Overview
Humanity Protocol provides a decentralized identity infrastructure designed to solve the “unique-human problem” in Web3 by verifying users as real, singular individuals, without compromising privacy. Built on a Layer-2 zk rollup, the protocol integrates biometric palm recognition, zero-knowledge proofs (ZKPs), and self-sovereign identity (SSI) frameworks to create a Sybil-resistant network.  This ensures applications like voting systems, Universal Basic Income (UBI) distributions, and governance mechanisms remain fair and bot-free. By decentralizing identity verification, Humanity Protocol addresses flaws in both Web2’s monopolistic data practices (e.g., Facebook, Google) and Web3’s vulnerability to fake accounts, enabling secure interoperability between the on-chain and off-chain realms.
This ensures applications like voting systems, Universal Basic Income (UBI) distributions, and governance mechanisms remain fair and bot-free. By decentralizing identity verification, Humanity Protocol addresses flaws in both Web2’s monopolistic data practices (e.g., Facebook, Google) and Web3’s vulnerability to fake accounts, enabling secure interoperability between the on-chain and off-chain realms.
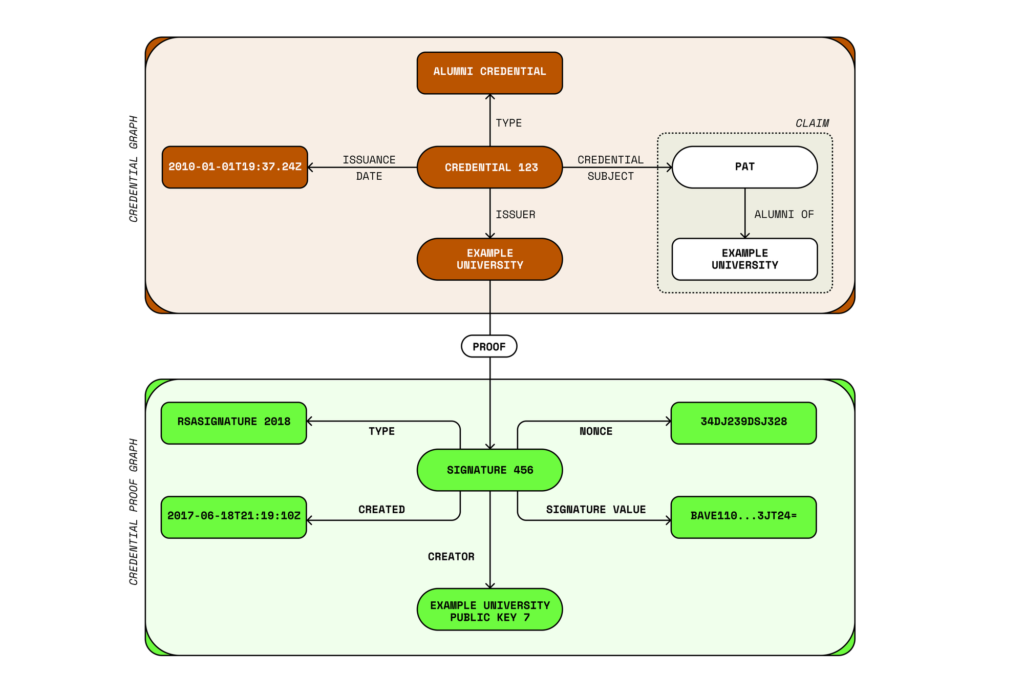
Verifiable Credentials
Verifiable Credentials (VC) are digital claims that represent a unique human user, sort of like your passport or identification cards. These generally contain information related to a specific holder, ranging from:
- Status (e.g. Human, institution)
- Identity (e.g. Name, Photo)
- Issuer (e.g. Government, KYC provider)
- Type (e.g. Education history, driver’s license)
- Constraints (e.g. Expiration, scope)
VCs are more convenient and tamper-resistant than traditional KYC methods because they are cryptographically secured with digital signatures. Once issued, they can also be independently verified via cryptographic proofs, making them ideal for use in the SSI model.
Why the Project was Created
Humanity Protocol was conceived to address systemic failures in digital identity systems across both centralized (Web2) and decentralized (Web3) ecosystems. These failures undermine fairness, privacy, and trust in critical applications—from financial services to governance.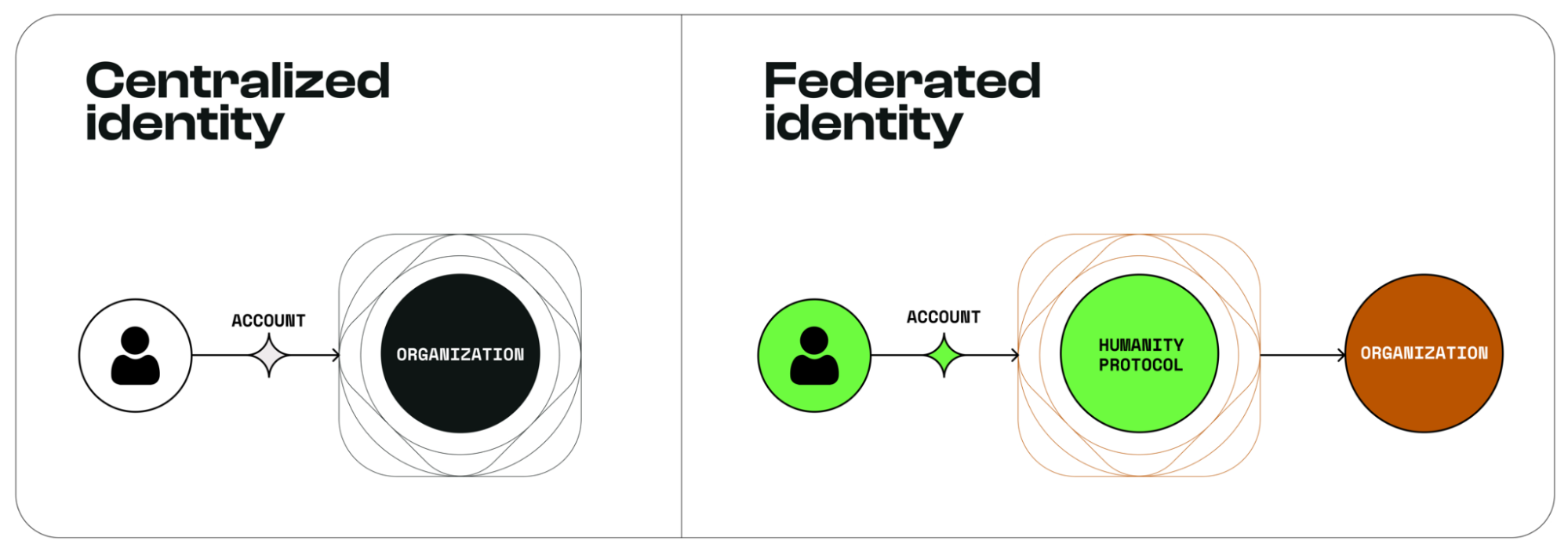 Traditional solutions, such as government-issued IDs or invasive facial recognition, compromise privacy or exclude marginalized populations. Humanity Protocol’s Proof-of-Humanity (PoH) mechanism sidesteps these issues by using palm-vein biometrics—a non-invasive, globally accessible method—paired with ZKPs to confirm uniqueness without storing sensitive data.
