Introduction
The blockchain industry has grown exponentially over the past few years, with hundreds of L1 chains, L2s and even L3 solutions unlocking unprecedented use cases but also inevitably fragmenting the on-chain scene. This fast-paced growth has introduced immense complexity for both users and protocols. The former must navigate this landscape with multiple wallets and bridged assets, while the latter must decide where to deploy its contracts based on available tooling, ecosystem partners, network effects of the underlying chain, and more.. According to DeFiLlama, over 50 chains now boast a total value locked (TVL) of more than $100 million, while L2BEAT reports nearly 100 operational L2s (including both rollups and validiums) and more launching soon—data testifying to vertical growth that shows no signs of slowing down. Yet, this rapid expansion has also deepened the barriers to adoption, resulting in both users and liquidity fragmentation.
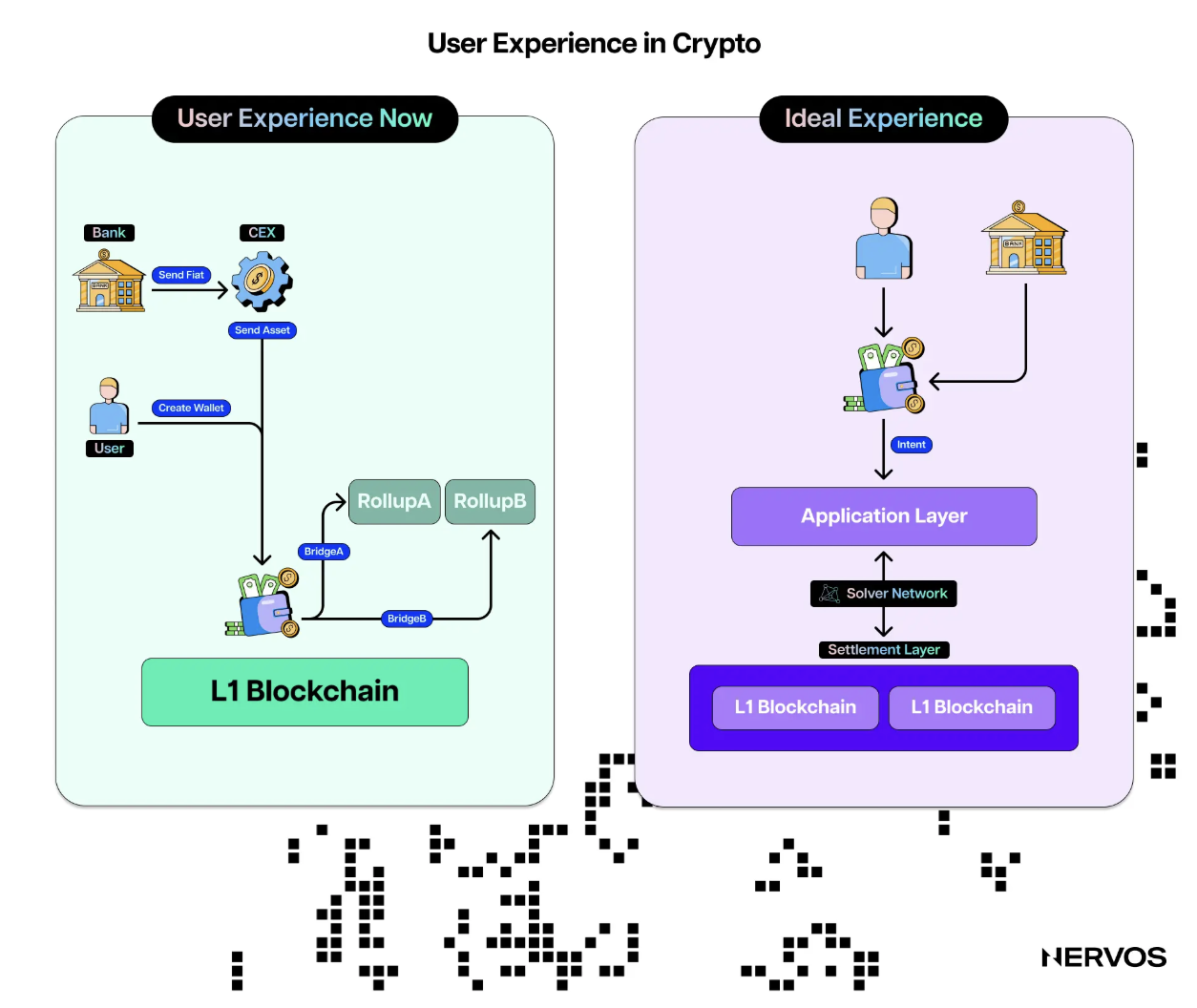
For users, interacting with decentralized applications (dApps) often feels like an obstacle course. Setting up a wallet, securing a seed phrase, bridging assets, and managing transactions across chains can be overwhelming. This fragmented user experience contrasts starkly with the seamless convenience of Web2 applications like Netflix or ChatGPT, which revolutionized their fields by prioritizing accessibility and usability.
As crypto matures and moves beyond early adopters to reach mainstream audiences, the need for standardization and unification has become increasingly evident. This shift has led to the emergence of “Chain Abstraction,” a movement aimed at creating a user experience in Web3 that matches the seamlessness of Web2. However, achieving this vision is complex and challenging.
Namely, Chain Abstraction, or ChA, aims to simplify this complexity, offering a unified interface that allows users to interact with multiple chains and dApps without grappling with the intricate backend at the infrastructure level. Much like email or internet protocols abstract away the technical layers of communication, Chain Abstraction distills the chain experience into intuitive actions. The goal is simple: make blockchain as easy to use as any mainstream Web2 app.
With Chain Abstraction, users can seamlessly move assets, execute transactions, and engage with dApps across multiple blockchain architectures, all without needing to know the intricacies of the underlying network. By integrating account, execution, and chain-level abstraction, this approach aims to eliminate pain points like bridging and fragmented interfaces. Users can now focus on the functionality of the applications they love, rather than the infrastructure behind them.
As chains and rollups increasingly move toward modular designs, Chain Abstraction represents the next step in blockchain evolution, paving the way for a more unified, accessible, and user-friendly decentralized internet.
This report explores the current fragmented state of the multi-chain ecosystem, the issues it poses, the solutions attempted so far, how to classify projects tackling this challenge, and how this radical simplification can reshape blockchain interactions for users.
Key Takeaways
Simplifying Blockchain Complexity. Users focus on actions and outcomes without worrying about gas fees, wallets, or cross-chain interactions—all of which entail technical complexities that hamper adoption.
Improving User Experience (UX). Provides seamless interfaces by abstracting technical details, making dApps more accessible—i.e. on-chain dApps should be as simple to use as any other online app.
