, primarily Bitcoin and stablecoin remittances, in 2022. This demonstrates Bitcoin’s global appeal and utility and is a useful metric as places where technology is adopted most rapidly in areas where it is most necessary are a reliable way to evaluate the usefulness of that technology as a whole.
Barriers to adoption
The financial services industry itself is experiencing significant changes due to technological innovation, regulatory changes, and the shifting of consumer needs. Blockchain technology, with its properties of immutability, fast transaction settlements, and decentralization, has the potential to enhance the operational efficiency of financial systems and form the basis for decentralized finance (DeFi). However, there are still several barriers that must be overcome for distributed ledger technology (DLT) to achieve more widespread adoption across different areas of finance. Some of the perceived barriers include
- Regulation and legislation are not mature enough.
- Substantial amount of change is required to existing systems and processes.
- Unclear case of investment as the outcomes and needs to maintain parallel infrastructure are unpredictable.
- Demand and supply needs to be scaled in order for sufficient liquidity.
- Not full interoperability with legacy infrastructure.
- Executives and senior stakeholders are generally not supportive of such investments.
- Requires the onboarding of the entire population to perceive the full benefits of the technology.
- The use of DLT for clearing public securities has been met with an asymmetric response from regulators. Some regulators look to off-chain methods for record-keeping, although they leverage on-chain security tokens to represent the securities themselves. Others have fully embraced the blockchain as the golden source of truth. There is still a debate on the Central Securities Depository’s role in improving processes.
Despite these barriers, The Depository Trust and Clearing Corporation (DTCC) launched a permissioned blockchain network called “Project Ion” as an alternative settlement platform in August 2022. DTCC claims that the blockchain system can cover around 10% of the trading volumes processed by the firm’s classic settlement solutions. However, there is no clarity on when and if “Project Ion” will ultimately replace the current settlement systems in place at the DTCC.
A decentralized medium of exchange
The global FIAT money supply is estimated to be around $82.7 trillion. As a result, the importance of the medium of exchange in the financial services industry should not be overlooked. Bitcoin, during its peak in the 2021 bull cycle, had a market cap that surpassed many of the world’s largest currencies. However, this does not necessarily reflect its adoption as a medium of exchange, suggesting that Bitcoin is still in the early stages of adoption, with its most promising feature as a medium of exchange that does not rely on trusted third-party intermediaries, in the digital realm.
Decentralization has its pros and cons. According to a recent report, Bitcoin is the most decentralized digital asset based on various factors. The number of Bitcoin holders has become more globally distributed, and active addresses have continued to increase.
Bitcoin’s computing power was previously dominated by operators in China, but due to China’s ban on these activities, the US now holds the top spot at around 38%.
Increased decentralization leads to better security, which is important for any decentralized medium of exchange. Bitcoin has become more decentralized as the number of holders has become more globally distributed, resulting in better security. The central area of concern for Bitcoin is a 51% attack, where a single entity controls more than half of the computational power of the network. Despite a report from the Defense Advanced Research Projects Agency (DARPA) indicating that the likelihood of a 51% attack may not be as remote as many think, Bitcoin remains the most secure digital asset compared to others using the same hashing method in terms of the hash rate or computer power required to secure the network.
Bitcoin’s high degree of decentralization leads to lower network throughput, and transactions are added to a memory pool before being picked up by miners and added to newly minted blocks. However, the network’s throughput is relatively low at around 4.6 transactions per second, which is significantly lower than the 5,000 and 24,000 transactions per second processed by Mastercard and Visa, respectively. The fees for transactions on the Bitcoin network are also volatile and depend on network congestion.
Corporate adoption of Bitcoin
A 2022 PYMNTS’ report indicates that 85% of firms with an annual income of at least $1 billion are adopting crypto payments, and merchant acceptance for Bitcoin increased by 60%. The COVID-19 pandemic has accelerated crypto adoption, and the rise of digital payments has made it easier for mainstream payment networks, such as Visa and Mastercard, to introduce crypto payments. Visa’s network processed over $2.5 billion in crypto transactions by Q2 2022, and crypto payments have become increasingly popular with the rise in the use of stablecoin payments. Crypto-linked debit cards have expanded the number of partnerships between crypto-native payment providers and traditional payment networks. The more people are aware of and understand cryptocurrencies, the more they will adopt it.
Major companies that accept or utilize Bitcoin are:
- Wikipedia – Accepts donations in BTC.
- Microsoft – Allows the use of Bitcoin to top up Microsoft accounts.
- AT&T – First major U.S. mobile carrier with an option for cryptocurrency payment through BitPay.
- Burger King:
- KFC – Bitcoin was accepted for a limited time in exchange for “Bitcoin Bucket” ( a limited meal promotion)
- Overstock – A famous American online retailer partnered with Coinbase in order to allow Bitcoin payments for their online orders.
- Twitch – Accepted Bitcoin as payment for its services.
- Virgin Galactic – Allows you to pay for space travel with Bitcoin.
- And many more
Bitcoin’s Sovereign Seal of Approval
Countries may wish to support Bitcoin as a sovereign currency for the following reasons. They include boosting foreign investment, attracting tourism, lowering the cost of remittances, increasing access to financial services, and promoting education and awareness of digital assets. On the other hand, countries generally find it difficult to shift to using Bitcoin as a sovereign currency or even as a part of their treasury. One of the main challenges is the limited capacity to save, which means that Bitcoin cannot be used as a store of value. Additionally, Bitcoin adoption has negatively impacted sovereign credit ratings due to disapproval from international financial institutions. Finally, little or no access to capital makes it difficult for developing countries to weather the volatility of the crypto market.
El Salvador
El Salvador’s decision to make Bitcoin legal tender in September 2021 was seen as a major step towards Bitcoin’s mass adoption as a medium of exchange, but the country’s use of public funds to purchase Bitcoin and distribute it to citizens was not universally popular. Despite this, the move aimed to attract foreign investments and alleviate the burden of high commissions paid on remittances. However, key indicators suggest that Bitcoin’s adoption in the country is still minimal.
Despite being hailed as a historic move for Bitcoin adoption, El Salvador’s use of public funds to purchase Bitcoin and distribute it to citizens via the Chivo wallet application wasn’t universally popular. Data shows that adoption of Bitcoin in the country is minimal, with over 20% of respondents never installing the Chivo wallet and only less than 10% of the population using Bitcoin within the wallet after spending the $30 incentive.