Traditional solutions, such as government-issued IDs or invasive facial recognition, compromise privacy or exclude marginalized populations. Humanity Protocol’s Proof-of-Humanity (PoH) mechanism sidesteps these issues by using palm-vein biometrics—a non-invasive, globally accessible method—paired with ZKPs to confirm uniqueness without storing sensitive data.
Humanity Protocol was developed to resolve two systemic challenges: Web2 centralization risks, and Web3 sybil attacks.
Web2 Centralization Risks
In Web2, dominant platforms like Google and Facebook act as de facto identity providers, harvesting and monetizing user data while exposing individuals to surveillance, breaches, and algorithmic manipulation. Billions lack government-issued IDs (e.g., 850M people globally, per World Bank), locking them out of digital economies. Federated identity models (e.g., “Sign in with Google”) deepen reliance on centralized gatekeepers.
Centralized identity systems, while efficient, suffer from critical flaws:
- Vendor Lock-In: Users and applications become dependent on single providers (e.g., AWS Cognito), risking service discontinuation or arbitrary fee hikes.
- Single Points of Failure: Data breaches at centralized custodians.
- Privacy Erosion: Centralized issuers retain full visibility into user activity, enabling mass profiling.
Web3 Sybil Attacks
Without robust identity layers, decentralized networks struggle with fake accounts distorting governance, airdrops, and resource allocation (e.g., bots claiming disproportionate UBI payments). The absence of credible identity frameworks limits Web3’s ability to bridge with traditional systems (e.g., credit scoring, property rights), perpetuating segregation between on-chain and off-chain economies.
Thus, the value proposition here is clear: a non-invasive biometrics KYC system (which are more culturally acceptable than iris/facial scans), using decentralized economics and interoperable credentials that can be ported across chains and real-world systems.
Protocol Architecture
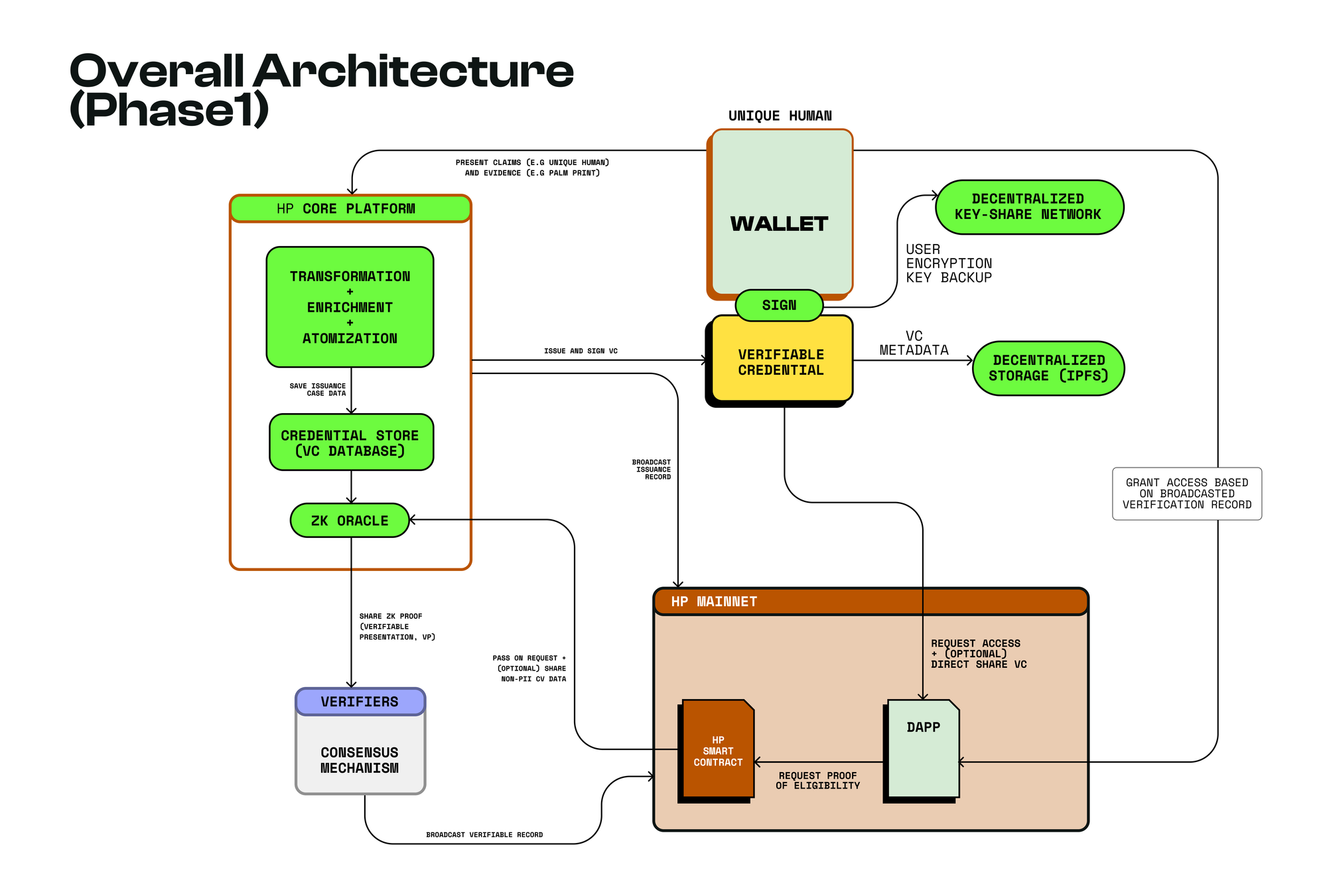
Humanity Protocol is engineered as a decentralized identity layer on a zkEVM-compatible Ethereum L2, structured to progressively decentralize and scale across two phases. In Phase 1, the protocol establishes a foundational network of verified unique humans.