Boosting Adoption. Reduces barriers to entry, making blockchain technology usable for non-crypto-native users and encouraging mass adoption (which has already embraced Web2 solutions).
Enabling Ecosystem Interoperability. Promotes smooth integration across multiple Layer 1 and Layer 2 solutions, removing the need for manual switching and thus lowering the related cognitive load.
Reducing Fragmentation. Chain Abstraction unifies decentralized ecosystems, mitigating tribalism between chains and allowing smoother cross-ecosystem interactions.
Understanding Chain Abstraction
Abstraction is a core concept in computer science. The aim is to reduce complexity by hiding unnecessary details from the user, enabling them to interact with higher-level operations without having to understand the intricate implementation details.
A useful real-world analogy for understanding the concept involved is the automobile: when you drive a car, you only need to understand how to operate the gas pedal, brake, and steering wheel but you don’t need to know how the internal combustion engine works, how the transmission changes gears, the details of the braking system, or how steering wheel movements translate to the car’s wheels. All this complexity is hidden from you through the abstraction of a simple interface (pedals, gear shift, and steering wheel) that makes driving accessible to people without requiring them to be automotive engineers.
Building on the general concept of abstraction, Chain Abstraction in blockchain technology involves designing systems where users or developers interact with blockchain functionalities without needing to understand the underlying chain-specific implementations (consensus mechanisms, Virtual Machines, networking protocols, storage systems, etc).
In other words, while the introduction of an increasing number of chains results in fragmentation of users and liquidity, chain abstraction unifies all of that through seamless unified interfaces. This simplifies user interactions across multiple networks and assets, thereby enhancing both user experience (UX) and developer productivity.
The Need for Chain Abstraction
Chain Abstraction aims to address several significant problems in the current multi-chain blockchain ecosystem:
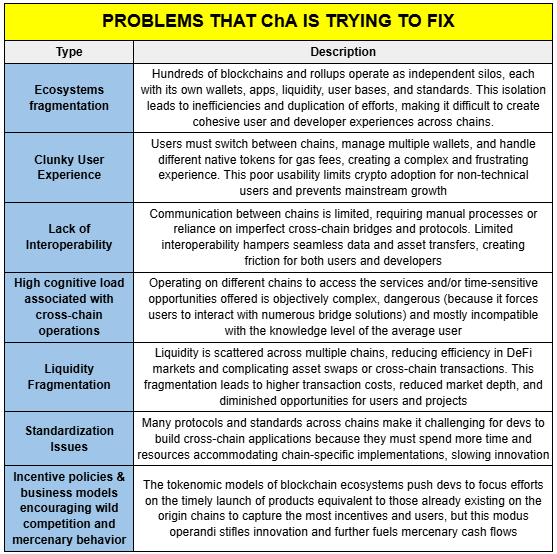
The Complexity of a Multi-Chain Paradigm
In the early days of blockchain, the ecosystem was simple. Bitcoin introduced the world to the revolutionary idea of a decentralized, censorship-resistant ledger, focused initially on payments. However, its open-source nature unleashed a wave of experimentation. Early projects like Namecoin, Dogecoin, and Litecoin explored new possibilities, setting the stage for broader innovation. The true turning point came with Ethereum, which expanded blockchain functionality with its Turing-complete design. By enabling developers to build decentralized applications (dApps) on a shared global ledger, Ethereum sparked an explosion of creativity, giving rise to stablecoins, decentralized finance (DeFi), gaming, and more.
Yet, Ethereum’s success soon became its bottleneck. The surge in user activity overwhelmed the network, leading to high transaction fees and long wait times. It became clear that general-purpose blockchains needed to scale to meet demand. This need for scalability brought two distinct approaches: enhancing Ethereum itself through layer 2 solutions (L2s) or creating entirely new chains optimized for performance.
L2 solutions like Arbitrum, Optimism, ZKSync, and Starknet emerged as a way to offload transactions from Ethereum while maintaining its security. While transactions would be executed outside of Ethereum mainnet, Ethereum would still be used for settlement. Hence, why execution could still be centralized on a L2 sequencer, the verification of such execution would remain permissionless and decentralized. To enable such a paradigm, rollups introduced different techniques, such as optimistic proofs and zero-knowledge proofs, unlocking scalability while maintaining the trustless properties of the base layer.
Simultaneously, alternative chains like Solana, Cosmos, and Near offered fresh L1 architecture designs that promised faster execution and unique features. Later entrants like Ton, Aptos and Sui followed suit, developing new blockchain stacks to compete in this evolving landscape. These efforts collectively created a fragmented ecosystem, with each chain operating as its own silo.
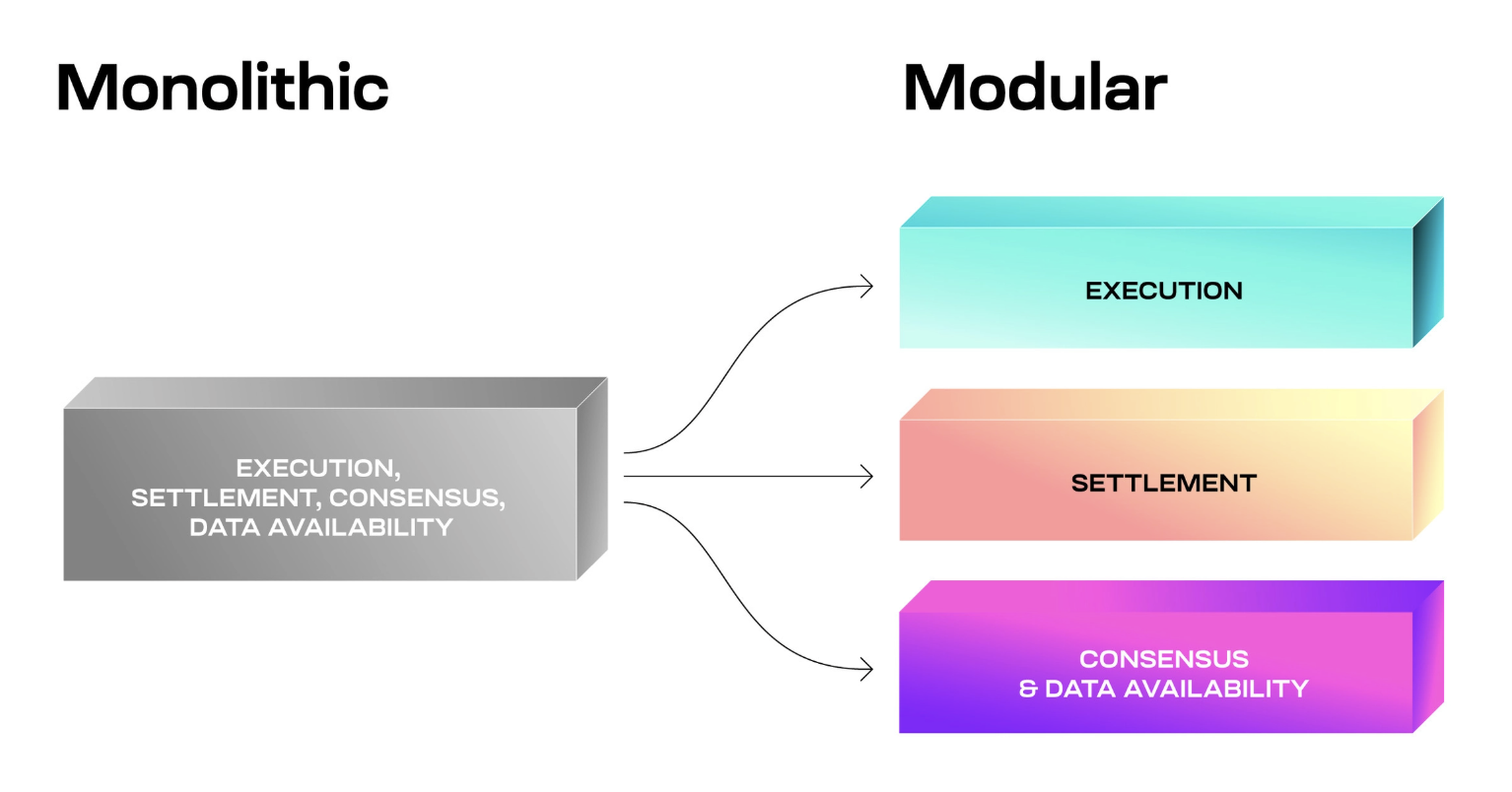
A key advancement that has heavily influenced the evolutionary path of the blockchain environment has been the introduction of modularity. Proposed by Mustafa Al-Bassam in his 2019 paper, “LazyLedger: A Distributed Data Availability Ledger with Client-Side Smart Contracts,” modularity involves separating key blockchain functions—such as consensus, data availability (DA), transaction settlement, and execution—into distinct layers. This shift away from monolithic designs enables specialization, improves scalability, and lowers the barriers to entry for new infrastructure projects.
The Multi-Chain Dilemma