El Salvador, however, continues with its Bitcoin program despite falling cryptocurrency prices, IMF warnings, and public discontent. The government has been purchasing 1 BTC per day since November 2022 and holds over 2,564 BTC, but is currently down by 44.5% on its Bitcoin holdings, resulting in an unrealized loss of over $49 million. However, as of March 2023, the total amount of BTC bought since El Salvador started its daily purchases of 1 BTC, along with its latest bulk purchase on July 1, 2022, has actually been profitable.
Central African Republic
The Central African Republic has passed legislation to adopt Bitcoin as a legal tender in order to attract foreign investment, lower remittance costs, and increase financial inclusion. Despite the many benefits, the country faces challenges, including having a purely digital medium of exchange in a country with an 11% internet penetration rate. However, the adoption of digital assets can be beneficial to the country’s competitiveness in the long term.
Why Bitcoin’s Blockchain is the Timechain
Archives have been published in Bitcointalk.org about how Satoshi shared pieces of Bitcoin’s code with cypherpunks before the launch of Bitcoin. In them, Satoshi thought of Bitcoin as a “timechain” and not a “blockchain”.
Find below a section of notes in a copy of the pre-release source code of Bitcoin that Satoshi shared with a few reviewers before mining the Genesis block in January 2009. This copy was shared on Bitcointalk.org in 2013
Blockchain and cryptocurrency inherently belong together. While blockchain is a distributed decentralized database that stores an ever-increasing number of records, Satoshi’s notes suggest that Bitcoin was meant to be a timechain, not a blockchain.
Naming a technology by the right name not only helps to separate and point out its uniqueness, but it also helps other people with understanding.
The term timechain was coined by Satoshi himself to reference Bitcoin’s time-based hashing operation, whose function is to serve as a distributed clock that makes sure that bitcoins get mined every 10 minutes on average. Besides, the term timechain also denotes immutability, where the longer chain is sufficient to trace back the entire transaction history of the chain.
The environmental effects of Bitcoin
Over the past years, there has been a growing concern over the high energy consumption and carbon footprint associated with Bitcoin mining. This is because bitcoins are made using electricity partially generated by gas and coal-fired power plants.
With the electricity consumption of entire nations, and the international community’s much stronger commitment to intensify decarbonization efforts to tackle climate change, Bitcoin seems to jeopardize those efforts. This has sparked a heated debate between proponents and opponents regarding the necessity of regulatory intervention.
As of 2022, bitcoin mining is estimated to be responsible for 0.1% of world greenhouse gas emissions. Other environmental concerns are linked to the air pollution caused by coal-fired electricity generation, and the e-waste (disposal of electronic appliances) due to the short life expectancy of bitcoin-mining equipment.
One of the biggest Bitcoin myths is that the Proof of Work (PoW) consensus mechanism used in the Bitcoin network is detrimental to the environment. This claim is often based on the large amount of energy required to mine Bitcoin and the carbon emissions associated with this energy consumption.
The Cambridge Bitcoin Electricity Consumption Index (CBECI) was launched in July 2019 in response to the growing demand for reliable data-driven insights about Bitcoin’s electricity consumption. The index estimates that by mid-September 2022, approximately 199.65 MtCO2e (million tonnes of carbon dioxide equivalent) can be attributed to the Bitcoin network since its inception. To put things into perspective, 48.35 MtCO2e represents approximately 0.10% of global greenhouse gas emissions and is similar to that of countries such as Nepal (48.37 MtCO2e) and the Central African Republic (46.58 MtCO2e), or about half that of gold mining (100.4 MtCO2e).
The annual energy consumption of Bitcoin mining is around 133.68 TWh, which is equivalent to the energy consumption of a small country like Argentina. At the same time, the carbon footprint of Bitcoin mining is around 63.6 million tons of CO2 per year, which is similar to the carbon footprint of the entire country of New Zealand
It should be noted that about 92% of the emissions have occurred since 2018
It’s important to note that the energy consumption of the Bitcoin network is often overstated and that much of the energy used in Bitcoin mining comes from renewable sources. Additionally, Bitcoin miners are incentivized to use the cheapest sources of energy available, which often means using excess energy that would otherwise go to waste.
“The heat from your computer is not wasted if you need to heat your home.” – Satoshi Nakamoto
Furthermore, the energy consumption of traditional banking and financial systems is often overlooked when comparing the environmental impact of different payment systems. Bitcoin’s PoW consensus mechanism provides a secure and decentralized system for processing transactions without the need for intermediaries or central authorities, which can ultimately reduce the overall energy consumption and carbon footprint of the financial industry.
- Not all energy use is harmful to the environment, since there are many forms of clean energy that are also cheaper than energy created from fossil fuels. The part of Bitcoin that uses electricity, mining, is an intensively competitive business and by necessity uses the cheapest sources of energy available, which come from clean sources of energy.
- Bitcoin incentivizes the development of abundant and clean energy that can benefit the efficiency of other industries as well as lower their pernicious environmental impact from fossil fuels. Also, the majority of miners are using energy that would otherwise have gone to waste. The process of oil extraction, for example, produces a natural gas byproduct that many companies simply choose to flare (burn off and waste) rather than building the infrastructure to capture it. As an example, crypto miners in North Dakota signed a deal with Exxon (a publicly traded oil and gas company) to direct gas emissions for new mining operations, instead of wasting it.
- If Bitcoin is considered to be sound money, then it can be argued that this is a good use of energy, or at least more worthwhile than other uses of energy, such as food processing, entertainment…
Climate damages for Bitcoin averaged 35% of its market value between 2016 and 2021. This share for Bitcoin was slightly less than the climate damages as a share of the market value of electricity produced by natural gas (46%) and gasoline produced from crude oil (41%), but more than those of beef production (33%) and gold mining (4%).
PoW vs PoS
PoW
Proof-of-Work (PoW) is the consensus mechanism that Bitcoin uses to regulate the creation of blocks and the state of the blockchain. Proof-of-Work provides an objective way for all members of the Bitcoin network to agree on the state of the blockchain and all Bitcoin transactions.
Transactions are verified by miners. They are participants that use a great amount of resources to ensure the network continues to run securely and correctly. Among other tasks, miners create and validate blocks of transactions. But in order to compete for the right to validate the next block, they need to use highly specialized mining hardware to solve complex mathematical puzzles.
PoW forces miners to make trillions of numerical guesses in order to produce a valid block, and thanks to the difficulty adjustment, miners collectively find one block every 10 minutes on average.