Self-Sovereign Identity
SSIs enable users to have full control and autonomy of their own identity data. Users can then digitally sign and share data with third-parties (Verifiers) to verify the authenticity of user data on the blockchain.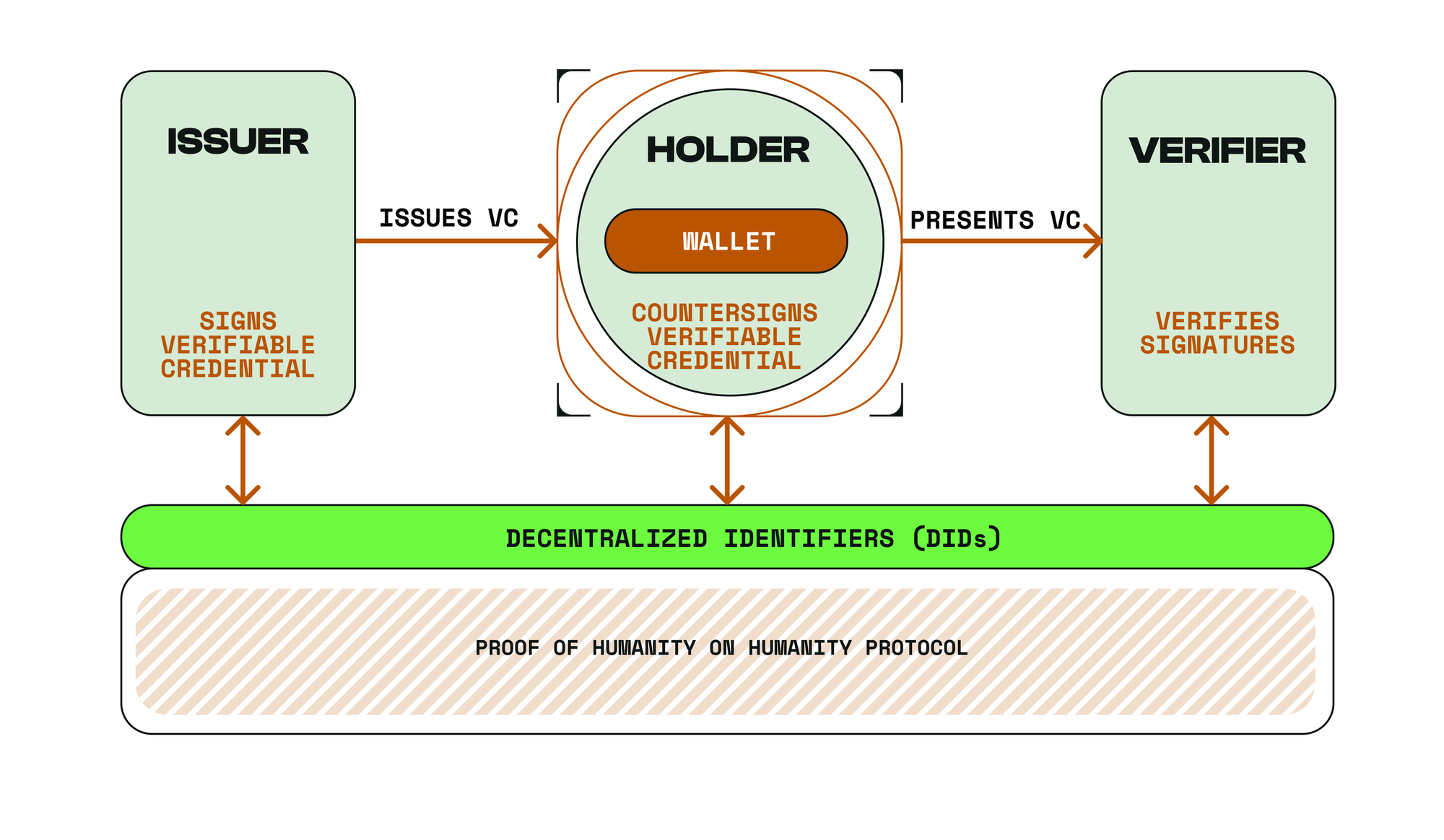 Proof of Humanity
Proof of Humanity
Users enroll by scanning their palm veins using accessible hardware—such as smartphones or specialized HP devices—leveraging an AI model trained on over 500,000 palm prints to ensure accuracy and resistance to spoofing. Biometric data is encrypted and stored off-chain in decentralized networks (e.g., IPFS), while only a cryptographic hash is recorded on-chain to preserve privacy.
ZKPs generated by zkProofer Nodes cryptographically confirm a user’s humanity without exposing sensitive details, anchoring these proofs to a decentralized identifier (DID) on-chain. Identity Validators, who stake the native $H token, then verify these proofs in a decentralized manner, ensuring Sybil resistance while earning rewards for honest participation.
Phase 2 expands the protocol into a full SSI ecosystem, enabling the issuance of verifiable credentials (VCs) for real-world attributes like education, employment, or asset ownership. Trusted entities—such as universities or employers—issue tamper-proof VCs linked to users’ DIDs, which are stored on-chain and controlled via private keys.
Users share credentials selectively using ZKPs, disclosing only necessary information (e.g., proving age without revealing a birthdate). The architecture adheres to W3C standards for interoperability, allowing credentials to function across blockchains, applications, and even physical systems. A modular design supports seamless upgrades, enabling integration of new credential types (e.g., healthcare data) or compliance frameworks (e.g., GDPR) without disrupting core operations.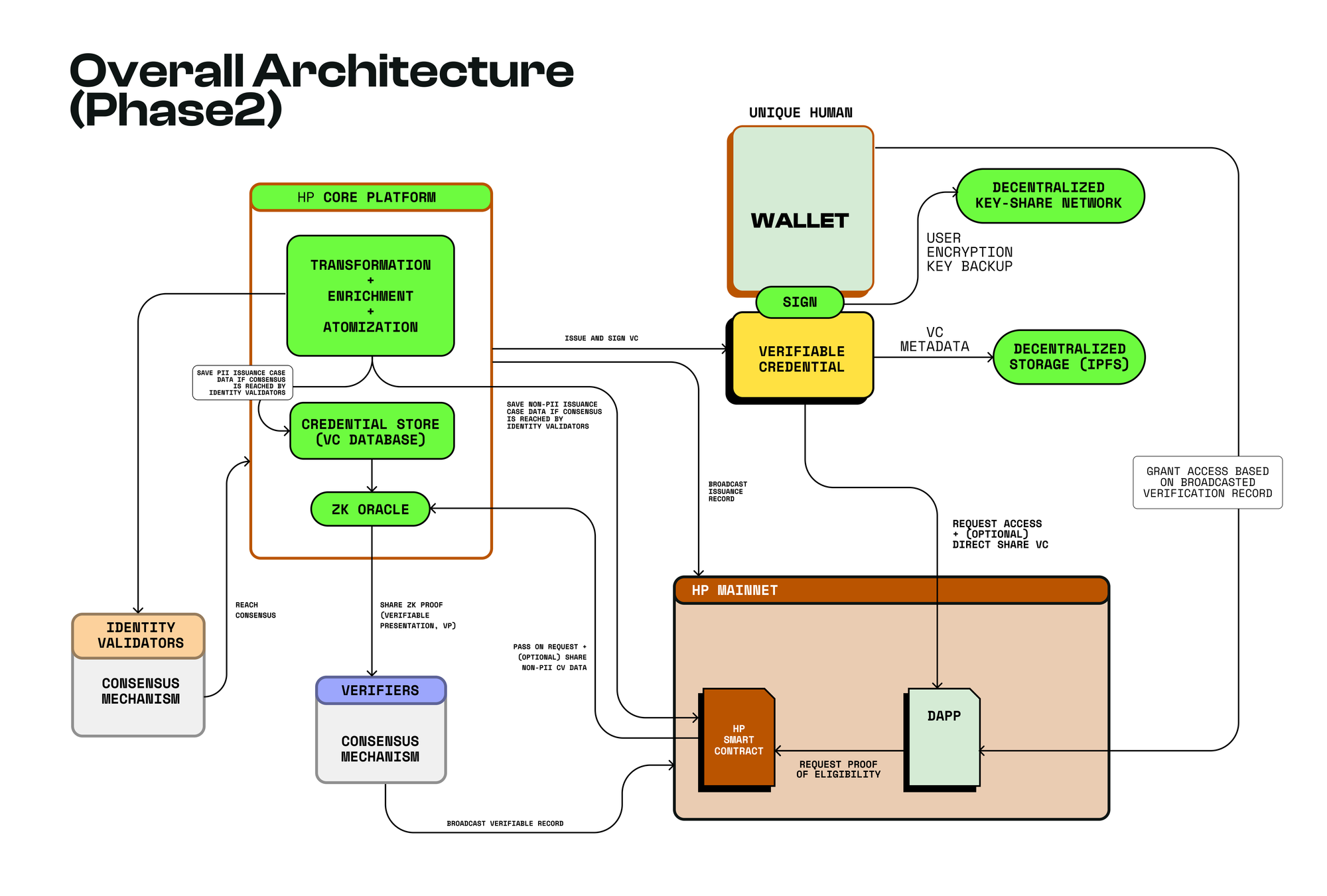
Human Recognition Module
Humanity Protocol’s Human Recognition Module employs a two-phased approach to verify human uniqueness. Phase 1 leverages smartphone cameras to capture palm prints via RGB imaging, ensuring accessibility through existing hardware. Phase 2 introduces palm vein recognition using a low-cost infrared device, enhancing accuracy by analyzing vein patterns. This dual-spectral method (visible + infrared light) balances inclusivity with precision, positioning the protocol as a scalable solution for global identity verification.
