Introduction
The adoption of blockchains hinges on their ability to balance the tradeoffs between security and functionality—a push and pull between Turing-completeness and key properties such as censorship-resistance and permissionlessness. Bitcoin is the ultimate example of this, focusing on security and decentralization while sacrificing flexibility. This focus has made Bitcoin the most secure blockchain, but it also limits what can be built on top of it.
However, as blockchains evolve and start supporting an increasing number of use cases built on top, new solutions are emerging to expand Bitcoin’s capabilities. The advent of Ordinals and popularity of token standards like BRC20s or Runes has culminated in the proliferation of multiple Bitcoin L2s and sidechains. They add extra utility for $BTC by allowing its use across DeFi without compromising Bitcoin’s ironclad security.
This report delves into these trade-offs, exploring how Bitlayer and other Layer 2 solutions are navigating the complexities of enhancing Bitcoin’s functionality without compromising its foundational principles.
Key Takeaways
- Security vs. Functionality: Bitcoin’s design prioritizes security and decentralization over Turing-completeness, limiting its native functionality but ensuring its role as the most secure blockchain and valuable digital asset.
- Layer 2 Solutions: Bitcoin L2 solutions—like state channels, sidechains, and rollups—aim to boost Bitcoin’s scalability and functionality, each offering a unique mix of benefits and drawbacks.
- Bitlayer’s value proposition: Bitlayer integrates BitVM and other technologies to deliver Bitcoin-equivalent security while achieving Turing completeness, enabling developers to build complex dApps and unlock new use cases for $BTC, all within a 100% EVM compatible framework.
- Sector Outlook: Since its V1 mainnet launch in April 2024, Bitlayer has seen significant adoption across various metrics, including TVL, unique addresses, transaction volume, and ecosystem growth. This rapid growth underscores the strong interest from users and developers, as well as the platform’s potential for further expansion.
Background
This section will lay the foundation by introducing a few key concepts. First, we’ll define what a Turing-complete system is and explore the use cases it enables within the blockchain context. Next, we’ll discuss the security risks associated with Turing-complete systems and explain why the Bitcoin blockchain was deliberately designed to not beTuring-complete. Finally, we’ll introduce the concept of Bitcoin Layers, which aim to address the growing interest among market participants for new use cases for $BTC. Unlike L2s in other ecosystems like Ethereum, L2s in Bitcoin do not provide scalability benefits, but rather function as extensions of the base layer to enable additional functionality, such as cheaper payments or smart contract programmability. We’ll also clarify how Bitcoin Layers 2 differs from Ethereum Layers 2 and identify the ideal key properties and features of a Bitcoin Layer 2 solution.
Turing completeness: what does it mean?
The idea of the Turing machine was conceived about 88 years ago, in 1936, by an English computer-scientist named Alan M. Turing. The Turing machine is a theoretical, abstract idea which can simulate any algorithm that can be logically constructed. This means that a Turing machine can solve any problem if it can be coded out. It doesn’t guarantee how much time it will take to solve the problem, but it is certain that it will solve the problem. So it can take a second, a minute, a lifetime, or an entire generation to solve a problem.
“Turing completeness” is a property used to describe programming languages that can be used to simulate a Turing machine: “A programming language that is Turing complete is theoretically capable of expressing all tasks accomplishable by computers; nearly all programming languages are Turing complete if the limitations of finite memory are ignored.”(Wikipedia, Turing Machine). Today, most of the programming languages – C++, Java, JavaScript, Solidity, Pascal, … – are defined as Turing complete, at least in a theoretical sense.
In the context of blockchains, the most well-known example of a smart contract machine which can be defined as theoretically “Turing complete” is the Ethereum Virtual Machine (EVM). The EVM, through Solidity, its programming language, enables developers to build any application logic that they desire. In order to do so, such smart contracts require global accessibility and persistent storage for their state and code. Above we used the expression “theoretically Turing complete”, as computations on Ethereum are subject to gas costs and block gas limits, thus preventing it to be Turing complete in a strict sense. However, for the purpose of this report we will use the term “Turing complete” to identify chains that allow developers to write fully-expressive smart contracts to build any application logic they can think of.
The Bitcoin blockchain, however, does not allow for arbitrary contract publishing and storing complex contract state and logic, thus it is not considered “Turing complete”.
Security Risk of Turing-completeness
Turing-completeness is a double-edged sword. The flexibility it offers also introduces security risks, as complex smart contracts can be exploited if they contain bugs or vulnerabilities. The infamous DAO attack on Ethereum in 2016 is a prime example. These risks derive from the flexibility developers have when programming smart contracts, thus a higher chance of introducing bugs and logics that can be exploited by malicious actors. As of today, multiple attack vectors have been exploited (see for example here and here) in DeFi applications that exposed millions of dollars at risk on-chain.
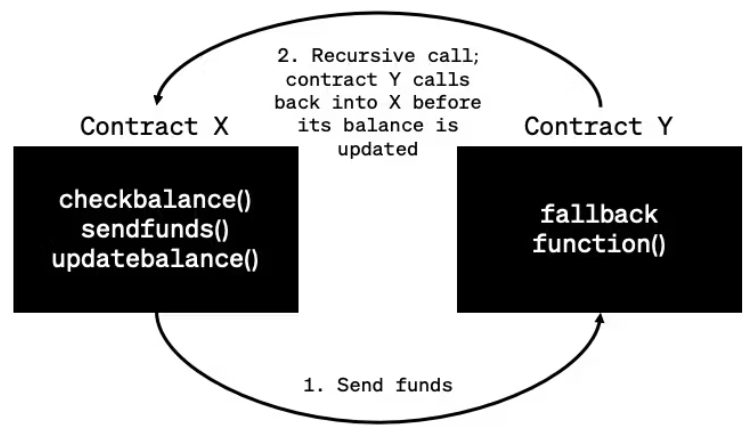
One of the first major exploits that even led to a fork of the original Ethereum chain was the DAO attack in 2016. A so-called re-entrancy attack allowed a hacker to drain 3.6M $ETH from the DAO smart contract, resulting in the Ethereum community hard-forking the entire network to restore their preferred version of history. The attacker was able to “ask” the smart contract (DAO) to give the $ETH back multiple times before the smart contract could update its balance. Two main issues made this possible: the fact that when the DAO smart contract was created the coders did not take into account the possibility of a recursive call, and the fact that the smart contract first sent the $ETH funds and then updated the internal token balance. It’s important to understand that this bug did not come from Ethereum itself, but from this one application that was built on Ethereum.
Figure 1: Single-function reentrancy attack scenario
Source: CryptoMarketPool
Over the years, the focus on smart contract security and the expertise of blockchain developers have greatly improved. Today, most DeFi applications conduct multiple security audits before deploying code in production. However, the number and variety of attacks and exploits have also risen, leading to millions of dollars in losses for numerous dApps, as confirmed by the long list of crypto hacks and exploits of 2024, all due to vulnerabilities in smart contracts. For a full list of historical attacks, you can have a look at DefiLlama’s directory.
Bitcoin: intentionally designed not to be Turing-complete
Bitcoin was intentionally designed to avoid these risks by not being Turing-complete. Its scripting language, Bitcoin Script, is limited in functionality, focusing instead on security and transaction validity. This makes Bitcoin a robust, decentralized digital currency, but it also limits its ability to support more sophisticated applications.