The following are the advantages of PoW:
- Fairness
- PoW is random and fair due to the strong randomness of the SHA-256 hash function which underlies the Proof-of-Work mechanism. There are no complex governance algorithms controlling which miners find blocks or decide the rules. Bitcoin relies completely on cryptography (a field of math), economic principles, and game theory to ensure that all miners remain honest.
- Incentives for decentralization
- PoW also incentivizes miner operations to decentralize geographically and organizationally, decentralizing Bitcoin as a whole. This is due to the fact that miners’ most significant cost is a variable cost: electricity. Miners are constantly in pursuit of lower energy costs, and because cheap energy is distributed across the globe, mining operations are also distributed across the globe.
- Scalable security
- Thanks to the difficulty adjustment, as Bitcoin rises in price, more miners start mining, driving the difficulty upwards and bolstering Bitcoin’s security. Thus, as Bitcoin becomes a more alluring target for attackers and a more threatening force to central banks, Bitcoin’s security increases, discouraging any attempts to attack the network.
- Algorithmic implementation
- PoW-based consensus algorithms and protocols are much simpler to implement and develop, as well as being less error-prone and therefore more secure, while PoS algorithms are more complex to implement, therefore more error-prone or more complicated to implement. extend its functionality. An example of this is the same Ethereum whose PoS was in development since 2018.
The following are the disadvantages of PoW:
- Energy Consumption
- PoS was invented to eliminate the massive energy costs of a PoW network. Many Bitcoin critics have cited its energy consumption as a downside to Bitcoin, and advocates of alternative cryptocurrencies have claimed their token will replace Bitcoin due to this fact.
- Both groups overlook or under-appreciate the value of Bitcoin’s ultimate security. No cryptocurrency, fiat currency, or even commodity-based money can match the security and immutability of Bitcoin’s blockchain. For high-value transactions, security and reliability are often more important than speed. Thus, Bitcoin’s energy consumption is well worth the cost, as indicated by the strong demand to transact on the Bitcoin blockchain. No cryptocurrency which has attempted to replicate Bitcoin and eliminate its energy requirements has established sufficient security and decentralization, precisely because PoW converts energy into security.
- Hardware Requirements
- Satisfying the PoW requirement necessitates physical computers and intensive computation. To maximize the energy efficiency of this process, miners use specialized hardware rather than normal laptops and general-purpose computers. These specialized computers are called ASICs, and they are not capable of anything other than Bitcoin mining.
- The fact that this hardware has only one use protects Bitcoin by discouraging attackers. If an attacker wanted to execute a 51% attack on the network, they would have to purchase millions if not billions of dollars worth of ASICs, only to render them useless by destroying the Bitcoin network.
- Vulnerability
- If you are vulnerable to a 51% attack or if you’re not on the most significant coin holder for any interchangeable hashing algorithm, individuals on a larger coin might turn their hardware against you and take you out, and you can no longer earn an incentive.
PoS
Proof-of-Stake (PoS) is an alternative consensus mechanism to PoW, developed and used by a few alternative cryptocurrencies. In the PoW model, stakers—the PoS equivalent of miners—lock up funds in a special smart contract. Every time a new block is needed by the network, an algorithm grants a specific staker the opportunity to publish the next block.
The algorithm selects the staker via lottery, depending on each staker’s percentage of total staked funds. For example, if a single staker controls 30% of all funds staked on a given network, they have a 30% chance of mining the next block.
The following are the advantages of PoS:
- Lowered energy consumption
- PoS does not require the immense amount of energy consumption required by PoW, because coins are simply locked in a specific smart contract on the blockchain. For this reason, individuals who criticize Bitcoin’s energy consumption prefer PoS.
- Better economical security
- PoS advocates also claim that PoS is more economically secure than PoW, however, this has been debated back and forth to no conclusion. Additionally, since Bitcoin has never been hacked and there are relatively few decentralized PoS systems, claims that PoS is more secure than PoW have remained purely theoretical and not based on any empirical evidence.
The following are the disadvantages of Pos:
- Governance problems
- PoS systems grant control of the network to owners of the token. Those with large amounts of the token can influence the rules of the network. They are also able to accumulate more of the token simply by staking. This positive feedback loop can lead to the centralization of staked funds in the hands of exchanges and large institutions that custody user funds.
- This is not the case for PoW systems. Bitcoin’s ruleset is controlled by nodes and miners, and no power over the network is given to Bitcoin owners.
- Vulnerability to Attack
- PoS systems are vulnerable to centralization and capture because control of the network is determined solely by capital, which is far more centralized than labor and cheap energy. In a PoS network worth $100 billion where 10% of tokens are staked, the $100 billion network can be taken over by any party able to allocate $10 billion. All the attacker would have to do is send $10 billion in tokens to a staking contract.
- In a PoW network, capital, labor, and efficient allocation of both are required to execute an attack on the network. Attacking a network with $10 billion of security would require purchasing ASICs, acquiring space and energy contracts to mine at a larger scale than the entire network, and acquiring and deploying the labor to execute the attack. If such an attack were underway, the entire network would likely be made aware ahead of time by the immense demand for ASICs and electricity.
- Track record
- As the concept is still relatively new, it may have drawbacks that are not yet evident to the crypto community. This paradigm, unlike proof-of-work, does not have a track record of performance.
Summary of Differences
| Proof of Work (PoW) | Proof of Stake (PoS) | |
| Who can mine/validate blocks? | The higher the computational power, the higher the probability of mining a block. | The more coins staked, the more likely you get to validate a new block |
| How is a block mined/validated? | Miners compete to solve complex mathematical puzzles using their computational resources. | Typically, the algorithm determines the winner randomly, taking into account the amount of coins staked. |
| Mining equipment | Professional mining hardware, such as ASIC, CPU, and GPU | Any computers or mobile devices with an internet connection |
| How are rewards distributed? | The first person to mine the block receives a block reward | Validators can receive a share of the transaction fees collected from the block they validated |
| How is the network secured | The greater the hash, the more secure the network | Staking locks crypto on the blockchain to secure the network |
Bitcoin myths
Bitcoin myths: We need Blockchain, not Bitcoin
It is often claimed by financial companies and fintech startups that Bitcoin would go away and that the blockchain technology behind the cryptocurrency could be implemented by traditional entities in the finance industry.
However, looking back at the origin story of Bitcoin as well as the cypherpunk inspiration and ethos behind its creation, it is clear that Bitcoin was not invented in order to help banks become more efficient.