The proliferation of new blockchains was driven not only by the need for scalability but also by competitive incentive structures. Each chain, seeking to attract developers and users, often introduces its own native token and incentivizes adoption through token rewards. Even though each design comes with its own tradeoffs, the second order effect is a competition for attracting developers and gaining mindshare by onboarding early adopters. Nonetheless, while some of these strategies can spur short-term growth, they also create a zero-sum competition among chains, where resources are spread thin and user bases are divided. Developers, in turn, are often forced to choose chains based on the profitability of these incentive campaigns rather than the intrinsic quality or technical merits of the underlying infrastructure. This misalignment contributes further to liquidity and user fragmentation.
Another driver for the surge of an increasing number of chains, mostly L2s and L3s, has been the commodification of blockchain infrastructure, primarily driven by Rollup-as-a-Service (RaaS) providers. In the past, creating a new chain required significant technical expertise and resources. Today, rollup-as-a-service platforms like Gelato, Conduit, or Caldera, to name a few, have dramatically lowered the barriers to entry, enabling even smaller teams to build their own blockchains in a few clicks. This ease of creation has led to an explosion of chains, each attempting to carve out its niche through technological differentiation, unique use cases, or community-focused strategies.
Additionally, having sovereignty over a dedicated blockchain allows projects to tailor their infrastructure, optimize performance, and enhance UX. This level of control enables developers to align every aspect of the chain—such as gas fees, consensus mechanisms, and tokenomics design—with the unique needs of their application and its users. From Fax to Swell via Uniswap and Aave, the strategic direction taken by protocols toward app-specific chains reflects a growing consensus: the benefits of owning an independent chain far outweigh the limitations of relying on general-purpose blockchains.

Appchains, essentially standalone blockchains, are designed to support a single or a set of functionalities. By dedicating all resources to a specific application or ecosystem, appchains provide better performance, predictability, and scalability compared to generalized networks. Projects can ensure consistent low fees, reduced latency, and improved transaction throughput, which are critical for use cases like trading, gaming, or social apps. Moreover, appchains empower teams to innovate freely, implementing custom economic models, governance systems, and incentivization strategies to align stakeholders and foster long-term growth.
However, this rapid growth has come at a cost: further fragmentation. Liquidity, the lifeblood of financial markets, is now spread thin across multiple chains. This not only reduces market efficiency but also complicates tasks like swapping assets, as liquidity pools are siloed within specific ecosystems. Beyond liquidity, the fragmentation extends to the composability of applications. On Ethereum, developers can seamlessly integrate protocols and assets, creating more complex and interconnected financial products. Across chains, this composability breaks down, limiting the ability to innovate and collaborate.
This division also affects users and communities. The tribal nature of chain ecosystems fosters loyalty to specific chains, often at the expense of interoperability. Developers face a dilemma when choosing where to build, as focusing on one chain excludes the user bases and features of others. For users, navigating this fragmented landscape is daunting. Simple tasks, like transferring funds between chains or purchasing NFTs, require navigating bridges, managing multiple wallets, and paying gas fees in various tokens. This clunky user experience is a significant barrier to broader adoption.
Despite these challenges, the multi-chain ecosystem is a testament to the creativity and resilience of the blockchain industry. It reflects a period of rapid experimentation and growth, akin to the early days of the internet. Yet, as the technology matures, the focus is shifting from creating new chains to finding ways to connect them seamlessly. Concepts like Chain Abstraction aim to address the complexity, making blockchain ecosystems interoperable and accessible to a wider audience.
As we look ahead, the goal is clear: to turn this fragmented landscape into a cohesive and user-friendly system. By simplifying interactions, consolidating liquidity, and enabling true interoperability, the industry can move closer to realizing the full potential of blockchain technology. The journey is far from over, but the vision of a unified, scalable, and accessible Web3 is beginning to take shape.
Classification Criteria
As is clear from the previous paragraphs, the topic of Chain Abstraction is extremely broad and encompasses many different layers. Indeed, the concept expresses an outcome to be pursued industry-wide, and not merely a protocol or a vertical primitive to be implemented. To fully understand how the entire background process works, we first need to look at each individual level involved.
Drawing insights from the CAKE framework, developed by Frontier Tech, and enriching it with the excellent educational contributions produced by the crypto community over the past year, the following levels can be identified:
- Application.
- Permission.
- Solving.
- Settlement.