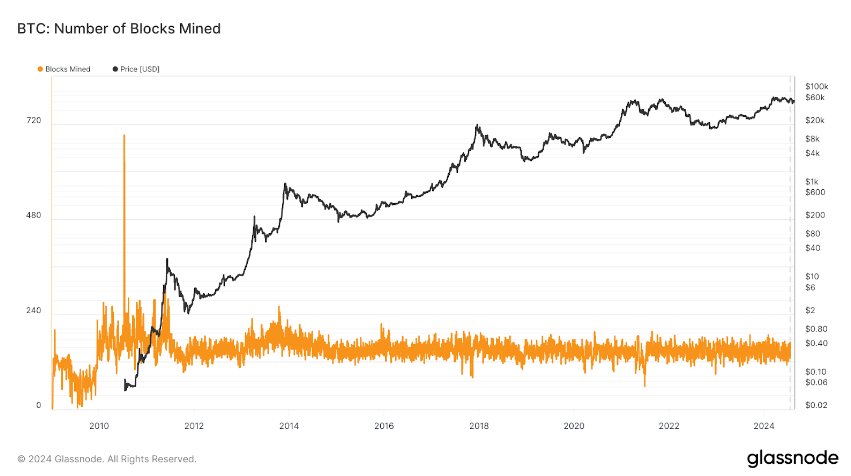
The Bitcoin blockchain is deliberately slow, minimal, and resistant to change, producing blocks every 10 minutes on average—about 140-150 blocks per day—with just 5-7 transactions per second. These design choices prioritize security and ensure the integrity of $BTC as a decentralized digital currency, rather than a general-purpose computing platform. This is why Bitcoin is regarded as the most decentralized, secure, and durable blockchain.
Figure 2: Bitcoin – Number of blocks mined vs Price (USD)
Source: Glassnode
The primary function of Bitcoin’s scripting language, Bitcoin Script, is to define spending conditions and verify transaction validity within the network, not to support general-purpose computation. It has a deliberately limited set of operations—a.k.a. opcodes—designed to ensure security and avoid vulnerabilities that could arise from more complex scripting. Because of this, Bitcoin Script lacks features essential for Turing completeness, such as performing repetitive computations or making conditional decisions. These limitations are intentionally imposed to maintain the security and stability of the Bitcoin network.
The properties that make Bitcoin an excellent form of decentralized money do not translate to be suitable for decentralized application development. Bitcoin lacks fully expressive smart contracts and fast performance, making it unsuitable for building sophisticated applications directly on its network. As a result, $BTC remains a passive asset, with most decentralized applications being built on Ethereum and other Layer 1 (L1) blockchains.
Bitcoin Programmability and Capital Efficiency
Since its inception in 2009, $BTC has been widely recognized as a Store of Value (SoV) and hedge against inflation. While originally intended to be used for peer-to-peer payments, its fixed supply and halving periods make it analogous to digital gold, representing digital ownerships and property rights that can be used to protect savings against devaluing currencies. During the years, $BTC has gained an ever growing attention, culminating in the institutional adoption marked by the 2024 $BTC Spot ETF approval in the U.S., finally recognizing it as an asset class.
Given its properties and use as “sound money”, there has recently been growing interest in using $BTC as a productive asset that can be used as collateral to unlock liquidity. However, perhaps the most significant turning point in this shift toward “Building on Bitcoin” was the introduction of NFTs inscribed on the actual Bitcoin L1—Ordinals at the end of 2022. Since then, the number of projects and developers building on Bitcoin has significantly increased. Numerous Bitcoin Layer 2 solutions have emerged, each employing different technologies and architectures but sharing the common goal of expanding Bitcoin’s programmability and capital efficiency, enabling use cases that go beyond NFTs and digital collectibles. Whether this is truly needed or desired by $BTC holders, investors, and miners remains to be seen.
However, increased usage of the underlying chain inevitably results in more fee generation, which is critical for the long-term sustainability of the chain when miner rewards finish in 2140 after reaching the maximum 21 million supply. As Satoshi Nakamoto predicted, “In a few decades when the reward gets too small, the transaction fee will become the main compensation for nodes”. Bitcoin halving refers to the periodic reduction of the reward given to miners for verifying transactions on the network, occurring approximately every four years. Currently, miners receive 3.125 BTC per block. With each halving, this reward decreases, which can impact network security in two significant ways: (1) it reduces the profitability of mining, causing some miners to shut down if the costs outweigh the rewards, and (2) it lowers the cost of executing a 51% attack, as the expense of bribing miners to conduct such an attack decreases with each halving. In this scenario, Bitcoin Layer 2 solutions are essential for the sustainability of the Bitcoin network. These L2s pay fees to the Bitcoin Layer 1, thereby generating ongoing demand for Bitcoin’s blockspace. This demand will help compensate miners for the declining block rewards, thus contributing to the security and longevity of the network, and this is not something that can be achieved with other alternatives like trusted custodians holding $BTC and issuing a wrapped version on another chain.
Making Bitcoin more “programmable” means addressing the limitations of Bitcoin’s native smart contracts and scaling capabilities. Its scope includes different verticals, such as:
- Interoperability: bridging and compatibility with popular Virtual Machines (VMs) used in other L1 environments.
- Complex DeFi Features: Decentralized exchanges (DEXs), synthetic assets, lending markets, liquid staking, and more..
- Issuance of New Assets: Using specific token standards on Bitcoin, like Ordinals, BRC-20, or Runes.
- Usage as Data Availability (DA) Layers: Layer 2 solutions that utilize Bitcoin as a data availability layer, such as rollups, sidechains, and other scaling solutions.
Nevertheless, making $BTC “a capital efficient and productive asset that is able to generate yield” involves primarily treating $BTC as a SoV while creating basic financial products on top of it, such as:
- Trustless $BTC staking and yield-generating activities, such as interest payments from lending.
- Native stablecoins and Collateralized Debt Positions that rely on the $BTC as collateral—$BTC-backed stablecoin.
- Insurance on Bitcoin, either on-chain or off-chain.
- Layer 2 solutions, defined in this context as any scaling solutions that speed up transactions and lower fees on the Bitcoin Network. This would be the equivalent of a smart contract platform like Ethereum but using $BTC as the canonical asset for transaction fees.
Bitcoin Layers and the L2 Trilemma
Bitcoin Layer 2 solutions focus both on programmability and capital efficiency. These layers extend the functionality and performance of the Bitcoin blockchain without requiring any changes to it, enabling sophisticated applications that need fully-expressive smart contracts, higher performance, or enhanced privacy.
It’s important to understand that Bitcoin L2s have different goals compared to L2s on other L1s like Ethereum. While Ethereum L2s primarily aim to improve scalability, Bitcoin L2s target both scalability and expanded functionality. This means that the Bitcoin blockchain itself cannot verify transactions on its L2s. Instead, the Virtual Machine (VM) for each layer handles transaction processing, verification, and settlement on Bitcoin, ensuring shared history and finality. Therefore, Bitcoin layers must deliver maximum functionality with minimal counterparty risk.