Humanity protocol’s reliance on palm biometrics—a high-information-density modality—ensures robust uniqueness. Palm prints (skin creases) and veins (haemoglobin patterns) provide distinct, stable identifiers. Fujitsu’s historical data (0.00008% false acceptance rate for veins) underscores technical viability. Combined, these modalities aim to resolve the “1-to-N” challenge, theoretically enabling uniqueness verification across billions of users.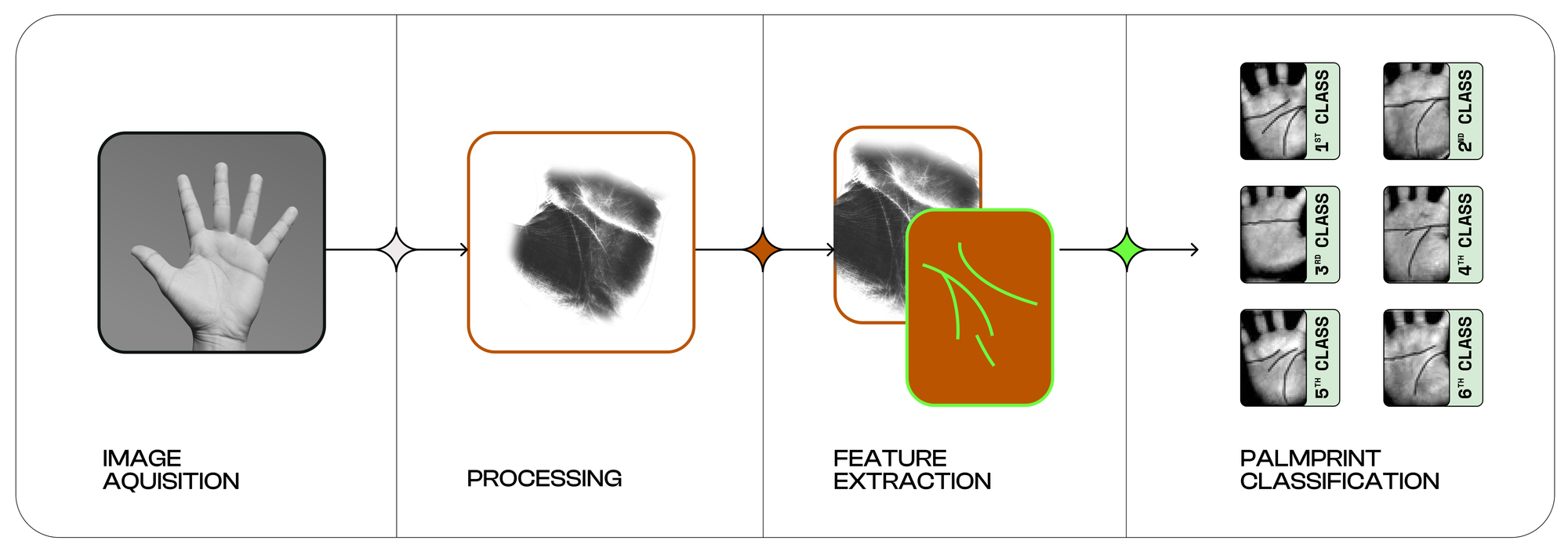 Unlike invasive methods (e.g., DNA), Humanity Protocol minimizes privacy risks by avoiding sensitive biometric storage. While specifics on data encryption are pending, the use of palm features—less personally identifiable than facial or fingerprint data—aligns with growing regulatory demands for privacy-first solutions.
Unlike invasive methods (e.g., DNA), Humanity Protocol minimizes privacy risks by avoiding sensitive biometric storage. While specifics on data encryption are pending, the use of palm features—less personally identifiable than facial or fingerprint data—aligns with growing regulatory demands for privacy-first solutions.
Privacy-Preserving Data Storage and Use
Humanity Protocol implements a multi-layered privacy protection framework to safeguard users’ personal data while enabling secure and seamless identity verification. At its core, the protocol uses Advanced Encryption Standard in Galois Counter Mode (AES-GCM) encryption, a robust and quantum-resistant encryption method, to protect all issued VCs. Each VC is linked to a user’s wallet and remains fully encrypted, preventing unauthorized access. Users also retain full control over their private keys, which are distributed across decentralized nodes using a key-share network like Lit Protocol. This decentralized key management system ensures enhanced security and key recovery, similar to Ethereum’s ERC-4337 account abstraction wallets, allowing users to regain access even if they lose their primary key.
Beyond encryption, Humanity Protocol decentralizes data storage to prevent any single entity from controlling user metadata. Instead of storing VCs in a centralized database, non-personally identifiable information (non-PII) is atomized and distributed across decentralized storage solutions such as the InterPlanetary File System (IPFS). To further enhance security, these VCs are indexed on-chain within an encrypted Merkle Tree, ensuring that data can be verified without revealing any sensitive information. Meanwhile, PII is stored off-chain using sharding techniques within the Humanity Protocol Core Platform, and access is restricted through ZKPs to prevent direct exposure of raw user data.
The final layer of privacy protection lies in privacy-preserving data use, ensuring that user data can only be accessed with explicit consent. Humanity Protocol allows two secure methods of credential verification for third-party applications. First, direct sharing of non-PII credentials allows users to verify basic information, such as proof of uniqueness, without exposing additional details. Second, indirect sharing of PII credentials through zero-knowledge verifiable presentations (VPs) enables applications to confirm specific user attributes—such as age, residency, or educational background—without ever revealing the actual data. This system ensures that even service providers requiring verification can validate user identities without compromising privacy.
By integrating these privacy-preserving mechanisms, Humanity Protocol provides a decentralized identity framework that balances security, control, and user convenience. With encryption, decentralized storage, and zero-knowledge proofs, users retain full ownership of their digital identities, aligning with self-sovereign identity (SSI) principles.
Identity Validators
Identity Validators in Humanity Protocol are trusted entities responsible for verifying user-submitted data and issuing domain-specific verifiable credentials (VCs) within the SSI framework.