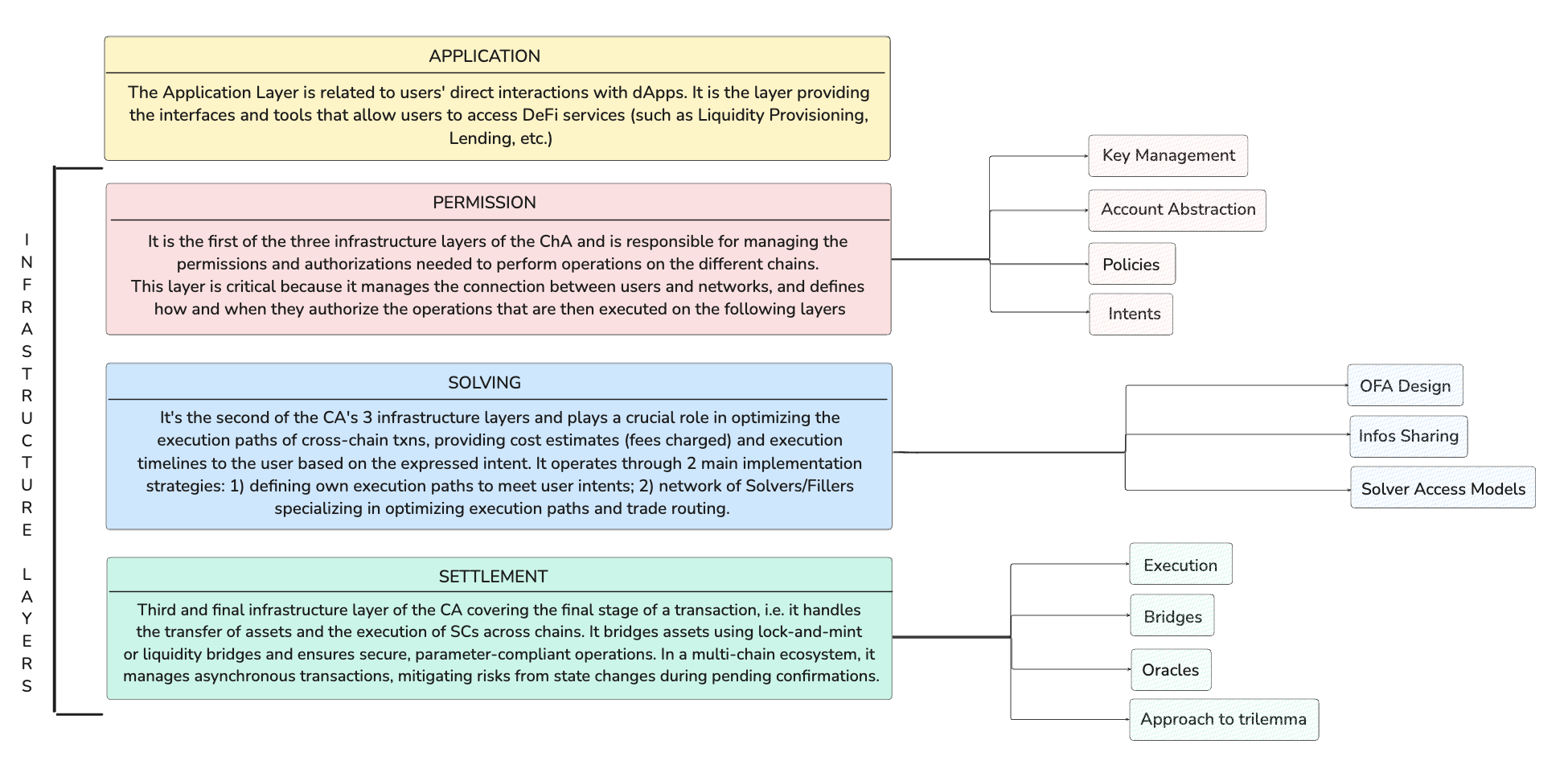
The Application Layer
The Application Layer acts as the primary gateway, handling the flow of user inputs and translating them into actionable intents for the relative chain. At the same time, it shows outputs in a clear and intuitive manner, ensuring that users can easily understand and interact with complex chain operations.
This layer includes all the interfaces and tools working seamlessly together to facilitate user engagement by simplifying intricate blockchain functionalities into accessible, everyday actions. Through this, users can initiate operations, such as creating transactions or querying data, without needing to navigate the complexities of the underlying systems.
The Permission Layer
The Permission Layer serves as a background interface between users and the blockchain ecosystem, managing account abstraction and transaction authorization while ensuring a seamless user experience. This layer simplifies complex blockchain interactions by abstracting the technical details away from end-users, allowing them to focus on outcomes rather than individual transaction specifics.
Namely, this level is responsible for connecting wallets and dApps, managing private keys, signing transactions (and thus expressing intents), and coordinating/managing the transaction flow over multiple chains.
At its core, the Permission Layer enables users to interact with dApps through wallet connections, facilitating intents such as transferring assets, staking, or executing swaps. Intents, in this context, represent the high-level outcomes users wish to achieve, rather than the granular steps required to execute them. For instance, instead of specifying every detail of a swap transaction, users can define their desired result, such as maximizing returns or buying at specific price levels, and the Permission Layer determines the optimal route to achieve it.
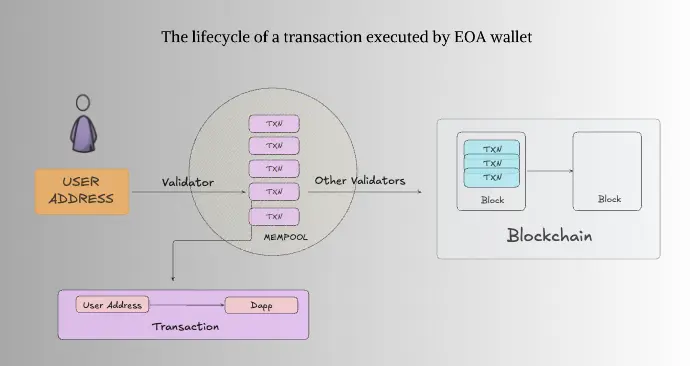
To better understand this layer, it is worth noting how it draws inspiration from the core principles that shaped Account Abstraction (AAs). Traditionally, Web3 users relied on Externally Owned Accounts (EOAs), such as those used by wallets like Metamask, Rabby or Phantom. While straightforward, EOAs are limited in functionality, tied to a single key pair, and prone to irrevocable loss if private keys are compromised. Furthermore, EOAs could only perform basic operations like signing transactions and interacting with smart contracts.