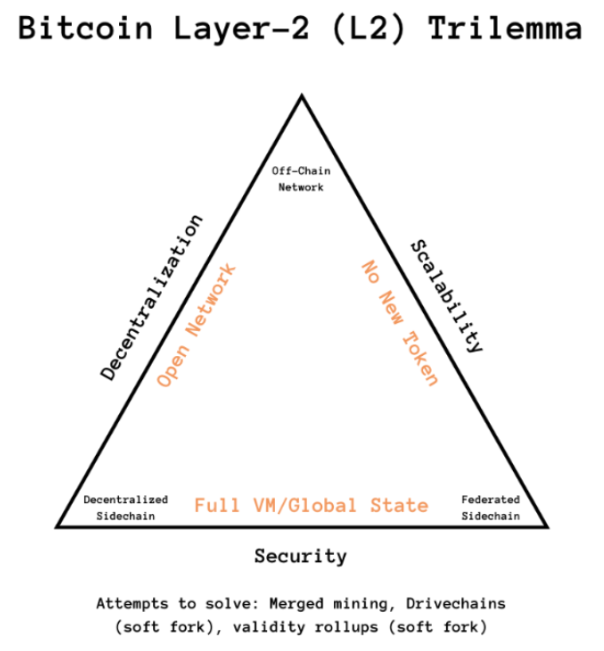
One way to categorize these solutions, as introduced by Trevor Owens, involves organizing them based on their approach to addressing the Bitcoin L2 trilemma, which segments L2 solutions into Off-Chain Networks, Decentralized Sidechains, and Federated Sidechains, each presenting unique approaches and trade-offs.
Figure 3: The Bitcoin Layer-2 Trilemma
Source: Spartan Research
Off-chain networks focus on scalability and privacy but can create user experience challenges (e.g., Lightning). Decentralized sidechains introduce new tokens and consensus mechanisms, enhancing functionality but potentially complicating user experience and raising centralization concerns (e.g., Stacks). Federated sidechains improve efficiency by relying on a trusted consortium, though this may compromise Bitcoin’s core principle of trustlessness (e.g., Liquid and Rootstock).
Another way, which emphasize more the key properties a Bitcoin L2 should have, has been provided by Stacks, which in its whitepaper suggests the following:
- Open-source and decentralized development process
- Full VM support and ability to program with expressive, high-level languages
- Fast transaction and block times (don’t need to wait 10-30 minutes for Bitcoin blocks)
- A trust-minimized way to move $BTC between L1 and L2
- $BTC as the primary asset deployed in L2 apps
- The ability to pay for L2 transactions in $BTC
- The ability to unilaterally withdraw your $BTC back from the L2 with no counterparty risk
Like the L2 Trilemma, achieving all these properties is a complex challenge, and only a few projects have come close to covering all of them.
Bitcoin Layers 2 Landscape
Layer 2 solutions for Bitcoin can be broadly categorized into different types, each offering a unique approach to scaling and enhancing the network’s capabilities.
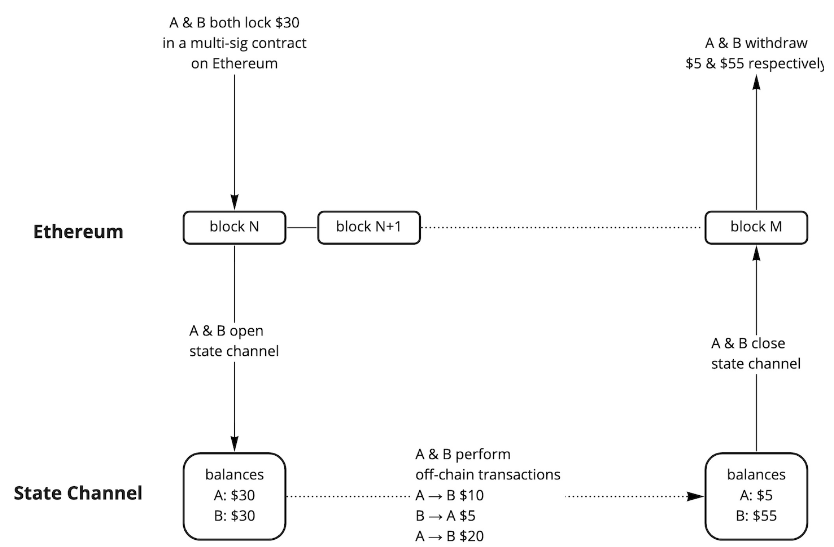
State channels enable multiple parties to open private channels for off-chain transactions, with only the opening and closing balances recorded on the blockchain. This method conserves resources and block space, leading to faster payments and lower fees. However, state channels offer limited functionality, as they do not support smart contracts—and trustless applications cannot builtand without smart contracts.
Figure 4: State Channel user flow. The number of Ethereum transactions can be reduced to 2: open and close channels
Source: Alpha Venture DAO Blog
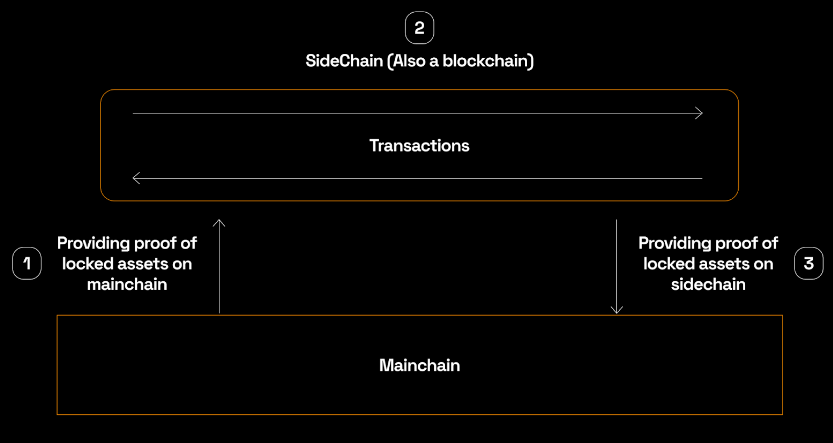
Sidechains are independent blockchains that run parallel to the main Bitcoin chain, allowing assets to be transferred between the two. This enables sidechains to operate under their own rules and protocols, often using a synthetic Bitcoin as the native currency instead of having their own gas asset. Sidechains can offer faster transactions, experimentation with new consensus and protocol designs, and support for features like smart contracts. However, they typically have lower security due to their independent consensus mechanisms, which are less robust than Bitcoin’s. In sidechains, $BTC is “pegged-in” as a derived asset with a 1:1 value to $BTC, enabling smart contracts to operate without much interaction with the Bitcoin blockchain. When needed, $BTC can be “pegged out” back to the Bitcoin blockchain.
Figure 5: Sidechains workflow
Source: Rootstock Blog
The main connection to Bitcoin is through these peg-in and peg-out processes and, in some cases, through using Bitcoin mining power in merged-mining approaches (e.g., Rootstock). Unlike some Bitcoin L2 layers like Stacks, which can directly interact with Bitcoin transactions, most Bitcoin sidechains (e.g., Liquid and Rootstock) don’t support open-membership peg-outs and instead rely on federations or centralized custodians.