The reason why Bitcoin has been able to stick around longer than things like Digicash and Egold is that it is powered by proof of work rather than trust in a centralized entity. Bitcoin’s greatest innovation is the fact that its payment processing technology and currency unit are the same thing and one cannot work without the other. This is the opposite of how things work, where payment processing technologies are controlled by corporations while currencies are backed by trust in centralized authority. As a result, there is no single point of failure to target. For true decentralization to exist, it is a requirement for the underlying token to be adopted and used to transact. This is also why the token is used to incentivize miners to secure the network.
With Bitcoin acting as the base layer, new digital cash systems, such as the Lightning Network, are able to be built without the risks of regulation or shutdown that were associated with the centralized systems of the past. This efficiency comes from the fact that it cannot be slowed down by regulatory pressures. As a matter of fact, if a blockchain can be easily controlled by regulators, then the reasoning behind using a blockchain in the first place becomes rather questionable because a centralized server will be more efficient than a distributed database.
Bitcoin myths: Bitcoin is not secure
The perception of Bitcoin’s insecurity stems from the frequent news and stories about hacks and scams involving Bitcoin exchanges and third-party services. None of these incidents reflect the security of the Bitcoin protocol itself.
The security of Bitcoin is based on its decentralized nature, which makes it difficult for any single actor to control the network, as well as the use of cryptography to secure transactions.
While individual users may fall victim to scams and hacks, the underlying Bitcoin protocol remains secure.
The key difference between Bitcoin and the traditional financial system comes down to personal responsibility. Most people are comfortable using platforms where transactions are reversible. In addition to the chances of having your credentials stolen and used for fraudulent purposes, online payment accounts are also subject to seizure, closure, and other types of financial censorship. For example, PayPal users have dealt with situations in which their funds have been seized or their accounts have been closed for a variety of reasons (e.g., Alex Jones, cam girls, Gab, WikiLeaks).
Bitcoin myths: Bitcoin is a Ponzi scheme
A Ponzi scheme is a fraudulent investment scheme where returns are paid to earlier investors using the capital of newer investors, without generating any real profits. However, Bitcoin is an open-source, decentralized digital currency that operates on a blockchain. It allows for peer-to-peer transactions without the need for intermediaries. As a result, the value of Bitcoin is determined by market demand and supply and not by any promises of returns.
Bitcoin myths: The intrinsic value fallacy
One of the earliest criticisms of Bitcoin was that the underlying token in the system had no intrinsic value. This point was an area of heavy debate among libertarians and Austrian economists who had become interested in Bitcoin as a potential digital alternative to gold in the early stages of the crypto asset’s development. Much of the debate revolved around Austrian school economist Ludwig Von Mises’s regression theorem. The regression theorem aims to explain the origin and development of money. According to this theorem, a good can only become a widely accepted medium of exchange (i.e. money) if it has a pre-existing non-monetary use, as this provides the initial demand for it. In other words, money must have some practical use beyond being used as a medium of exchange. For example, gold has non-monetary uses in jewelry, electronics, and other industries, which helped establish it as a widely accepted form of money.
The concept of intrinsic value is subjective. Ultimately, all value can be determined by supply and demand. One thing can be deemed valuable because people believe it is so. Bitcoin, for example, has several properties that give it value, such as its scarcity, divisibility, and portability. Bitcoin’s value is not based on speculation alone, but on the fact that it provides a useful function as a decentralized and censorship-resistant digital currency.
Bitcoin myths: Bitcoin is only used by criminals
Bitcoin’s core value proposition is that it is an uncontrolled, apolitical money. Because of that, some might infer that Bitcoin is only useful to people who want to get around various regulations imposed on the world’s financial systems and society more generally.
Bitcoin can be quite useful for criminals, much like physical cash. However, the permissionless nature of Bitcoin also enables other valuable use cases of this new technology. Cash, not Bitcoin, is still the preferred medium of exchange for illegal transactions. One reason for that is that Bitcoin’s public ledger makes it easy to track and trace illicit transactions, which makes it less attractive to criminals.
How Bitcoin differs from traditional payment systems
Traditional payment systems rely on the banking network to process transactions. Banks around the world are directly or indirectly connected to each other, and when a payment is initiated from a payer’s bank, it goes sequentially through various checking processes across a network of intermediaries. In contrast, the Bitcoin network is a peer-to-peer network of interconnected computers that verify and approve transactions while maintaining a ledger of all past transactions – the blockchain.
At the core of every transaction system lies a fundamental element of trust. This is handled differently based on whether the payment is done with cash, a credit card, or with bitcoin.
For example, with physical cash transactions, there is no intermediary. However, you still have to trust that you have not received a counterfeit banknote.
Card payments require processing from a payment network, such as VISA or Mastercard, as well as a banking network for authorization, clearing, and settlement. As a result, trust is generated by relying on reputable financial institutions that run a number of checks while the transaction is in progress.
For instance, the authorization stage verifies a customer’s identity as the owner of the funds and makes sure that there is enough balance. When the customer inserts a credit card into a terminal and enters the pin code, the following will occur:
- The payment details and your card information are sent to the merchant’s bank.
- The merchant’s bank then submits all the details it has received to the card network.
- The network will request authorization to your bank
- If the details are correct and there are available funds, then your bank will send an authorization to the merchant going through the same intermediaries over again.
This entire process happens within a few seconds. However, you can still walk out of the shop with your goods and the process will continue in the background.
The clearing process involves the exchange of transaction-related information that is used for the verification of the money debited from the customer’s bank and credited to the seller’s bank. At the end of every day, all approved transactions for the day are sent from the merchant to the merchant’s bank, which then transmits the details to the card network. The card network validates the information, sends the purchase information to customers’ banks, and finally sends reconciliation information to both the merchant’s and the customer’s banks.
Finally, settlements occur daily on an aggregated net basis, which involves the actual transfer of funds. The card network computes the net settlement position that the customer’s bank needs to pay to the merchant’s bank and sends that information to both banks, plus a new actor, the settlement bank. This settlement bank pays the merchant’s bank, and the customer’s bank pays the settlement bank. To finish the process, the merchant gets credited, and the customer gets debited.
In general, this entire process takes between 24 and 48 hours
As an alternative to the cumbersome and information-heavy process involved in traditional payment networks, Bitcoin transactions follow a very different path where there are no intermediaries.