Identity Validators form the backbone of the SSI ecosystem, transitioning from a centralized Phase 1 to a hybrid decentralized model in Phase 2. In Phase 1, the HP Core Platform acts as the sole Issuer, generating unique-human VCs after validating palm biometrics.
Phase 2 introduces a network of accredited, token-staked Identity Validators, distributing trust while maintaining accountability through economic incentives and institutional credibility. In this Phase, validators are required to stake $H tokens, aligning incentives with protocol integrity. This “trust-but-verify” model mitigates risks of a fully permissionless system while avoiding over-reliance on a single centralized issuer, balancing decentralization with user data privacy and safety.
Governance allows nominations and elections for Validator roles, with fixed terms to prevent power consolidation. This semi-decentralized approach fosters inclusivity and reduces collusion risks. However, Validator criteria (e.g., accreditation standards, stake size) will need rigorous enforcement to maintain trust in VC issuance.
Identity Validators access only the PII (Personally Identifiable Information) relevant to their domain (e.g., a university verifies academic records, not financial data). Sharding of PII metadata further limits exposure, reducing breach risks. However, encryption standards and ZK-proof implementations for verifiable presentations (VPs) must be robust to ensure end-to-end privacy.
zkProofer Nodes
zkProofer Nodes are a crucial component of the Humanity Protocol’s SSI framework, designed to facilitate secure and private identity verification. These nodes are responsible for processing and authenticating VCs and zero-knowledge (ZK) Verifiable Presentations (VPs), allowing users to prove aspects of their identity without exposing sensitive information. Their primary role is to verify credentials when users interact with third-party dApps, ensuring that authentication is conducted in a privacy-preserving manner.
To participate in the Humanity Protocol, zkProofer Nodes must obtain a license, distinguishing them from Identity Validators, which require a substantial stake in the protocol. This licensing model ensures that node operators are committed to maintaining network integrity. Additionally, verification requests undergo a consensus-driven process, where multiple Verifier Nodes must approve a credential before it is validated. The idea behind this decentralized verification mechanism is to strengthen the reliability of the system, preventing single points of failure.
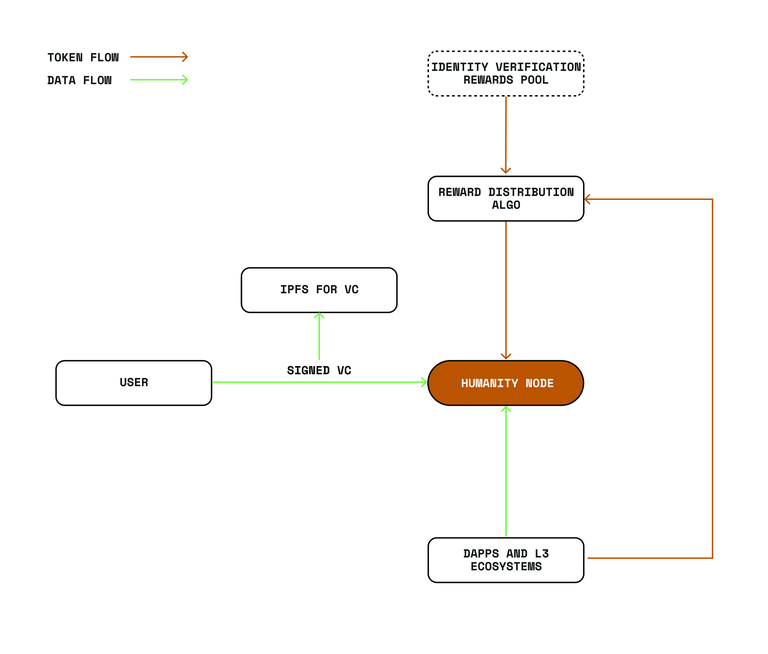
The incentive structure for zkProofer Nodes is designed to reward active participation. Operators receive compensation from two primary sources: the Identity Verification Rewards pool, which distributes the native $H token, and a minimum 25% share of verification fees collected from third-party DApps and ecosystem projects. These rewards are transparently recorded on the blockchain, ensuring accountability. Furthermore, to promote engagement, the Humanity Protocol introduces a tiered system, categorizing zkProofer Nodes into Basic, OG, and Founder tiers. Each tier offers different reward structures, with allocations determined through a random draw to maintain fairness.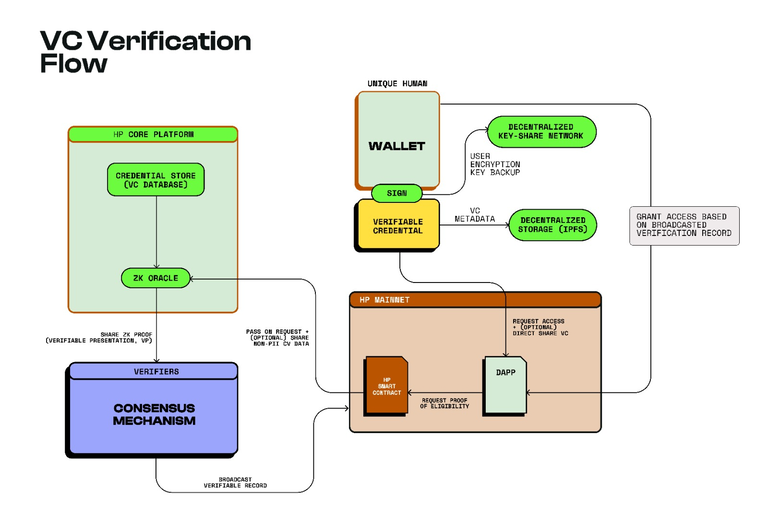 Node licenses are allocated through a random draw system. This mechanism ensures that all participants have an equal opportunity to acquire nodes of varying tiers, preventing centralization and promoting widespread network participation. The total supply of zkProofer Node Licenses is capped at 100,000, with availability determined by the structured draw system. This approach maintains a balanced ecosystem where node ownership is widely distributed rather than concentrated among a few entities.
Node licenses are allocated through a random draw system. This mechanism ensures that all participants have an equal opportunity to acquire nodes of varying tiers, preventing centralization and promoting widespread network participation. The total supply of zkProofer Node Licenses is capped at 100,000, with availability determined by the structured draw system. This approach maintains a balanced ecosystem where node ownership is widely distributed rather than concentrated among a few entities.
Different node tiers have different allocations as follows: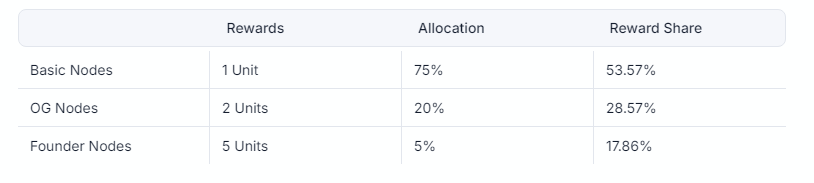 To reinforce the long-term sustainability of the ecosystem, 18% of all $H tokens are allocated to Verifier Nodes for user-related verification tasks. Additionally, 25% of all verification fees collected from ecosystem DApps are distributed among zkProofer Nodes. This dual-reward structure ensures that node operators remain incentivized to maintain network security, privacy, and efficiency.