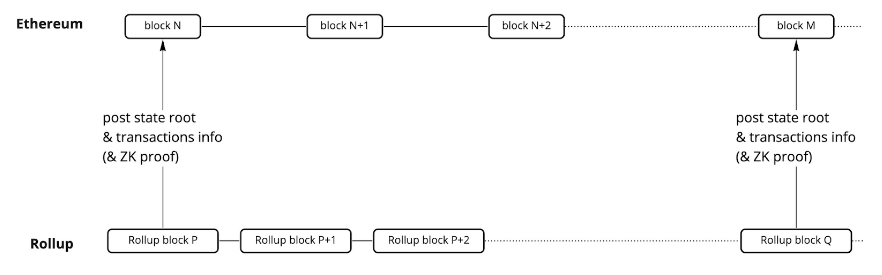
Rollups are a solution that enables smart contract execution off-chain while storing only the data on-chain. Unlike sidechains, rollups typically use their own token for transaction fees. There are two main types: Optimistic Rollups and ZK-Rollups. Both bundle multiple transactions into a single proof, which is then posted to the main chain. The key difference lies in how the proof is generated and verified.
Figure 6: Rollup post both state root and compressed transaction info (plus ZK proof in ZK rollup)
Source: Alpha Venture DAO Blog
Here are some well-known Bitcoin L2s that utilize these solutions.
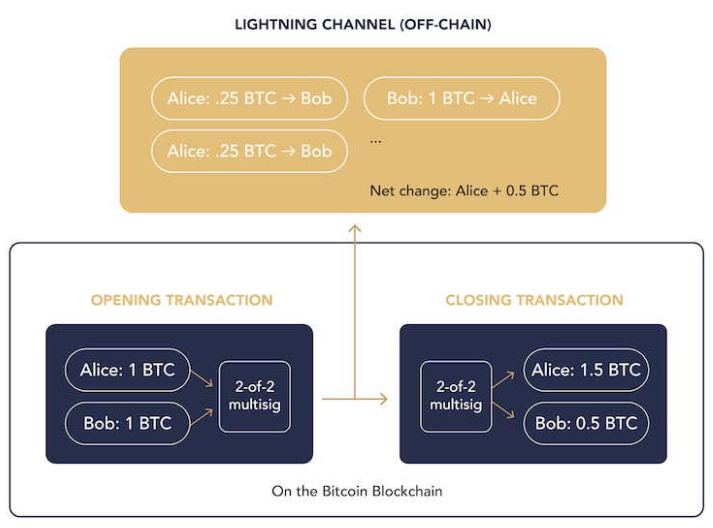
Lightning Network
Lightning Network is a layer 2 payment protocol for Bitcoin that enables fast, low-fee transactions through off-chain channels. Its strength lies in its ability to conduct an almost unlimited number of transactions between parties, with only the final state of the transactions being recorded on the Bitcoin blockchain.
Figure 7: Lightning Network – Workflow
Source: River Learn
This reduces transaction fees and increases speed significantly. However, Lightning is not a blockchain: it can’t support smart contracts and more complicated applications. It’s the oldest and most widely adopted Bitcoin Layer 2, with about 5,000 $BTC locked inside it.
Liquid Network
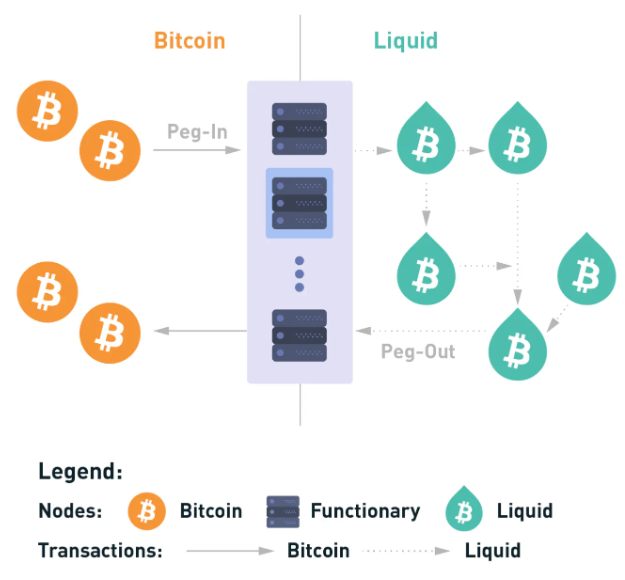
The Liquid Network is a Bitcoin sidechain designed to increase transaction speed and privacy through confidential transactions, which allow users to hide transaction amounts. It introduces Liquid Bitcoin (L-BTC) and supports the issuance of new digital assets, such as tokenized fiat, cryptocurrencies, and securities.
Figure 8: The Liquid Network – L-BTC issuance
Source: Nervos
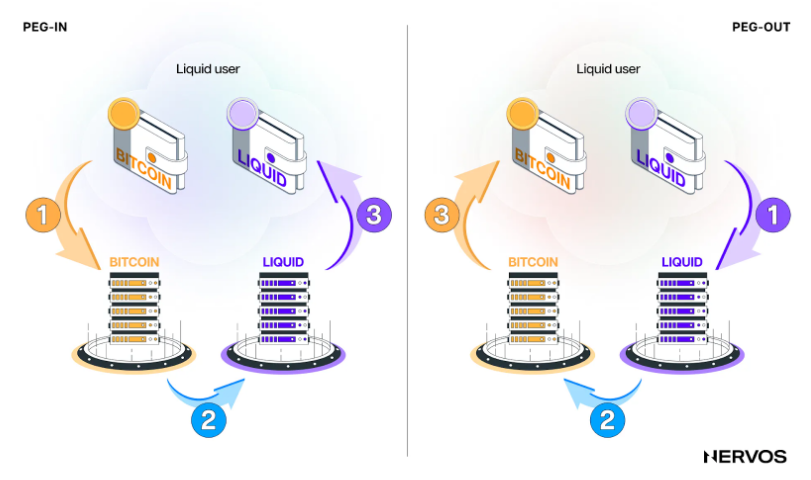
Liquid operates as a centralized, permissioned chain with faster block times (one minute) and two-block finality, using a proof of authority consensus. Transactions and blocks are signed by a federation of blocksigners, while $BTC withdrawals (“peg-outs”) are managed by a federation of “watchmen.” The “peg-in” process transfers $BTC to Liquid, converting it into L-BTC, which is backed by real $BTC on Layer 1.
Figure 9: The Liquid Network – Peg-in/out process
Source: Nervos
However, Liquid does not inherit Bitcoin’s security guarantees and does not allow permissionless $BTC withdrawals directly to Layer 1.
Rootstock
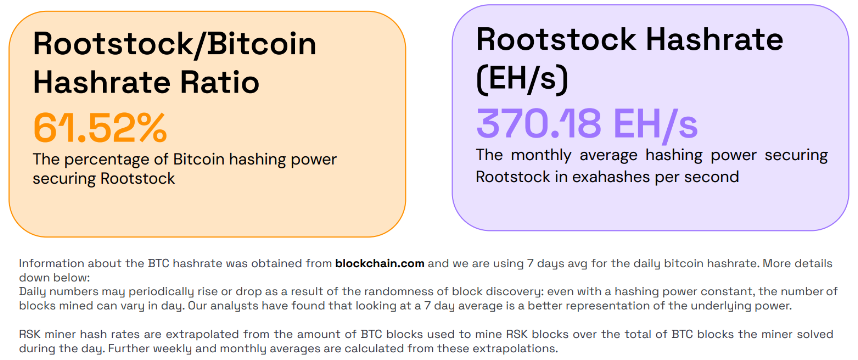
Rootstock is an EVM-compatible, smart contract-enabled sidechain that extends Bitcoin’s functionality by allowing Turing-complete smart contracts and DeFi applications using synthetic Bitcoin (RBTC). Unlike Liquid, which is a centralized sidechain, Rootstock partially inherits Bitcoin’s security through merged mining, enabling Bitcoin miners to mine Rootstock blocks alongside Bitcoin at minimal extra cost. This process provides Rootstock with additional security, backed as per now by around 60% of Bitcoin’s hash rate, though it remains vulnerable to potential attacks if miner incentives decline.