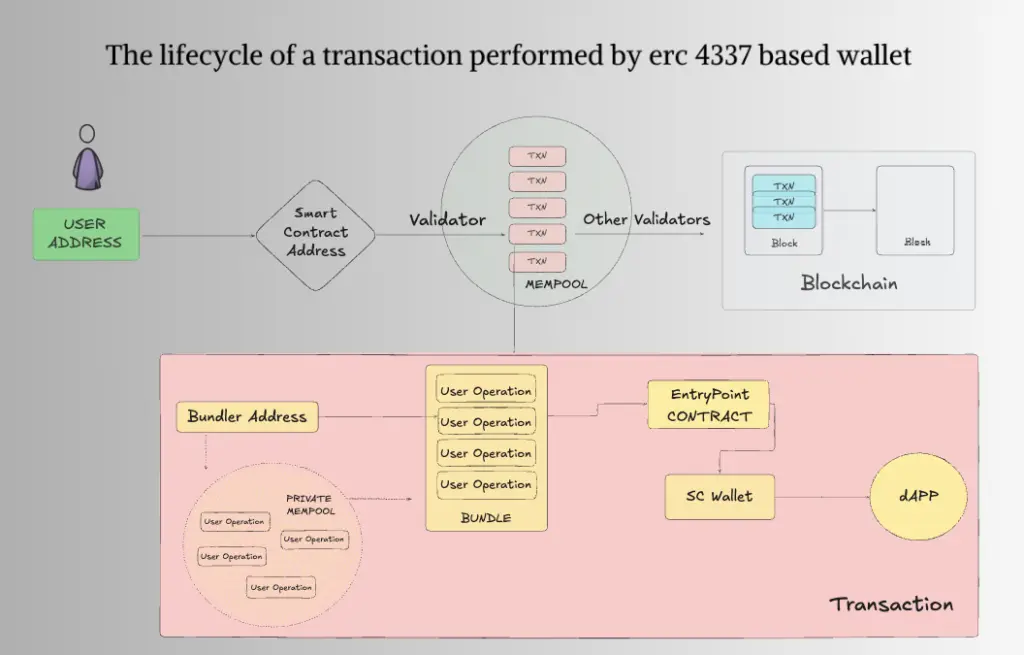
With advancements like Ethereum’s ERC-4337 standard, Smart Contract Accounts (SCA) have become a viable alternative. These accounts operate through custom logic encoded in smart contracts, allowing for features such as multi-signature approvals, programmable transaction rules, gas sponsorship, and enhanced security measures. This flexibility transforms the user experience, making it adaptable to individual preferences and use cases: from gas abstraction to recurring payments to session keys via transaction bundling, imagination is the limit.
The benefits provided by Account Abstraction are truly countless and span a wide range of use cases and functionalities, significantly improving user experience, security, and operational efficiency; they can be generally summarized as follows:
- Enhanced security features. Signature Abstraction provides the ability to define custom transaction authorization rules, such as transaction limits, multi-party approvals, social recovery mechanisms for lost keys, freezing of funds to prevent unauthorized access, and Two-Factor Authentication (passwords, biometric data, or physical devices).
- Operational efficiency. AA enables batching multiple operations, such as approving and executing a transaction, into a single atomic transaction. This reduces processing time, improves the user experience, and minimizes the need for repeated confirmations. It also enables multiple authorized signers with specific permissions, setting different spending limits for different signers (e.g., smaller transactions can be handled by less secure devices, while larger transactions require hardware wallets).
- Financial flexibility. Fee abstraction allows users to pay gas fees using any token, such as $USDC or $USDT, instead of the native chain token. This feature is complemented by the use of “Paymaster” contracts, which enable developers or sponsors to cover transaction costs on behalf of users, paving the way for gasless transactions on the user side. Flexible gas policies provide developers with the ability to create tailored fee structures, accommodating a wide range of application-specific requirements and simplifying the overall UX.
Recently introduced by One Balance (a product incubated by Frontier Research), a new type of accounts called Credible Accounts enhance existing formats like external accounts, smart accounts, and stateful accounts. They allow for credible commitments, i.e. trustworthy resource allocations, without relying on global consensus. This is key to creating a seamless, multi-chain user experience.
At the heart of Credible Accounts is the Credible Stack, an interoperability framework that deals with the distribution of credible accounts based on community-defined standards; it includes the tools and protocols needed to manage Resource Locks and ensure smooth interoperability between chains. Resource Locks, issued by Credible Accounts, are conditional requests that solvers execute on target chains, bypassing the need for all chains to synchronize.
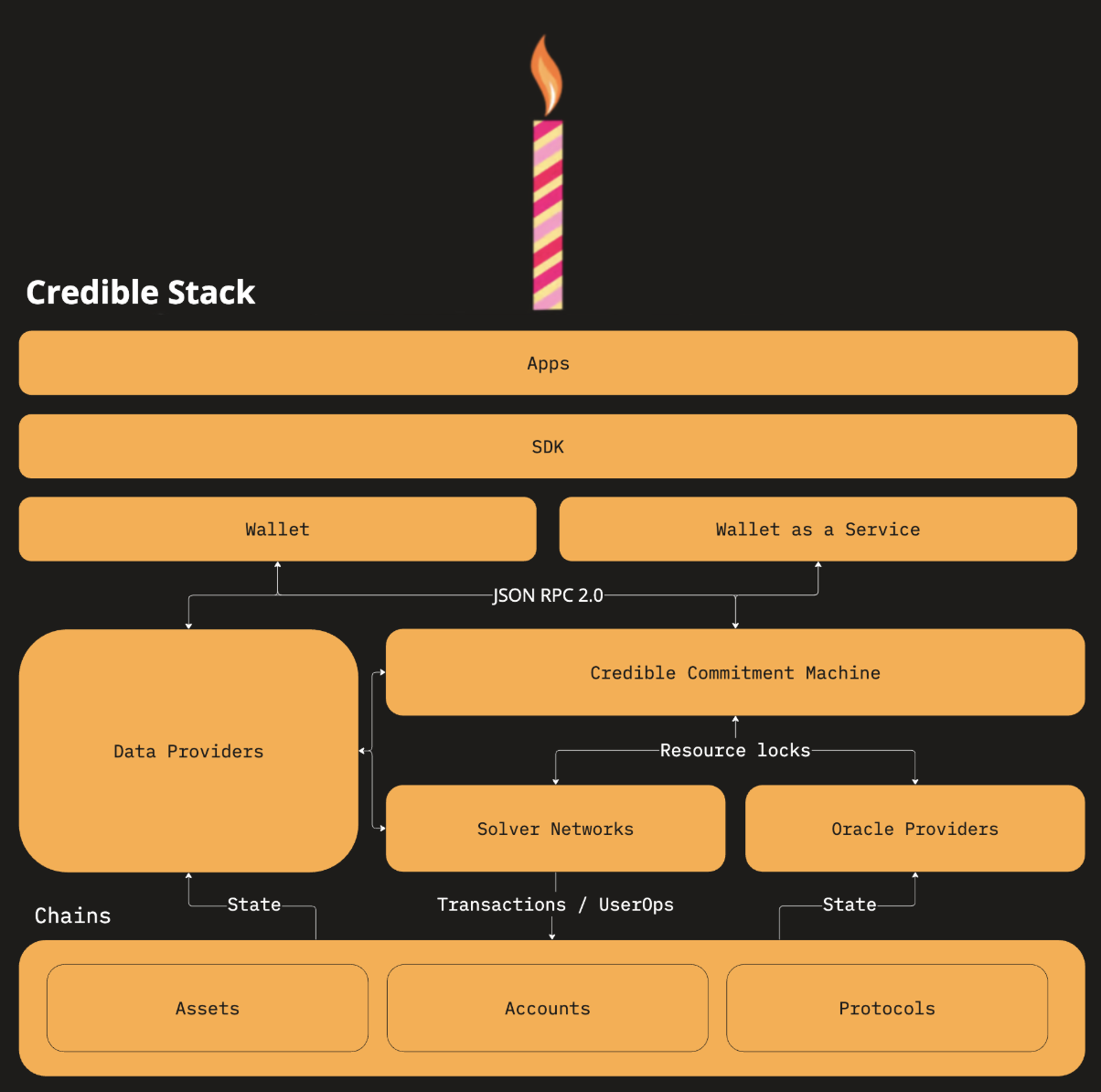
Managing multi-chain transactions is probably the last critical function of the Permission Layer. A single transaction often involves several sub-transactions across different blockchain networks, each with its own time-sensitive fees and nonce requirements. The execution of these sub-transactions must occur in a precise order to ensure correctness and reliability. The coordination and settlement of such complex interactions present a unique design challenge for the Permission Layer, demanding robust mechanisms to synchronize activities across multiple chains seamlessly.