To reinforce the long-term sustainability of the ecosystem, 18% of all $H tokens are allocated to Verifier Nodes for user-related verification tasks. Additionally, 25% of all verification fees collected from ecosystem DApps are distributed among zkProofer Nodes. This dual-reward structure ensures that node operators remain incentivized to maintain network security, privacy, and efficiency.
Human ID is Humanity’s protocol unique identification card.
It is currently on testnet but you can already register for it here: https://testnet.humanity.org/login Once in you are able to create your Human ID and key in your referral code and information.
Once in you are able to create your Human ID and key in your referral code and information.
 Once created, you’ll be in the dashboard. It is currently on testnet. The Palm Not Enrolled is a feature that will be released in Phase 2 when the palm scanners are distributed.
Once created, you’ll be in the dashboard. It is currently on testnet. The Palm Not Enrolled is a feature that will be released in Phase 2 when the palm scanners are distributed.
Palm Recognition
Humanity Protocol’s palm recognition biometrics scanner leverages both palm print and palm vein recognition to create a robust and highly reliable method for verifying human identity. Compared to other biometric systems, such as fingerprint or iris scans, palm recognition offers significant advantages due to the larger surface area of the palm and the complexity of its unique features. This complexity ensures a higher level of differentiation among individuals, making it an ideal solution for identity verification in digital ecosystems. The palm recognition process is executed in two phases to maximize accessibility and precision. Phase 1 employs palm print recognition, which uses personal smartphone cameras to capture images of the palm’s external features, such as skin patterns, lines, and creases. These attributes are analyzed using Convolutional Neural Networks (CNN) to extract key features and differentiate individuals. This phase enables quick and convenient user verification while ensuring a high level of accuracy in identifying unique individuals. However, since external palm prints may change over time due to aging or environmental factors, Phase 2 introduces a more advanced biometric approach.
The palm recognition process is executed in two phases to maximize accessibility and precision. Phase 1 employs palm print recognition, which uses personal smartphone cameras to capture images of the palm’s external features, such as skin patterns, lines, and creases. These attributes are analyzed using Convolutional Neural Networks (CNN) to extract key features and differentiate individuals. This phase enables quick and convenient user verification while ensuring a high level of accuracy in identifying unique individuals. However, since external palm prints may change over time due to aging or environmental factors, Phase 2 introduces a more advanced biometric approach.
Phase 2 enhances identity verification by incorporating palm vein recognition, which requires a specialized infrared-enabled device connected to a smartphone. This method captures the internal vascular structure of the palm, which remains stable throughout an individual’s lifetime and is nearly impossible to replicate or forge. Studies, such as those conducted by Fujitsu, have demonstrated that palm vein recognition offers an exceptional false acceptance rate of less than 0.00008% and a false rejection rate of only 0.01%. By analyzing both palm prints and palm veins, the Humanity Protocol ensures an unparalleled level of biometric accuracy, creating a unique digital identity signature for every verified user.
More Information can be found here
Use Cases
Universal Basic Income (UBI): the protocol ensures equitable distribution by restricting payouts to wallets linked to ZK-verified humans, eliminating Sybil attacks that plague existing systems.
Enterprise DeFi: institutions can issue KYC-compliant credentials as VCs, allowing users to participate in regulated financial markets without relying on centralized custodians—enabling privacy-preserving compliance at scale.
DePIN: biometric-authenticated DIDs replace insecure Radio-frequency identification (RFID) cards, granting blockchain-verified access to shared resources like co-working spaces or electric vehicle networks.
Governance and airdrops: Ensuring one-person-one-vote mechanisms and Sybil-resistant “fairdrops,” restoring trust in decentralized decision-making.
Real-world: Notaries or governments can issue ownership VCs, enabling users to mint asset-backed tokens (e.g., real estate) without intermediaries. Cross-border credential portability addresses inefficiencies in education and employment, as migrants share tamper-proof diplomas or licenses globally via interoperable DIDs. Even sensitive sectors like healthcare benefit, as patients share anonymized medical data via ZKPs, enabling research without compromising privacy.
Sector Outlook
The Decentralized Identity (DID) landscape is evolving to address a broad spectrum of applications beyond the Web3 domain, emphasizing enhanced privacy and user control across various sectors. DIDs empower individuals to manage their personal information, ensuring secure and private digital interactions without reliance on centralized authorities.
In the financial services industry, DIDs streamline the Know Your Customer (KYC) process, allowing users to verify their identities efficiently while maintaining control over their data. This approach not only enhances user experience but also reduces operational costs for institutions.
In healthcare, DIDs facilitate secure management of medical records, enabling patients to share their health information seamlessly with authorized professionals. This ensures data accuracy and upholds patient privacy.
The concept of self-sovereign identity (SSI) is central to DIDs, granting individuals autonomy over their digital identities. SSI allows users to selectively disclose information, enhancing privacy and security in online interactions.
Unlike dystopian alternatives (e.g., Worldcoin’s iris scans), Humanity Protocol prioritizes privacy and accessibility. Its palm-scanning hardware and modular architecture enable seamless integration with DeFi, DePIN, and enterprise applications—bridging Web3’s trustless ethos with real-world compliance needs (e.g., KYC for institutional DeFi). By decentralizing identity verification, the protocol mitigates single points of failure while fostering applications like one-person-one-vote DAOs, RWA tokenization, and cross-chain credential portability.
Competitive Landscape
The decentralized identity (DID) landscape is rapidly evolving, with various protocols offering unique approaches to identity verification while balancing privacy, security, and decentralization.
Worldcoin, Humanode, Fractal ID, Iden3, and Humanity Protocol are among the key players in this space, each leveraging different technologies to establish trust and authenticity in the digital world.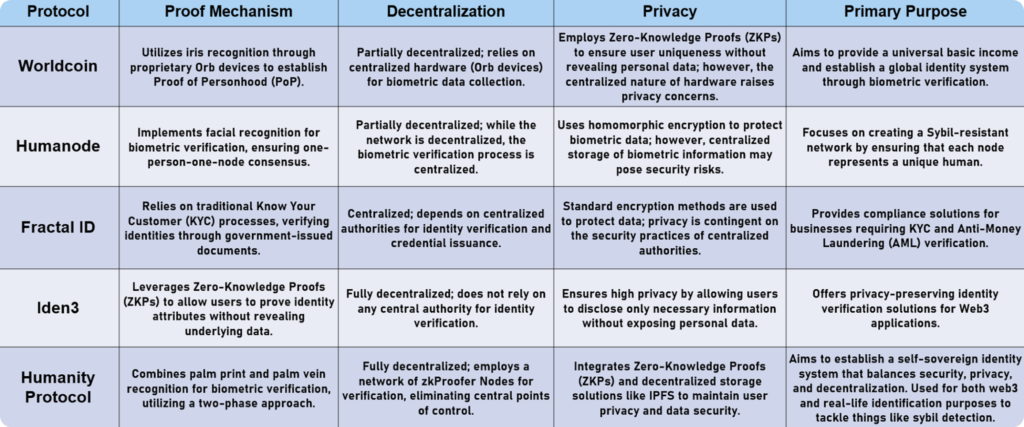
Potential Adoption
The demand for enhanced privacy and control over personal data has become a significant concern among consumers, leading to a growing market for data protection solutions. A survey highlighted that 53% of U.S. consumers feel they have little control over their online identity, and 34% report feeling overwhelmed about managing their privacy.