Figure 10: Rootstock/Bitcoin Hashrate Ratio and monthly average hashing power securing Roostock
Source: Rootstock x Bitcoin Mining Report, Q2 2024
This security largely depends on the Bitcoin miners’ self-interest in securing additional revenues from Rootstock transaction fees. If the activity on the sidechain were to drop, the incentives for merge-mining would diminish, leaving Rootstock vulnerable to relatively low-cost 51% attacks and MEV or double-spend-motivated chain reorganizations. Additionally, mining a smart contract-enabled chain differs from Bitcoin mining, as it requires more computational resources. As smart contract activity grows on Layer 2, merge-mining may become less appealing to Bitcoin miners, who can opt out at any time. This could lead to centralization risks in block production on the merge-mined chain.
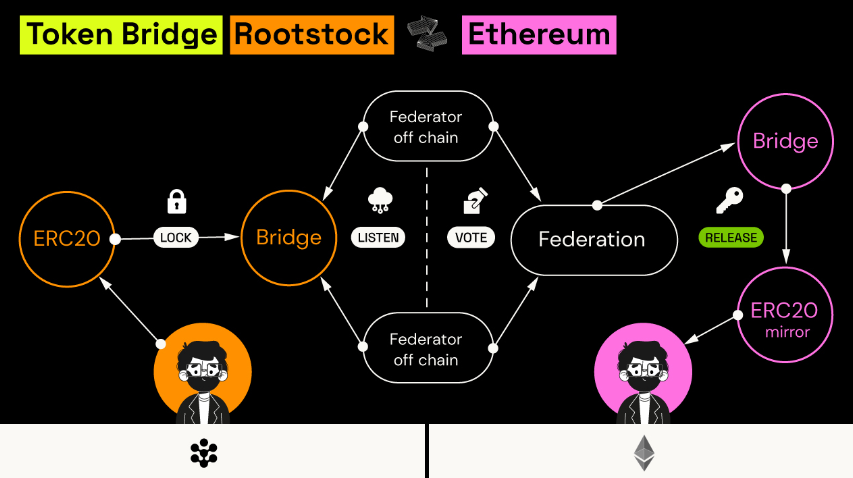
Rootstock’s two-way peg system, similar to Liquid’s, involves locking $BTC on the Bitcoin network and minting equivalent RBTC on Rootstock, managed by a semi-trusted Federation.
Figure 11: Rootstock – Token Bridge
Source: Rootstock Documentation
Although this system isn’t fully trust-minimized, it automates withdrawals without human intervention. Rootstock does not require a native token, with RBTC used for transaction fees, relying instead on Bitcoin’s security infrastructure, though this approach may face challenges as smart contract activity increases, potentially making merge mining less attractive to Bitcoin miners.
Stacks
Stacks is a Bitcoin layer for smart contracts, enabling decentralized applications to use Bitcoin as an asset in a trust-minimized way and settle transactions on the Bitcoin blockchain. Launched in 2021, Stacks introduced Bitcoin settlement, the Clarity language for safe contracts, and atomic swaps with $BTC. The upcoming Nakamoto release will enhance Stacks by adding: (a) a decentralized, two-way Bitcoin peg to move $BTC in/out of the layer and write to Bitcoin, (b) transactions secured by Bitcoin finality, and (c) fast transaction and block times. For this reason, Stacks is not really a sidechain, as Stacks layer will follow Bitcoin finality with 100% Bitcoin hashpower – this is very similar to reorg resistance of sovereign rollups.
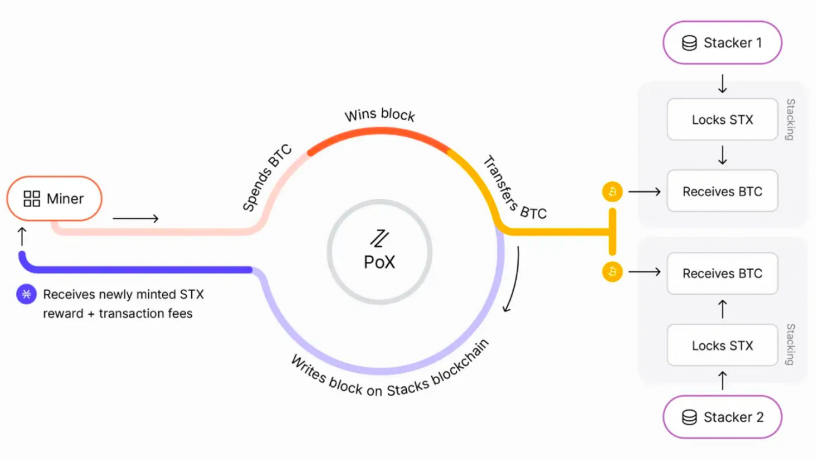
Stacks’ smart contracts are written in its proprietary Clarity language and they are not compatible with the Solidity code that dominates other smart contract platforms. Moreover, unlike Liquid and Rootstock, Stacks has its own native token, $STX, which is central to its Proof-of-Transfer (PoX) consensus mechanism. In PoX, Stacks miners spend $BTC and are rewarded in $STX, similar to Bitcoin’s Proof-of-Work but with a unique integration with Bitcoin. Stacks miners use a BFT-style quorum to mine blocks every 5 seconds, while Bitcoin blocks serve as settlement points, securing Stacks’ transaction history.
Figure 12: Stacks – Proof of Transfer
Source: Stacks Docs
Post-Nakamoto, Stacks will feature two types of blocks: fast blocks (every 5 seconds) and settlement blocks (every Bitcoin block), with most of Stacks’ history secured by Bitcoin’s hash rate. This dual security budget—combining $BTC spent by miners and Bitcoin’s full security—makes Stacks more secure than Liquid or Rootstock. The sBTC peg in Stacks, managed by Stackers who lock STX as collateral, offers decentralized, permissionless peg management, providing better security guarantees than federated models.
Bitlayer
Bitlayer, the main topic of this report, describes itself as the first Layer 2 solution offering Bitcoin-equivalent security and Turing completeness. It is also the first Layer 2 built on BitVM, aiming to be the computation layer of Bitcoin. The solutions offered by Bitlayer do not fundamentally alter Bitcoin in any way, nor do they necessitate the promotion of a Bitcoin Improvement Proposal (BIP) upgrade. In Bitlayer’s team vision, Bitcoin should function just as it always has.
Bitlayer’s approach combines the value of $BTC with the complex applications that can be built on top of a programmable layer supported by smart contracts. With Bitlayer, developers can write and deploy complex smart contracts using their preferred language and toolchain. Applications of all kinds can be developed and supported similarly to other Layer 1 (L1) and L2 blockchains, adding more utility to $BTC by expanding the opportunity set and use cases.