The sender of a transaction only needs to specify the recipient’s Bitcoin address (similar to a bank account in a bank transfer) and the number of Bitcoins to send. Next, the sender wallet signs the transaction with the sender’s private keys to digitally sign the transaction and prove ownership of the funds. After that, a few nodes will receive the transaction and broadcast it to the network so that it can be independently verified by each of the nodes. Bitcoin miners will then gather transactions in a batch and begin trying to solve a computational problem in order to add the next block. When the block is added to the chain, all other nodes can easily check that the transactions have been included and that they cannot be reversed. The reason for that is that modifying the chain would require an extensive amount of computing power. As more blocks are added after the block containing your transaction, it becomes exponentially harder to modify that block by rewriting the chain. Finally, the merchant’s wallet will be able to confirm that the payment has been confirmed and that they are the owner of those bitcoins.
The completion time of this process varies depending on a variety of factors. On average, it takes 10 minutes to mine a Bitcoin block. It is recommended to wait at least 5 or 6 block confirmations to really consider a transaction effective (approximately 1 hour).
Bitcoin not only offers advantages in terms of anonymity, transparency, and independence from governments and central banks. When sending bitcoins to another party, it is a peer-to-peer transfer where there are no intermediaries. This is not the case in the traditional card payment system, which requires a minimum of four intermediaries, and often more.
Furthermore, Bitcoin is a distributed system that allows all components of the system to access and verify all transactions. This reduces the number of parties involved in a transaction and eliminates the need for third-party verification, which can speed up the transaction process. In addition to that, Bitcoin is a global system with an underlying set of rules that make fraud, manipulation, and errors almost impossible. As a matter of fact, in Bitcoin’s 10-year track record, no security flaw has ever been discovered and no one has found a way to change a signed transaction, or modify the blockchain.
Bitcoin Forum
While the original forum was created in November 2008, via Sourceforge, the new Bitcoin forum was launched by Satoshi in November 2009 and is still operating today. The forum was transferred to a new domain, Bitcointalk.org, on June 24, 2023. From the period of 2011 to 2024, Bitcointalk was the dominant venue for Bitcoin-related discussion.
Known hosts, owners, and associate names of the forum host include:
- Satoshi Nakamoto
- Sirius (Martti Malmi)
- Cobra
- Jeff Garzik
- Theymos (Michael Marquart), who was the main moderator/caretaker and is still active as of September 2023.
The main online venue for discussing Bitcoin appears to have shifted over the years. From the Bitcoin forum from 2010 to 2013, the subreddit from 2013 to 2017, and then finally onto Twitter. However, despite all the hiccups mentioned in this piece, the Bitcoin forum is still around and somewhat popular to this day.
FAQ
- What’s the difference between Bitcoin and Bitcoin?
- Bitcoin with capital B refers to the Bitcoin protocol
- Bitcoin with lower b refers to the virtual currency unit that operates in the system.
- What’s the difference between a Bitcoin node and a miner?
- A node is a computer that runs Bitcoin software and helps to verify transactions and maintain the integrity of the network by communicating with other nodes. By storing a copy of the blockchain, nodes can validate new transactions and enforce the consensus roles of the network.
- Miners are nodes that participate in the process of adding new blocks to the blockchain. They compete with each other to solve complex mathematical problems as part of the PoW algorithm. The first miner to solve the algorithm is rewarded with a certain amount of newly created bitcoins, and the new block is added to the blockchain.
- Is Bitcoin anonymous or pseudonymous?
- Bitcoin transactions are pseudonymous, meaning that while the identity of the person or entity behind a particular transaction is not immediately revealed, it is still possible to track the activities of any given wallet address over time.
- All Bitcoin transactions are recorded on the public blockchain, which is a decentralized ledger that is visible to anyone with an internet connection. While these public addresses are not directly linked to the identity of the person or entity that controls them, they can be traced back to a particular wallet or user through various methods, such as IP address tracking or analyzing patterns of transactions.
- Even though Bitcoin transactions do not reveal the identity of the user, they can still reveal information about the transaction itself, such as the amount of bitcoins transferred, the time of the transaction, and the destination address. This information, when combined with other data, can potentially be used to identify the user behind the transaction.
- What is the difference between a soft and a hard fork?
- Soft forks are backward-compatible changes to the protocol, meaning that nodes that have not upgraded to the new version will still recognize and accept the new blocks. Typically, soft forks don’t introduce new features and do not result in a split in the blockchain.
- Hard forks are non-backward-compatible changes to the protocol, meaning that the nodes that have not upgraded to the newer version will not recognize or accept the new block. Typically, hard forks introduce new features to the protocol, such as increasing the block-size limit. Because they are not backward-compatible, hard forks can result in a split in the blockchain, creating two or more different versions of the blockchain that are incompatible with each other.
- What are block rewards?
- Block rewards are a form of incentive for miners to validate transactions and add new blocks to the blockchain in a proof-of-work system like Bitcoin.
- Every time a miner successfully adds a new block to the blockchain, they are rewarded with a certain amount of new Bitcoin, which is called the block reward. This reward is created by the protocol itself and is designed to decrease over time.
- What’s the network hash rate?
- The hash rate of the Bitcoin network is the cumulative processing power of the mining machines securing the network.
- Does the halving influence Bitcoin’s price?
- The Bitcoin halving can affect Bitcoin’s price, although the exact impact is difficult to predict and depends on a variety of factors.
- One of the main reasons why the halving can affect bitcoin’s price is because it reduces the rate at which new bitcoin is introduced into the market. With fewer new bitcoins being created, the supply of available bitcoin is reduced, which can create upward pressure on the price as demand remains constant or increases. This has historically led to Bitcoin price increases following halving events.
- However, halving is not the only factor that can influence Bitcoin’s price, and other market factors such as investor sentiment, global economic conditions, regulatory changes, and technological advancements can also play a significant role. For instance, some investors believe that Bitcoin halvings should be priced in because their occurrence is public knowledge.
- What will happen when the block reward becomes too small?
- Ultimately, transaction fees will replace the block reward as the primary revenue for miners.
- For some, this will be economically untenable. At the same time, it can be argued that advancements in transaction batching and other layer-two technologies will likely iterate this problem away.
- What is backing Bitcoin?
- Bitcoin is not backed by any physical commodity or government, which is one of the key differences between it and traditional fiat currencies like the US dollar or the Euro. Instead, Bitcoin’s value is primarily derived from a combination of factors such as supply and demand dynamics, scarcity, investor sentiment (medium of exchange, store of value…), adoption rates, and the perceived utility of the currency.
- How much is Satoshi Nakamoto worth?
- Satoshi reportedly holds 1M bitcoin. The total value depends upon market conditions and Bitcoin’s price. For example, if Bitcoin had a market value of $29,000, the total value would be $29 billion.
- What is the difference between P2PKH and P2SH?