The Solving Layer
The Solving Layer within a Chain Abstraction Framework (CAF) is responsible for translating user intents into actionable transactions, managing their execution across chains and dApps. Unlike traditional transaction-based paradigms, where users define each step, the solving layer operates under an intent-based model, where users specify desired outcomes, leaving execution complexities to qualified third parties, i.e. solvers. For example, instead of detailing the parameters for swapping tokens on a specific platform, a user might simply request the best rate for a swap, and the solving layer takes over from there.
What solvers are and what they do
Solvers are off-chain agents or entities responsible for interpreting user intents and executing them across chains and dApps. They basically act as intermediaries that manage the complexities of cross-chain transaction flow, ensuring efficient, accurate, and seamless fulfillment of user-defined outcomes.
The solver-based model is currently the most efficient because:
- It is based on competition among qualified entities, which stimulates better price discovery.
- It delegates the execution of intent orders to specialized parties, transferring the MEV risk to the solver.
- Auction designs are extremely flexible and can easily adapt to the needs of any protocol.
At the solver level, key functions include:
- Intent Interpretation. Solvers take high-level user intents, such as “swap 1000 $USDT for the maximum amount of $ETH at the lowest cost,” and translate them into executable actions. This eliminates the need for users to specify the intricate details of execution paths, such as the exact dApp, route, or chain to use.
- Route Optimization. Solvers identify the most efficient path across multiple chains and dApps to achieve the user’s desired outcome. This involves selecting the best protocols, liquidity pools, and execution strategies—managing their own inventory of assets across chains.
- Fee Estimation. Solvers calculate the total cost of fulfilling the intent, including gas fees and any associated charges, providing users with clear and predictable costs.
- Execution Speed Estimation. Solves predict the time required for the transaction to settle, helping users understand the performance trade-offs.
- Transaction Execution. Solvers perform the actual transaction on behalf of the user, managing asynchronous cross-chain operations and ensuring that the correct sequence of actions is executed for the desired result.
The role played by solvers is, therefore, crucial, as are the choices made by teams on the auction infrastructure design.
Managing Extractable Value (EV)
The solving layer deals with 2 key types of extractable value (EV) arising from user intents: EV_ordering and EV_signal. EV_ordering is closely tied to the blockchain’s internal mechanics and can be defined as the value obtained from executing user orders. EV_signal, on the other hand, is the value that can be exploited by observing an order before it gets executed, such as in cases of front-running. Competition among solvers often hinges on how these EV dynamics are managed. Public systems, like mempools, are especially prone to value leakage because they openly reveal both EV types. Private mempools, now supported by technologies like Multi-Party Computation (MPC) and Trusted Execution Environments (TEEs), aim to mitigate these leaks by encrypting user intents until the point of execution. However, even private mempools can’t entirely prevent the race to exploit EV_signal, as some opportunities for value capture may still persist.
Approaches to Information Sharing
The CAF has to decide how much information to reveal to solvers and this is another crucial aspect because the way user intents are shared with these qualified third parties greatly affects the overall efficiency and security. There are essentially 3 kinds of approaches
- Public mempools broadcast user intents openly, leading to high levels of EV leakage.
- Partial sharing limits the exposed information but may reduce price optimization and lead to latency-related inefficiencies.
- Private mempools offer greater confidentiality by restricting information to secure environments, but even they face challenges, such as latency races for fresh data once blocks are confirmed.
Solver Access Models
The framework also defines how solvers participate in the auction to execute intents:
- Open Access. Allows unrestricted participation, similar to public mempools, but risks value leakage.
- Gated Access. Solvers are selectively permitted, often based on whitelists, reputations, or fees, striking a balance between openness and security. This approach is used by platforms like 1inch, CowSwap, and Uniswap X.
- Exclusive Access. Limits participation to a single solver per period, eliminating competition and potential front-running but restricting price improvements.
The Settlement Layer
The Settlement Layer is the last critical component within a Chain Abstraction Stack, ensuring the correctness and immutability of transactions while updating the blockchain’s state. It facilitates the execution of signed transactions, but complexities arise in cross-chain operations, where asynchronous processes and changing states on target chains can lead to failures (potentially able to halt all related transactions). Key considerations in the Settlement Layer include security, confirmation time, and execution guarantees.
Cross-chain Infrastructure
For the reasons above, choosing and managing oracle and bridging solutions proves to be crucial to the success of any ChA Framework, with the awareness that every project needs to reach a trade-off between execution guarantee, low fees and execution speed.
Cross-Chain Operations and Oracles
Cross-chain transactions require intermediaries like oracles to transfer information between blockchains with different states and consensus mechanisms. Oracles act as relays, verifying actions such as locking funds on one chain and minting tokens on another. Their performance depends on the speed of the slower chain, as they must wait for sufficient confirmations to avoid risks like reorganization (reorg) attacks.