Overview
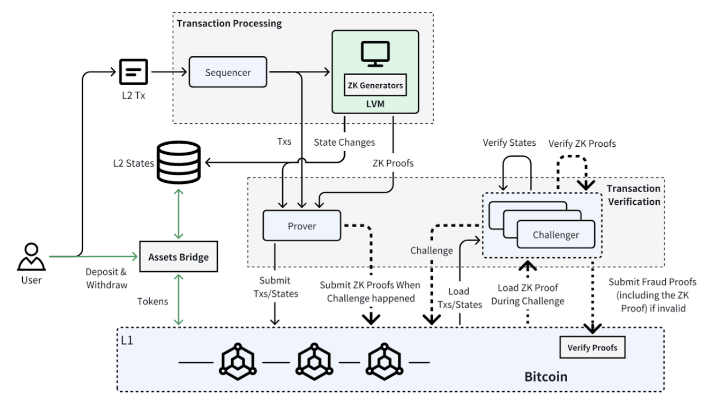
From an architectural point of view, Bitlayer is a fairly typical example of a Rollup-equivalent model. Its design is inspired by BitVM, DLC/LN (Discreet Log Contract/Lightning Network) technical protocols, and multiple VMs (including EVM, the Ethereum Virtual Machine). Based on this tech stack, Bitlayer aims to address three core challenges faced by second layers relative to the following components: (1) transaction processing, (2) transaction verification, and (3) asset bridging.
Figure 13: Bitlayer Architecture
Source: Bitlayer Docs
The transaction processing in Bitlayer uses a Turing-complete Layer 2 virtual machine, starting with Ethereum Virtual Machine (EVM) compatibility. This allows Ethereum applications and developers to migrate to Bitlayer with minimal changes. Future plans also include support for additional VMs to offer a wider range of on-chain applications. For transaction verification, Bitlayer opted to rely on BitVM’s fraud-proof protocol, which enables security comparable to Bitcoin’s base layer. Finally, the asset bridging component integrates OP-DLC with the BitVM bridge, offering a trustless model for cross-chain asset transfers. This approach enhances security beyond traditional TSS/Multisig methods, making Layer 2 assets as secure as those on Bitcoin’s base chain.
Transaction Processing
Transaction processing in Bitlayer combines a sequencer and a Layered Virtual Machine (LVM) to efficiently handle and execute transactions.
The sequencer, similar to those in other L2 solutions, collects and sorts cached transactions, acting as the gateway for incoming transactions to ensure orderly processing. The LVM serves as Bitlayer’s computational backbone, executing smart contracts and generating the latest states along with zero-knowledge proofs. These proofs are essential for verification, allowing challengers to dispute execution results. The LVM’s versatility and security make it a powerful tool for executing smart contracts across various blockchain ecosystems.
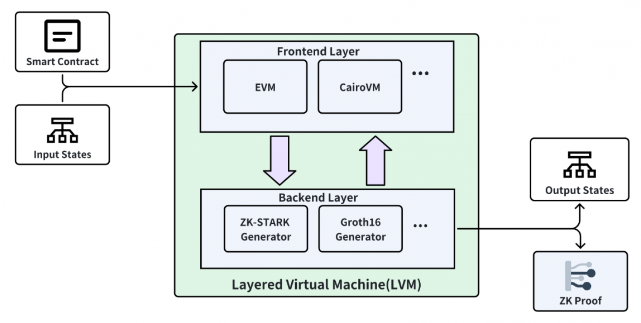
Figure 14: Bitlayer – Layered Virtual Machine (LVM)
Source: Bitlayer Docs
LVM technology enables the integration of multiple frontend smart contract platforms, such as the EVM the CairoVM, making it accessible to developers from various blockchain ecosystems who can use familiar tools for Bitcoin. On the backend, LVM incorporates zero-knowledge proof generators like ZK-STARKs and ZK-SNARKs, which are crucial for ensuring computation integrity and privacy without exposing underlying data.
The use of diverse zero-knowledge-proof technologies improves transaction verification, optimizing the dispute resolution process within Bitlayer.
Transaction Verification
Layer 2 state transition verification operates on a principle akin to proving innocence, where the security of the Layer 2 network is determined by the underlying network used for verification. By leveraging Bitcoin’s base layer, thanks to the integration of BitVM, Bitlayer can inherit Bitcoin’s robust security, achieving security levels comparable to Bitcoin itself.
Transaction verification in Bitlayer is handled through a zero-knowledge-based optimistic mechanism involving both provers and challengers to ensure adherence to network rules. The Prover submits L2 transactions and their execution states to the Bitcoin blockchain, and if challenged, must reveal zero-knowledge proofs on-chain to validate the transactions. The Challenger monitors these submissions, scrutinizing execution states and proofs. If any discrepancies or malicious activity are found, the Challenger initiates a challenge process by generating and submitting fraud proofs to the L1 chain. The dynamic between Prover and Challenger is crucial, as their interaction directly impacts the verification of transactions.
Asset Bridging
The most common approach in the industry currently involves Layer 2 platforms setting up a multi-signature account based on MPC-TSS (Multi-Party Computation and Threshold Signature Scheme) or native multisig, which are controlled by the platform. Thus, the security of assets is determined by the platform’s capability to manage these multi-signatures. This traditional approach results in users completely losing control of their assets, while the platform’s multi-signature management capabilities retain the power to impact the security of those assets.
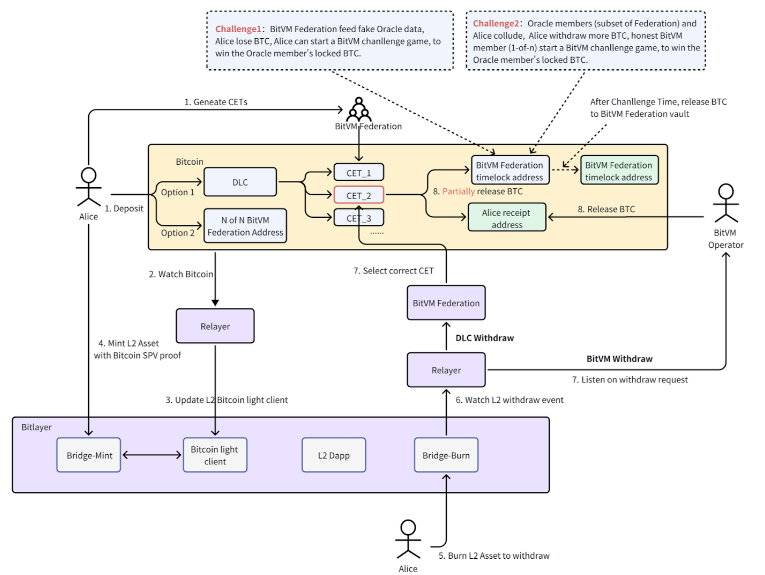
The Bitlayer team took another direction, believing that DLC (Discreet Log Contracts), a bilateral game model, combined with BitVM represents a stronger direction for asset security. The model achieves a superior asset bridge model compared to MPC-TSS/Multisig, in that DLC executes conditional Bitcoin transactions directly on the Bitcoin blockchain, eliminating the need for external validators. For this reason, on Bitlayer, no single entity can gain excessive control or influence, as users retain full ownership and control over their funds.