- P2PKH and P2SH are both different types of Bitcoin transaction output scripts that specify how the recipient can claim the funds sent to their Bitcoin address.
- P2PKH (Pay to Public Key Hash) is the most common type of transaction output script used in Bitcoin. It requires the recipient to provide a public key and a digital signature that proves they are the rightful owner of the Bitcoin address. The public key is hashed using the SHA-256 and RIPEMD-160 algorithms to create a unique identifier called a “hash160” that is used as the recipient’s Bitcoin address.
- P2SH (Pay to Script Hash) is a type of transaction output script that allows for more complex spending conditions. Instead of specifying a public key hash as the recipient address, P2SH specifies a hash of a script that the recipient must satisfy to spend the funds. This script can be any valid Bitcoin script, including multi-sig scripts and more complex smart contracts. This makes P2SH more flexible than P2PKH and allows for more complex spending conditions.
- What happens after all 21 million bitcoin are mined?
- Miners don’t only mint new coins – they also collect transaction fees. The issuance of new coins is only meant to help bootstrap the system while the transaction volume is low. As Bitcoin adoption increases, so does demand for (limited) block space and thus so do transaction fees.
- Can the maximum limit of 21M bitcoin be changed?
- Technically yes, although this is a question about governance and incentives. Anyone can change the limits enforced by their own node – the hard part is convincing everybody else to do the same with their nodes.
- A few Bitcoin critics claim that since Bitcoin is nothing more than software, the rules of the Bitcoin network can be changed easily. These critics believe that as the block subsidy—the amount of new bitcoin minted in each block—shrinks every four years, miners, who expend resources to produce new bitcoin, will seek to defend their revenue stream by increasing the supply cap beyond 21 million bitcoin.
- In order to change the supply cap of Bitcoin, several groups would have to collaborate. First, developers would have to propose and then write the code to implement this change. Next, the community would have to agree to an activation path, in order to ensure that the network transitioned to the new ruleset collectively. Finally, a hard fork would be required so that all nodes on the network either accept the changes or are forced to leave the network.
- Can a software bug kill Bitcoin?
- Bitcoin is a decentralized network, and the software that runs it is open-source and maintained by a community of developers. Therefore, any bugs or vulnerabilities discovered in the software can be fixed by the developers through updates and patches.
- However, a severe bug or vulnerability could potentially lead to the loss of funds or other disruptions to the network. For example, in 2018, a bug was discovered in Bitcoin’s software that could have allowed an attacker to create an unlimited number of bitcoins. This bug was quickly patched by developers, but if it had not been caught and fixed, it could have caused significant harm to the network.
- If a critical vulnerability was detected, the first step would be for the developers to release a fix as soon as possible. The fix would be disseminated to the Bitcoin network, and node operators would be encouraged to update their software to the new version that contains the fix. In the event that a large number of nodes and miners do not upgrade their software to the fixed version, a “fork” could occur, where the blockchain splits into two separate chains with different rules. This could potentially result in two separate versions of Bitcoin, each with its own distinct set of rules and users.
- To prevent this from happening, Bitcoin developers and community members would likely work together to encourage as many nodes and miners as possible to upgrade to the fixed software. They may also consider implementing a “flag day” where all nodes must update their software by a certain date or risk being left behind on an obsolete chain.
- Is Bitcoin centralized and controlled by its developers?
- Bitcoin is not centralized and is not controlled by its developers. Bitcoin is a decentralized network that operates on a consensus mechanism where changes to the protocol are proposed by developers and implemented by users through nodes. The Bitcoin protocol is open source and anyone can contribute to its development by proposing changes or improvements. However, changes to the protocol must be approved by the network’s users through a consensus mechanism, which includes miners, node operators, and other stakeholders. This means that while developers play an important role in proposing changes, they do not have complete control over the network.
- While Bitcoin Core has some structure (it uses centralized communications channels in order to coordinate), the project itself is not subject to being controlled by any of its participants — even those who have escalated privileges on the GitHub repository. While it is technically possible for a maintainer-organized coup to hijack the GitHub repository, censor dissenting developers, and perhaps even maintain the brand name of “Bitcoin Core,” the result would be that Bitcoin Core would stop being the development focal point. Developers who disagreed with the actions of the maintainers would simply fork the code and shift their work to a different repository over which the Bitcoin Core maintainers had no administrative privileges.
- Who controls Bitcoin?
- It’s practically impossible to fully comprehend Bitcoin as a system. The definition (control) of Bitcoin protocol is like the definition of a language. Languages emerge spontaneously; the consensus over the meaning of words is organic rather than dictated by dictionaries.
- While changes to the Bitcoin protocol itself are usually made via the Bitcoin Improvement Proposal process, even this is only a recommended best practice and no one can be forced to follow it. It is merely a more formalized way of trying to guide a change through a process of peer review and consensus building.
- Why isn’t my transaction confirmed?
- If it has been a while and your transaction has not been confirmed yet, this is probably because you are using a lower fee rate relative to other transactions in the mempool. There’s no need to panic—a Bitcoin transaction will always either confirm completely (or not at all) at some point. As long as you have your transaction ID, you can always see where your funds are.
- Does MEV apply to Bitcoin?
- MEV can be present in both PoW and PoS consensus. However, MEV has rarely appeared on Bitcoin since practically all Bitcoin transactions are “simple” transactions that only transfer Bitcoin between two parties. In practice, more complex transactions are required for MEV to flourish, such as frontrunning, backrunning, sandwich attacks…
- There is no mechanism preventing MEV from occurring other than the fact that Bitcoin’s present use cases do not create many opportunities for MEV.
- What is an orphan block?
- In blockchain terms, orphan blocks are blocks that are mined simultaneously as another block, but that do not end up being accepted by the blockchain. Most of the time, this is because there are not enough blocks generated from that block for the network to recognize it as the longest chain. Only one of these blocks can be included in the blockchain, and the other is considered an orphan block.
- When two miners solve a block at nearly the same time, they both broadcast their solutions to the network. This creates a temporary fork in the blockchain until one of the two blocks is accepted by the network as the valid block, and the other block becomes an orphan block. Orphan blocks typically occur when two miners solve a block at nearly the same time, which is known as a race condition. The orphan block is still considered a valid block and contains valid transactions, but it is not included in the blockchain and its miner does not receive the block reward or transaction fees associated with it.
- Orphan blocks are a natural occurrence in the Bitcoin network, and they can be caused by factors such as network latency and miner hash rate fluctuations. While orphan blocks do not have any negative impact on the security of the Bitcoin network, they can lead to temporary delays in transaction confirmations and can also result in the loss of block rewards and transaction fees for the miners who produced them.