Oracles are categorized as:
- Out-of-Protocol Oracles, which rely on external validators to transfer information. Examples include LayerZero, Wormhole, Chainlink, and Axelar.
- In-Protocol Oracles, integrated into the consensus mechanisms of specific ecosystems, such as Cosmos’ IBC or Optimism’s Superchain, which use native validators to transfer data within the ecosystem.
- Shared Sequencers, still in development, bundle transactions across chains and aim to achieve atomic cross-chain execution by conditioning subsequent transactions on the success of earlier ones.
Bridging Tokens
In a multi-chain environment, users must transfer token balances between networks for cross-chain operations. Two main types of token bridges handle this:
- Lock and Mint Bridges, such as Wrapped BTC, Polygon PoS bridge and StarkGate, which lock tokens on the origin chain and mint corresponding tokens (e.g., wrapped tokens like USDC.e) on the target chain. These bridges require smaller capital to operate but demand significant investment for secure transfer of locking information.
- Liquidity Bridges, like Stargate and Synapse, which utilize liquidity pools on both chains to convert tokens. While they have higher initial costs, they are less reliant on strict security guarantees since only the liquidity pool is at risk during a breach.
- Intent-based bridges, such as Across and Everclear, a type of cross-chain protocol designed to facilitate efficient, user-friendly, and fast transactions by focusing on the user’s desired outcome, or “intent”. Each project in this category has always 3 key elements:
- a bridging contract;
- a Solver network;
- a native or third-party cross chain messaging/oracle system.
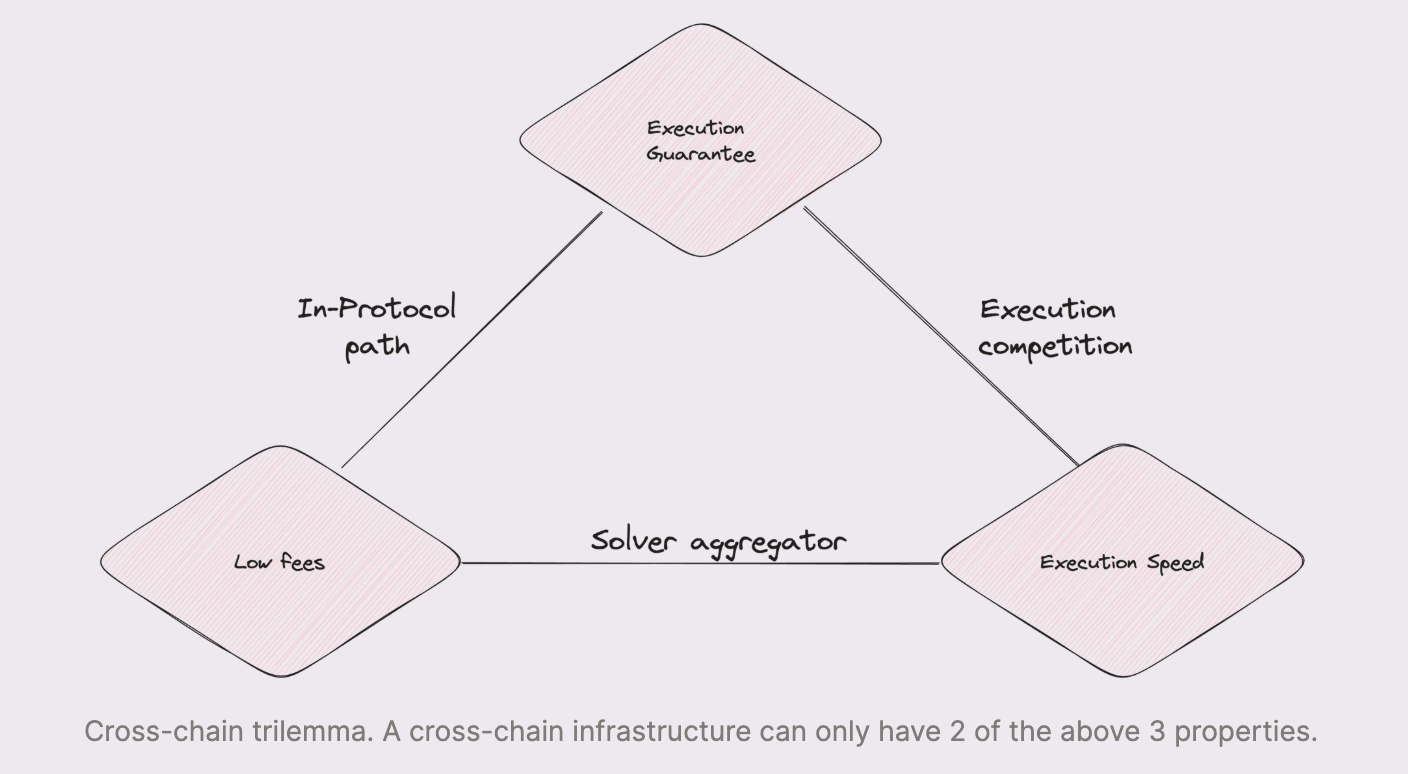
Cross-Chain Trilemma
The Settlement Layer faces a trade-off between three key properties in cross-chain operations: execution guarantee, low fees, and execution speed. This “cross-chain trilemma” forces frameworks to prioritize two at the expense of the third:
- In-protocol paths prioritize security and lower costs but sacrifice speed due to reorg risk management.
- Solver aggregation identifies the cheapest and fastest path for fulfilling a user’s intent but can lead to adverse selection and occasional failures.
- Execution competition among solvers increases fees as competition focuses on securing execution rights rather than optimizing for cost or efficiency.
Tradeoffs and Security Concerns
Chain abstraction envisions a blockchain ecosystem where users and developers experience seamless interaction, devoid of technical complexities. While this vision aims to unify the fragmented blockchain landscape, it introduces tradeoffs and challenges that must be addressed to balance efficiency, security, and inclusivity.
Tradeoffs on the UX side
Achieving frictionless user experiences necessitates significant advancements, but these improvements come with inherent compromises. For instance, ensuring low latency and high transaction throughput demands next-generation virtual machines, horizontal scaling, and optimized consensus algorithms. However, these technologies require substantial infrastructure upgrades and may introduce new vulnerabilities or operational complexities.
Similarly, universal gas standards, enabling transactions without user concern for gas tokens or fees, rely on chain-agnostic solutions or subsidized gas models. While these advancements enhance usability, they may lead to economic inefficiencies or over-reliance on protocol-level subsidies, which could strain chain sustainability.