Additionally, to meet different security and operational needs, Bitlayer implements a dual-channel, two-way peg asset bridge. This dual-channel approach offers two key advantages: (1) it diversifies security options for users, and (2) it enhances system scalability, allowing efficient performance even under high demand.
The first channel, the OP-DLC Bridge, enables users to lock $BTC in a trustless, self-controlled manner. It introduces a novel challenge protocol to address potential oracle collusion in the original DLC protocol, providing greater security and user autonomy. The second channel, the BitVM Bridge, operates under a minimally trusted custodian model—BitVM Federation nodes—requiring only 1 of N security, making it ideal for users who prioritize flexibility and speed over the stricter security of the OP-DLC channel.
The asset bridge’s security model is built on the strong security foundation of the Bitcoin blockchain as the base layer. However, it also recognizes potential vulnerabilities within the BitVM Federation nodes that manage the bridge. The model is designed to withstand an adversary compromising up to n−1 nodes, maintaining the system’s integrity as long as at least one node remains secure and operational.
Figure 15: Bitlayer – Dual channel architecture
Source: Bitlayer Docs
The four main components of the Bitlayer bridge are: (1) BitVM Federation, (2) DLC components, (3) L2 smart contracts, and (4) Relayers.
The BitVM Federation improves security and decentralization by acting as the verification network, ensuring secure execution of L2 transactions and stable bridge operation. Nodes in the federation join by depositing $BTC and serve a dual role, also acting as oracles for the OP-DLC channel. The DLC components manage user-controlled asset deposits and withdrawals with predefined CETs, ensuring precise and flexible transaction management. L2 Smart Contracts include the bridge and light client contracts. The bridge contract handles the issuance and destruction of $BTC assets on L2, while the light client contract ensures Bitcoin block header information is current using ZKP-based state proofs. It also includes a Verify function for validating Bitcoin transactions through SPV (Simplified Payment Verification), ensuring trustless issuance of L2 $BTC assets. Finally, Relayers maintain the bridge’s operation by monitoring both Bitcoin and Bitlayer networks, updating the state of light client data on L2 with zero-knowledge proofs. When a bridge transaction occurs, the relayer sends it to a smart contract or BitVM Federation node for further processing, ensuring continuous functionality.
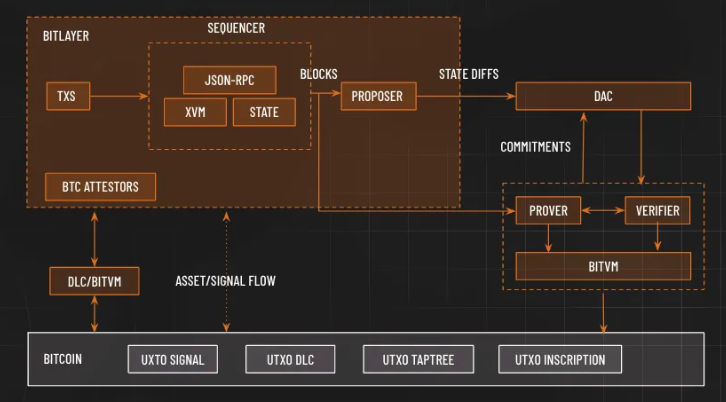
Achieving Bitcoin security equivalence through BitVM
In December 2023, Robin Linus, the project leader of ZeroSync, published a white paper titled “BitVM:Compute Anything On Bitcoin”. The paper proposed a Turing-complete Bitcoin contract solution that can execute any complex computation on Bitcoin without changing the network’s consensus rules or altering Bitcoin’s fundamental principles. Rather than executing computations on Bitcoin, they are merely verified, similarly to optimistic rollups. A prover makes a claim that a given function evaluates for some particular inputs to some specific output. If that claim is false, anyone can perform a fraud proof and punish the prover. Using this mechanism, any computable function can be verified on Bitcoin and on-chain execution is only required in the event of a dispute. On the other hand, if both operators and validators cooperate, any complex, stateful off-chain computation can be executed without leaving any trace on the blockchain.
The introduction of BitVM effectively makes Layer 2 state verifications on Bitcoin possible. Therefore, Bitlayer integrated it into its tech stack to enable Bitcoin security equivalence. Thanks to BitVM, Bitlayer can perform the bulk of its computational work off-chain, resulting in a minimal footprint and computational burden on the Bitcoin blockchain.
Figure 16: The central role of BitVM in Bitlayer’s architecture
Source: Bitlayer Documentation
However, the original BitVM design was limited to a two-party configuration. Later developments combined parallel and redundant instances to introduce multi-party configurations based on 1-of-n honesty assumptions. Still, a major limitation of these contracts is that all verifiers must be defined during compile time, and the setup cost increases with the number of verifiers. This means that the number of parties that could be bribed to compromise a contract is inherently limited.
Addressing these limitations, Robin recently proposed BitVM 2, a new variant where anyone can act as a verifier. While it still requires a one-time setup with a 1-of-n honesty assumption, during runtime, any party can challenge an invalid assertion without needing to be part of the initial verifier group. This design overcomes previous limitations and strengthens trust assumptions. Bridges still require a predefined set of m operators, with at least one acting honestly. Even if all operators are dishonest, they cannot steal deposits, only burn them at worst.
BitVM 2 could greatly benefit rollups and other L2s using BitVM as a two-way peg. A rollup operator (the prover in BitVM) can use their own funds to cover user withdrawals, periodically withdrawing from BitVM to reimburse themselves. If the operator fails to process withdrawals correctly, any user or interested party can penalize them by burning their funds.
As a final note, the security of a BitVM 2 instance ultimately depends on the n-of-n keyholders, although anyone outside this group can still challenge the prover. Because the prover has an efficient exit if unchallenged, and anyone can fund a challenge transaction, the n-of-n funding multisig could adopt a setup and key deletion ceremony, similar to the Zcash launch, to increase its security.
Sector Outlook
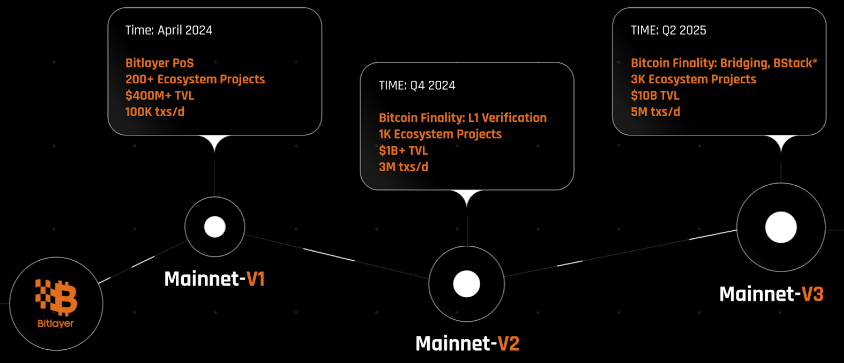
The development of Bitlayer is structured into a phased rollout of its mainnet, each designed to progressively improve the platform’s capabilities, improve user experience, and integrate solid security measures aligned with Bitcoin’s consensus mechanisms and onchain activities.