In response to these concerns, the data protection market is experiencing substantial growth. The global data protection market is projected to grow from US$61.525 billion in 2024 to US$115.204 billion by 2029, at a compound annual growth rate (CAGR) of 13.37%.
Humanity Protocol addresses the growing demand for enhanced privacy and control over personal data by offering a decentralized identity verification system that empowers individuals to manage their digital identities securely. For users, this means having complete ownership of their data, with the ability to decide what information to share and with whom. Service providers benefit from Humanity Protocol by gaining access to a secure and reliable method of verifying user identities without compromising user privacy.
Human ID can also be utilized across different services, eliminating the need to create and manage separate accounts. This interoperability not only simplifies the user experience but also promotes consistency and ease of access, as users can authenticate themselves seamlessly across participating platforms.
$H Token
Humanity Protocol ($H) is a multi-functional ERC-20 token designed to support a decentralized identity verification network. With a fixed supply of 10 billion tokens, the protocol aims to balance demand through identity attestation services, staking rewards, governance mechanisms, and partnerships with third-party applications.
Unlike inflationary token models, Humanity Protocol employs a structured incentive mechanism that enhances ecosystem participation without undermining token value.
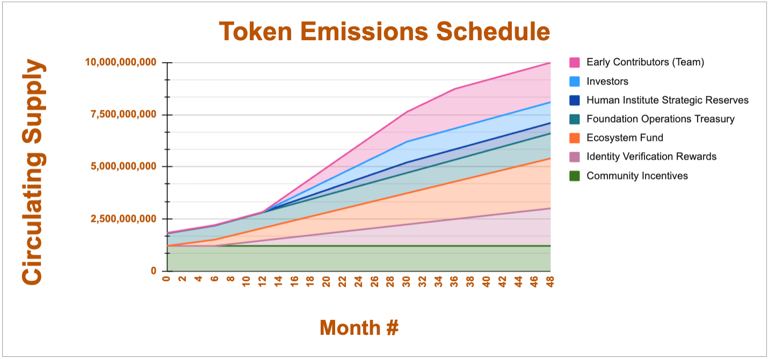
Token Allocation
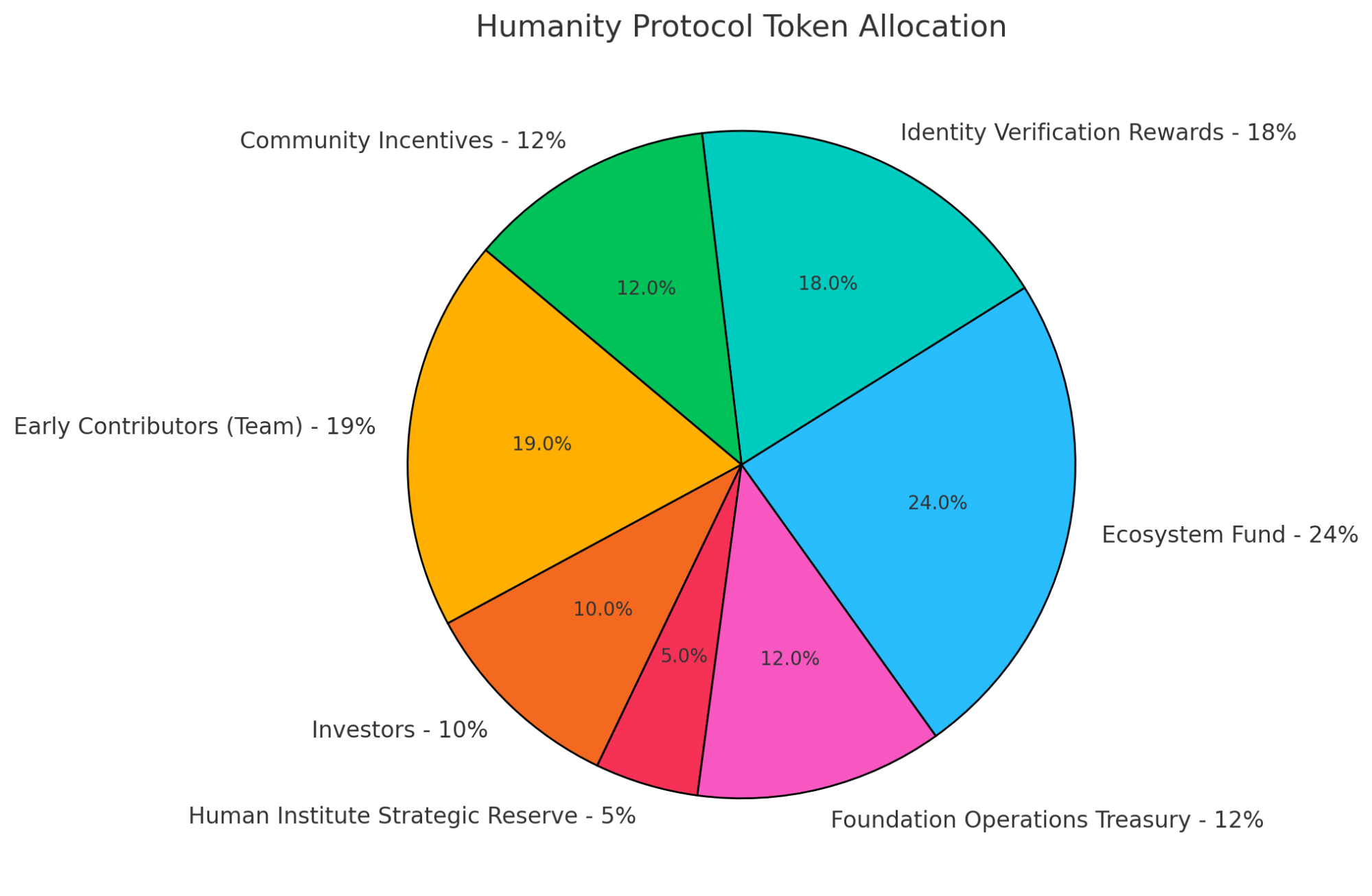
Total Supply: 10 Billion
- Early Contributors (Team) – 19%: Allocated to founding team members and early contributors who played a role in protocol development.
- Investors – 10%: Reserved for strategic investors who provided funding for ecosystem growth.
- Human Institute Strategic Reserve – 5%: Supports operational services and future strategic partnerships.
- Foundation Operations Treasury – 12%: Used for ecosystem liquidity, operational costs, and future initiatives aligned with Humanity Protocol’s mission.
- Ecosystem Fund – 24%: Dedicated to incentivizing partners, developers, and projects building on the protocol.
- Identity Verification Rewards – 18%: Forms the base incentive pool for zkProofer Node Operators, ensuring long-term participation in verification activities.
- Community Incentives – 12%: Supports user onboarding, airdrops, and reward programs to drive network adoption.