Liquidity and Cross-Chain Concerns
One of the most pressing challenges in chain abstraction is liquidity fragmentation. Users often face high slippage, unreliable bridging, and decreased incentives to engage with DeFi protocols due to liquidity imbalances. Proposed solutions like liquidity hubs aim to centralize resources, but they risk introducing central points of failure, reduced decentralization, or market manipulation risks. Balancing liquidity centralization with decentralization principles still remains a critical challenge.
Additionally, encrypted activities and protection from toxic Maximum Extractable Value (MEV) are essential for preserving user privacy and trust. Implementing such features requires encryption standards akin to HTTPS, but this could increase computational overhead and delay adoption due to technical and regulatory hurdles.
Developer-Centric Challenges
From the developer’s perspective, chain abstraction demands unified execution environments and more reliable code compilers. While multi-VM and blended VM ecosystems allow developers to work in their preferred programming languages, these systems require complex engineering efforts. Building reliable compilers to support multiple programming languages and translate them into machine-readable formats is both resource-intensive and prone to operational bugs. Delays or errors in compiler development could slow the adoption of unified environments, perpetuating fragmentation in the developer experience.
Broader Systemic Risks
The transition toward chain abstraction also raises systemic concerns. Bridging networks for cross-chain operations increase the attack surface for exploits, as seen with previous security breaches in lock-and-mint and liquidity bridges. While enhancing these systems could mitigate risks, the high costs of implementation and the potential for failure remain significant concerns.
Furthermore, the pursuit of a seamless, abstracted blockchain experience may inadvertently compromise decentralization. Reliance on shared sequencers or centralized orchestration mechanisms could lead to concentration of power, undermining the core ethos of blockchain technology.
Key Players Taking the Lead
As we have seen, the topic of Chain Abstraction is extremely broad, as it actually embraces all possible infrastructure layers and involves different actors/entities in the abstraction process.
While the CAKE Framework is the main source of information on the technical level, in order to understand which projects are working on which steps/aspects of the ChA, we need to refer to an easier and more intuitive classification criterion (taking a leaf out of the Multi Layer Framework developed by Particle Network), which divides ChA approaches into two main groups: comprehensive solutions, and component solutions, each further divided into distinct sub-categories.
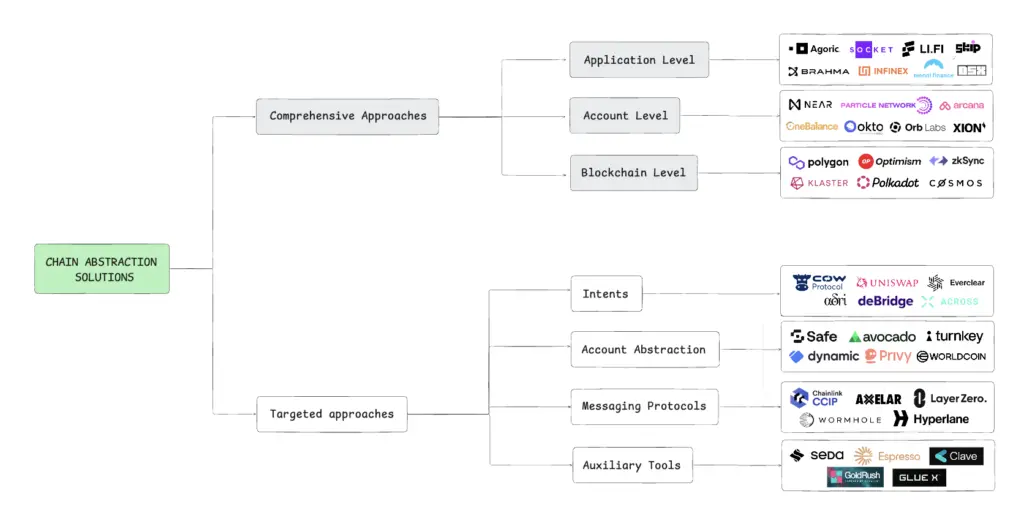
Comprehensive Solutions aim to provide a full-stack approach to chain abstraction. These solutions address multiple friction points in the user experience, functioning as an all-encompassing framework. They are analogous to monolithic blockchains in that they offer a seamless and unified experience, abstracting the complexity of underlying chains almost entirely from the user.
Component Solutions focus on solving specific, isolated problems within the broader context of chain abstraction. These solutions act as building blocks that contribute to the overall ecosystem but do not attempt to cover all aspects of abstraction. They are modular and typically designed to integrate with other tools or frameworks to collectively achieve chain abstraction.
Conclusion
Chain abstraction marks a pivotal step in the evolution of blockchain technology, aiming to simplify user interactions within a fragmented, multi-chain ecosystem. By eliminating technical barriers and limiting cognitive burdens, it fosters seamless cross-chain operations, reduces friction, and enhances accessibility for both users and developers.
As blockchain technology matures, chain abstraction offers a path toward standardization and interoperability, enabling a cohesive and user-friendly decentralized internet. While challenges such as liquidity fragmentation, interoperability, and user experience remain, the ongoing research and collaboration in this space signal a promising future for blockchain adoption and usability.
References
“Particle Network: The Chain Abstraction Layer” (2024), published by Shoal Research on its substack official page. Link
“Clearing the Path to Chain Abstraction” (2024), published on Substack by Modular Media on its official page. Link
“Chain Abstraction: Simplifying Interaction in The Fragmented Crypto World” (2024), published by Yugi AI on its Substack page. Link
“The Rise of Chain Abstraction” (2024), published by Paul Veradittakit (Panthera Capital) on his Substack page. Link
“Abstracting Chains” (2024), published by Shlok Khemani (Decentralised.co) on Decentralised.co’s Substack page. Link
“The 0-1 of Chain Abstraction” (2024), Shoal Research, published on Substack. Link
“Chain Abstraction Landscape” (2024), ASXN Digital Asset Research firm, published on Substack. Link
“Aggregated Blockchains”, Brendan Farmer, published on Mirror. Link
“Chain Abstraction – The Ultimate User Experience?”, 0xNairolf, published on Substack. Link
“The CAKE Framework”, Frontier Research (Ankit Chiplunkar and Stephane Gosselin). Link
Particle Network official blog. Link
“Solvers: The Backbone of Intent-Based Transactions” (2024), published on Substack by Modula Media on its official page. Link
“Intents and Chain Abstraction 101” (2024), published by Li.Fi in the “knowledge hub” section of its website. Link
“Blockchain bridges and their classification” (2022), published by Li.Fi within its knowledge hub. Link
Disclosures
Alea Research is engaged in commercial relationships with some of the projects mentioned, but this report is not part of any agreement with the clients.
Members of the Alea Research team, including those directly involved in the analysis above, may have positions in the tokens discussed.
This content is provided for educational purposes only and does not constitute financial or investment advice. You should do your own research and only invest what you can afford to lose. Alea is a research platform and not an investment or financial advisor.