Figure 17: Bitlayer Roadmap
Source: Bitlayer Documentation
In April 2024, the V1 was launched on mainnet. During this phase, Bitlayer adopts a PoS + Multisig security model, working with multiple MPC custody platforms, and mainly focusing on onboarding users and developers through a 100% EVM compatible environment.
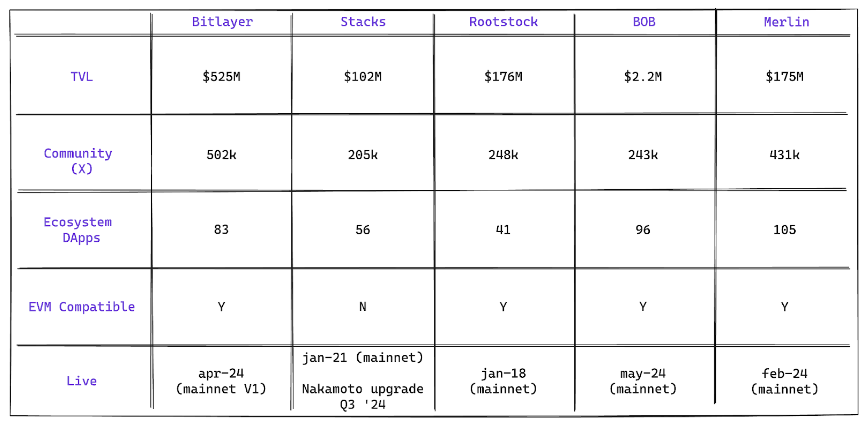
Since its launch, Bitlayer has shown rapid growth across various metrics, surpassing even well-established L2 competitors like Merlin, Rootstock, and Stacks.
Figure 18: Bitcoin L2s key metrics comparison
Source: Projects websites, DefiLlama, Dune Analytics, Revelo Intel. As of August 2024
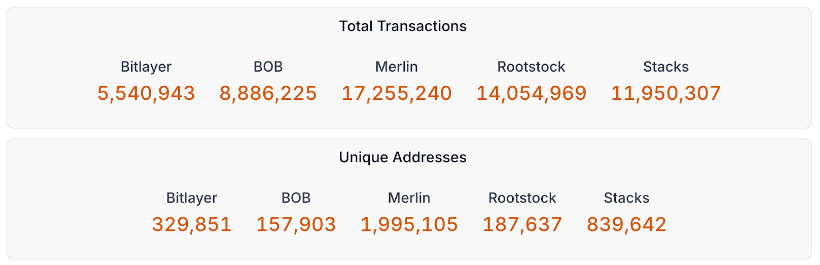
Even in terms of total transactions and unique addresses, Bitlayer has already surpassed, or is rapidly closing the gap with, its main competitors.
Figure 19: Bitcoin L2s – Total transactions and unique Addresses
Source: Signal21. As of August 20, 2024
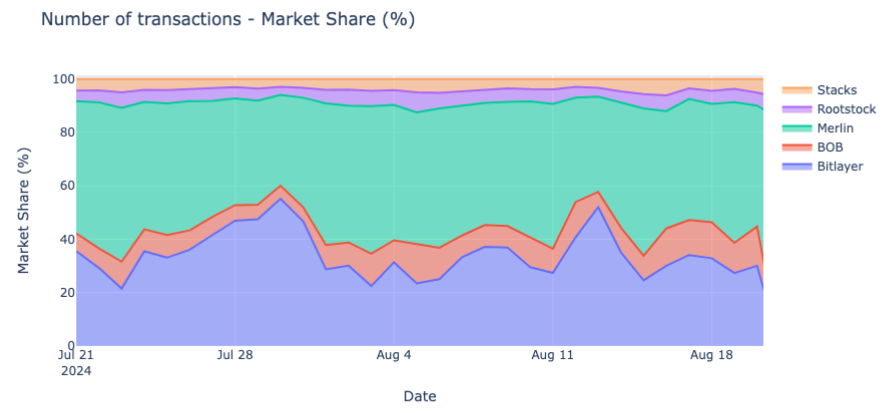
Finally, since July 2024, Bitlayer has stabilized its market share of transactions between 20% and 30%, second only to Merlin.
Figure 20: Bitcoin L2s – Transactions market share (%)
Source: Signal21, Revelo Intel. As of August 20, 2024
Conclusion
The exploration of Turing-completeness and security in blockchain technology highlights the deliberate choices made in the design of Bitcoin. Bitcoin’s architecture prioritizes security and decentralization, which has made it the most secure and durable blockchain, but at the cost of limited functionality. As the demand for more sophisticated applications grows, Layer 2 (L2) solutions have emerged to extend Bitcoin’s capabilities without altering its core design.
The current L2 landscape offers a variety of approaches, each addressing the trade-offs between scalability, functionality, and security in different ways. Solutions like state channels, sidechains, and rollups provide unique methods for improving Bitcoin’s performance and enabling more complex applications, but each comes with its own set of challenges and limitations.
Bitlayer stands out in this landscape by aiming to combine Bitcoin’s inherent security with enhanced programmability through its integration of BitVM. By leveraging a dual-channel asset bridge, a Layered Virtual Machine, and zero-knowledge proof mechanisms, Bitlayer offers a compelling approach to making Bitcoin more versatile while maintaining its security standards. The phased rollout of Bitlayer’s mainnet is expected to further solidify its position in the market, as it continues to grow and attract both users and developers.
Looking ahead, the sector’s outlook is promising, but the success of these L2 solutions will depend on their ability to effectively balance the complex trade-offs they face. As the ecosystem evolves, Bitlayer and other projects will play a crucial role in shaping the future of Bitcoin as both a secure store of value and a platform for decentralized applications.
References
Bitlayer, (2024) Bitlayer: Amplifying Bitcoin. Published on Medium | Link
Bitlayer, (2024) Introducing Bitlayer: The First Bitcoin Security-Equivalent Layer 2 Based on BitVM Scheme. Published on Medium | Link
Bitlayer White Paper (2024) | Link
BitVM Website | Link
Falkon S., (2017) The Story of the DAO – Its History and Consequences | Link
Kumar K., (2023) Decoding Satoshi’s Non-Turing Completeness Strategy for Bitcoin | Link
Lyndell, (2024) BitVM and its optimization considerations. Bitlayer Blog | Link
Nervos, (2024) The Ultimate Guide to Bitcoin Layer 2s: From Liquid, Rootstock, and Stacks to RGB (Part 1) | Link
Revelo Intel, (2024) Bitlayer – Project Breakdown | Link
Singh N., (2019) Turing Completeness and the Ethereum Blockchain. Published on Medium | Link
Spartan Research, (2023) Bitcoin Layers – Tapestry of a Trustless Financial Era | Link
Stacks: A Bitcoin Layer for Smart Contracts – White Paper | Link
Wang C., (2023) Our Bitcoin Thesis: The Panda Renaissance. Portal Ventures | Link
Xavier, (2024) BitVM Bridge Becomes Practical. Bitlayer Blog | Link
Disclosures
Revelo Intel is engaged in a commercial relationship with Bitlayer as part of an educational initiative and this report was commissioned as part of that engagement.
Members of the Revelo Intel team, including those directly involved in the analysis above, may have positions in the tokens discussed.
This content is provided for educational purposes only and does not constitute financial or investment advice. You should do your own research and only invest what you can afford to lose. Revelo Intel is a research platform and not an investment or financial advisor.