- How difficult is it to make a Bitcoin payment?
- Bitcoin payments are easier to make than debit or credit card purchases and can be received without a merchant account. Payments are made from a wallet application, either on your computer or smartphone, by entering the recipient’s address, and the payment amount, and pressing send. To make it easier to enter a recipient’s address, many wallets can obtain the address by scanning a QR code or touching two phones together with NFC technology.
- Why do people trust Bitcoin?
- Much of the trust in Bitcoin comes from the fact that it requires no trust at all. Bitcoin is fully open-source and decentralized. This means that anyone has access to the entire source code at any time. Any developer in the world can therefore verify exactly how Bitcoin works. All transactions and bitcoins issued into existence can be transparently consulted in real time by anyone. All payments can be made without reliance on a third party and the whole system is protected by heavily peer-reviewed cryptographic algorithms like those used for online banking. No organization or individual can control Bitcoin, and the network remains secure even if not all of its users can be trusted.
- Is Bitcoin fully virtual and immaterial?
- Bitcoin is as virtual as the credit cards and online banking networks people use every day. Bitcoin can be used to pay online and in physical stores just like any other form of money. Bitcoins can also be exchanged in physical form such as the Denarium coins, but paying with a mobile phone usually remains more convenient. Bitcoin balances are stored in a large distributed network, and they cannot be fraudulently altered by anybody. In other words, Bitcoin users have exclusive control over their funds and Bitcoins cannot vanish just because they are virtual.
- Is Bitcoin anonymous?
- Bitcoin is designed to allow its users to send and receive payments with an acceptable level of privacy as well as any other form of money. However, Bitcoin is not anonymous and cannot offer the same level of privacy as cash. The use of Bitcoin leaves extensive public records. Various mechanisms exist to protect users’ privacy, and more are in development. However, there is still work to be done before these features are used correctly by most Bitcoin users.
- Some concerns have been raised that private transactions could be used for illegal purposes with Bitcoin. However, it is worth noting that Bitcoin will undoubtedly be subjected to similar regulations that are already in place inside existing financial systems. Bitcoin cannot be more anonymous than cash and it is not likely to prevent criminal investigations from being conducted. Additionally, Bitcoin is also designed to prevent a large range of financial crimes.
- Is Bitcoin useful for illegal activities?
- Bitcoin is money, and money has always been used both for legal and illegal purposes. Cash, credit cards, and current banking systems widely surpass Bitcoin in terms of their use to finance crime. Bitcoin can bring significant innovation in payment systems and the benefits of such innovation are often considered to be far beyond their potential drawbacks.
- Bitcoin is designed to be a huge step forward in making money more secure and could also act as a significant protection against many forms of financial crime. For instance, bitcoins are completely impossible to counterfeit. Users are in full control of their payments and cannot receive unapproved charges such as with credit card fraud. Bitcoin transactions are irreversible and immune to fraudulent chargebacks. Bitcoin allows money to be secured against theft and loss using very strong and useful mechanisms such as backups, encryption, and multiple signatures.
- Some concerns have been raised that Bitcoin could be more attractive to criminals because it can be used to make private and irreversible payments. However, these features already exist with cash and wire transfer, which are widely used and well-established. The use of Bitcoin will undoubtedly be subjected to similar regulations that are already in place inside existing financial systems, and Bitcoin is not likely to prevent criminal investigations from being conducted. In general, it is common for important breakthroughs to be perceived as being controversial before their benefits are well understood. The Internet is a good example among many others to illustrate this.
- Can Bitcoin be regulated?
- The Bitcoin protocol itself cannot be modified without the cooperation of nearly all its users, who choose what software they use. Attempting to assign special rights to a local authority in the rules of the global Bitcoin network is not a practical possibility. Any rich organization could choose to invest in mining hardware to control half of the computing power of the network and become able to block or reverse recent transactions. However, there is no guarantee that they could retain this power since this requires them to invest as much as all other miners in the world.
- It is however possible to regulate the use of Bitcoin in a similar way to any other instrument. Just like the dollar, Bitcoin can be used for a wide variety of purposes, some of which can be considered legitimate or not as per each jurisdiction’s laws. In this regard, Bitcoin is no different than any other tool or resource and can be subjected to different regulations in each country. Bitcoin use could also be made difficult by restrictive regulations, in which case it is hard to determine what percentage of users would keep using the technology. A government that chooses to ban Bitcoin would prevent domestic businesses and markets from developing, shifting innovation to other countries. The challenge for regulators, as always, is to develop efficient solutions while not impairing the growth of new emerging markets and businesses.
- Is Bitcoin a Ponzi scheme?
- A Ponzi scheme is a fraudulent investment operation that pays returns to its investors from their own money, or the money paid by subsequent investors, instead of from profit earned by the individuals running the business. Ponzi schemes are designed to collapse at the expense of the last investors when there is not enough new participants.
- Bitcoin is a free software project with no central authority. Consequently, no one is in a position to make fraudulent representations about investment returns. Like other major currencies such as gold, United States dollar, euro, yen, etc. there is no guaranteed purchasing power and the exchange rate floats freely. This leads to volatility where owners of bitcoins can unpredictably make or lose money. Beyond speculation, Bitcoin is also a payment system with useful and competitive attributes that are being used by thousands of users and businesses.
- Doesn’t Bitcoin unfairly benefit early adopters?
- Some early adopters have large numbers of bitcoins because they took risks and invested time and resources in an unproven technology that was hardly used by anyone and that was much harder to secure properly. Many early adopters spent large numbers of bitcoins quite a few times before they became valuable or bought only small amounts and didn’t make huge gains. There is no guarantee that the price of a bitcoin will increase or drop. This is very similar to investing in an early startup that can either gain value through its usefulness and popularity or just never break through. Bitcoin is still in its infancy, and it has been designed with a very long-term view; it is hard to imagine how it could be less biased towards early adopters, and today’s users may or may not be the early adopters of tomorrow.
- Won’t Bitcoin fall into a deflationary spiral?
- The deflationary spiral theory says that if prices are expected to fall, people will move purchases into the future in order to benefit from the lower prices. That fall in demand will in turn cause merchants to lower their prices to try and stimulate demand, making the problem worse and leading to an economic depression.
- Although this theory is a popular way to justify inflation amongst central bankers, it does not appear to always hold true and is considered controversial amongst economists. Consumer electronics is one example of a market where prices constantly fall but which is not in depression. Similarly, the value of bitcoins has risen over time and yet the size of the Bitcoin economy has also grown dramatically along with it. Because both the value of the currency and the size of its economy started at zero in 2009, Bitcoin is a counterexample to the theory showing that it must sometimes be wrong.