Stakeholders
The Humanity Protocol ecosystem is composed of several key stakeholders, each playing a distinct role in the network’s functionality and economic sustainability. These participants contribute to the protocol’s security, governance, and adoption through various mechanisms.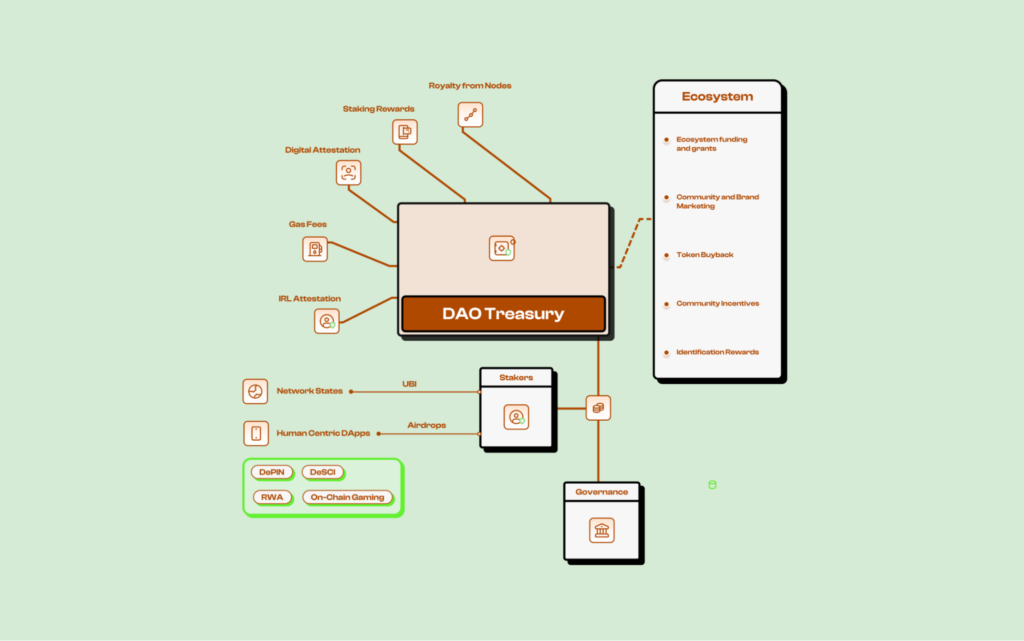 Primary Stakeholders:
Primary Stakeholders:
- End Users: Individuals who engage with the network by verifying their identity, participating in governance, and utilizing ecosystem applications. These users benefit from secure identity verification and may receive incentives for their engagement.
- Identity Validators: Participants who stake $H tokens to issue and verify identity credentials. Their role is crucial in maintaining network integrity, and they earn a share of verification fees as compensation.
- zkProofer Node Operators: Responsible for running verification proofs that validate credentials. These operators receive rewards in return for their computational efforts, which support the protocol’s trust architecture.
- Third-Party Applications: External platforms that integrate with the Humanity Protocol to utilize identity verification and attestation services. These applications contribute to network activity and may receive onboarding incentives for participation.
- Humanity Protocol Foundation: Manages various aspects of the protocol, including operational costs, partnerships, and community incentives. The foundation also plays a role in maintaining liquidity and supporting ecosystem development.
- Governance Participants: $H token holders who participate in governance by voting on key protocol decisions. Their involvement ensures decentralized decision-making and long-term network sustainability.
The interaction between these stakeholders establishes an interconnected ecosystem where each participant benefits from and contributes to the overall functionality of the Humanity Protocol. As adoption grows, the collective engagement of these groups is expected to drive network expansion and enhance the token’s utility.
Risks
Biometric Data Security and Privacy
End users verifying their identity on Humanity Protocol is the key risk of the platform. In order to undergo identity verification, users are required to provide sensitive biometric data, specifically palm scans. Despite the protocol’s implementation of privacy-preserving measures, such as zero-knowledge proofs and decentralized storage, there remains an inherent risk associated with the collection and handling of biometric information. Users must trust that their data is securely managed and protected against unauthorized access or potential breaches.
Building trust among potential users involves transparent communication about data handling practices, security protocols, and the tangible benefits of the system. Users need assurance that their biometric data is handled securely and that their privacy is preserved. Any perception of inadequate data protection or misuse of personal information could hinder user adoption and engagement.
Technological Dependence and Accessibility
The effectiveness of Humanity Protocol is contingent upon users’ access to compatible palm-scanning devices. This technological requirement may inadvertently exclude individuals without access to such devices, leading to potential accessibility issues and limiting the protocol’s inclusivity. Additionally, any technical malfunctions, hardware failures, or software vulnerabilities could impede users’ ability to verify their identities, thereby restricting access to services that depend on the protocol. Continuous technological support and infrastructure maintenance are essential to mitigate these risks.
Team
Humanity Protocol is developed by a team of seasoned entrepreneurs
Core Team:
- Terence Kwok (CEO): Seasoned entrepreneur who previously founded Hong Kong-based unicorn Tink Labs.
- Yat Siu (Director): Chairman and co-founder Animoca Brands
- Mario Nawfal (Director): Serial entrepreneur who has founded companies like International Blockchain Consulting Group and Froothie. Also runs one of the largest citizen journalists on X.
Project Investors
On 27 Jan 2025, Humanity Protocol secured a $20M funding round co-led by Pantera and Jump, raising at a FDV of $1.1B.
Other investors include Animoca, Shima, Hashed, Mechanism Capital, Cypher, and more.
FAQ
How does Humanity Protocol ensure my privacy?
The protocol employs zero-knowledge proofs and advanced encryption techniques to verify your identity without exposing personal information. Biometric data is securely stored and processed, maintaining user privacy and data integrity.
What is a Human ID, and how do I obtain one?
A Human ID is a unique identifier within the Humanity Protocol ecosystem, serving as your digital identity across various applications. To obtain one, you can reserve your Human ID by signing up through the testnet platform using methods like Email, Telegram, X, Discord, Google, or MetaMask.
How can I participate in the referral program?
After reserving your Human ID, you’ll receive a unique referral link. Sharing this link with friends and family allows you to earn rewards and airdrops once the testnet is fully rolled out. The more people you refer, the greater your potential rewards.
What incentives are available for stakers in Humanity Protocol?
While specific staking incentives have not been explicitly outlined, participants who engage in network activities, such as verification processes, may earn rewards in the form of protocol tokens.
What makes Humanity Protocol different from other decentralized identity solutions?
Humanity Protocol differentiates itself by using palm vein recognition instead of traditional biometric methods like iris scans (e.g., Worldcoin) or facial recognition (e.g., Humanode). It also integrates zero-knowledge proofs (ZKPs) and decentralized storage, ensuring privacy-preserving identity verification.
Does Humanity Protocol require KYC verification?
No, the protocol enables self-sovereign identity (SSI), meaning users do not need to rely on centralized KYC providers. Instead, they control their own credentials and selectively share them using ZKPs.
Where can I use my Humanity Protocol identity?
Humanity Protocol enables identity verification for various applications, including:
- DeFi (Decentralized Finance) for KYC-free lending and trading
- DAOs (Decentralized Autonomous Organizations) for one-person-one-vote governance
- Web3 gaming to prevent bot-driven economies
- Social networks to eliminate fake accounts
- Real-World Asset (RWA) tokenization for on-chain identity verification