- Notwithstanding this, Bitcoin is not designed to be a deflationary currency. It is more accurate to say Bitcoin is intended to inflate in its early years and become stable in its later years. The only time the quantity of bitcoins in circulation will drop is if people carelessly lose their wallets by failing to make backups. With a stable monetary base and a stable economy, the value of the currency should remain the same.
- Isn’t Bitcoin mining a waste of energy?
- Spending energy to secure and operate a payment system is hardly a waste. Like any other payment service, the use of Bitcoin entails processing costs. Services necessary for the operation of currently widespread monetary systems, such as banks, credit cards, and armored vehicles, also use a lot of energy. However, unlike Bitcoin, their total energy consumption is not transparent and cannot be as easily measured.
- Bitcoin mining has been designed to become more optimized over time with specialized hardware consuming less energy, and the operating costs of mining should continue to be proportional to demand. When Bitcoin mining becomes too competitive and less profitable, some miners choose to stop their activities. Furthermore, all energy expended mining is eventually transformed into heat, and the most profitable miners will be those who have put this heat to good use. An optimally efficient mining network is one that isn’t actually consuming any extra energy. While this is an ideal, the economics of mining are such that miners individually strive toward it.
- Could users collude against Bitcoin?
- It is not possible to change the Bitcoin protocol that easily. Any Bitcoin client that doesn’t comply with the same rules cannot enforce their own rules on other users. As per the current specification, double spending is not possible on the same blockchain, and neither is spending bitcoins without a valid signature. Therefore, it is not possible to generate uncontrolled amounts of bitcoins out of thin air, spend other users’ funds, corrupt the network, or anything similar.
- However, powerful miners could arbitrarily choose to block or reverse recent transactions. A majority of users can also put pressure for some changes to be adopted. Because Bitcoin only works correctly with a complete consensus between all users, changing the protocol can be very difficult and requires an overwhelming majority of users to adopt the changes in such a way that the remaining users have nearly no choice but to follow. As a general rule, it is hard to imagine why any Bitcoin user would choose to adopt any change that could compromise their own money.
- Is Bitcoin vulnerable to quantum computing?
- Yes, most systems relying on cryptography in general are, including traditional banking systems. However, quantum computers don’t yet exist and probably won’t for a while. In the event that quantum computing could be an imminent threat to Bitcoin, the protocol could be upgraded to use post-quantum algorithms. Given the importance that this update would have, it can be safely expected that it would be highly reviewed by developers and adopted by all Bitcoin users.
- Why isn’t my transaction confirming?
- If it’s been a while and your transaction hasn’t been confirmed, your transaction is probably using a lower fee rate relative to other transactions currently in the mempool. Depending on how you made your transaction, there may be ways to accelerate the process.
- There’s no need to panic—a Bitcoin transaction will always either confirm completely (or not at all) at some point. As long as you have your transaction ID, you can always see where your funds are.
- How can I get my transaction confirmed more quickly?
- How can I get my transaction confirmed more quickly?
- To get your transaction confirmed quicker, you will need to increase its effective fee rate.
- If your transaction was created with RBF enabled, your stuck transaction can simply be replaced with a new one that has a higher fee.
- Otherwise, if you control any of the stuck transaction’s outputs, you can use CPFP to increase your stuck transaction’s effective fee rate.
- If you are not sure how to do RBF or CPFP, work with the tool you used to make the transaction (wallet software, exchange company, etc). This website only provides data about the Bitcoin network, so there is nothing it can do to help you get your transaction confirmed quicker.
- How can I prevent a transaction from getting stuck in the future?
- You must use an adequate transaction fee commensurate with how quickly you need the transaction to be confirmed. See Mempool’s fee estimates on the front page.
- Also consider using RBF (if your wallet supports it) so that you can bump the fee rate on your transaction if it does end up getting stuck.
- Why are there empty blocks?
- When a new block is found, mining pools send miners a block template with no transactions so they can start searching for the next block as soon as possible. They send a block template full of transactions right afterward, but a full block template is a bigger data transfer and takes slightly longer to reach miners.
- In this intervening time, which is usually no more than 1-2 seconds, miners sometimes get lucky and find a new block using the empty block template.
- What does it mean for a mempool to be “full”?
- What does it mean for the mempool to be “full”?
- When a Bitcoin transaction is made, it is stored in a Bitcoin node’s mempool before it is confirmed into a block. When the rate of incoming transactions exceeds the rate transactions are confirmed, the mempool grows in size.
- By default, Bitcoin Core allocates 300MB of memory for its mempool, so when a node’s mempool grows big enough to use all 300MB of allocated memory, we say it’s “full”.
- Once a node’s mempool is using all of its allocated memory, it will start rejecting new transactions below a certain fee rate threshold—so when this is the case, be extra sure to set a fee rate that (at a minimum) exceeds that threshold. The current threshold fee rate (and memory usage) are displayed right on Mempool’s front page.
- Could the Bitcoin network be destroyed by someone generating endless Bitcoin addresses?
- When you generate a new Bitcoin address, it only takes disk space on your own computer (like 500 bytes). It’s like generating a new PGP private key, but less CPU intensive due to the use of ECC. The address space is effectively unlimited and, therefore, it doesn’t hurt the network if anyone chooses to generate more and more addresses.
- Why don’t block timestamps always increase?
- Block validation rules do not strictly require that a block’s timestamp be more recent than the timestamp of the block preceding it. Without a central authority, it’s impossible to know what the exact correct time is. Instead, the Bitcoin protocol requires that a block’s timestamp meet certain requirements. One of those requirements is that a block’s timestamp cannot be older than the median timestamp of the 12 blocks that came before it. See more details here.
- As a result, timestamps are only accurate to within an hour or so, which sometimes results in blocks with timestamps that appear out of order.
Community Links
- Bitcoin whitepaper: https://bitcoin.org/bitcoin.pdf
- Cypherpunk manifesto: https://nakamotoinstitute.org/static/docs/cypherpunk-manifesto.txt
- Nakamoto Institute: https://nakamotoinstitute.org/literature/
- Bitcoin core: https://github.com/bitcoin/bitcoin
- Bitcoin mempool explorer:
https://mempool.space/
- Bitcoin fees:
https://bitcoinfees.info/
- Coingecko: https://www.coingecko.com/en/coins/bitcoin